Cisco Firepower Port Scan Detection, as the name suggests, detects and filters all port scan activity from unauthorized sources.
Cisco Firepower Port Scan Detection Configuration
As we did in the previous section for sensitive data detection, to enable port scan detection we must first enable port scan detection in active network analysis policy and then enable port scan signatures with group id 122 in IPS policy.
Configure Port Scan Detection in Network Analysis Policy
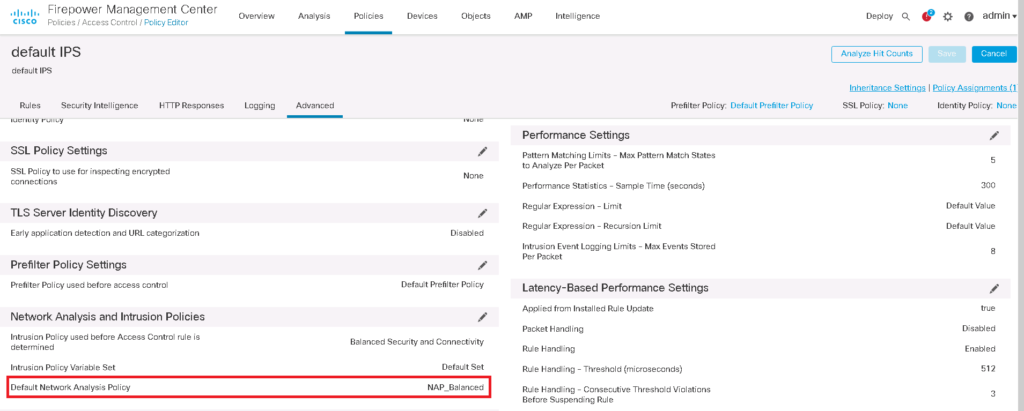
If you remember we have enabled a custom default Network Analysis Policy in the previous video. You can check which network analysis policy is the default one in access control policy advanced tab.
Policies -> Access Control -> Edit Policy -> Advanced -> Network Analysis and Intrusion Policies
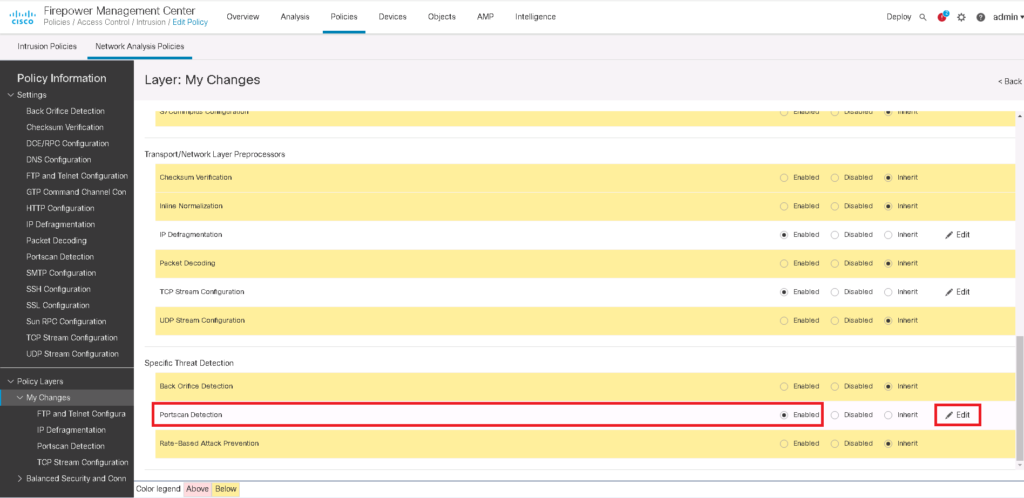
Now we have to enable port scan detection in active network analysis policy.
Policies -> Intrusion -> Network Analysis Policies -> Edit Snort 2 Version of Active Network Analysis Policy -> Policy Layers -> My Changes -> Enable Port Scan Detection
I edit snort version 2 since the required features are not still available in snort version 3.
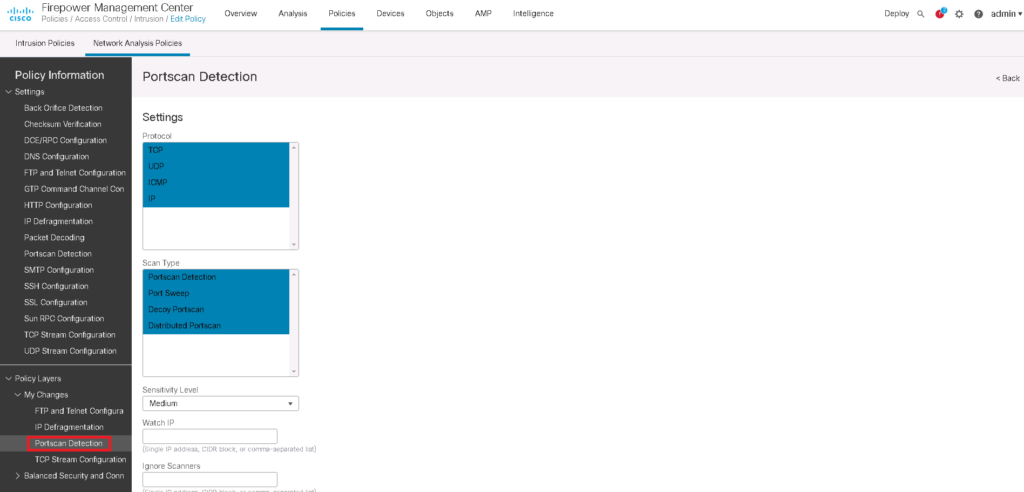
Then we edit port scan detection parameters. By default only TCP and UDP scan are detected. I add also IP and ICMP scan also to be detected.
