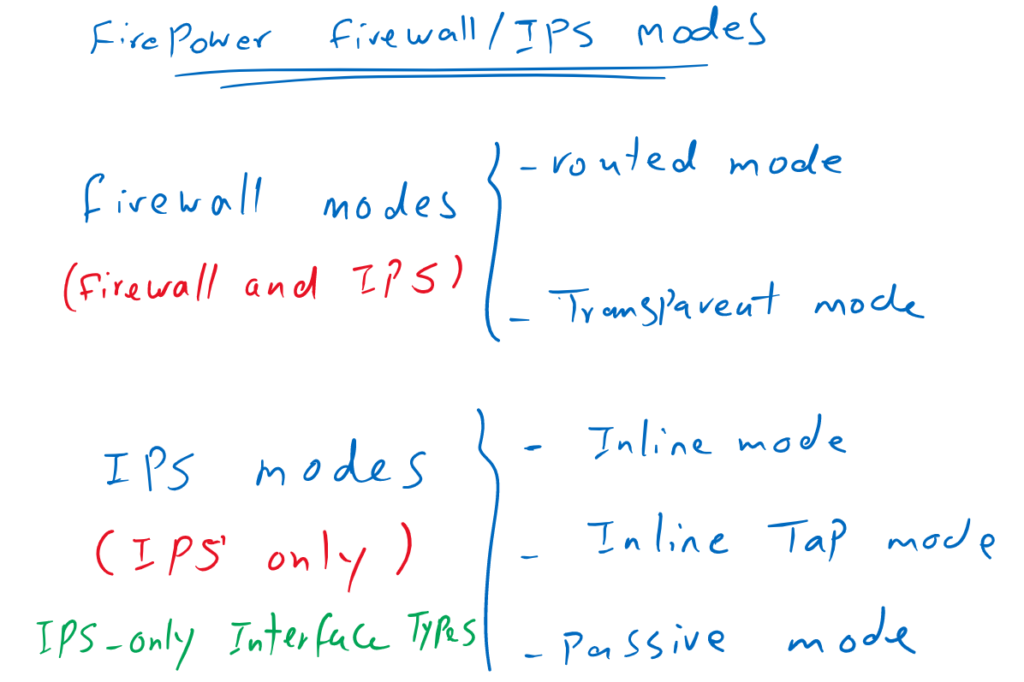
Cisco Firepower deployment modes are the methods to insert a Firepower into the network as a Firewall/IPS device or as a IPS-only device. In Firewall/IPS mode, you have the option to choose routed or transparent mode and as a IPS-only device you can choose between inline and passive mode.
We discussed routing mode and transparent mode in the previous sections. In this section, we will discuss IPS-only inline and passive modes.
Cisco Firepower Firewall and IPS Deployment Modes
routed/transparent mode as firewall and inline/passive mode as IPS-only device
What we have implemented so far is firepower firewall routing mode and transport mode, in which not only firewall services are available but you can also implement IPS services as we saw in the previous section.
Just to review, in routed mode, the firewall does routing. So we need to give IP addresses to firewall interfaces and do static or dynamic routing like any other router.
In transparent mode, firepower acts like a switch. It’s easier to add a switch or transparent firewall in an existing network because it doesn’t change any IP addressing or routing infrastructure.
But sometimes you use a separate firewall and you want to use firepower as an IPS-only service. In this condition we have three main options to use. Inline mode, inline tap mode or passive mode.
