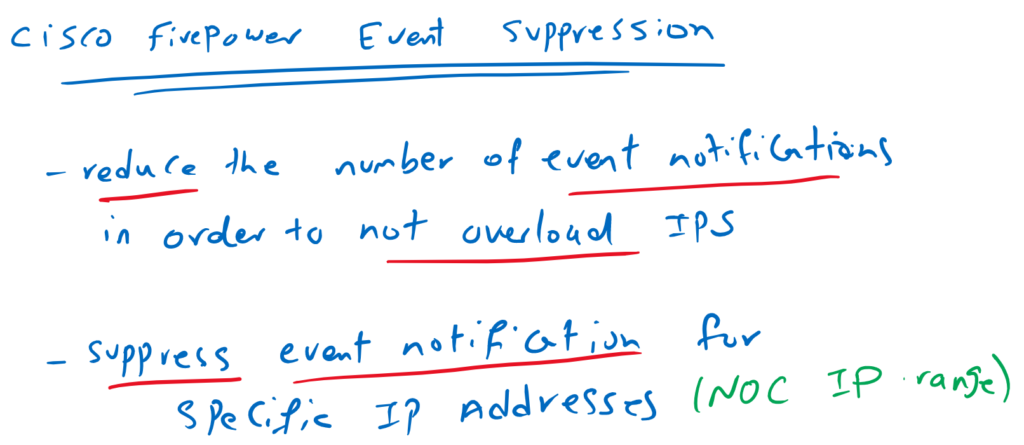
Cisco Firepower Event Suppression is a feature to reduce or suppress intrusion event notification based on some thresholds or IP address range.
Cisco Firepower Event Suppression Applications
A firepower can be overloaded by generating too many event notifications when an attacker triggers a particular signature (IPS rule) at a high rate. so it is necessary to control the rate of event notifications.
Sometimes it is also necessary to exempt some IP addresses from triggering an IPS signature event notification.
For example, NOC IP addresses are allowed to scan the network to discover vulnerabilities, but users outside of the NOC or the company are not allowed to scan our network. so the IP address range of NOC department must be excepte from generating event notification.
Cisco Firepower Event threshold configuration
Firepower event notifications Topology Overview
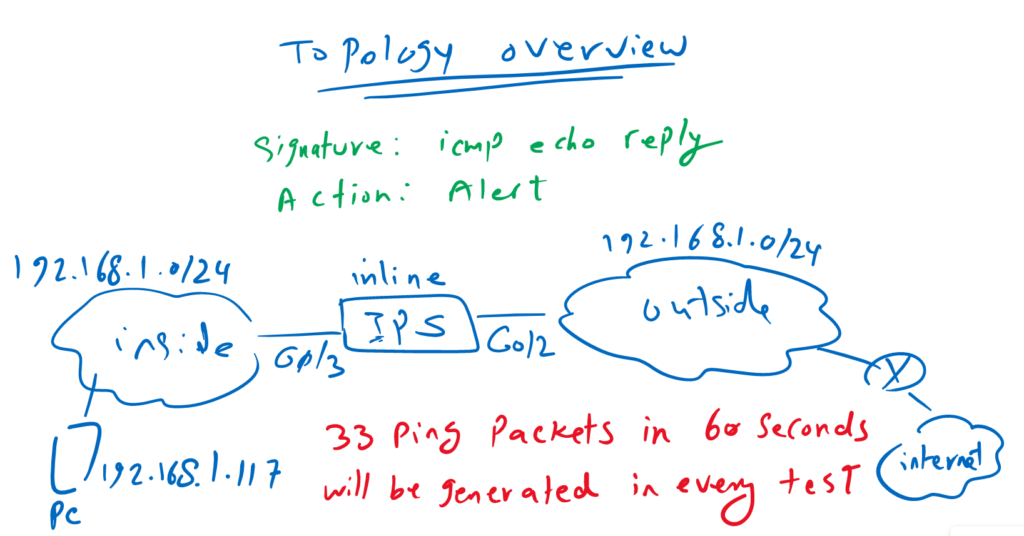
To configure Cisco Firepower Event Suppression, let’s first review the topology.
IPS-only device is connecting our inside network to outside network and internet.
