Cisco FTD application control provides the capability to control many applications and micro-applications based on the factory-configured signatures. signatures recognize applications based on many fields in the application layer.
Topology Overview
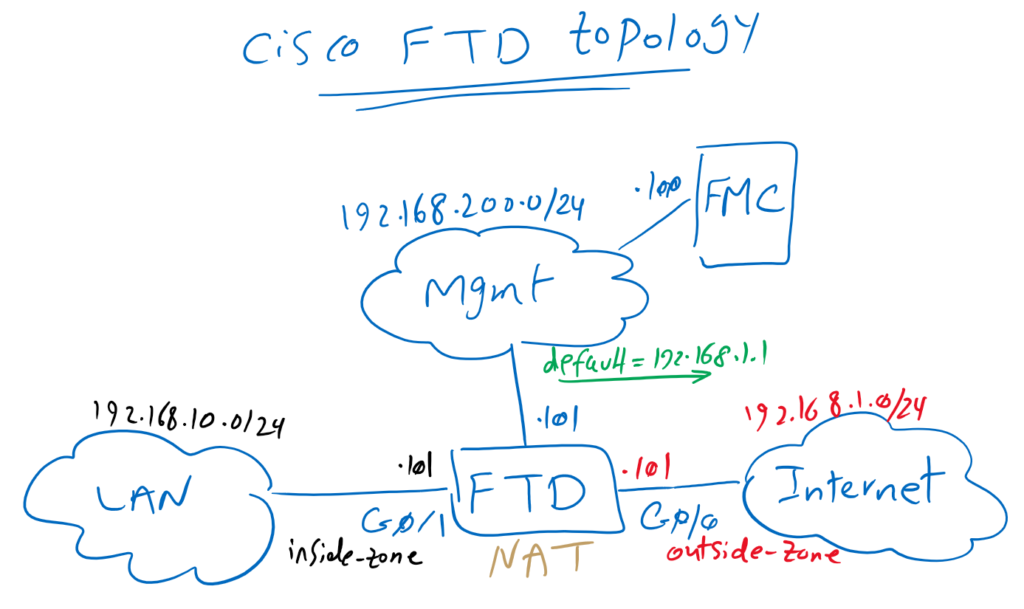
Just to review the topology, we have one FTD with two zones, inside and outside zones with IP subnet 192.168.10.0/24 and 192.168.1.0/24. Outside zone is connected to internet. Internet is shared to the inside zone with configuring a default route and NAT rule, implemented in previous sections.
FTD is managed through FMC over an out-of-band management network with IP subnet 192.168.200.0/24. We have connected FMC and FTD to each other in previous sections.
2. Cisco FTD Installation Guide (Version 7.0.1)
FTD Application Detectors Signatures
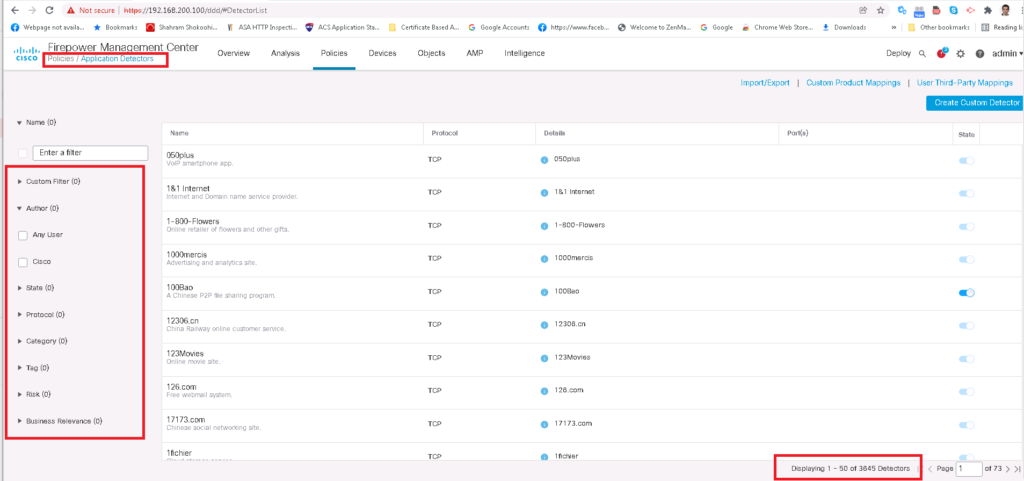
FTD is able to recognize many applications and micro-applications through predefined signatures. The list of signatures can be viewed in the “Application Detectors” sub-menu in the “Policies” menu.