Cisco Firepower Deployment Mode: IPS-only Inline Mode
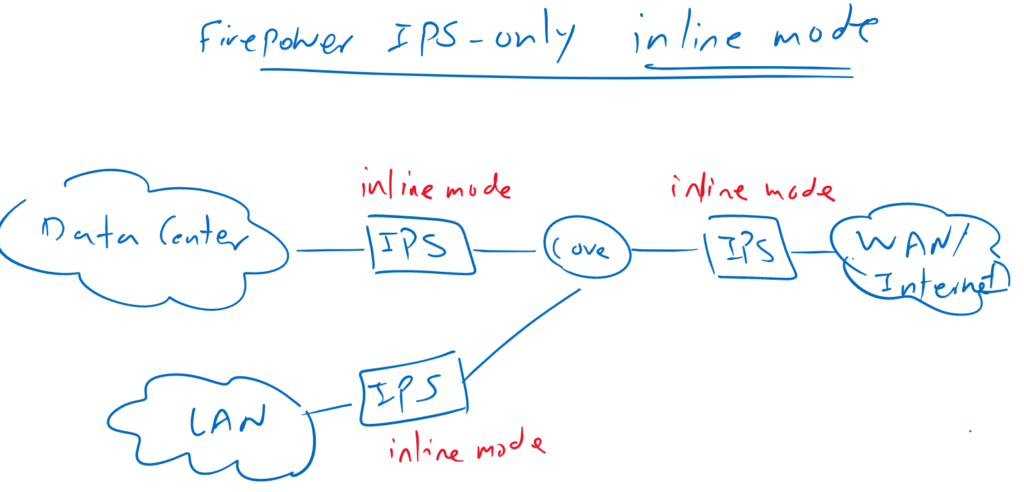
In inline mode, Firepower is physically inserted into the path, so all traffic is forwarded through the Firepower IPS device. For example, we can insert the firepower physically between the data center and the enterprise core, or between the enterprise core and the WAN edge.
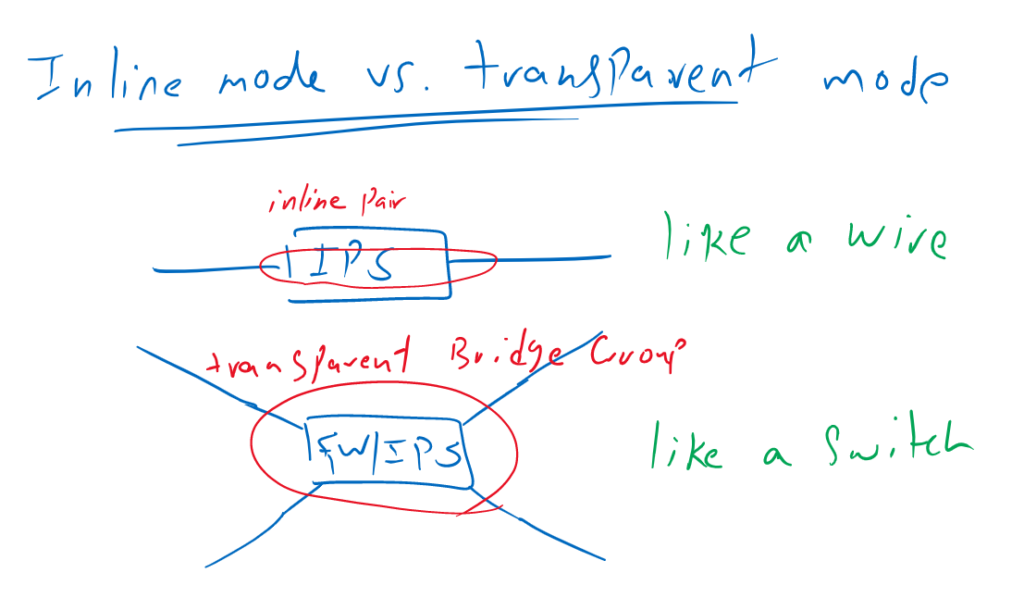
Firepower Inline mode versus Transparent mode
In inline mode, there can be added only two interfaces in each inline pair. What is received in each interface, will be forwarded to other interface after inspection, without MAC switching or IP routing. It behaves like a wire with an inspection module in between.
Inline mode can be used when we are using a Firepower as an IPS-only device in which most firewall services are not working.
Inline mode differs from transparent mode, in which multiple interfaces can be added in each bridge group and each bridge group behaves like an isolated switch.
Transparent mode is used as a mode when we use Firepower as a firewall service, which can also be used as an IPS device at the same time.
Cisco Firepower Deployment Mode: IPS-only Inline Tap Mode
Firepower in Inline tap mode will be deployed exactly as inline mode. the difference is that in inline tap mode, traffic itself will not be inspected but just a copy of traffic is inspected. Therefore in inline tap mode, it is not possible to drop intrusions and they will be just alerted.