There is a computer with IP address 192.168.1.117 behind IPS that generates 33 packets in a 60 second time interval to see how many event notifications are generated for each of test scenarios.
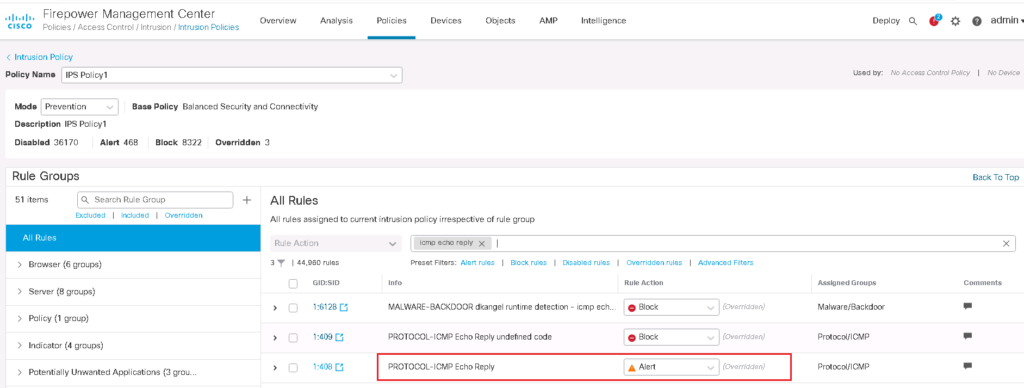
enable Alert action for “ICMP ECHO REPLY” signature
To implement our scenarios, we need to ensure that the “icmp Echo Reply” signature is active and generate an event notification for “icmp Echo Reply” packets forwarded through the IPS device.
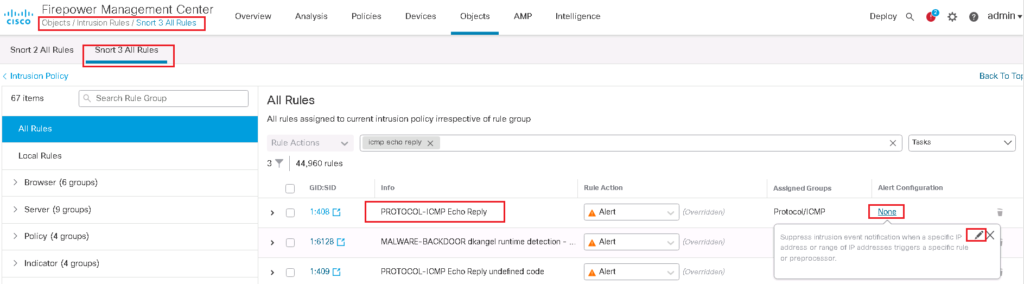
Policies -> Access Control -> Intrusion -> IPS Policy1 -> Snort 3 Version
scenario1: Cisco Firepower Event threshold configuration: LIMIT parameter
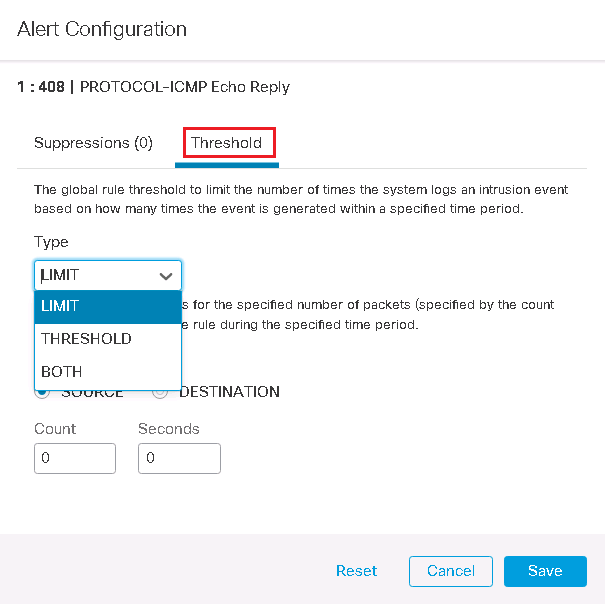
To control the number of event notifications, we have “Alert Configuration” option beside each IPS rule. By default it is not configured and the default value is None.
