Juniper SRX Source NAT Pool based and Proxy ARP is the discussion topic of this section.
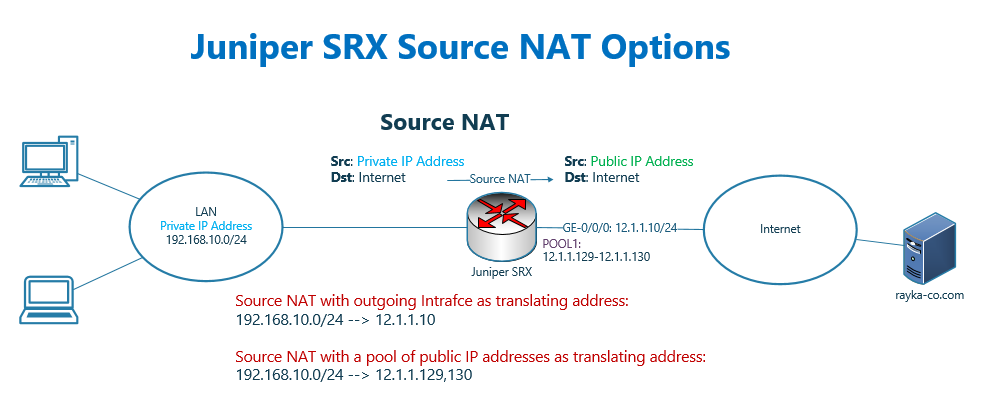
With Source NAT all users with private IP addresses can access to the internet.
With configuring a pool of public IP addresses, source private IP address of outgoing traffic is translated to IP addresses configured in the pool.
Juniper SRX Source NAT Pool based Fundamental
In the previous section, we have discussed different types of NAT and how they are used in the network.
We have also started the configuration of source NAT.
As you know, we have two options for source NAT. in the first option, source IP address of users is translated to IP address of outgoing interface which we have configured in the previous section.
In the second option, source IP address of users is translated to an IP address taken from pool of IP addresses which will be discussed in this section.
Juniper SRX Source NAT Topology
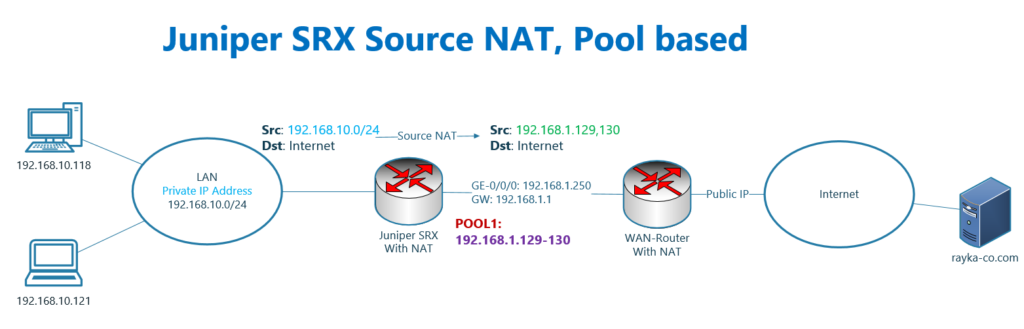
This is the topology that we have used also in the previous section to configure source NAT.
The difference is that, in this section we configure a pool of IP addresses, to be used for address translation.
As you can see in the topology, users inside the network with IP address subnet 192.168.10.0/24 are connected to the internet through two intervening devices.
The first device juniper SRX translate the IP address of users in the subnet 192.168.10.0/24 to 192.168.1.29-30, IP addresses configured in the pool.
The second device, WAN router, which is not under my control, translates the IP addresses in the 192.168.1.0/24 subnet to a specific public IP address.
Juniper SRX Pool based Source NAT Configuration
This is the configuration of pool based NAT.
set security nat source pool POOL1 address 192.168.1.129 to 192.168.1.130
set security nat source rule-set SOURCE-NAT from zone inside
set security nat source rule-set SOURCE-NAT to zone outside
set security nat source rule-set SOURCE-NAT rule NAT-POOL match source-address 192.168.10.0/24
set security nat source rule-set SOURCE-NAT rule NAT-POOL then source-nat pool POOL1
set security nat source address-persistentIn the first line we configure a NAT pool with the name of POOL1 including two IP addresses from 192.168.1.129 to 192.168.1.130.
Then we configure a NAT rule set with the name of SOURCE-NAT which is applied for the traffic from inside zone to the outside zone.
