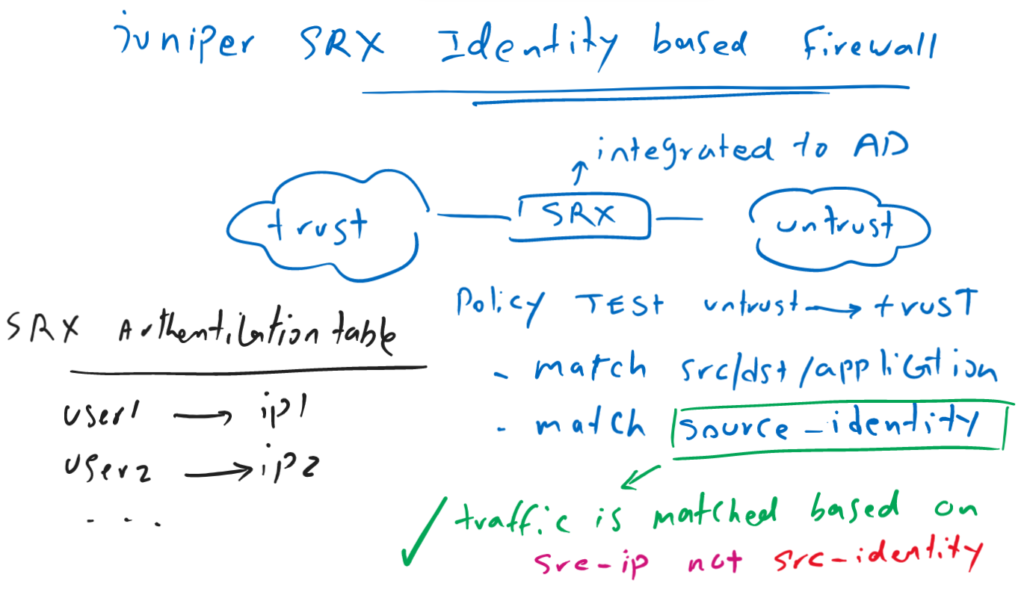
Juniper SRX Identity based Firewall provide the capability to control traffic based on user name in addition to source IP address that we use normally.
As we have discussed in the previous section, user information and corresponding IP address is retrieved using LDAP and the Active Directory event log database..
Juniper SRX Identity based Firewall Configuration
In this section we will learn how to control traffic based on username in Juniper SRX device.
But before that, make sure that you have studied previous section which show how to integrate Juniper SRX with active directory in order to retrieve user information and updated IP address of the user.
To configure a user firewall, we configure security policies as we have learned in the previous section. The only difference is that as a “match” condition we have the new option, “source-identity” which point to the user active in active directory.
What the firewall is actually doing behind the scenes is matching the traffic’s IP address, not the username. This is because the username doesn’t exist in the traffic itself.
But first it refers to Juniper SRX authentication table which include the IP address of active users. It retrieve the current IP address of the user. Then it match incoming traffic with the IP address retrieved from authentication table.
retrieve current active users in authentication table
Before starting the identity based firewall configuration, just to review the result of what we have configured in the previous section, let’s monitor juniper SRX authentication table.
With the command “show services user-identification authentication-table authentication-source active-directory”, we can retrieve the current active users in active directory and their corresponding IP address from authentication table.
rayka# run show services user-identification authentication-table authentication-source active-directory
Logical System: root-logical-system
Domain: rayka-co.local
Total entries: 2
Source IP Username groups(Ref by policy) state
192.168.1.99 majid Valid
192.168.1.250 administrator Valid
Domain: NULL
Total entries: 1
Source IP Username groups(Ref by policy) state
192.168.1.88 Invalid
[edit]
rayka#As you can see, there currently two active users “majid” and “administrator”. And their IP address is also displayed in the output of the command.
configure Juniper SRX identity based Firewall
To configure a sample user based or identity based firewall, I want to deny ping from outside to inside for all users except the user “majid”.
This is the policy that I have previously prepared.
I have three policies. In the first policy with the name of “PERMIT-ICMP-MAJID”, only the user majid is to send ICMP traffic from outside to the inside.