To configure it, just click over None and then Edit option.
There are two options to configure, suppression and threshold. For the first three scenarios, we configure the threshold section.
In threshold tab, there are three options to configure: LIMIT, THRESHOLD and BOTH.
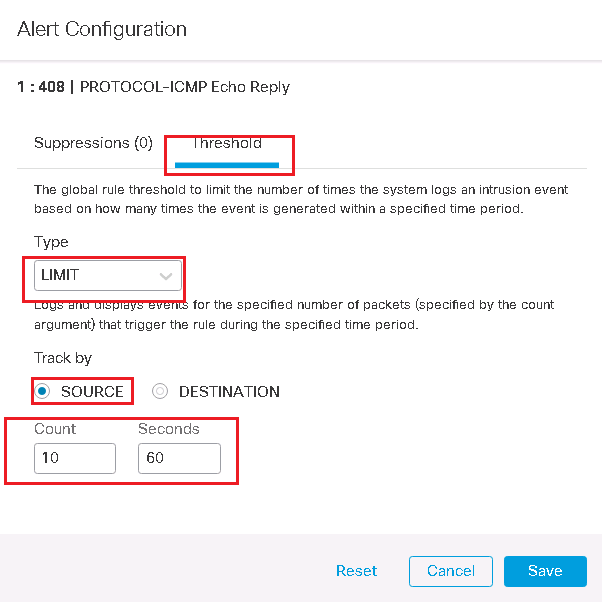
In the first scenario We configure LIMIT parameter in threshold tab.
There are two parameters in LIMIT section to configure. Count and Seconds.
To understand it. I explain it through an example.
suppose we configure the value of count to 10 and seconds to 60 seconds:
LIMIT: count=10, seconds: 60
It means, generate no more than 10 event in each 60 seconds time interval for a specific source or destination address which trigger this specific IPS rule.
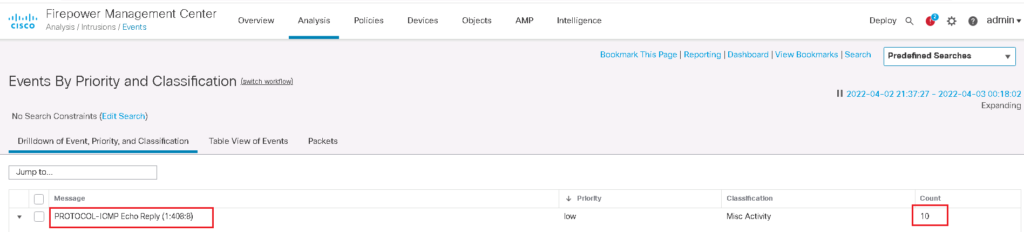
To test it, For each scenario, we generate 33 ping packet from inside to outside inside the interval of 60 seconds. Then we will check how many event notifications are generated.
Windows Command: ping 8.8.8.8 -n 33
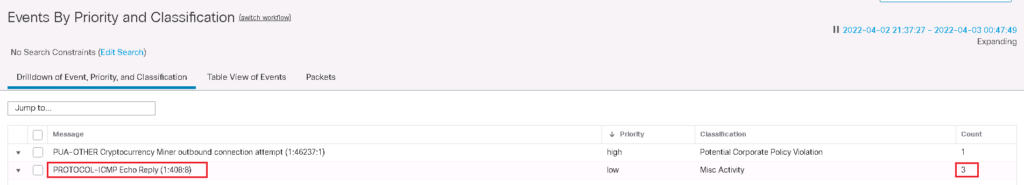
As expected, only 10 events are generated even though 33 icmp echo reply packets are received in the 60 second interval.
