Firepower Sensitive Data Detection, or Data Loss Prevention (DLP), detects and generates events where intentionally or accidentally sensitive data such as social security numbers, credit card numbers, driver’s license numbers, etc. are leaked.
Configuring Firepower Sensitive Data Detection
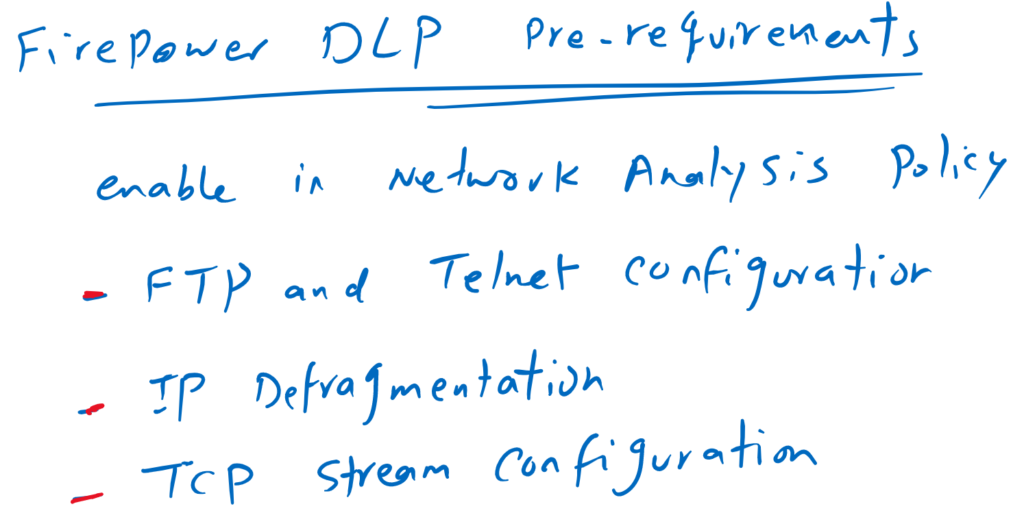
Network Analysis Policy pre-requirement
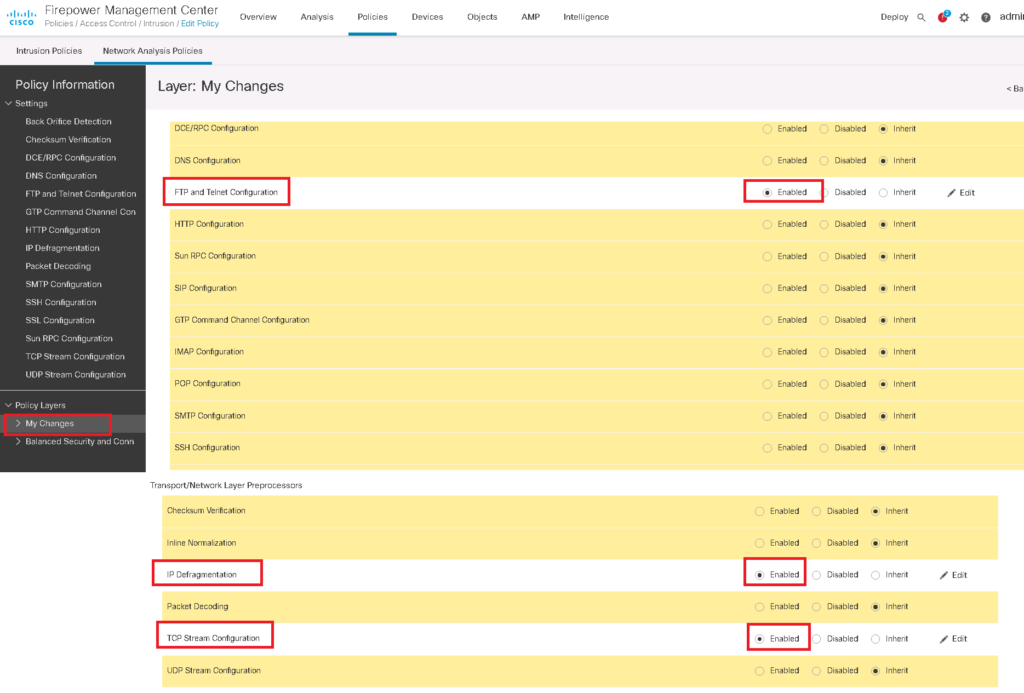
Before configuring sensitive data detection, make sure that FTP and Telnet Configuration, IP Defragmentation and TCP Stream Configuration are active in network analysis policy.
