Cisco SD-WAN VPN Label concept is important to understand so we can analyse and troubleshoot Cisco SD-WAN network connectivity. I decided to discuss this topic in this section so that we can better understand the concept of service chaining, which will be discussed in the next few sections.
Cisco SD-WAN VPN Label Requirement
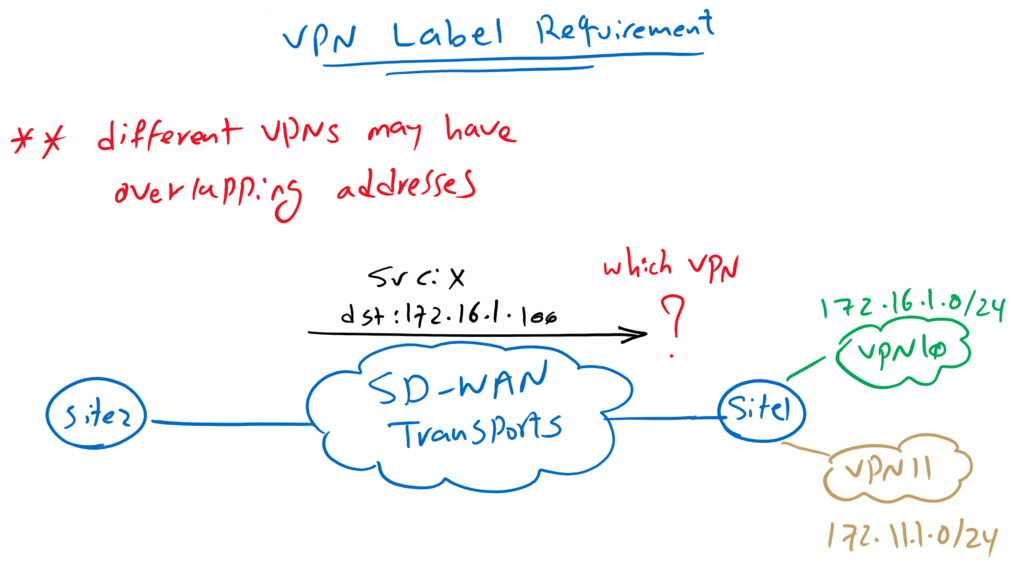
Let’s look at a part of our topology to understand the requirements of VPN label in Cisco SD-WAN infrastructure.
Site1 and Site2 are shown in the topology connected by SD-WAN transports. There are two service VPNs behind WAN Edge Routers like what is shown behind Site1 WAN edge router, VPN10 with IP range 172.16.1.0/24 and VPN11 with IP range 172.11.1.0/24.
The question now arises, how edge routers know to which service VPN a traffic must be routed when it is received through SD-WAN transports?
In our topology, the data traffic is received via SD-WAN transports with the destination address 172.16.1.100 in the Site1 WAN Edge Router. How does the WAN edge router know whether it needs to be forwarded to Service VPN 10 or Service VPN 11? Of course, it cannot detect the target service VPN based on the IP address because different service VPNs can have overlapping IP addresses.
So this is the main reason for the VPN label to exist.