In the second policy, with the name of “DENY-ICMP”, ICMP traffic is rejected for all other IP addresses from outside to the inside zone.
In the third policy, with the name of “PERMIT-ALL”, all other traffic are permitted from outside to the inside.
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID match source-address any
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID match destination-address any
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID match application junos-icmp-all
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID match source-identity rayka-co.local\majid
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID then permit
set security policies from-zone outside to-zone inside policy PERMIT-ICMP-MAJID then log session-init
set security policies from-zone outside to-zone inside policy DENY-ICMP match source-address any
set security policies from-zone outside to-zone inside policy DENY-ICMP match destination-address any
set security policies from-zone outside to-zone inside policy DENY-ICMP match application junos-icmp-all
set security policies from-zone outside to-zone inside policy DENY-ICMP then reject
set security policies from-zone outside to-zone inside policy DENY-ICMP then log session-init
set security policies from-zone outside to-zone inside policy PERMIT-ALL match source-address any
set security policies from-zone outside to-zone inside policy PERMIT-ALL match destination-address any
set security policies from-zone outside to-zone inside policy PERMIT-ALL match application any
set security policies from-zone outside to-zone inside policy PERMIT-ALL then permit
set security policies from-zone outside to-zone inside policy PERMIT-ALL then log session-initNow I can copy and commit the configuration.
test and monitor Juniper SRX Identity based Firewall
To test the result of the configuration, I ping from two computers in the outside zone to a destination in inside zone.
The first computer with IP address “192.168.1.88” is not joined with the active directory. and the second computer with the IP address “192.168.1.99” is joined to the active directory.
At the same time I enable to monitor the result of log file “FIREWALL”, that we have configured in the section 8, “Monitoring and Troubleshooting Security Policies in Juniper SRX”.
with the command “monitor start FIREWALL” we can turn on live monitoring of the log file and with the command “monitor stop”, we can turn it off.
rayka# run monitor start FIREWALL
[edit]
rayka#
*** FIREWALL ***
Aug 19 16:42:46 RT_FLOW: RT_FLOW_SESSION_DENY: session denied 192.168.1.88/1->192.168.10.118/318 0x0 icmp 1(8) DENY-ICMP outside inside UNKNOWN UNKNOWN unknown-user(N/A) ge-0/0/0.0 No Rejected by policy 4295224685 N/A N/A -1 N/A N/A N/A N/A N/A
Aug 19 16:42:46 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.1.99/1->192.168.10.118/22 0x0 icmp 192.168.1.99/1->192.168.10.118/22 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP-MAJID outside inside 4295224686 majid(N/A) ge-0/0/0.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 19 16:42:46 RT_FLOW: RT_FLOW_SESSION_DENY: session denied 192.168.10.118/44177->194.225.150.25/123 0x0 junos-ntp 17(0) DENY-ALL inside outside NTP UNKNOWN N/A(N/A) ge-0/0/1.0 No Rejected by policy 4295224687 Infrastructure Networking 2 N/A N/A N/A N/A N/A
Aug 19 16:42:47 RT_FLOW: RT_FLOW_SESSION_DENY: session denied 192.168.1.88/1->192.168.10.118/319 0x0 icmp 1(8) DENY-ICMP outside inside UNKNOWN UNKNOWN unknown-user(N/A) ge-0/0/0.0 No Rejected by policy 4295224688 N/A N/A -1 N/A N/A N/A N/A N/A
Aug 19 16:42:47 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.1.99/1->192.168.10.118/23 0x0 icmp 192.168.1.99/1->192.168.10.118/23 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP-MAJID outside inside 4295224689 majid(N/A) ge-0/0/0.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
...
[edit]
rayka# The result of log fie shows that ICMP traffic with the source of “192.168.1.88” is matched with the policy “DENY-ICMP” and ICMP traffic with the source of “192.168.1.99” is matched with the policy, “PERMIT-ICMP-MAJID”.
Therefore SRX knows that the IP address of “192.168.1.99” is currently belongs to the user “majid”.