scenario2: Cisco Firepower Event threshold configuration: threshold parameter
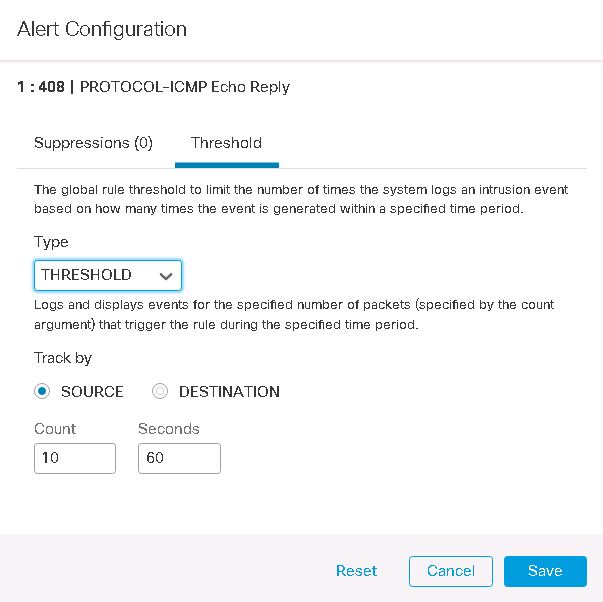
In the second scenario We configure threshold parameter in threshold tab.
We configure the value of Count and Seconds to 10 and 60 seconds as previous example.
THRESHOLD: count=10, seconds: 60
It means, generate event only once for every 10 packets that trigger the rule in the 60 second time interval.
after generating event, both counter and timer are reset to zero. that means if 33 packet trigger the rule in 60 seconds, then 3 events will be generated.
Before testing, I delete previous Icmp echo reply intrusion events so that we can more easily analyse the number of intrusion events.
Now I generate 33 ping packet by “ping 8.8.8.8 -n 33” command.
As we expect, only 3 event notification are generated.
scenario3: Cisco Firepower Event threshold configuration: BOTH parameter
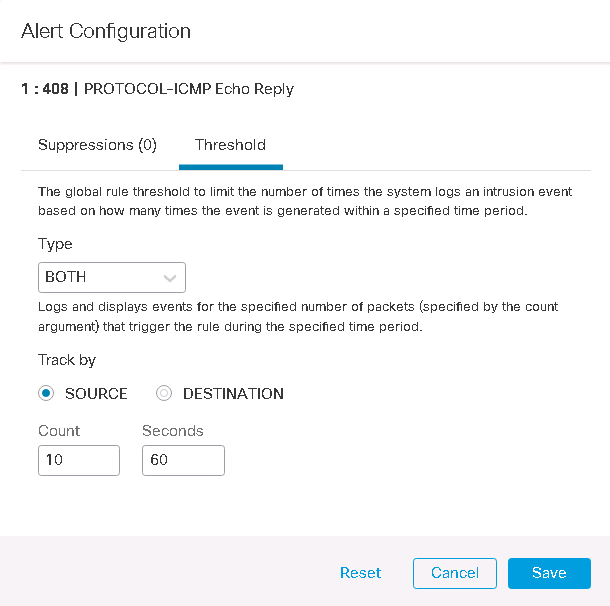
In the third scenario We configure BOTH parameter in threshold tab.
We configure the value of Count and Seconds to 10 and 60 seconds as previous examples.
BOTH: count=10, seconds: 60
It means, generate event only once when at least 10 packets trigger the rule in the 60 second time interval.
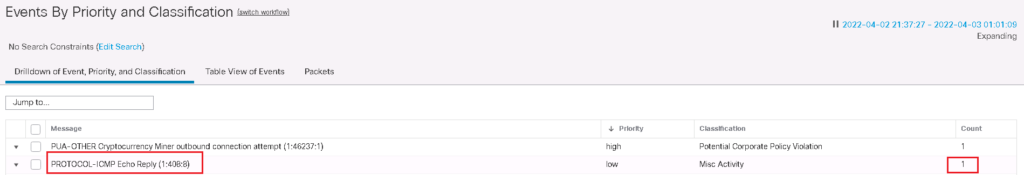
after generating event, the counter and the timer are not reset to zero. that means if 33 packet trigger the rule in 60 seconds, then only 1 event will be generated.
Before testing, I delete previous icmp echo reply intrusion events so that we can more easily analyse the number of intrusion events.
Now I generate 33 ping packet by “ping 8.8.8.8 -n 33” command.
As we expect, only 1 event notification are generated.
Cisco Firepower Event Suppression configuration
In the first three scenarios, I have reduced the number of event notification by configuring threshold parameters.