Cisco SD-WAN VPN Label Operation
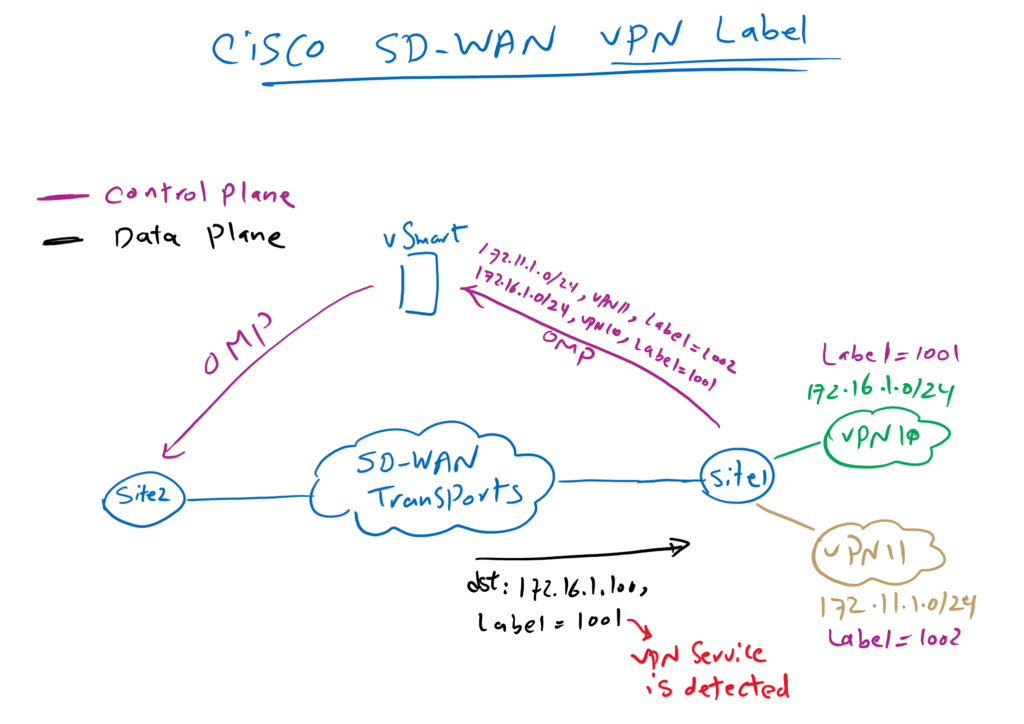
in the same topology it is shown how the VPN label works in the Cisco SD-WAN infrastructure.
The operation of the control plane is indicated by the purple color and data traffic is displayed with black color.
Each WAN edge router specifies a unique label for each of its local service VPNs. Here the WAN edge router in Site1 assigns label 1001 for service VPN 10 and label 1002 for service VPN 11.
VPN labels are then made known to other WAN edge routers through OMP routing protocol and vSmart controller. Therefore, other WAN edge routers know which VPN label to use to route traffic to the destination.
The purple color indicates what is being advertised by the WAN edge router in Site1. As you can see, in addition to the IP address, the labels assigned to each service VPN are also advertised through OMP protocol to vSamrt controller. 172.16.1.0/24 is advertised with label 1001 and 172.11.1.0/24 is advertised with label 1002.
When Site2 WAN edge router forward a traffic to destination 172.16.1.100 in Service VPN 10, it knows already that it must be forwarded with VPN label 1001.
And when the WAN edge router in site1 receives traffic with the VPN label 1001 via SD-WAN transports, from label 1001, it knows that it belongs to the service VPN 10 . Therefore, it knows exactly to which Service VPN, receiving traffic needs to be forwarded.
Cisco SD-WAN VPN Label Encapulation
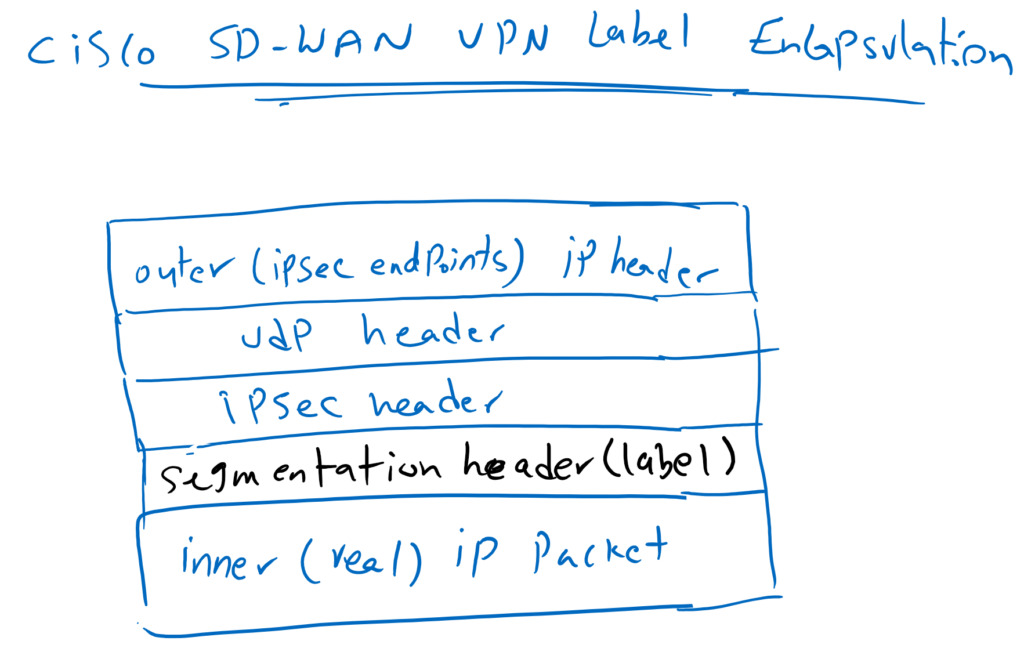
The next question is, in which part of data traffic, the VPN label is encapsulated?