We have activated these settings in the previous video but to make sure, let’s check it once again.
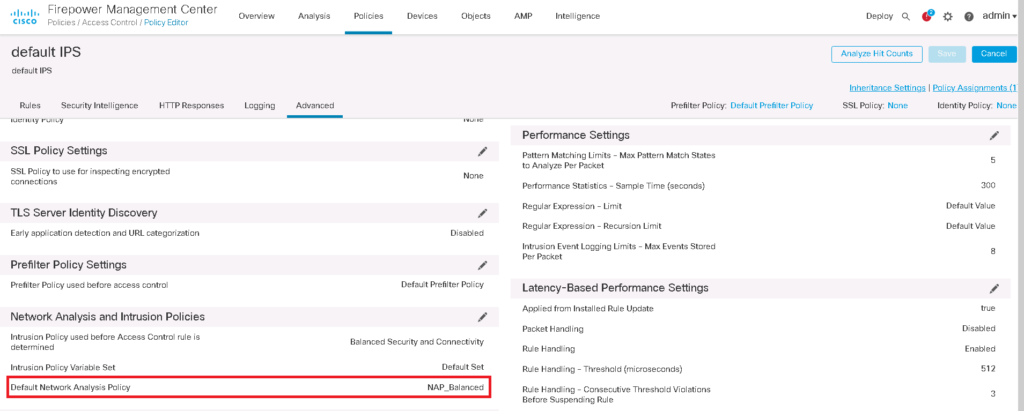
First let’s check which network analysis policy is activated globally.
Policies -> Access Control -> Edit Policy -> Advanced -> Network Analysis and Intrusion Policies
As you can see, our customized network analysis policy, NAP_BALANCED is activated.
Then we have to make sure that required options are active in network analysis Policy.
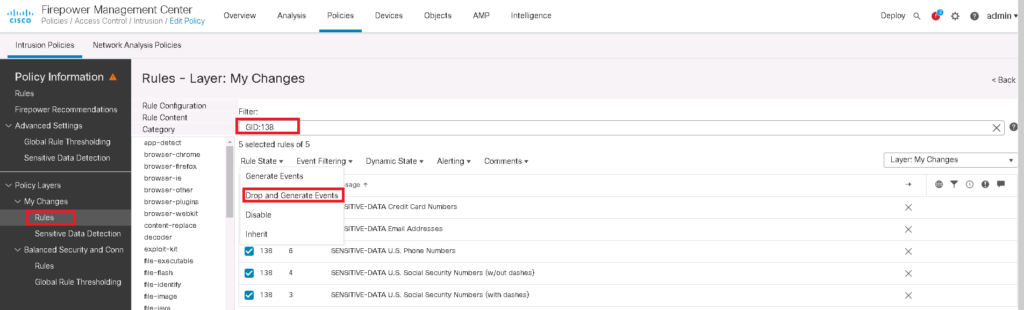
Policies -> Intrusion -> Network Analysis Policies -> Edit Snort 2 Version of Active Network Analysis Policy -> Policy Layers -> My Changes
I edit snort version 2 since the required features are not still available in snort version 3.