There is already 3845 signatures pre-configured in FTD and they are pre-classified from different perspectives. For example how risky they are or which protocol they use.
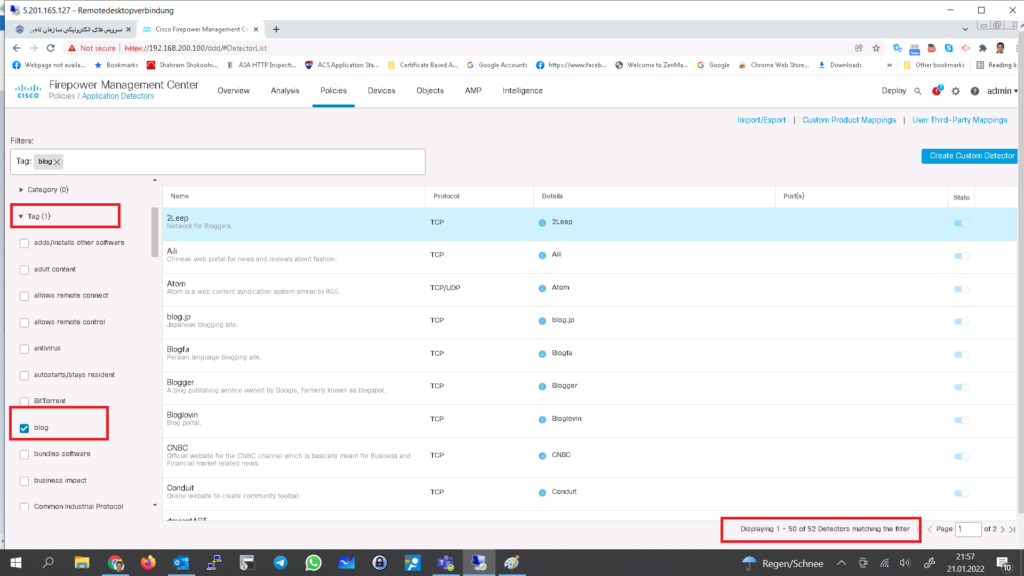
You can filter application detectors based on specific category. As an example there are 52 applications with “blog” tag.
Search Applications in Cisco FTD
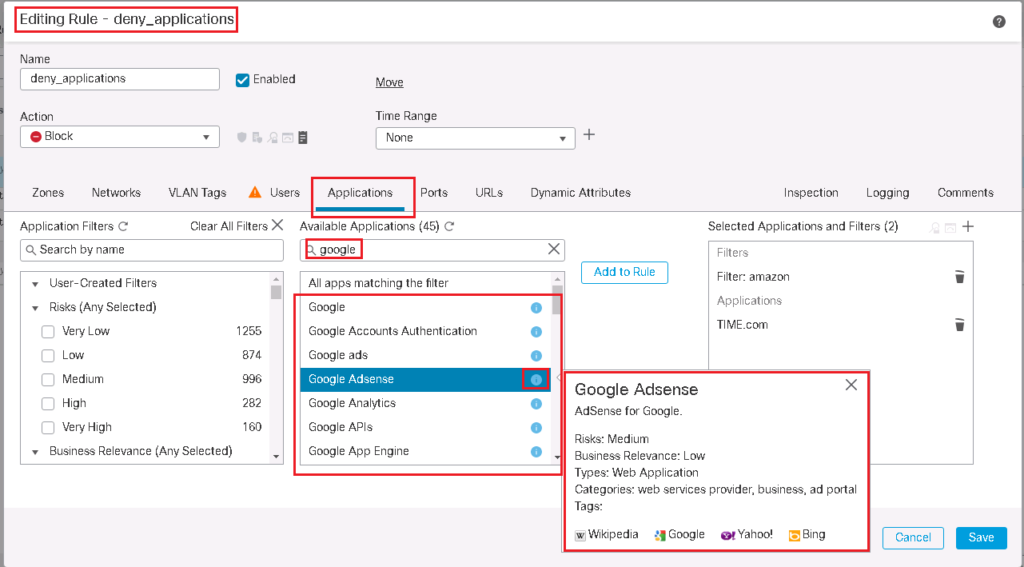
You can search applications and micro-application in any access control policy rules in “Applications” Tab. For example by searching “google”, any applications and micro-applications related to google are displayed.
By clicking blue info button beside applications, properties of the application is shown. For example, “Google AdSense” is a web based medium-risk application with low business relevance.
