What is F5 LTM? a reverse proxy solution used to optimize and secure application delivery with features like Load Balancing and SSL Offloading.
In this section, we discuss the full proxy or reverse proxy architecture of F5 BIG-IP LTM.
F5 BIG-IP LTM and other well-known Modules
F5 is an American company in the field of application delivery that started its business with a “Load Balancer” called “BIG-IP”, which is still the main F5 product and is called “BIG-IP LTM” or “Local Traffic Manager”.
The name has been changed to LTM because, in addition to acting as a load balancer, it offers us many other optimization and security features such as SSL offloading.
BIG-IP with it’s proprietary operating system, TMOS (Traffic Management Operating System), is not just limited to LTM in today’s F5 business, there are many more modules being added to this product.
Among these modules, some of them like DNS (formerly called GTM), Advanced Web Application Firewall (AWAF) and Access Policy Manager (APM) are the most famous BIG-IP modules.
The main function of BIG-IP LTM is a server load balancer, which means distribute application loads between different server to avoid overloading a specific server.
The main function of BIG-IP DNS is site load balancer, which is to load application traffic to different data centers based on client location or data center load to avoid overloading a specific data center.
BIG-IP AWAF is a firewall for web applications and is a new replacement for BIG-IP ASM module.
And finally BIG-IP APM is a secure remote access solution to enterprise applications.
These are not the only BIG-IP modules but the most well-known modules that I see a lot in enterprises. The list of F5 BIG-IP modules can be found in this link.
reverse proxy versus forward proxy
This course is dedicated to F5 BIG-IP LTM module, a full proxy and reverse proxy solution that, in addition to load balancing, offers many other optimization and security solutions like SSL offloading that will be discussed during the course.
Therefore, in this lesson we will see what reverse proxy is and how it differs from proxy (forward proxy). What is the difference between half proxy and full proxy? And also discuss what are load balancing and SSL offloading, two of the main features of the BIG-IP LTM module.
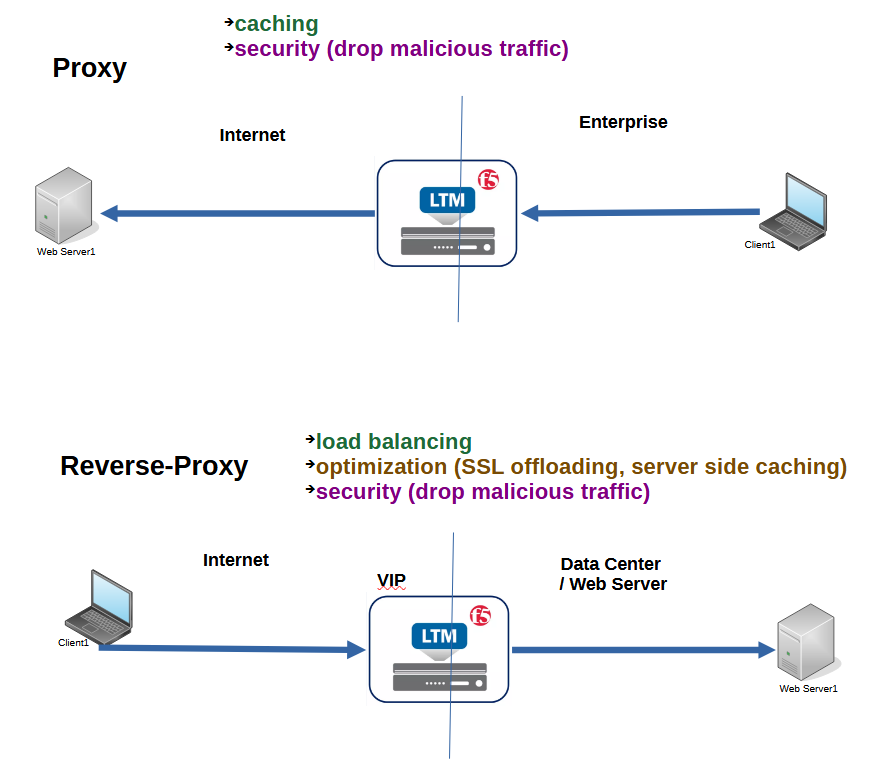
This figure show the difference between proxy (forward proxy) and reverse proxy.
