Firepower Custom Application Detector gives the capability to add signatures for our custom business applications to the list of application detectors so that we can call them when we add an access control rule. In this section we will create a custom application detector specific to our business.
Topology and Custom Application Overview
Topology Overview
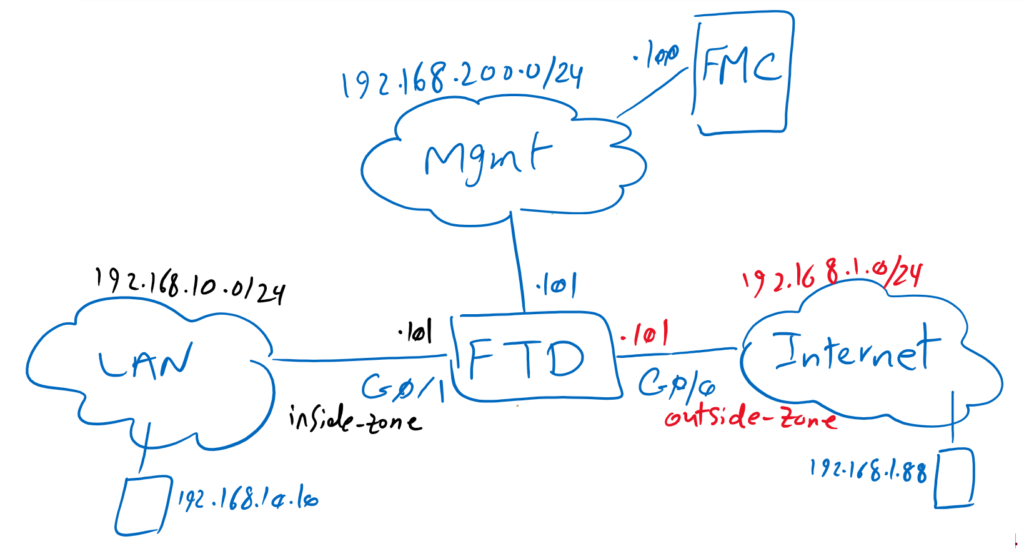
Just to review the topology, we have one FTD with two zones, inside and outside zones with IP subnet 192.168.10.0/24 and 192.168.1.0/24. Outside zone is connected to internet. inside zone is connected to the LAN. There are two computers for testing purposes, one with IP address 192.168.10.10 in inside zone and one with IP address 192.168.1.88 in outside zone.
Custom Application Overview
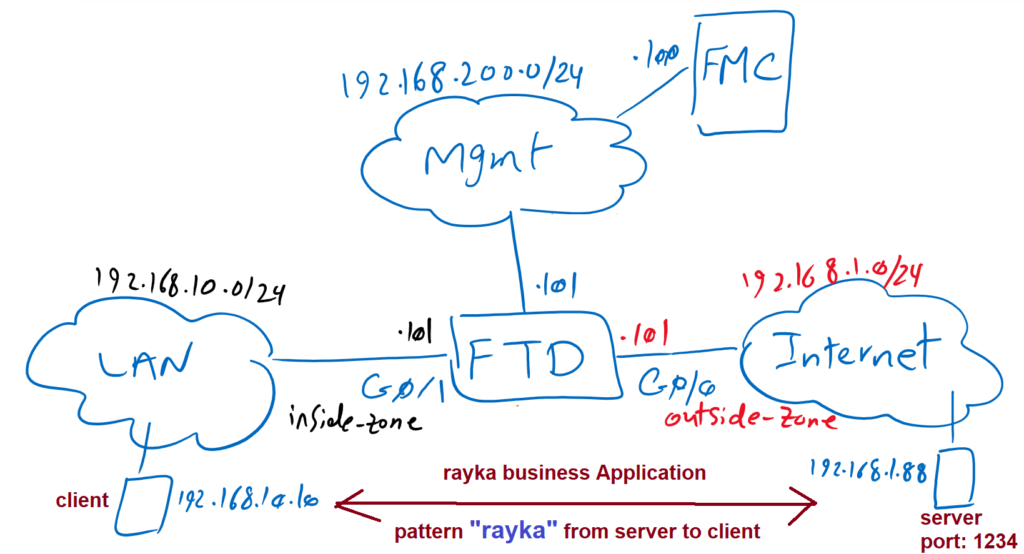
We have one business application running over TCP port 1234.we are going to write a custom application detector to detect traffic matching our business application. What is special about our application is the “rayka” pattern within the content that is transmitted from the server to the client over TCP port 1234. This is what we will search in our custom application detector signature.