Inside the rule set, there is only one rule with the name of NAT-POOL.
It matches the traffic with the source of 192.168.10.0/24 which will be translated to the IP addresses configured in the NAT pool, POOL1.
In the last line, “address-persistent”, guarantees that source IP address of different traffic belonging to a specific user is always translated to the same IP address. In other words IP address translation is always persistent.
Now we can commit the configuration and test the result of the configuration by sending some traffic from inside zone to the outside zone.
But unlike our expectation, users inside the network cannot communicate with the internet.
Juniper SRX Source NAT Proxy ARP
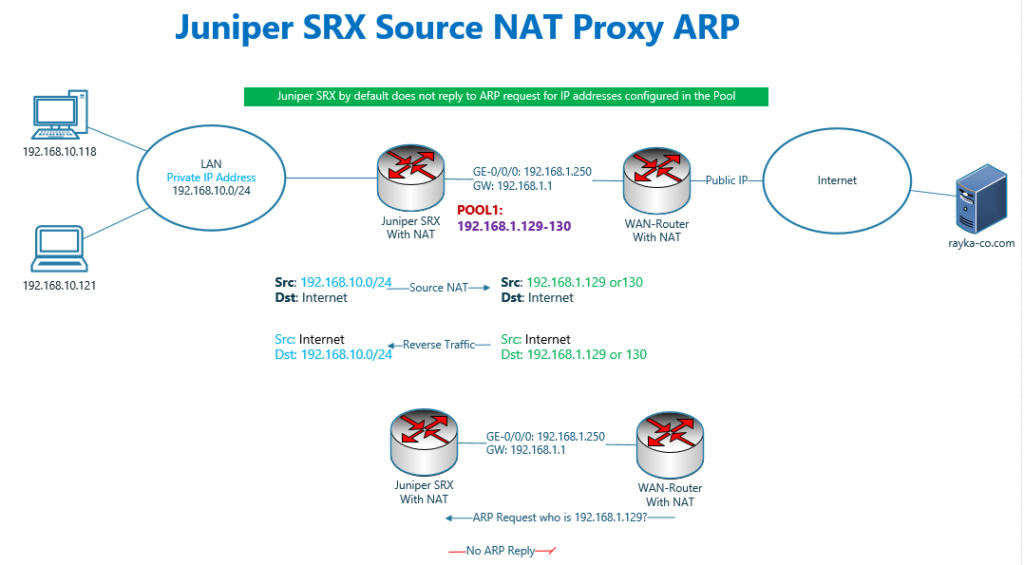
What is the problem?
As you know, the source address of outgoing traffic s translated to IP addresses configured in the pool, 192.168.1.129 and 192.168.1.130.
Therefore destination address of return traffic before reaching juniper SRX is the IP addresses configured in the Pool.
The problem is that, by default juniper SRX, unlike Cisco Firewalls, does not reply to ARP request to IP addresses configured in NAT pool. Therefore return traffic never reach juniper SRX.
In juniper SRX, Proxy ARP for IP addresses inside the pool must be explicitly configured.
This is the command that we enable proxy ARP for IP addresses inside the Pool.
set security nat proxy-arp interface ge-0/0/0.0 address 192.168.1.129 to 192.168.1.130After applying proxy ARP configuration, we send again different type of traffic and we expect that the communication with Internet is correctly established.
With the command “show security flow session”, we can check flow table to see how addresses are translated in the source NAT.
rayka# run show security flow session
Session ID: 8589978171, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 276, Valid
In: 192.168.10.118/34690 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 140,
Out: 216.239.38.120/80 --> 192.168.1.130/16368;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
Session ID: 8589978190, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 296, Valid
In: 192.168.10.121/1075 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 144,
Out: 216.239.38.120/80 --> 192.168.1.130/29022;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
...
As you can see, the source IP addresses inside the subnet 192.168.10.0/24 are always translated to one of the IP addresses configured in the pool.
We can also enable live monitoring of log file, with “monitor start” command.
rayka# run monitor start FIREWALL
*** FIREWALL ***
Aug 24 11:01:06 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.118/34690->216.239.38.120/80 0x0 junos-http 192.168.1.130/16368->216.239.38.120/80 0x0 source rule NAT-POOL N/A N/A 6 PERMIT-WEB inside outside 8589978171 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 24 11:01:28 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.121/1075->216.239.38.120/80 0x0 junos-http 192.168.1.130/29022->216.239.38.120/80 0x0 source rule NAT-POOL N/A N/A 6 PERMIT-WEB inside outside 8589978190 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
....
