Juniper SRX Source NAT Off allows to disable source NAT for some specific Traffic.
It can be very helpful for VPN traffic, since most VPN protocols are not compatible with NAT services.
Disabling NAT can also be configured for destination NAT, however it is mostly useful for source NAT.
Juniper SRX Source-NAT off Fundamental
Sometime it is necessary or useful to disable NAT for some specific traffic especially for VPN traffic.
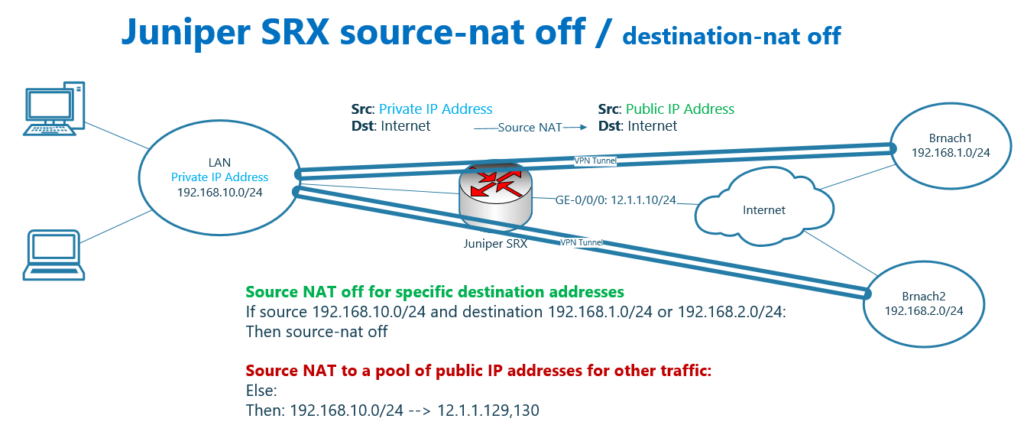
Look at this topology that we have activated source NAT in juniper SRX so users inside the network with private IP addresses can connect to the internet.
Now suppose that we have VPN connection from a VPN server behind juniper SRX or from Juniper SRX itself to the branches.
In other words, VPN-encapsulated traffic, and likely encrypted traffic, is routed through a device with activated NAT services.
But most of the time, translating these kind of traffic are not easy and sometimes impossible. In other words, the VPN traffic is incompatible with NAT and the VPN connection will drop.
One solution is to disable NAT for certain traffic, here VPN traffic, between main office and branch offices.
The other solution is to use NAT traversal solutions which makes VPN traffic compatible with NAT services which is not discussion of this section.
Juniper SRX Source-NAT off Configuration
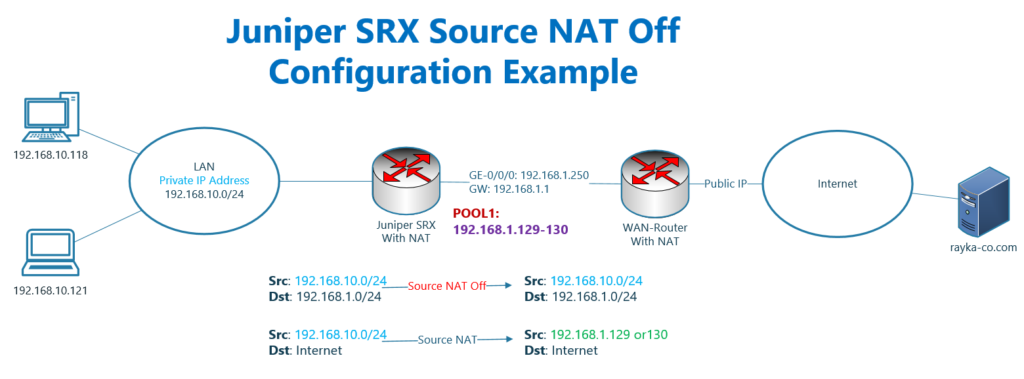
This is the topology that we configured the source NAT in the previous sections.
Users inside the network with IP address in the subnet 192.168.10.0/24 are connected to the internet through two intervening devices.
All traffic with the source 192.168.10.0/24 are translated in juniper SRX into a pool with two IP addresses in the subnet 192.168.1.0/24, .129 and .130.
The second device, WAN router, which is not under my control, translates the IP addresses in the subnet 192.168.1.0/24 to a specific public IP address.
The problem is that even if the destination of the traffic coming from the LAN subnet is 192.168.1.0/24, it will be translated which is not required in this topology.
What we are going to configure in this section is to exclude traffic with the source 192.168.10.0/24 and destination 192.168.1.0/24 from the NAT service.