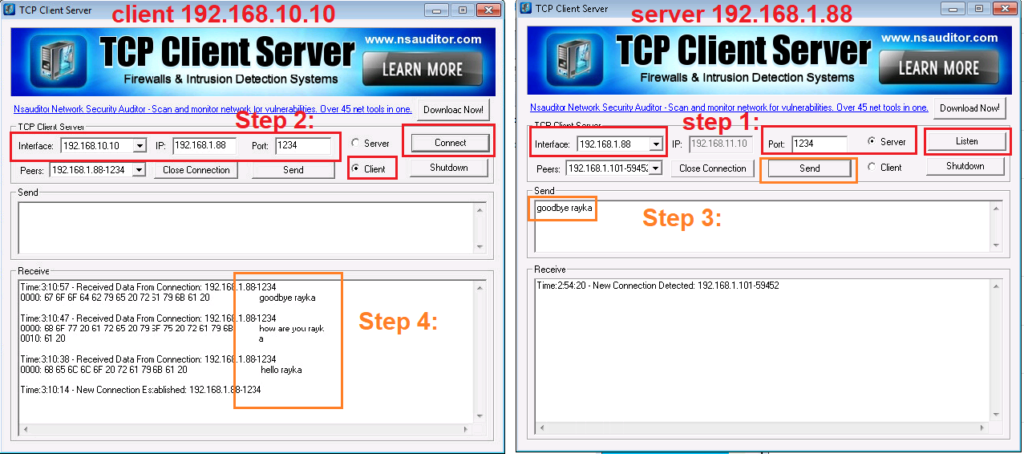
To ensure that our signature works correctly, we generate traffic between our test machines with IP address 192.168.10.10 as client and 192.168.1.88 as server listening on TCP port 1234.
Create Custom Application Detector
Simulate Custom Application
We will use the software “TCP Client Server” to simulate the traffic.
we will also use Wireshark software to capture sample of Rayka business application. With this sample traffic we can make sure if our signature works correctly.
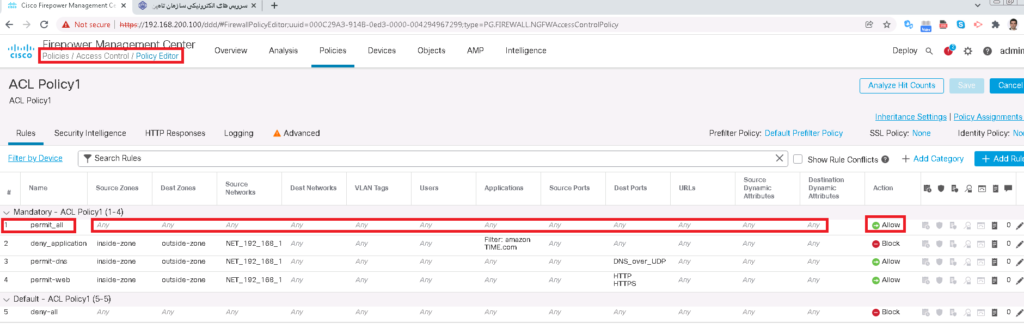
To simulate traffic, Let’s first add a rule at the top of access control to permit anything so we can simulate any traffic between inside and outside zone. We also enable logging to monitor simulated traffic.