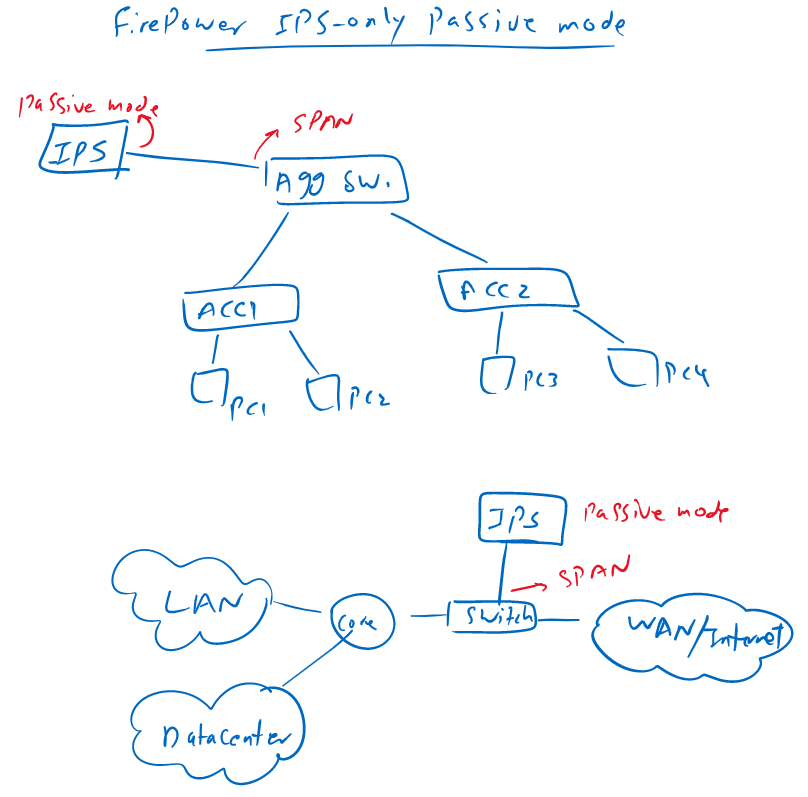
Cisco Firepower Deployment Mode: IPS-only Passive Mode
In passive mode, firepower will not be inserted physically in path.
Actually sometimes, it is not possible to insert an IPS device physically in the path to inspect all traffic. For example in the LAN, it is not possible to insert an IPS so it can inspect all LAN traffic.
In passive mode, copy of traffic will be sent to the IPS with the help of SPAN/RSPAN/ERSPAN technology.
Therefore, in passive mode like inline tap mode, only copy of traffic are inspected, so it is not possible to drop a traffic if it is intrusion, and only an alert is given.
Although there are some methods to block intruders in inline tap mode and passive mode, they are not real-time. For example, they can block intruders’ source IP by inserting an access rule in a firewall.
Passive mode is also used when we want just to monitor what is coming in our network with inserting an IPS in passive mode in edge of the network.
Firepower IPS inline mode and inline tap mode configuration
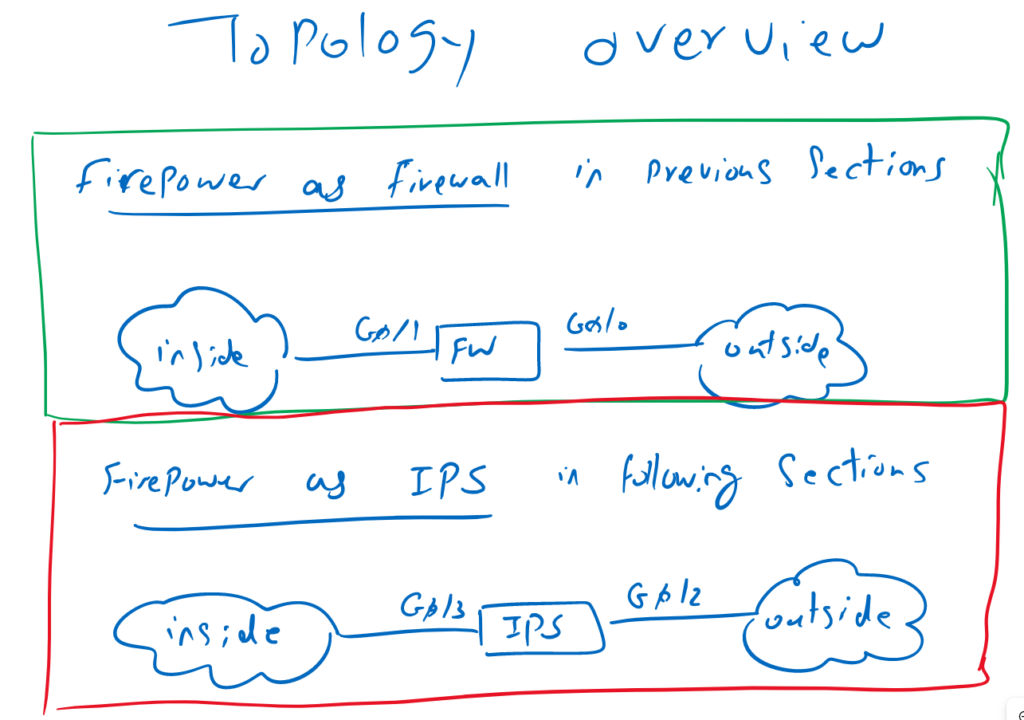
Firepower Firewall and IPS Topology Review
So far we have used Firepower as Firewall, in which G0/0 was connected to outside interface and G0/1 was connected to inside network.
