Juniper SRX Content Filtering is another UTM feature used to filter traffic based on file type (MIME type), file extension and also protocol commands.
It is also possible to filter cookie, ActiveX, java applet and some other content types.
In previous sections, we have discussed configured UTM antivirus and antispam features. This section is dedicated to content filtering feature.
Juniper SRX Content Filtering
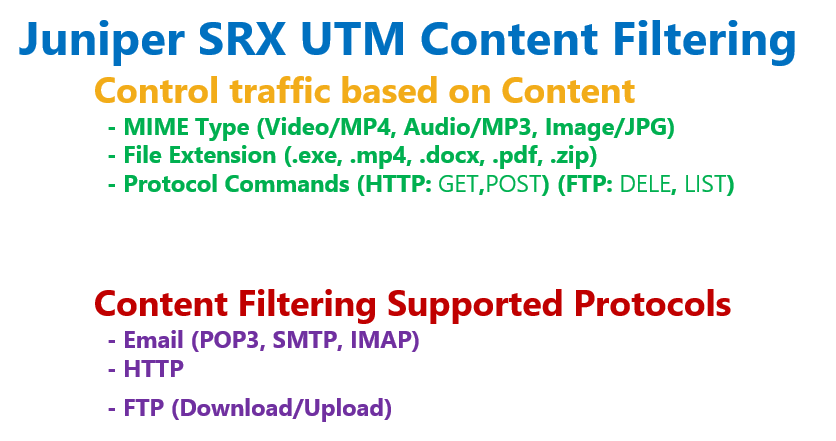
As we have mentioned several times, with content filtering it is possible to inspect web, FTP and email traffic to control or filter them based on the content type.
MIME type, file extension, and protocol commands are the main content that we can inspect and control.
By MIME type, it means mostly the type of the media. For example an MP4 video or MP3 audio or an image with jpeg type are some MIME type examples.
The meaning of the file extension is clear. .exe, .zip and .doc are some examples from file extension.
But by protocol command you can control the traffic based on the commands used in the application header.
For example in HTTP, get command is the most important command to browse or download the web content. Or in FTP, delete command is used to delete a file in a FTP server.
Juniper SRX Content Filtering Configuration
Juniper SRX Content Filtering Configuration Steps
The configuration of Content Filtering is very similar to antivirus and antispam.
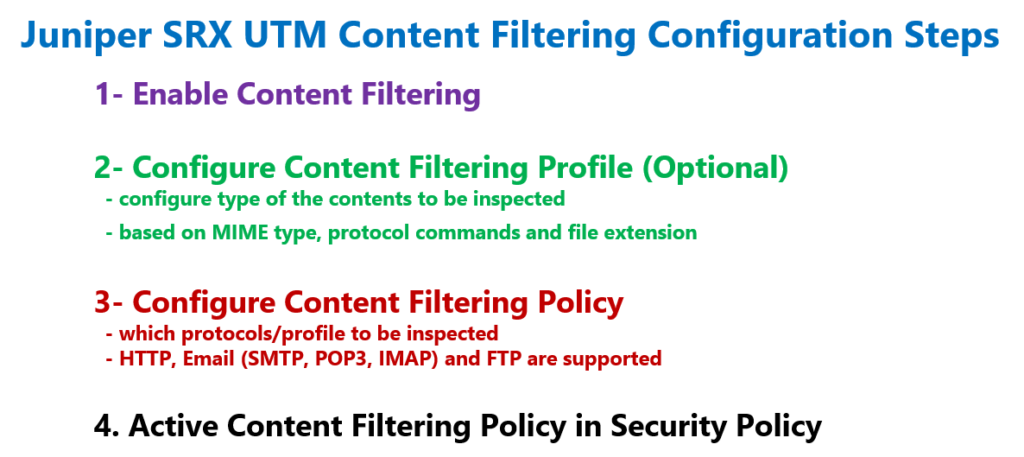
In the first step, we have to enable UTM content filtering feature.
In the second step, we configure content filtering profile. In the profile we configure the type of contents to be inspected.
For each content type, MIME type, protocol commands and file extension, a separate list of content types can be configured.
In the third step, we configure content filtering policy. In the policy we configure which protocols to be inspected. HTTP, Email and FTP protocols are supported.
For each protocol, we have to specify, the content filtering profile, configured earlier or the default content filtering profile.
In the last step, content filtering policy must be activated in a security policy.
Juniper SRX Content Filtering Configuration
Enable Content Filtering
To start the configuration, we enable UTM content filtering feature.