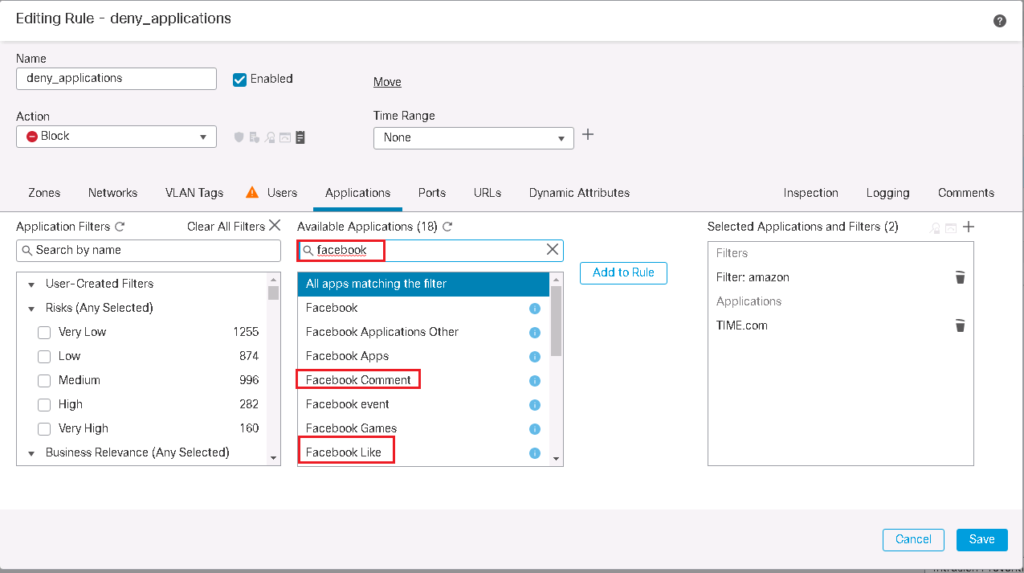
If you search Facebook, you see that you can control “Facebook Comment” or “Facebook Like” micro-applications separately. This also applies to many other applications.
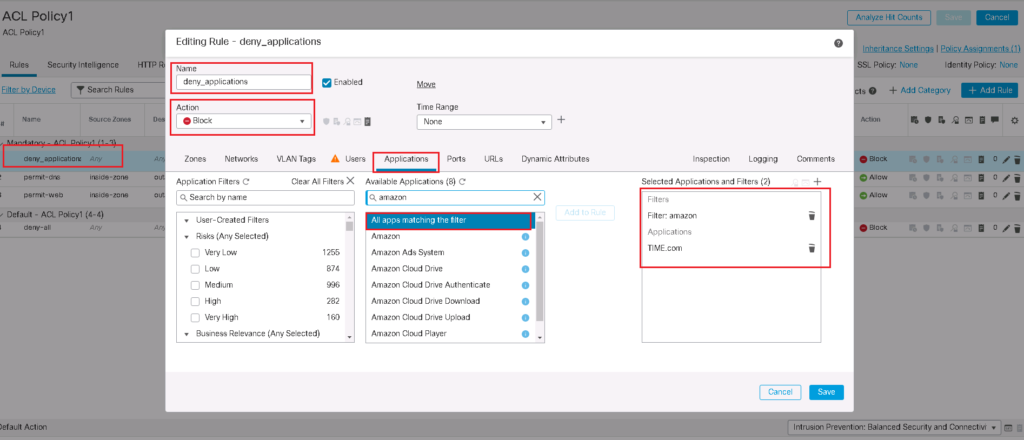
Cisco FTD Application Control Configuration Example
Just for a test, let’s add a rule to filter amazon related applications and also time magazine web portal “time.com”.
