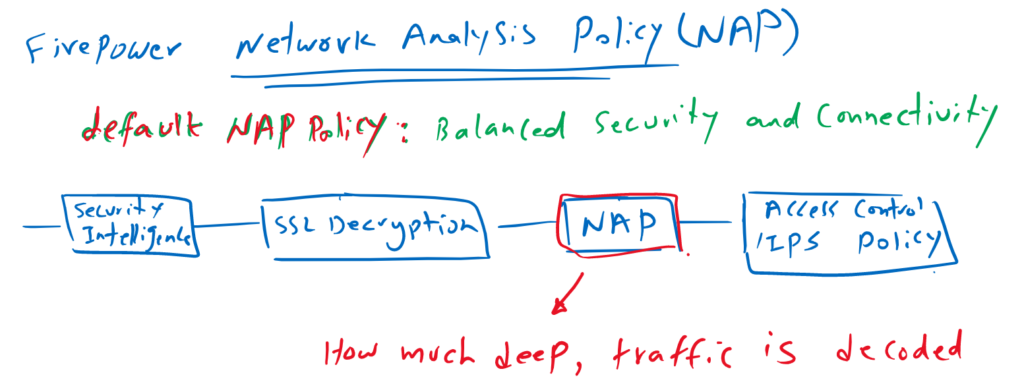
Cisco Firepower Network Analysis Policy determines how much deep a traffic must be pre-processed and decoded before traffic is inspected by access control and IPS policy. Some features like data loss detection or port scan detection require deep traffic pre-processing.
what is Firepower Network Analysis Policy?
Network Analysis Policy occurs after Security Intelligence and SSL decryption, but before access control or intrusion policy begins.
There is a default Network Analysis Policy activated based on Balanced Security and Connectivity inspection.
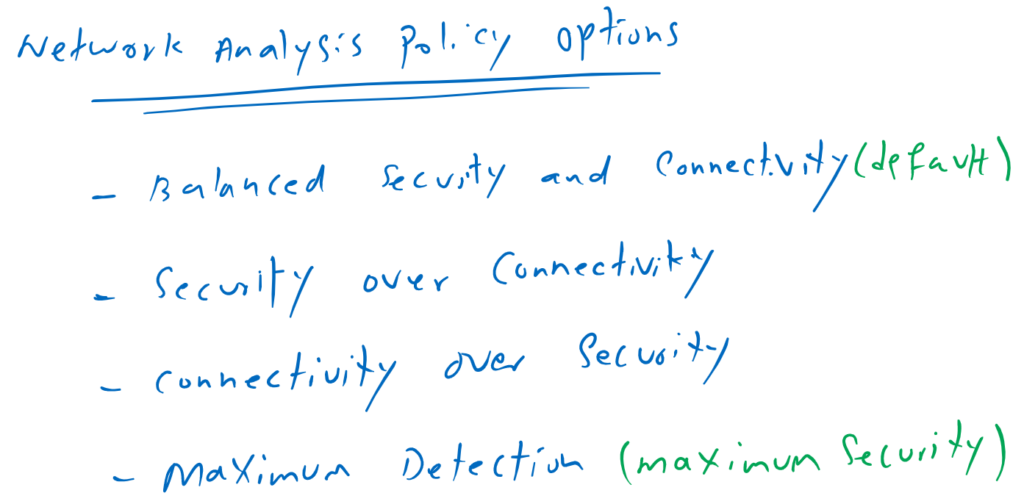
Depending on if security or performance is more important to you, you can choose Security over Connectivity, Connectivity over Security or Balanced Security and Connectivity. Another option is maximum detection of which traffic is decoded the deepest.
After choosing your default network analysis policy, you can change the options according to your needs as we will make changes in the next video.
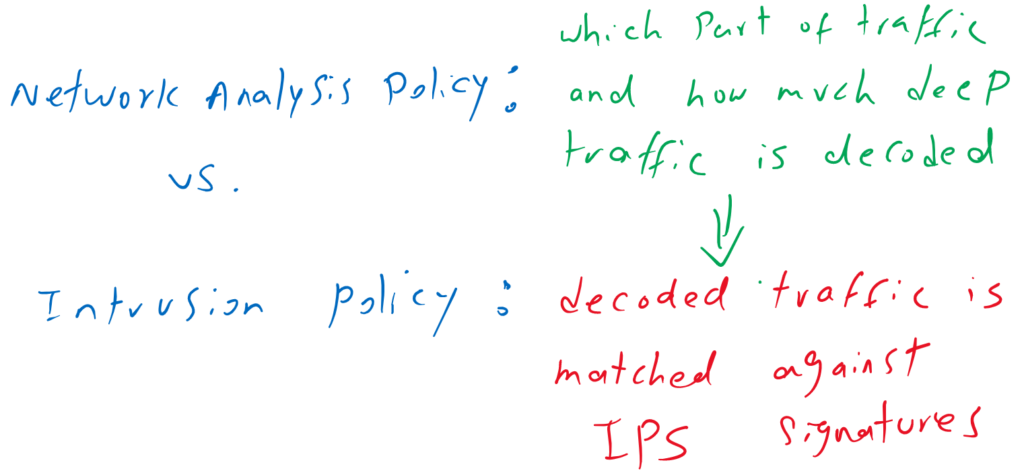
Notice that IPS policy and Network Analysis Policy are different, however the options seems to be the same. Network Analysis Policy determines which part of traffic must be decoded. Then it is inspected and matched with IPS signatures according to IPS Policy.