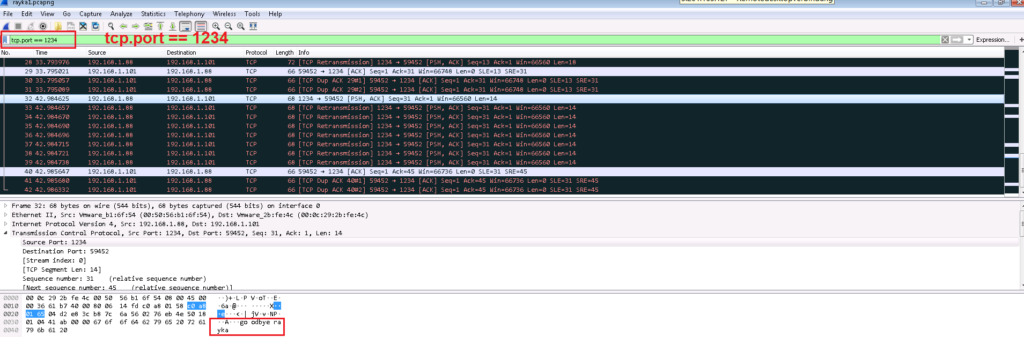
Before we generate any traffic, let’s open the Wireshark software to listen on “tcp.port == 1234” to capture any traffic going over TCP port 1234.
To generate sample Rayka business application traffic, First we open “TCP Client Server” software on the server side to listen on IP address 192.168.1.88 TCP port 1234.
Then we will open the same software on client machine to connect to 192.168.1.88 with TCP port 1234 from interface with IP address 192.168.10.10.
Then we write some text on the server side including the keyword “rayka” that will be sent to the client side. This text must be displayed on the client side when you click the “Send” button.
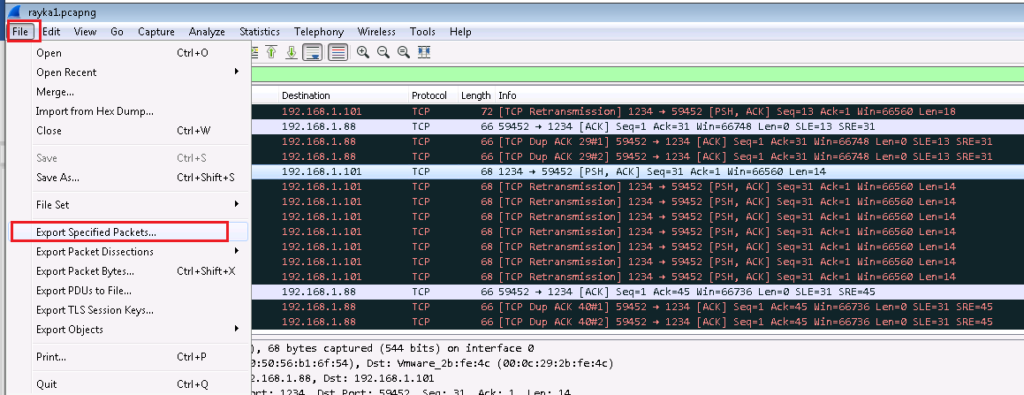
All traffic between client and server are captured in Wireshark. we save the captured traffic (“Export Specific Packets”) in a file. This file needs to be checked against our custom signature to ensure that the signature works properly.
