The VXLAN network is likely only part of your network. To have end-to-end connectivity with other parts of your network that are not based on VXLAN technology, you need VXLAN BGP EVPN external connectivity. For example, VXLAN is implemented in your data center and in order to have end-to-end connectivity to LAN, WAN and the Internet, these must be connected to your VXLAN network. The most common types of external connectivity are L2 and L3 connectivity, which we will discuss in this video.
VXLAN EVPN COnfiguration Example1
External connectivities are usually terminated in leaf switches and not in spine switches. This is because Leafs are the switches that terminate VXLAN tunnels and spine switches just forward VXLAN tunnel. If external connectivity is terminated in spine switches, our traffic should be terminated in spine switches on the VXLAN network before forwarding it to the external network. This is not impossible, but normally all external connections are made through leaf switches.
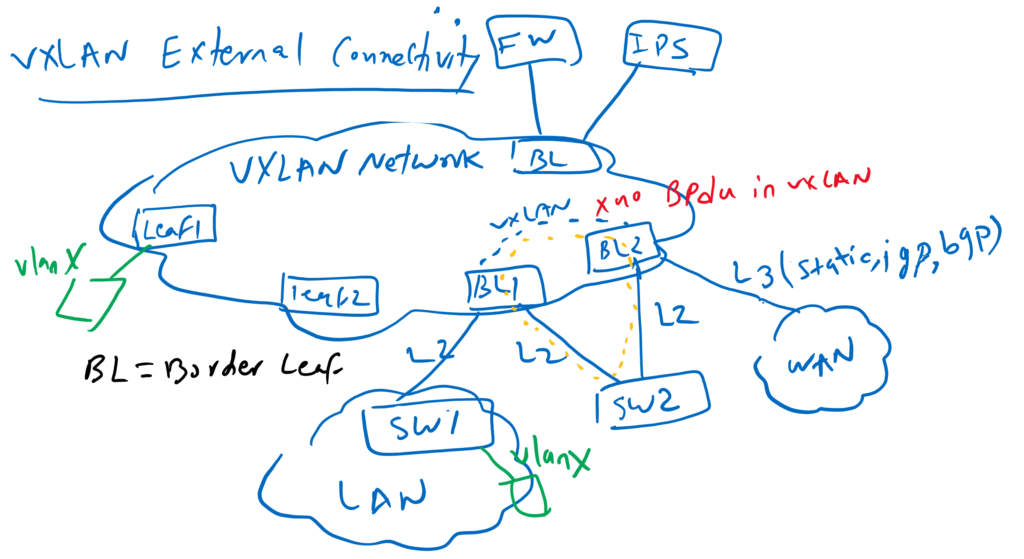
The leaf switches to which we connect our external VXLAN connectivity are called border leaf switches. There is no difference between normal leaf switch and border leaf switch. Only we call them differently to isolates internal traffic from external traffic.
Network services such as firewall and IPS are also usually connected to border leaf switches.
The two most common types of external connectivity are L2 connectivity and L3 connectivity.
L2 connectivity is typically established when you want to extend an L2 VLAN between a traditional Ethernet network and a VXLAN network. for example in our topology VLAN X is extended between Datacenter VXLAN network and LAN traditional ethernet network.
If you are connecting an external L2 network to your VXLAN network, make sure you create a loop-free topology like we did between BL1 and SW1. Otherwise Loop will be created. This is because STP BPDU is not forwarded to VXLAN network and Loop will not be detected through STP protocol.
In our topology, SW2 is dual-homed with two border leaf switches with L2 connectivity. There is a loop here, but it is not recognized by STP because the BPDU is not forwarded over the VXLAN network. There are three solutions to solve this problem. 1. Create only a loop-free L2 topology with your VXLAN network like what we have done between SW1 and BL1. 2. You can implement VPC between these two border leaf switches so that these two switches behave like one switch in the STP and LACP protocol. We will implement this solution in the next few videos. 3. We can use EVPN Route Type 4 which is designed for L2 multi-home connectivity. We will also implement this solution in the next few videos.
L3 external connectivity is normally used to connect your VXLAN network with internet and your enterprise WAN environment. This is done by configuring VRF lite in your Border Leaf Switch. Static routing, IGP routing protocol or BGP is used to exchange the routes between the external network and the VXLAN network. In this video we will implement a L3 external connectivity with VRF Lite and OSPF routing protocol.
following our previous topology, VXLAN EVPN with eBGP, In this video we implement the VXLAN EVPN L3 external connectivity.