From now own we will use firepower as IPS-only device with G0/2 connected to outside interface and G0/3 connected to inside interface.
Cisco Firepower IPS Inline mode configuration
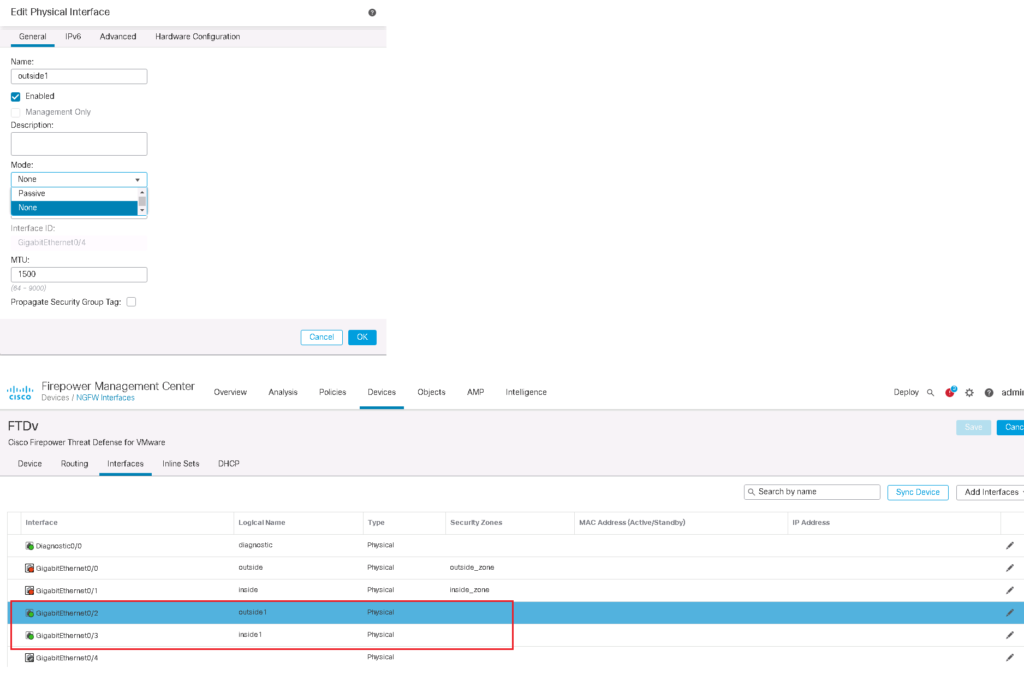
First we configure and enable G0/2 and G0/3 interfaces as outside1 and inside1 interface.
In interface configuration, there is an option to change interface mode to passive mode in which is ready to receive the copy of traffic and inspect the receiving traffic. The copy of traffic can be sent to this interface with any methods like SPAN/RSPAN switch feature.
Then we configure an inline pair and add these two interfaces into the inline pair.