Create Custom Application Detector Signature
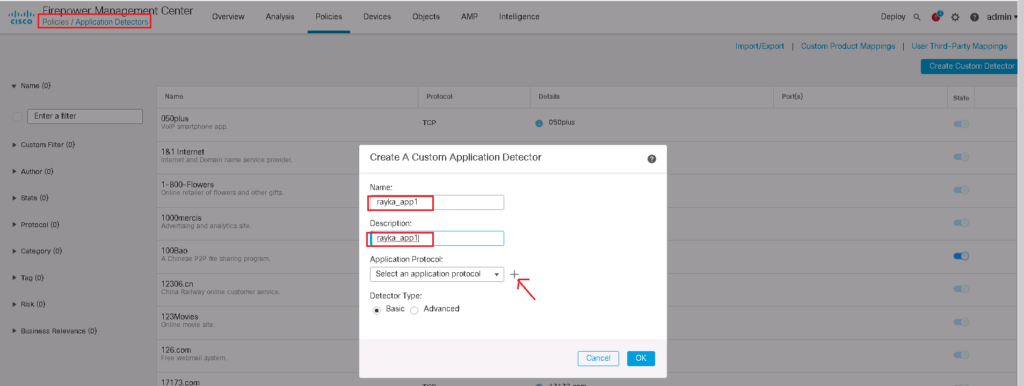
Now we can create our custom application detector signature using “Create Custom Detector” in:
Policies -> Application Detectors -> Create Custom DetectorGive a name and description for your application. Then click plus button to create a new basic application protocol.
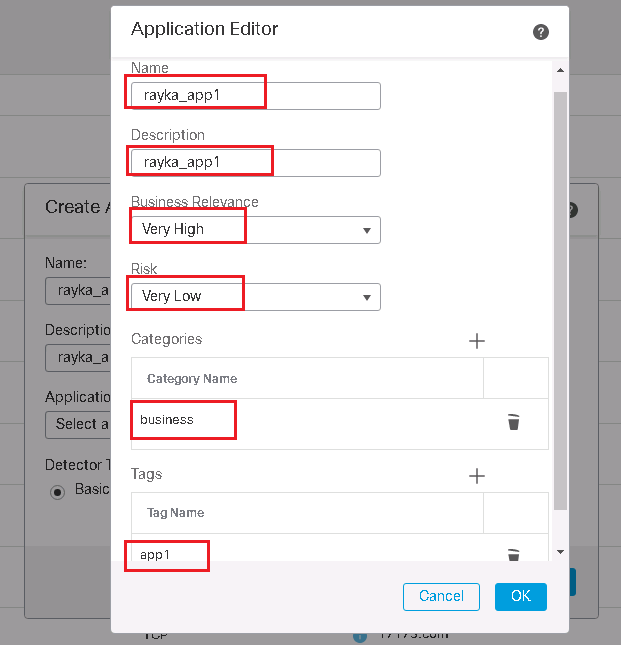
In the application protocol section, we also need to provide a name and description. then we have to indicate how business relevant the application is and how risky it is from a security point of view. It’s also a good idea to categorize the application. Then we can add as many tags that introduce the application.
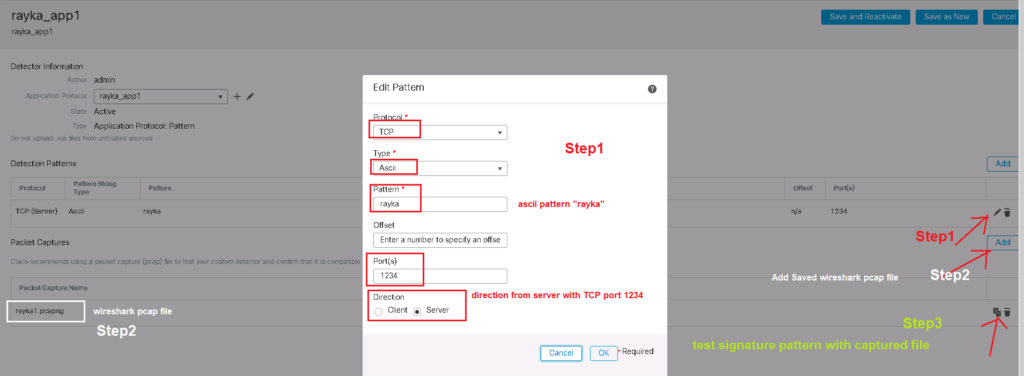
A new window for the new application will be open. This is the section that you have to specify your signature. Here you can add a sample traffic of the application to make sure that signature works correctly.