But sometime we want to suppress event notification for specific IP addresses.
For example, NOC users are allowed to scan the network to extract vulnerabilities. So we expect no event to be generated when NOC’s IP address range scans the network. But scanning from any other IP address must be notified.
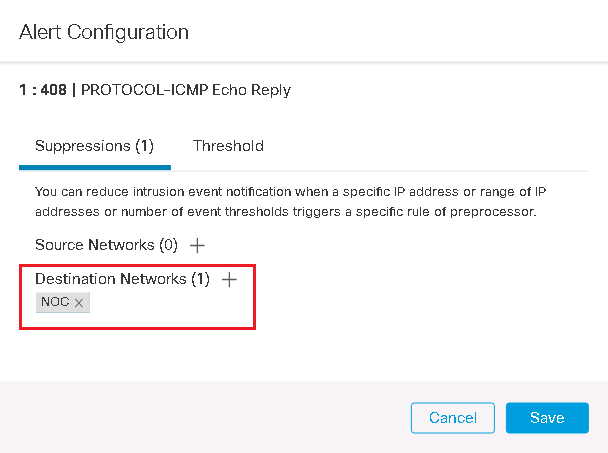
To exclude an IP address or a range of IP addresses in the alarm configuration, we need to configure the IP address on the Suppression tab.
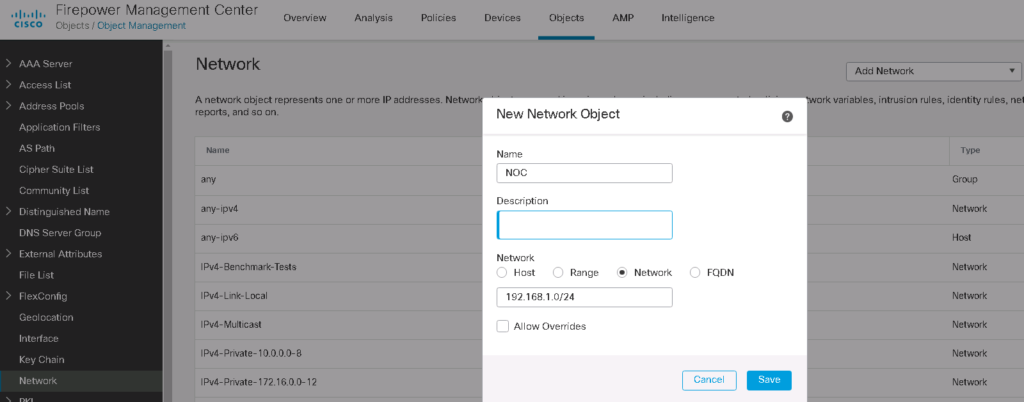
We are allowed to configure the IP address range only through network object. Therefore at first we configure and network object for NOC users.
Then we configure NOC IP address range on the Suppressions tab to be exempt from alarm notification.
Note that in ICMP echo reply packets, NOC users’ IP address are specified as destination IP address and not the source IP address. Therefore, we configure that all ICMP echo reply traffic with the NOC IP address range as the destination address must be excluded from event notification.
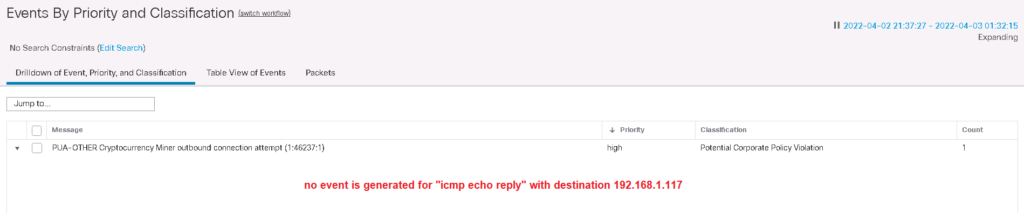
Now we expect that no event will be generated when we ping from 192.168.1.117 to 8.8.8.8.
Before testing, I delete previous icmp echo reply intrusion events so that we can more easily analyse the number of intrusion events.
Now I generate 33 ping packet by “ping 8.8.8.8 -n 33” command.
As we expect, no event notification are generated.