Enable Sensitive Data Detection
Then we enable Sensitive Data Detection
Policies -> Intrusion -> Edit Snort 2 Version -> Advanced Setting -> Sensitive Data Detection -> Enable
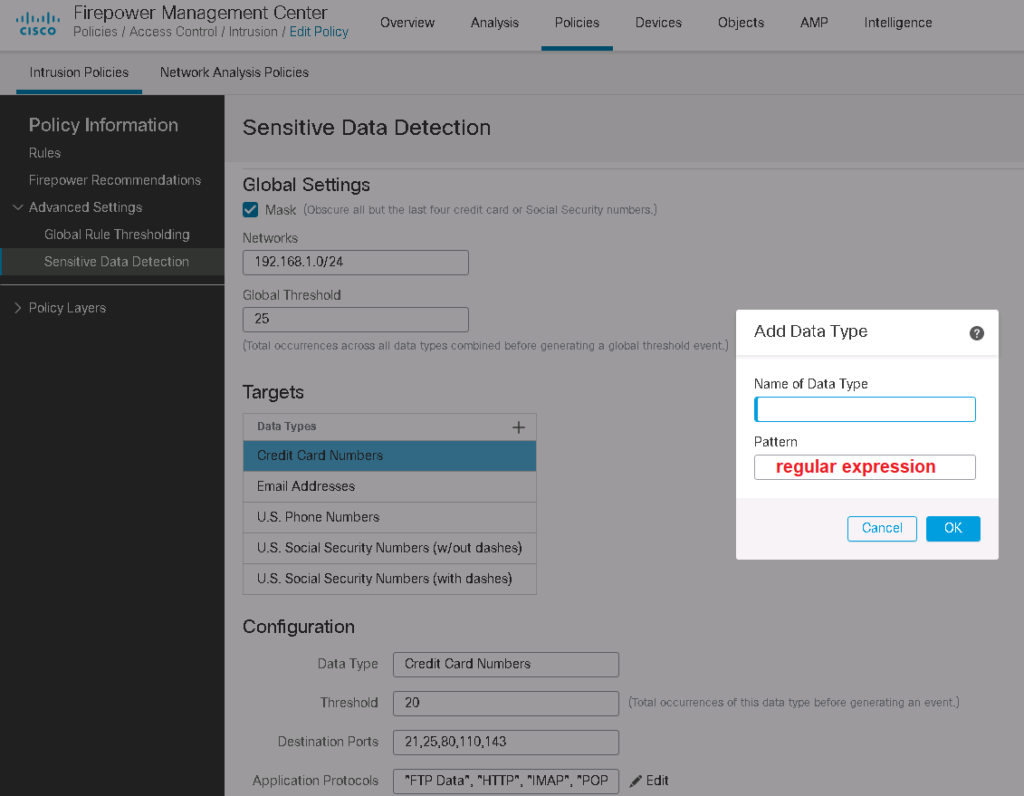
After activating sensitive data detection, some settings are available to configure.
Mask: if it is enabled, replaces all but the last four digits of credit card numbers and Social Security numbers with Xs in the triggering packet.
Networks: Specifies the destination host or hosts to monitor for sensitive data. You can specify a single IP address, address block, or a comma-separated list of IP addresses.
Global Threshold: Specifies total number of all occurrences of all data types during a single session that the pre-processor must detect before generating an event.
By default there are some data types which are detected by sensitive data detection module like credit card numbers, email addresses, US phone numbers and social security numbers. But we can add our own data type with the help of regular expression.
For each data type, there is a threshold field independent of global threshold field to trigger an event, destination ports to monitor for the data type, application protocols to monitor for the data type and regular expression pattern to detect.
Enable Sensitive Data Rules in the intrusion Policy
To detect and generate event or drop offending packets, we need to also enable corresponding IPS rules in intrusion policy.
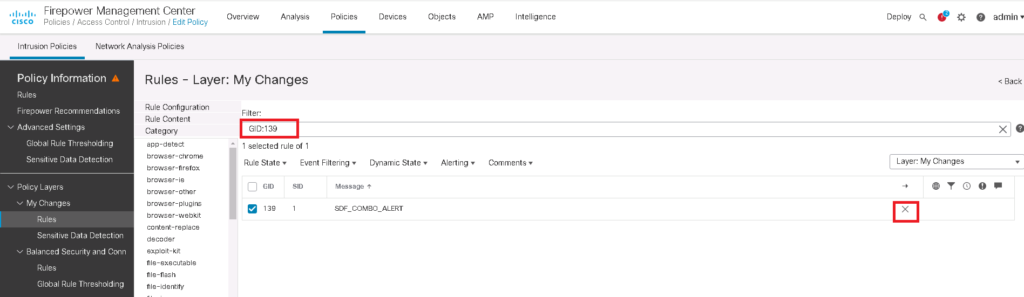
To do that, we enable signatures with GID of 138 and 139 in intrusion policy. for each sensitive data type, there is an intrusion rule with GID of 138.
IPS signature rule 139:1 is required also to be enables to detect and generate events and drop offending packets on combined data type occurrences.