In our example, these are the parameters of the signature by which the traffic from Rayka app1 will be distinguished.
Any TCP traffic with direction from server to client with port number 1234 including ascii pattern “rayka”.
Then we add sample traffic captured by Wireshark.
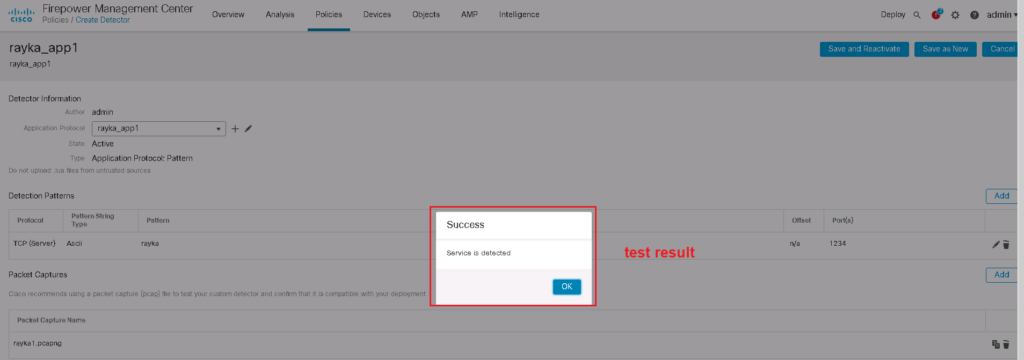
Then we test the signature with sample traffic. if it returns ok then it means that you have created a correct signature.
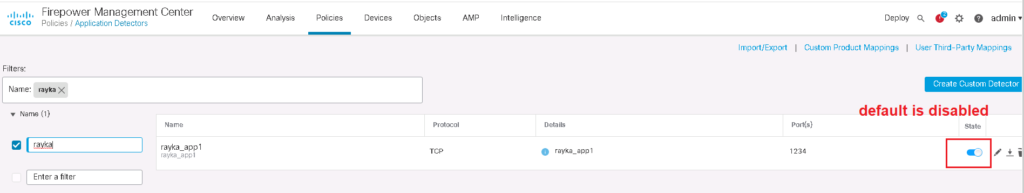
custom application detectors are dsabled by default. you have to enable it before using in access control rule.
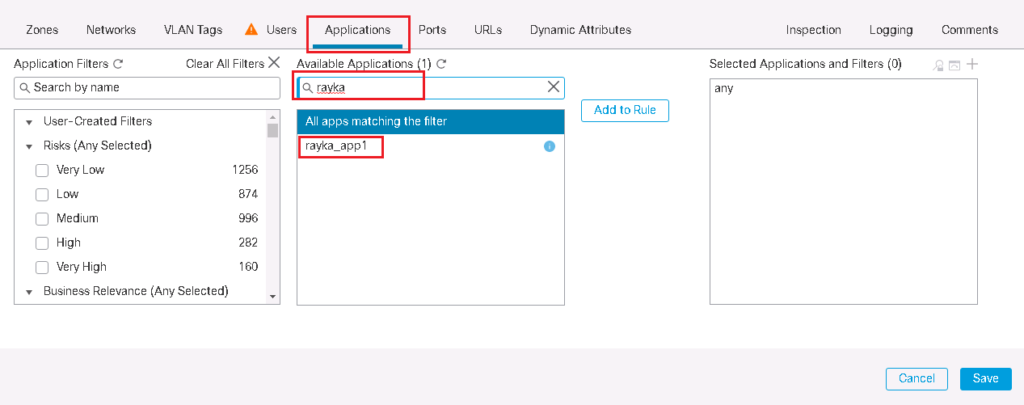
Now you are ready to add you custom detector in any access rule with searching your application name in application tab.