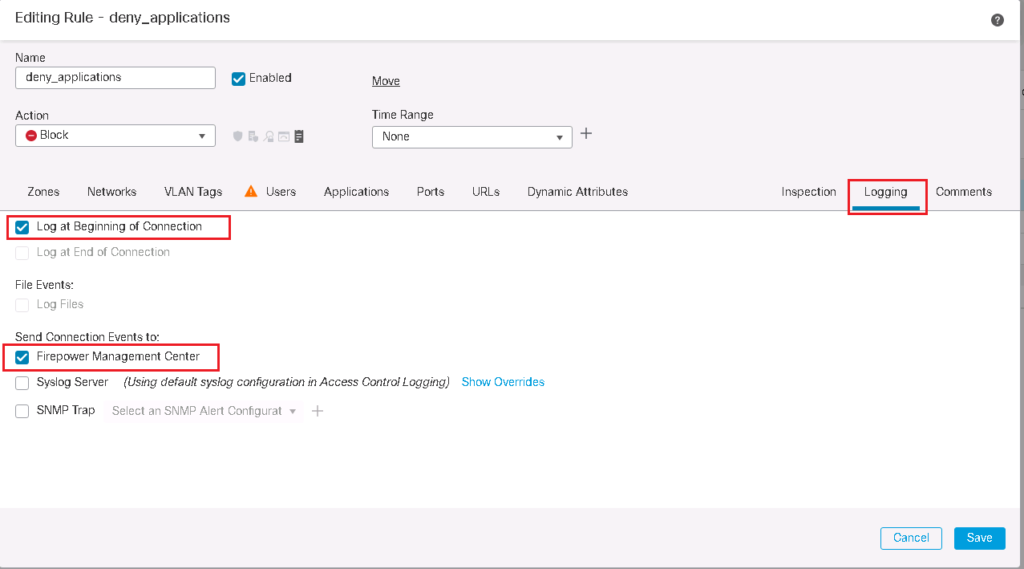
We also enable logging so we can monitor when these rules are matched. All the details of the traffic that matched the rule will be logged to be monitored.
Note that “application control” is more than “URL filtering”. With application control, you can control applications even when they are accessed from mobile apps because they are recognized not only by the URL but by many other fields in application header.
Monitor and Troubleshoot Cisco FTD Application Control
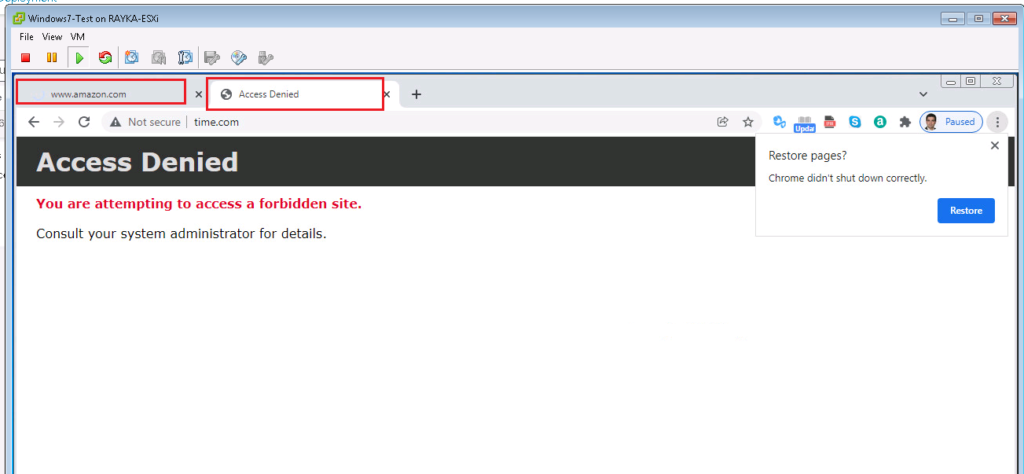
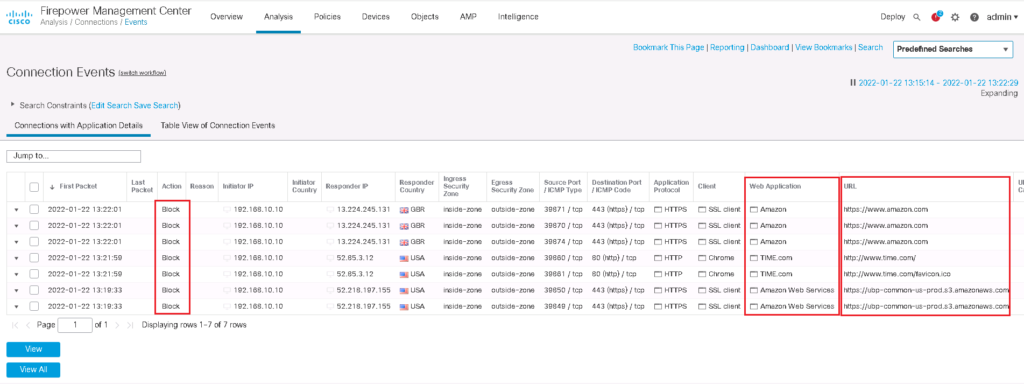
By browsing amazon and time.com web-sites, we can make sure if they are correctly filtered.
