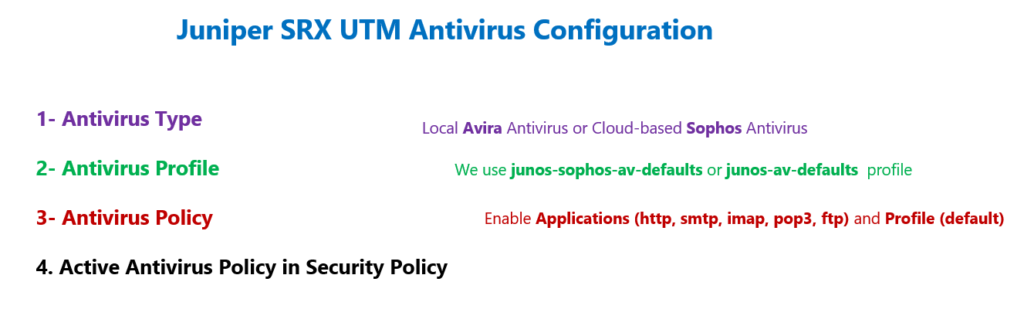
Juniper SRX UTM Antivirus is one of the four services in UTM that we will discuss and configure in this section.
Juniper SRX UTM Antivirus Fundamental
As we discussed in the previous section, we have two options for antivirus in Juniper SRX devices. Local Avira antivirus and cloud-based Sophos antivirus.
In the first step, we have to configure the type of antivirus.
I am using a trial license and have the only option of cloud-based Sophos antivirus for 30 days, but the configuration is similar in both antivirus.
In the second step we can configure a profile or antivirus setting. This step is optional since there are default settings for both antivirus options.
We are allowed to edit the profile when there is a valid license.
In the third step, we configure an antivirus policy. Here you can select which traffic should be scanned by Antivirus. There are options to enable HTTP, email and FTP applications in the antivirus policy.
In the last step, we enable UTM antivirus policy in security policy.
Juniper SRX UTM Antivirus Configuration
Before starting antivirus configuration, let’s check system license with the command “show system license”.
I have trial license which support only cloud-based Sophos antivirus for 30 days.
rayka@vSRX1# run show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 30 days
idp-sig 0 1 0 30 days
appid-sig 0 1 0 30 days
av_key_sophos_engine 1 1 0 29 days
...To start the configuration, we have to enable antivirus engine in the first step. This is configured with the command “set security utm default-configuration anti-virus type ?”.
Here the only option is to enable sophos-engine or disable antivirus.
[edit]
rayka@vSRX1# set security utm default-configuration anti-virus type ?
Possible completions:
sophos-engine Anti-virus sophos-engine
anti-virus-none
[edit]
rayka@vSRX1# set security utm default-configuration anti-virus type sophos-engine
[edit]The second step is to configure or change the antivirus settings. By default, there are antivirus profiles for both antivirus. But because of the missing license I am not able to edit the setting.
You can check the name of antivirus default profile with the command “show groups junos-defaults security utm feature-profile anti-virus profile ?” in configuration mode.
[edit]
rayka@vSRX1# show groups junos-defaults security utm feature-profile anti-virus profile ?
Possible completions:
<name> Anti-virus profile name
junos-av-defaults Anti-virus profile name
junos-sophos-av-defaults Anti-virus profile name
[edit]
rayka@vSRX1# show groups junos-defaults security utm feature-profile anti-virus profile junos-sophos-av-defaults
##
## protect: groups junos-defaults
##
[edit]
rayka@vSRX1# show groups junos-defaults security utm feature-profile anti-virus profile junos-av-defaults
##
## protect: groups junos-defaults
##
[edit]
rayka@vSRX1# In the third step we will configure the antivirus policy. In antivirus policy named ANTIVIRUS POLICY1 we enable antivirus for all existing applications which are HTTP, Email and FTP.
In the policy, we also call the new configured or default profile. Here the default profile junos-sophos-av-defaults is enabled.
[edit]
rayka@vSRX1# run show configuration security utm | display set
set security utm default-configuration anti-virus type sophos-engine
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus http-profile junos-sophos-av-defaults
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus ftp upload-profile junos-sophos-av-defaults
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus ftp download-profile junos-sophos-av-defaults
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus smtp-profile junos-sophos-av-defaults
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus pop3-profile junos-sophos-av-defaults
set security utm utm-policy ANTIVIRUS_POLICY1 anti-virus imap-profile junos-sophos-av-defaultsIn the last step, we enable the configured policy in security policy.
From untrust zone to trust zone, there is a default default-permit rule that we configured in the previous sections.
We enable UTM ANTIVIRUS POLICY1 in default-permit security policy.
rayka@vSRX1# run show configuration security policies from-zone untrust to-zone trust | display set
set security policies from-zone untrust to-zone trust policy default-permit match source-address any
set security policies from-zone untrust to-zone trust policy default-permit match destination-address any
set security policies from-zone untrust to-zone trust policy default-permit match application any
set security policies from-zone untrust to-zone trust policy default-permit then permit
rayka@vSRX1# set security policies from-zone untrust to-zone trust policy default-permit then permit application-services utm-policy ANTIVIRUS_POLICY1
rayka@vSRX1# run show configuration security policies from-zone untrust to-zone trust | display set
set security policies from-zone untrust to-zone trust policy default-permit match source-address any
set security policies from-zone untrust to-zone trust policy default-permit match destination-address any
set security policies from-zone untrust to-zone trust policy default-permit match application any
set security policies from-zone untrust to-zone trust policy default-permit then permit application-services utm-policy ANTIVIRUS_POLICY1
These are all that need to be configured for antivirus protection.