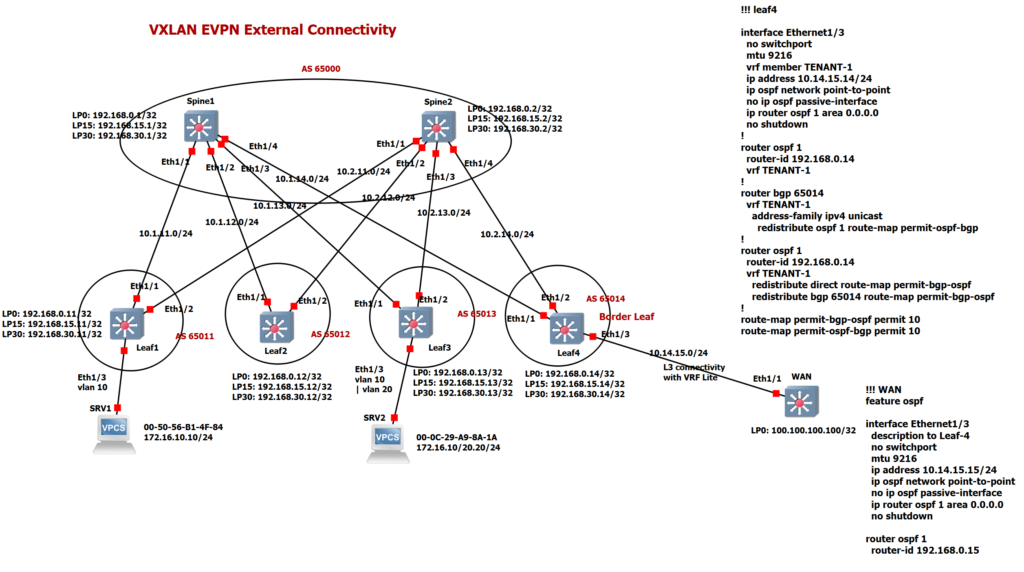
As you can see, the Leaf4 switch is considered as border leaf and is connected to the WAN router via the L3 connection with the IP address 10.14.15.x. We have also created a loopback interface in the WAN router with the address 100.100.100.100, which we will ping from the VXLAN network.
!!! leaf4
feature ospf
interface Ethernet1/3
no switchport
mtu 9216
vrf member TENANT-1
ip address 10.14.15.14/24
ip ospf network point-to-point
no ip ospf passive-interface
ip router ospf 1 area 0.0.0.0
no shutdown
router ospf 1
router-id 192.168.0.14
vrf TENANT-1
!!! WAN
feature ospf
interface Ethernet1/3
description to Leaf-4
no switchport
mtu 9216
ip address 10.14.15.15/24
ip ospf network point-to-point
no ip ospf passive-interface
ip router ospf 1 area 0.0.0.0
no shutdown
interface loopback 0
ip address 100.100.100.100/32
router ospf 1
router-id 192.168.0.15!!! leaf4
router bgp 65014
vrf TENANT-1
address-family ipv4 unicast
advertise l2vpn evpn
redistribute ospf 1 route-map permit-ospf-bgp
router ospf 1
router-id 192.168.0.14
vrf TENANT-1
redistribute direct route-map permit-bgp-ospf
redistribute bgp 65014 route-map permit-bgp-ospf
route-map permit-bgp-ospf permit 10
route-map permit-ospf-bgp permit 10
We have created OSPF routing protocol between these two devices Leaf4 and WAN router. This OSPF is different with the OSPF protocol which is already implemented as underlay protocol in VXLAN network.
Interface Eth1/3 is a member of VRF TENANT-1. New OSPF process is also implemented in VRF TENANT-1 in leaf4 switch. server1 and server2 are also members of VRF TENANT-1 in the VXLAN network.
As you can see, OSPF in VRF TENANT-1 is redistributed into BGP. BGP in VRF TENANT-1 is also redistributed into OSPF process 1 in the same VRF. Now we expect the IP address 100.100.100.100 to be advertised via BGP and imported into other leaf switches with the same VRF.
This is the first time that an external IP is advertised using the BGP EVPN address family. It is interesting to know that external routes are advertised via route type 5 in BGP EVPN. You can check it in other leaf switches with command “show bgp l2vpn evpn 100.100.100.100”.
leaf2(config-evpn-evi)# show bgp l2vpn evpn 100.100.100.100
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 192.168.15.14:3
BGP routing table entry for [5]:[0]:[0]:[32]:[100.100.100.100]/224, version 9414
Paths: (2 available, best #2)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not i
n HW
Multipath: eBGP
Path type: external, path is valid, not best reason: newer EBGP path, no label
ed nexthop
Gateway IP: 0.0.0.0
AS-Path: 65000 65014 , path sourced external to AS
192.168.30.14 (metric 81) from 192.168.15.2 (192.168.15.2)
Origin incomplete, MED not set, localpref 100, weight 0
Received label 30077
Extcommunity: RT:65012:30077 ENCAP:8 Router MAC:000c.2945.0180
OSPF RT:0.0.0.0:0:0
Advertised path-id 1
Path type: external, path is valid, is best path, no labeled nexthop
Imported to 1 destination(s)
Gateway IP: 0.0.0.0
AS-Path: 65000 65014 , path sourced external to AS
192.168.30.14 (metric 81) from 192.168.15.1 (192.168.15.1)
Origin incomplete, MED not set, localpref 100, weight 0
Received label 30077
Extcommunity: RT:65012:30077 ENCAP:8 Router MAC:000c.2945.0180
OSPF RT:0.0.0.0:0:0
Path-id 1 not advertised to any peer
As you can see, this route is advertised through Route Type 5 with L3 VNI 30077. just to repeat, In route Type 5, external prefix and L3 VNI is advertised.