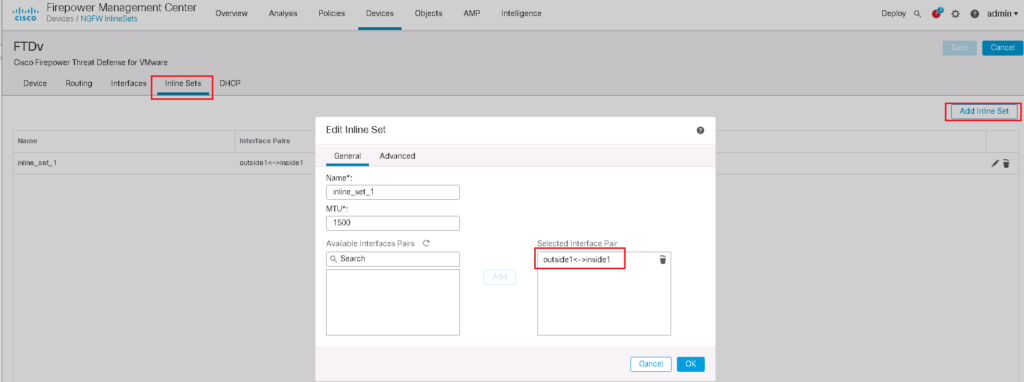
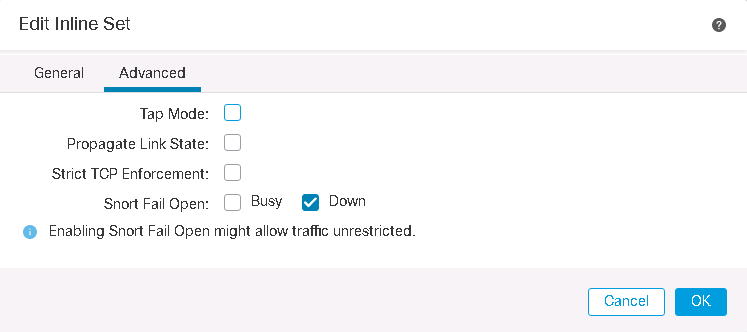
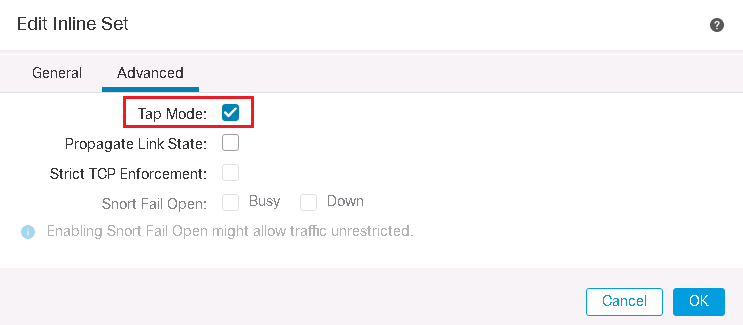
in Advanced Tab, we have some options to configure:
- Tap mode: with enabling this option, the copy of traffic will be inspected. I will implement it in the next section
- Propagate Link State: automatically brings down the second interface in the inline interface pair when one of the interfaces goes down.
- Strict TCP Enforcement: it is a security feature and blocks connections where three-way handshake are not completed
- Snort Fail Open: when it is selected, traffic will be pass without inspection when the Snort process is busy or down.
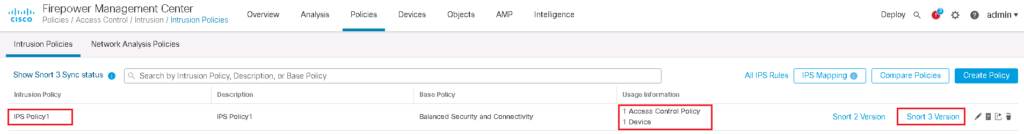
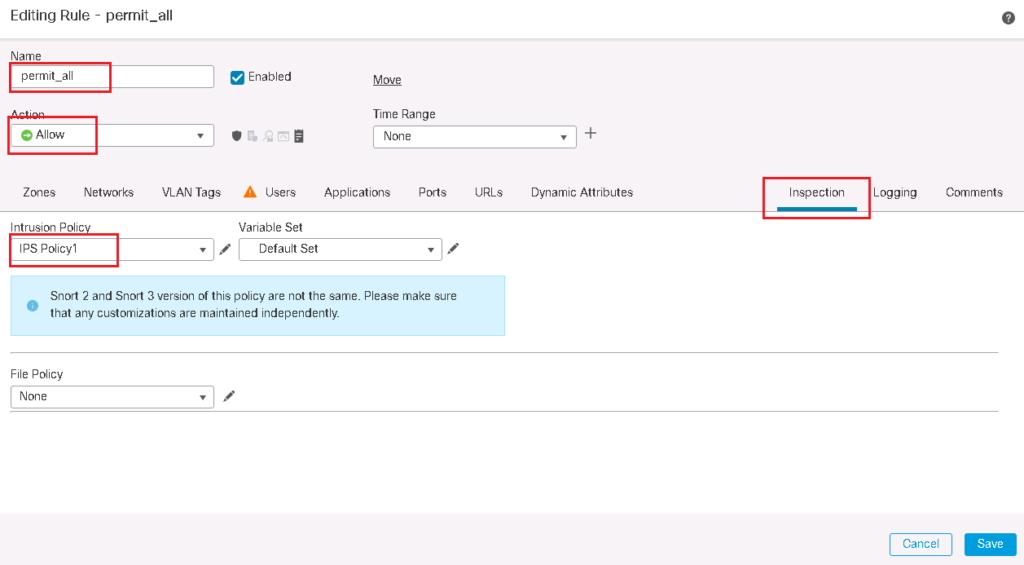
Then IPS policy must be configured and be applied to the access control rule.