As you know and it is also shown in the figure, data traffic between sites are encapsulated and forwarded through IPsec tunnel.
In this encapsulation, the real IP header points to the IP address of the real source and destination that generate and ultimately use the data traffic. It is encapsulated inside another IP header through an IPsec tunnel. the source and destination addresses of the outer IP header point to endpoints of the IPSec tunnel, which are actually WAN edge routers.
In Cisco SD-WAN infrastructure, there is an additional header between the real IP header and IPsec header called segmentation. One of the most important fields in segmentation header is VPN label, which indicates the destination service VPN.
Cisco SD-WAN VPN Label Monitoring
To better understand let’s check which labels are assigned by site1 to service VPN 10 and service VPN 11. and if they are advertised to site2?
With command “show sdwan omp services”, you can discover which labels are assigned to each service VPN. We check it in site1.
cEdge1#show sdwan omp services
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Stg -> staged
Inv -> invalid
ADDRESS PATH
FAMILY VPN SERVICE ORIGINATOR FROM PEER ID LABEL STATUS
--------------------------------------------------------------------------------
ipv4 10 VPN 1.1.1.101 0.0.0.0 69 1001 C,Red,R
11 VPN 1.1.1.101 0.0.0.0 69 1002 C,Red,R
65528 VPN 1.1.1.101 0.0.0.0 69 1003 C,Red,R
ipv6 10 VPN 1.1.1.101 0.0.0.0 69 1001 C,Red,R
11 VPN 1.1.1.101 0.0.0.0 69 1002 C,Red,RAs you can see, label 1001 is assigned to service VPN 10 and label 1002 is assigned to service VPN 11.
Now we check if these label are known to site2 through OMP protocol? With command “show sdwan omp routes”, we can discover if other wan edge routers know labels assigned by site1.
cEdge1#show sdwan omp routes 172.16.1./24
show omp routes
syntax error: unknown argument
cEdge1#show sdwan omp routes 172.16.1.0/24
---------------------------------------------------
omp route entries for vpn 10 route 172.16.1.0/24
---------------------------------------------------
RECEIVED FROM:
peer 0.0.0.0
path-id 69
label 1001
status C,Red,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 1.1.1.101
type installed
tloc 1.1.1.101, public-internet, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 101
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 1.1.1.52
cEdge1#
cEdge1#show sdwan omp routes 172.11.1.0/24
---------------------------------------------------
omp route entries for vpn 11 route 172.11.1.0/24
---------------------------------------------------
RECEIVED FROM:
peer 0.0.0.0
path-id 69
label 1002
status C,Red,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 1.1.1.101
type installed
tloc 1.1.1.101, public-internet, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 101
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
unknown-attr-len not set
ADVERTISED TO:
peer 1.1.1.52As you can see, site2 know, with which label traffic must be forwarded to 172.16.1.0/24 in VPN 10 and 172.11.1.0/24 in VPN 11.
VPN label operation in cisco SD-WAN is very similar to VPN label in MPLS VPN service if you know it.
In this section we have discussed VPN label to better understand service chaining concept which will be discussed in the next few sections.
Thanks for the clear and detailed explanations