Aug 24 11:01:53 RT_FLOW: RT_FLOW_SESSION_CLOSE: session closed TCP FIN: 192.168.10.118/34690->216.239.38.120/80 0x0 junos-http 192.168.1.130/16368->216.239.38.120/80 0x0 source rule NAT-POOL N/A N/A 6 PERMIT-WEB inside outside 8589978171 4(180) 4(184) 47 UNKNOWN UNKNOWN N/A(N/A) ge-0/0/1.0 UNKNOWN N/A N/A -1 N/A NA 0 0.0.0.0/0->0.0.0.0/0 NA NA N/A N/A Off root 0 N/A N/A
Aug 24 11:02:15 RT_FLOW: RT_FLOW_SESSION_CLOSE: session closed TCP FIN: 192.168.10.121/1075->216.239.38.120/80 0x0 junos-http 192.168.1.130/29022->216.239.38.120/80 0x0 source rule NAT-POOL N/A N/A 6 PERMIT-WEB inside outside 8589978190 6(264) 5(224) 48 UNKNOWN UNKNOWN N/A(N/A) ge-0/0/1.0 UNKNOWN N/A N/A -1 N/A NA 0 0.0.0.0/0->0.0.0.0/0 NA NA N/A N/A Off root 0 N/A N/A
In the output of log files show, with which rule in the security policies and also NAT policies are matched and how IP addresses are translated.
Juniper SRX Source NAT “port no-translation” and “overflow-pool” options
Now I will discuss two options in the source NAT in juniper SRX, “port no-translation” and “overflow-pool”.
However I believe that they are not very applicable and you can ignore it, except that you are preparing yourself for the exam.
If you look at the output of session table or log file carefully, you will notice that in addition to source IP address, source port of traffic are also translated.
rayka# run show security flow session
Session ID: 8589978171, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 276, Valid
In: 192.168.10.118/34690 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 140,
Out: 216.239.38.120/80 --> 192.168.1.130/16368;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
Session ID: 8589978190, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 296, Valid
In: 192.168.10.121/1075 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 144,
Out: 216.239.38.120/80 --> 192.168.1.130/29022;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
...
With the help of port translation it becomes possible that many addresses inside the network can access internet with just one or a few public IP addresses.
Without port translation, the number of users with private IP addresses that can access internet are limited to the number of public IP addresses. I assume that you know the reason and I do not need to explain more about it.
With configuring the option “port no-translation”, in the NAT pool, we disable port translation and therefore the number of users accessing internet are limited to the number of public IP addresses.
Let’s limit at the same time the number of IP addresses in the pool just to one IP address.
delete security nat source pool POOL1 address 192.168.1.129 to 192.168.1.130
set security nat source pool POOL1 address 192.168.1.129
set security nat source pool POOL1 port no-translationThen we will try to access to the internet from two different sources. We expect that from the first source, it is possible to access the internet but from the second source it will not be possible.
Then in the output of session table, “show security flow session”, you can see that the source address of the first computer is translated but the port is not translated. And the source port of outgoing traffic and destination port of return traffic are the same.
rayka# run show security flow session
Session ID: 8590119643, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 294, Valid
In: 192.168.10.121/16029 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 144,
Out: 216.239.38.120/80 --> 192.168.1.129/16029;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
...Now with the option “overflow-pool interface” in the NAT pool, we can ask juniper when the IP address of pool is exhausted, then you have to translate the IP address of other users to the outgoing interface with port translation.
set security nat source pool POOL1 overflow-pool interfaceWith adding this option, now it is expected that both computers are able to connect to the internet.
Now with exploring the output of session table, we can see that the source IP address of the first computer, 192.168.10.118, is translated to the pool IP address, 192.168.1.129, and without port translation. But the source IP address of the second computer, 192.168.10.121, is translated to outgoing interface IP address, 192.168.1.250, and with port translation.
rayka# run show security flow session
Session ID: 8590122205, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 280, Valid
In: 192.168.10.118/34708 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 140,
Out: 216.239.38.120/80 --> 192.168.1.129/34708;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
Session ID: 8590122234, Policy name: PERMIT-WEB/8, State: Stand-alone, Timeout: 296, Valid
In: 192.168.10.121/16104 --> 216.239.38.120/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 3, Bytes: 144,
Out: 216.239.38.120/80 --> 192.168.1.250/12397;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 2, Bytes: 104,
...