We will use the IPS policy that we have configured in previous section, IPS Policy1.
In this policy we have configured to Block “ICMP ECHO REPLY” traffic which is implemented in previous section.
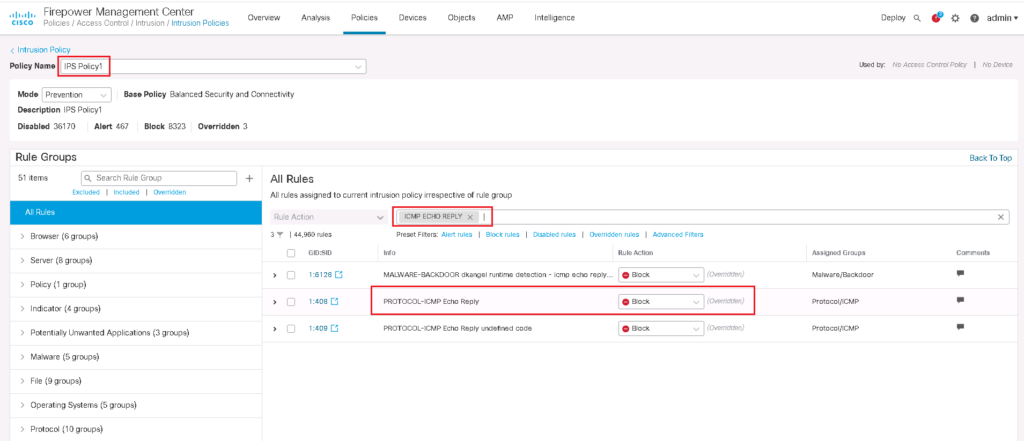
In the previous section we have also activated IPS policy in a rule in which permit all traffic. It is obvious that it does not mean to inspect the traffic in a rule in which drop the traffic.