Forward proxy is an intermediary device for clients in an enterprise to access the Internet.
All client requests, especially web requests, are forwarded to the proxy. The proxy then forwards the request to the server over the Internet. The response is returned back to the proxy. The proxy inspects the traffic and forwards it to the client if it is not malicious and compliant with the company’s security policies.
The proxy can also cache the information it receives, so it doesn’t consume internet bandwidth for the next client that requests the same content.
With the reverse proxy, it’s the other way around. Users access the proxy virtual IP from the Internet. The proxy checks the health and load of the servers behind the virtual IP and then decides which server to forward the request to. That’s exactly what F5 LTM does for us.
full proxy versus half proxy
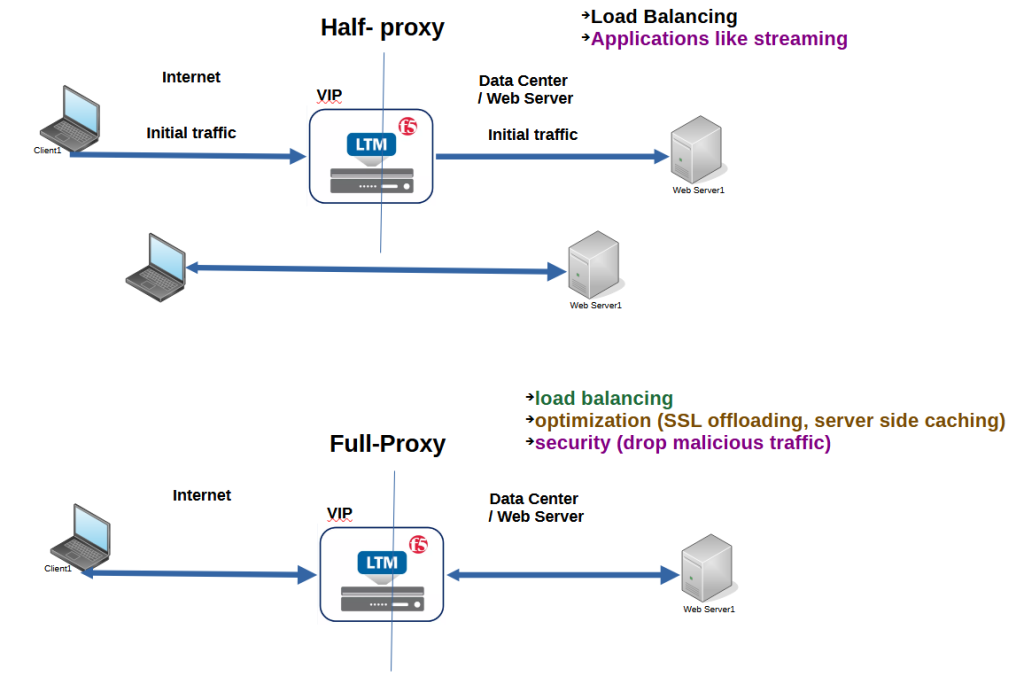
The reverse proxy can be half proxy or full proxy.
In the half proxy, the initial request will be given to the VIP of the BIG-IP and then BIG-IP forward the request to the selected server.
But afterwards, there is a direct communication between server and the client.
In this mode, the role of the reverse proxy is simply to distribute the load of the request across different servers. It can be mainly used for streaming applications where there should be no intermediate device between client and server.
However, with full proxy, all information between client and server is passed through the proxy. This means that the proxy can do some optimization and security checks before forwarding the information between client and server.
F5 BIG-IP LTM offers us all the full features like SSL offloading when it works in full proxy mode.
F5 BIg-IP LTM as Load Balancer
Load Balancing and SSL Offloading are two of the main features of F5 LTM which will be discussed during the course.
But just to get a first impression, these are two photos that may help to understand how these two features work.