Cisco Firepower Network Analysis Policy Configuration
To add Network Analysis Policy, go to
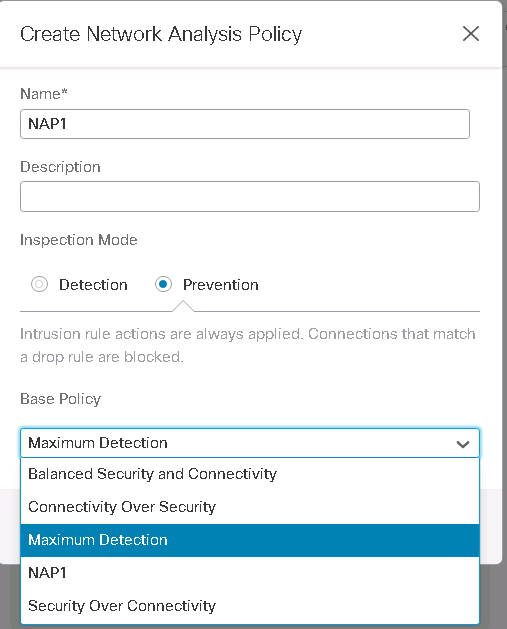
Policies -> Intrusion -> Network Analysis Policies -> create Policy
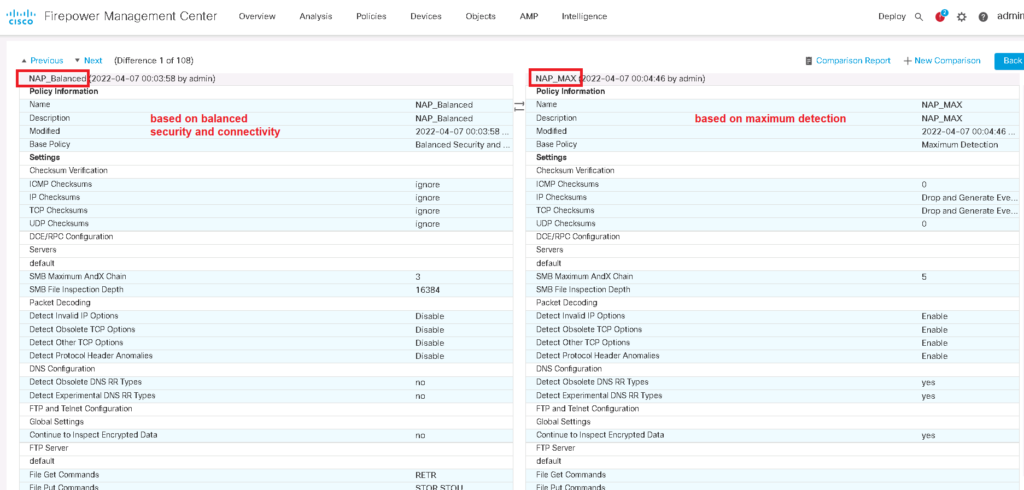
To see how traffic is decoded differently, I create two network analysis policies, one based on Balanced Security and connectivity and the other based on Maximum detection. then I compare between these two policies.
As you can see, in balanced security and connectivity, there are many option which are disabled or ignored but they are enabled in maximum detection option.
To configure Network Analysis Policy, there are two options, snort version 2 and snort version 3.
Normally I should configure Snort version 3, but since the setting that I need for the next video, Sensitive Data Detection, is still not exist in Snort version 3, I configure Snort version 2 settings of Network Analysis Policy.