Firepower IPS Inline mode monitoring and troubleshooting
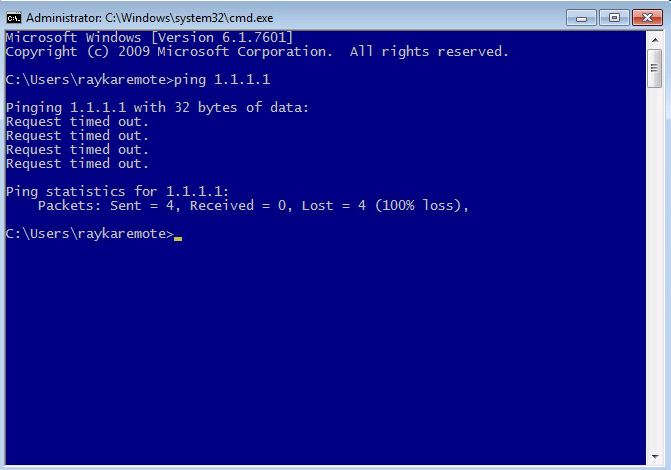
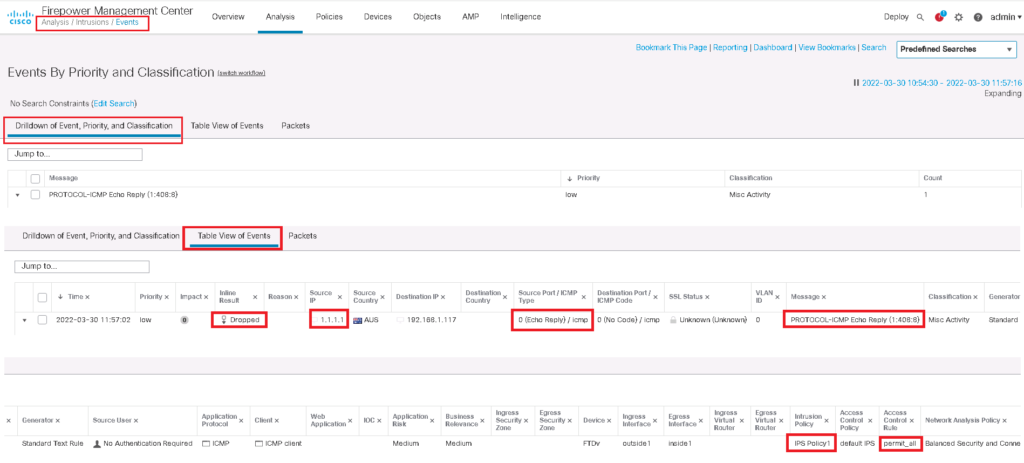
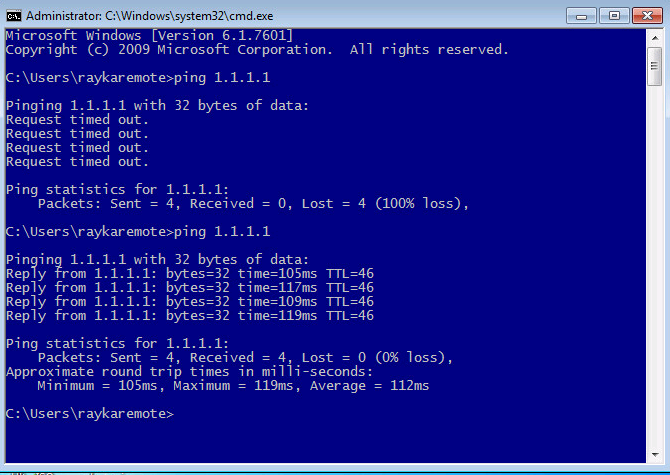
To test that our IPS policy works, it is enough just to ping an external IP from a computer behind Firepower. We expect that ping reply will not be received.
Then we have to check intrusion events to make sure that the ping reply is dropped with our IPS policy.
We can check intrusion events in “Analysis -> Intrusion -> Event”.
Firepower IPS Inline tap mode configuration and monitoring
To implement IPS inline tap mode, the implementation is exactly the same. The only difference is that we have to enable tap mode in inline pair.
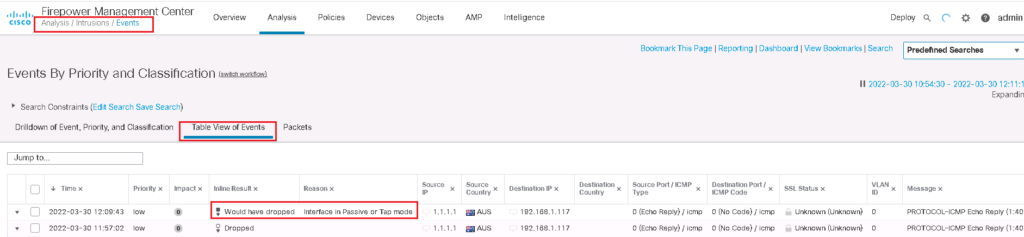
In inline tap mode, as we know, no traffic can be dropped. In other words, all traffic with Block action, will be just alerted.
To make sure, we will ping the same address as inline mode.
now we expect that our ping traffic will be replied.
But there must also be an intrusion event where the traffic should be dropped but cannot be dropped because the copy of the traffic is inspected and the original traffic is already forwarded.

The best explanation I have seen.
Thanks. you are welcome
very good
mr asadpoor is the best teacher in Network and security
thanks. you are welcome.
Amazing explanation!