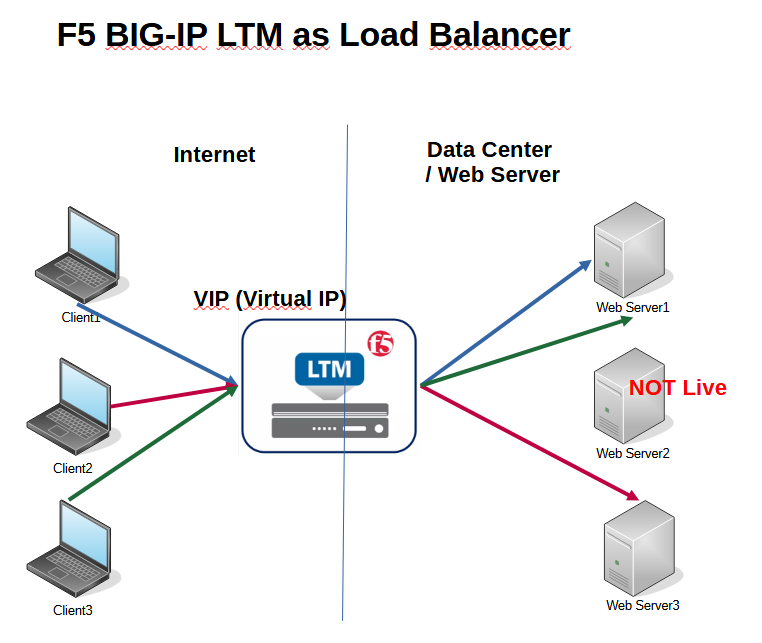
This photo shows how load balancing works in application delivery.
All users give the request to the VIP of the BIG-IP LTM module over the Internet.
BIG-IP LTM checks the health status and utilization of the servers behind the VIP based on the algorithm configured by the administrator.
Then decide to which server this request should be forwarded.
In this example there are three servers providing an application service behind the VIP address. The users iver the internet give the request to the VIP to access the application service.
The first request is forwarded to the first server. The second request is forwarded to the third server because the second server is not healthy and it is not available. The third request is forwarded again to the first server based on the algorithm configured in BIG-IP LTM, which can be as an instance, round-robin algorithm.
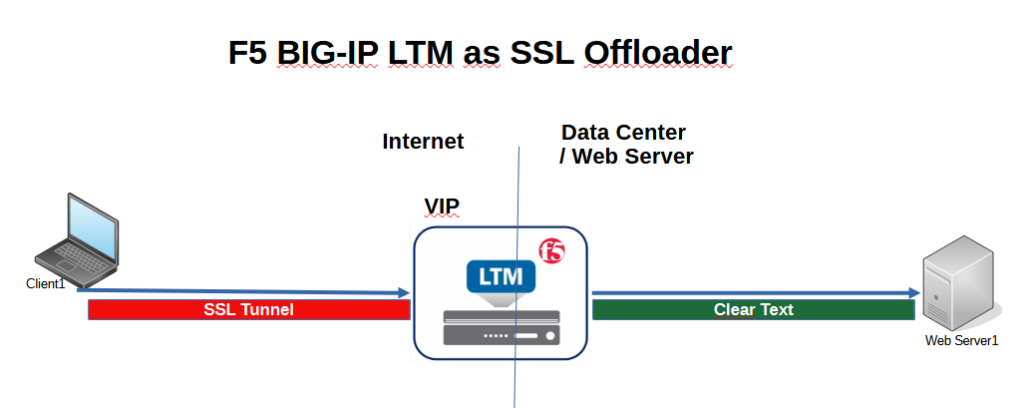
F5 BIG-IP LTM as SSL Offloader
Today, many applications provide services over a secure SSL/TLS infrastructure, which puts an additional load on the server in addition to the application itself.
SSL offloading provides the capability to terminate the secure SSL/TLS infrastructure on the BIG-IP LTM itself, and communication between the LTM and the application service inside the enterprise can be in the clear text to avoid congestion on the server.