Now we can also look at the logs to see the details of the traffic that matched the rule.
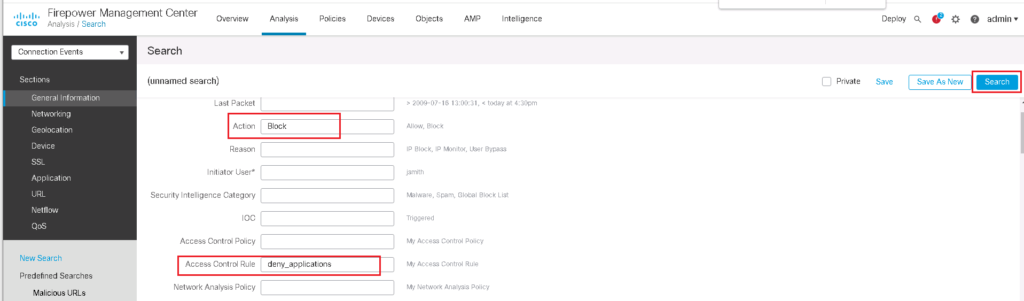
To filter logs to show only specific output, we use “Edit Search” option to show only logs with “Block” Action and traffic that are matched with the “deny_application” rule.
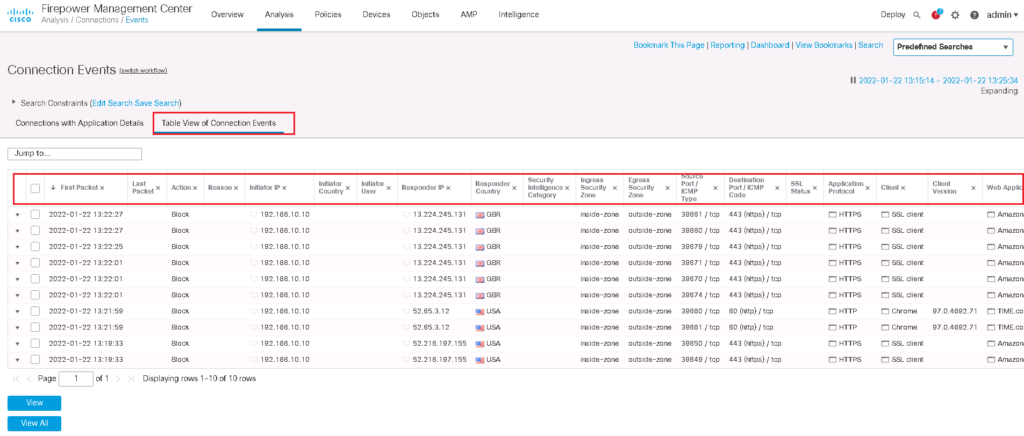
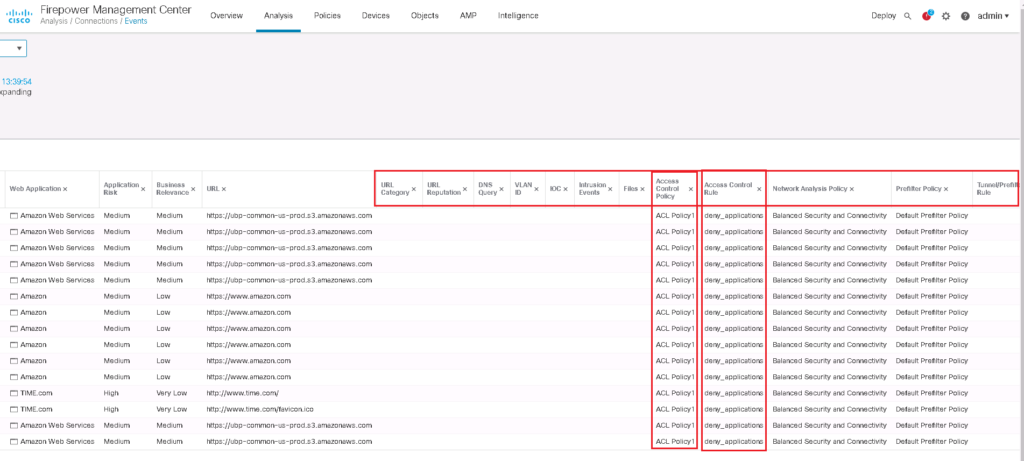
You can also choose to show “Table View of Connection Events”. With this option , you can see, not only application details but also FTD engines and rules matching the traffic. with this option you can make sure if intended traffic is matched as you wish or not.