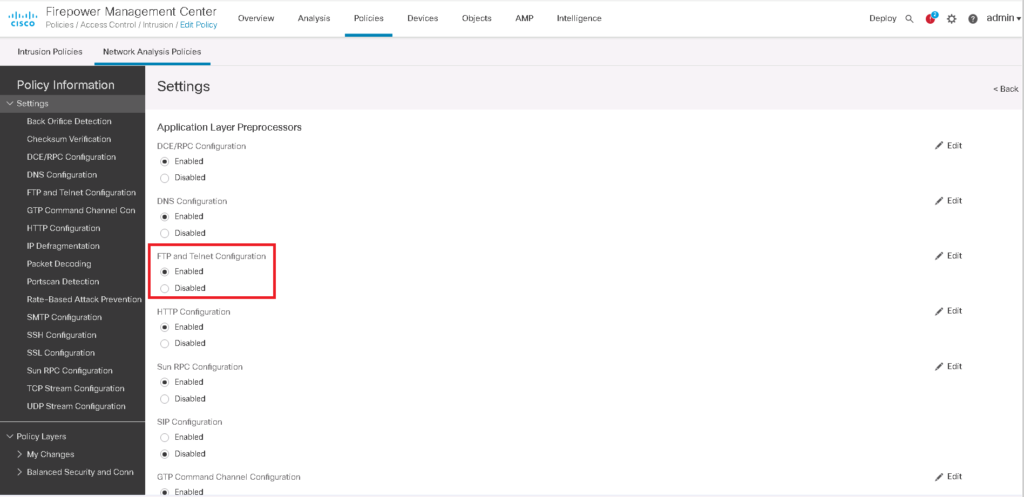
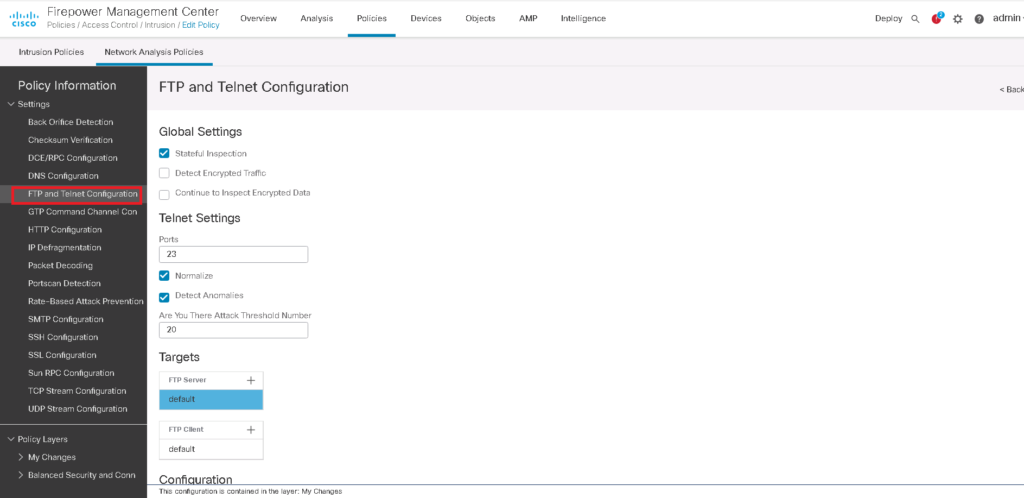
As an example, to implement “Sensitive Data Detection” that will be configured in the next video, we need to enable FTP and Telnet configuration, IP defragmentation, and TCP stream in Network Analysis Policy.
For each of these settings, there are a few parameters that can be adjusted. Parameters are advanced settings that must not be manipulated unless there is sufficient knowledge.
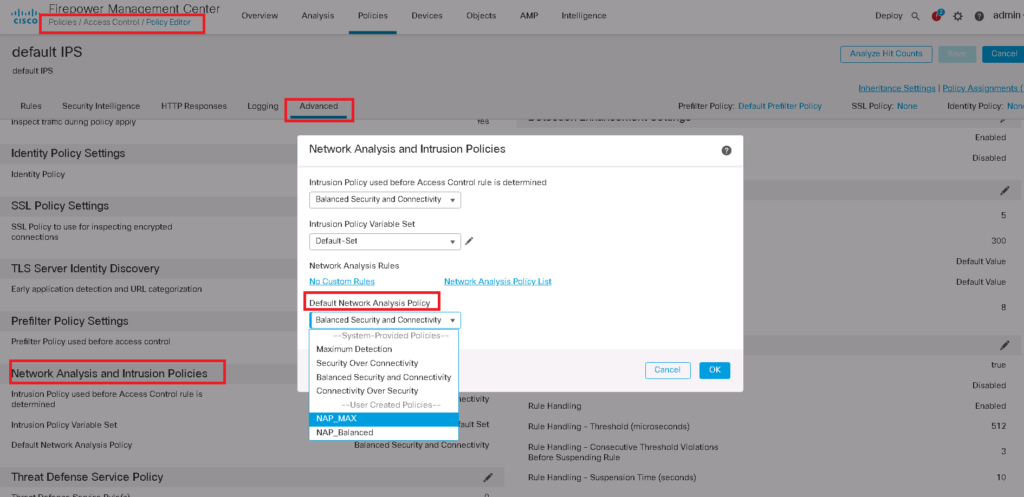
As I have mentioned earlier, default network analysis policy is based on balanced security and connectivity. To change it to your own customized network analysis policy, go to
Policies -> access control -> edit policy -> advanced -> network analysis and intrusion policies section -> edit -> change default network analysis policy to your own customized policy.
Notice that default network analysis policy is balanced security and connectivity.
Also notice that network analysis policy is configured globally and not per access control rule.