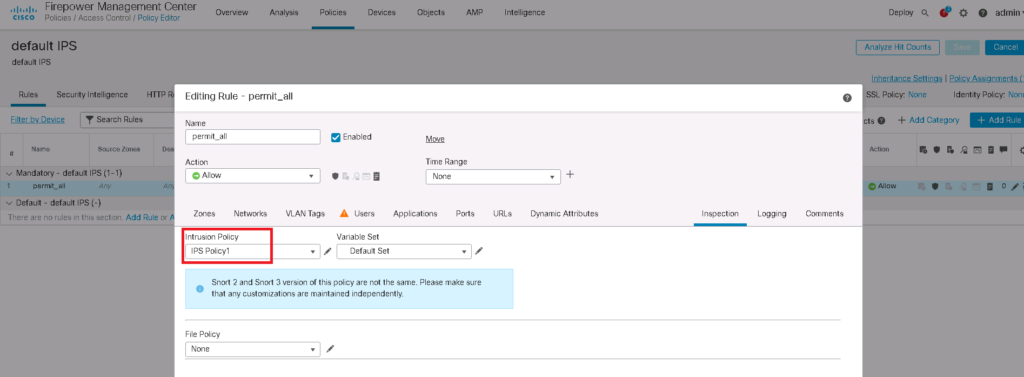
Also do not forget to enable intrusion policy in access control policy. we have already activated in the previous sections.
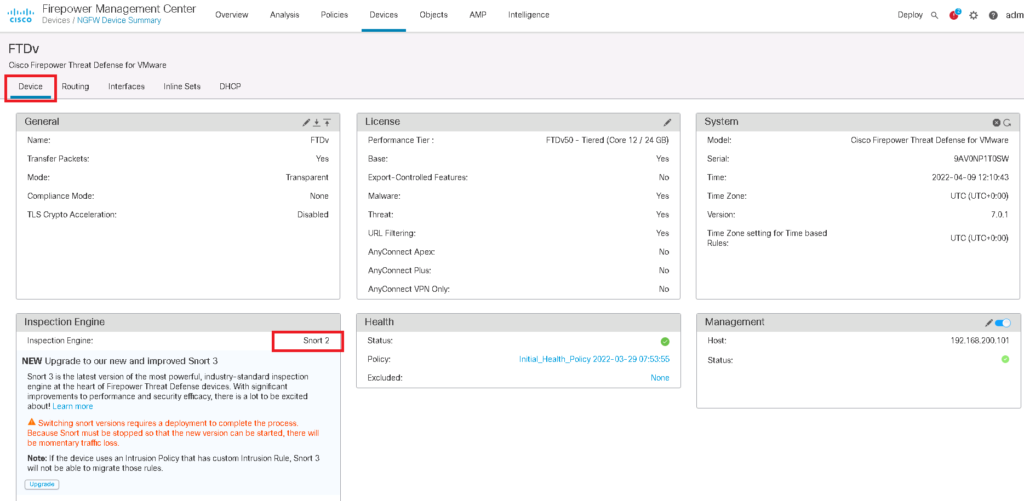
Since we configured Snort version 2, I also need to change the device Snort version from 3 to 2 to see the result of the policy. but I hope that we have sensitive data detection feature also in snort version 3 soon.
Devices -> Device Management -> click IPS Device -> Device -> Inspection Engine -> Snort Version 2
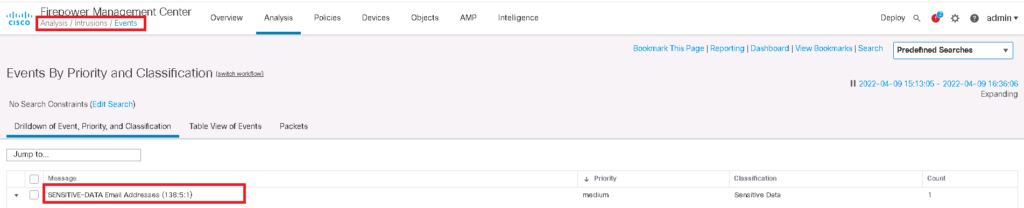
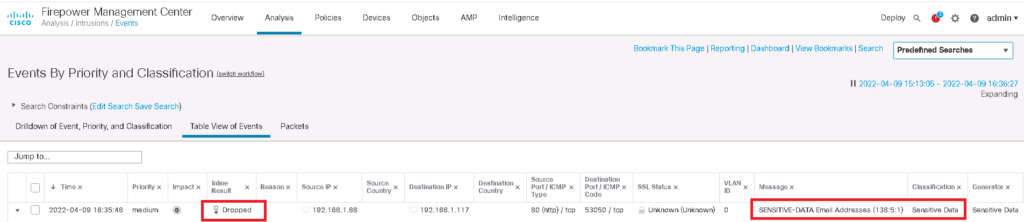
check the result of Sensitive Data Detection policy
To check the result of sensitive data detection policy, we try to download a list of email addresses through IPS device and then check intrusion event.