Check current source NAT configuration
Before we start excluding some traffic from the source NAT service, let’s look at the current configuration of the source NAT.
With command “show configuration | display set | grep “nat source””, we can check the current configuration of source NAT.
rayka# run show configuration | display set | grep "nat source"
set security nat source pool POOL1 address 192.168.1.129/32
set security nat source pool POOL1 port no-translation
set security nat source pool POOL1 overflow-pool interface
set security nat source address-persistent
set security nat source rule-set SOURCE-NAT from zone inside
set security nat source rule-set SOURCE-NAT to zone outside
set security nat source rule-set SOURCE-NAT rule NAT-POOL match source-address 192.168.10.0/24
set security nat source rule-set SOURCE-NAT rule NAT-POOL then source-nat pool POOL1As you can, all traffic from the inside zone to the outside zone with the source IP address in the subnet 192.168.10.0/24 is first translated to the IP address 192.168.1.129 configured in the pool without port translation, and then to the outgoing interface IP Address with port translation.
monitor status of translation before “source-NAT off” configuration
Before configuring “source-nat off” or disabling source NAT for traffic to the destination 192.168.1.0/24, let’s monitor the current status of translation.
We monitor live status of log file, with the command “monitor start” command.
To generate a traffic, we send HTTP traffic from inside zone to the outside zone with destination 192.168.1.88.
Sep 2 14:28:18 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.118/48062->192.168.1.88/80 0x0 junos-http 192.168.1.250/2877->192.168.1.88/80 0x0 source rule NAT-POOL N/A N/A 6 PERMIT-WEB inside outside 17179902873 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A The output of log file shows that the source of traffic is translated from 192.168.10.118 to 192.168.1.250 and it is matched with the rule “NAT-POOL” in the NAT rules and “PERMIT-WEB” in security policies.
We can also monitor the status of the session in the session table with the command “show security flow session | grep /80”.
rayka# run show security flow session | grep /80
In: 192.168.10.118/48060 --> 192.168.1.88/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 2, Bytes: 112,
Out: 192.168.1.88/80 --> 192.168.1.250/21556;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 1, Bytes: 60, As you can see, the source IP the original traffic is 192.168.10.118 but destination IP address of return traffic is 192.168.1.250.
It means that it is translated according to the source NAT rule.
Juniper SRX source NAT off configuration
Now it is the time to configure “source-nat off”.
This is the configuration to disable and exclude traffic with the source on the subnet 192.168.10.0/24 and the destination on the subnet 192.168.1.0/24 from the source NAT.
The last line of configuration inserts NAT exemption rule before the general source NAT configuration.
set security nat source rule-set SOURCE-NAT rule SNAT-OFF match source-address 192.168.10.0/24
set security nat source rule-set SOURCE-NAT rule SNAT-OFF match destination-address 192.168.1.0/24
set security nat source rule-set SOURCE-NAT rule SNAT-OFF then source-nat off
insert security nat source rule-set SOURCE-NAT rule SNAT-OFF before rule NAT-POOL Now we can copy and commit the configuration
monitor status of translation after “source-NAT off” configuration
Now that we have disabled source NAT for some specific traffic, let’s generate again the traffic between these two subnets, from 192.168.10.0/24 to 192.168.1.0/24 and monitor status of translation with the same monitoring commands.
The command, “monitor start” is already activated.
We send again HTTP traffic.
Sep 2 14:29:14 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.118/48064->192.168.1.88/80 0x0 junos-http 192.168.10.118/48064->192.168.1.88/80 0x0 source rule SNAT-OFF N/A N/A 6 PERMIT-WEB inside outside 17179902949 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
The output of log file shows that traffic is forwarded without any translation. It also shows that the traffic is matched with “SNAT-OFF” rule.
The output of session table shows also the same result.
rayka# run show security flow session | grep /80
In: 192.168.10.118/48058 --> 192.168.1.88/80;tcp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 2, Bytes: 112,
Out: 192.168.1.88/80 --> 192.168.10.118/48058;tcp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 1, Bytes: 60, Juniper SRX destination NAT off configuration
As I have explained in the introduction of this video, it is also possible to disable NAT in the destination NAT for some specific traffic.
The configuration is exactly like “source-nat off”, but let’s just to check the configuration.
With the command “set security nat destination rule-set DNAT rule DNAT-OFF then destination-nat ?“, you can see that there is an “off” option, where you can disable destination NAT for some traffic.
rayka# set security nat destination rule-set DNAT rule DNAT-OFF then destination-nat ?
Possible completions:
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
off No action
> pool Use Destination NAT pool
> rule-session-count-alarm Config rule-session-count-alarm to destination rule
[edit]