This feature unlike antivirus and antispam does not require any license.
With the command “set security utm default-configuration content-filtering type ?”, you have the option to enable or disable the content filtering.
With “local” keyword, you activate content filtering based on local policies.
[edit]
rayka@vSRX1# set security utm default-configuration content-filtering type ?
Possible completions:
local Content-filtering local
content-filtering-none
set security utm default-configuration content-filtering type local
Configure Content Filtering Profile
In the second step, we configure a content filtering profile.
In the profile, we specify which content to be inspected.
For each content type, MIME type, file extension and protocol commands, you can configure separate lists.
As an example, here we create four custom objects.
set security utm custom-objects filename-extension EXE_ZIP value [exe zip]
set security utm custom-objects protocol-command FTP_DEL value DELE
set security utm custom-objects mime-pattern QUICK_JPEG value [ video/quicktime image/jpeg ]
set security utm custom-objects mime-pattern MP4 value video/mp4
[edit]
rayka@vSRX1# set security utm feature-profile content-filtering profile CF_PROFILE ?
Possible completions:
<[Enter]> Execute this command
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
block-command Block command list
> block-content-type Content-filtering feature block content type
block-extension Block extension list
> block-mime Content-filtering feature block MIME
> notification-options Notification options
permit-command Permit command list
| Pipe through a command
set security utm feature-profile content-filtering profile CF_PROFILE block-extension EXE_ZIP
set security utm feature-profile content-filtering profile CF_PROFILE block-command FTP_DEL
set security utm feature-profile content-filtering profile CF_PROFILE block-mime list QUICK_JPEG
set security utm feature-profile content-filtering profile CF_PROFILE block-mime exception MP4 The first is based on file extension. .exe and .zip extensions are in the list.
The second is based on protocol commands. FTP delete command is the only protocol command in the list.
The third list is based on MIME type, includes video QuickTime and image jpeg files.
The last list is also based on MIME type, include video MP4 file.
Then we create a profile with the name of “CF_PROFILE”, which inspect and block the first three list but permit the file type including in the fourth list.
In the content filtering, whitelist is created using “exception” keyword.
Configure Content Filtering Policy
In the third step, we configure content filtering policy.
In content filtering we specify which protocols to be inspected. In each protocol, we have to specify which profile should be used for the inspection.
Here I create a content filtering policy with the name of “CF_POLICY”, which inspect FTP download and upload traffic to check contents configured in the “CF_PROFILE” profile.
set security utm utm-policy CF_POLICY content-filtering ftp download-profile CF_PROFILE
set security utm utm-policy CF_POLICY content-filtering ftp upload-profile CF_PROFILEApply Content Filtering Policy in Security Policy
In the last step, we have to apply the content filtering policy in one security policy.
From untrust zone to trust zone, there is a default default-permit rule that we configured in the previous sections.
At the end of “then” command, we add content filtering policy “CF_POLICY” in default-permit security policy.
set security policies from-zone untrust to-zone trust policy default-permit match source-address any
set security policies from-zone untrust to-zone trust policy default-permit match destination-address any
set security policies from-zone untrust to-zone trust policy default-permit match application any
set security policies from-zone untrust to-zone trust policy default-permit then permit
set security policies from-zone untrust to-zone trust policy default-permit then permit application-services utm-policy CF_POLICYAfter committing, we can check it with the command, “show configuration security policies from-zone untrust to-zone trust policy default-permit | display set”
[edit]
rayka@vSRX1# run show configuration security policies from-zone untrust to-zone trust | display set
set security policies from-zone untrust to-zone trust policy default-permit match source-address any
set security policies from-zone untrust to-zone trust policy default-permit match destination-address any
set security policies from-zone untrust to-zone trust policy default-permit match application any
set security policies from-zone untrust to-zone trust policy default-permit then permit application-services utm-policy CF_POLICYThese are all the configuration that we need to configure to start using content filtering feature in juniper SRX device.
Content Filtering Monitoring and Troubleshooting
To make sure that content filtering feature is correctly configured and it is inspecting the configured contents, there is one main monitoring commands.
With the command “show security utm content-filtering statistics”, you can make sure that content filtering feature is activated and how many contents of each type are filtered.
[edit]
rayka@vSRX1# run show security utm content-filtering statistics
Content-filtering-statistic: Blocked
Base on command list: 0
Base on mime list: 0
Base on extension list: 0
ActiveX plugin: 0
Java applet: 0
EXE files: 0
ZIP files: 0
HTTP cookie: 0