I change severity Level from low to medium or high depending on how important it is on our business.
We can also except some IP addresses to be ignored when they scan the network or when they are scanned in the network. Probably they are intentional NOC port scan to find network vulnerabilities.
Configure Port Scan Signatures in IPS Policy
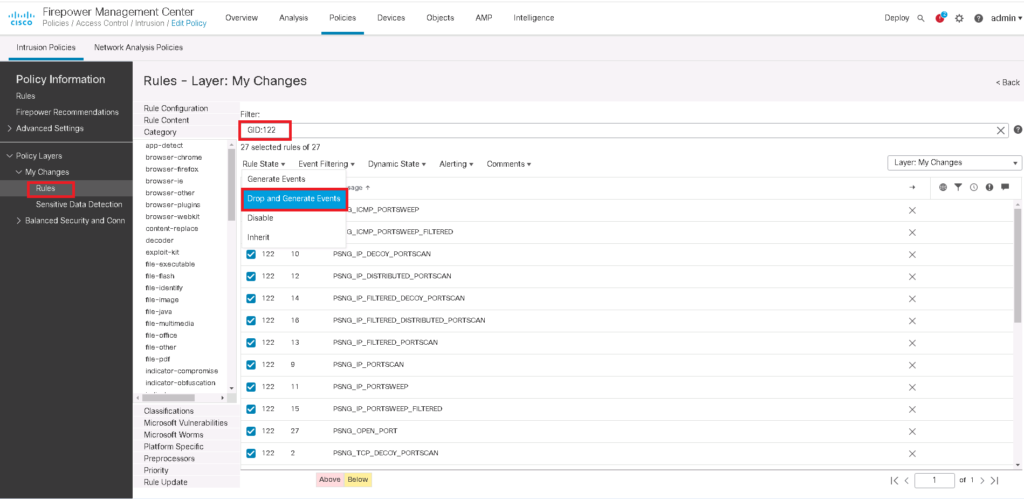
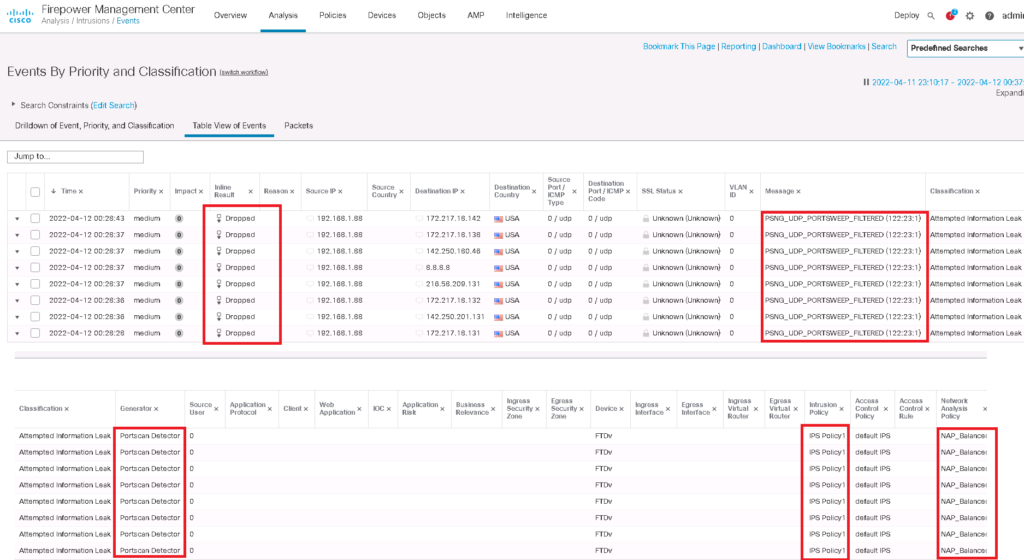
In the next step, we need to enable IPS signatures related to port scan with GID of 122 to filter or alert when scan activities from unauthorized IP addresses are detected.
Policies -> Intrusion -> Intrusion Policies -> Edit Snort 2 Version -> search GID:122 -> Action: DROP and Create Events
Scan the Network and See The Result of Port Scan Detection
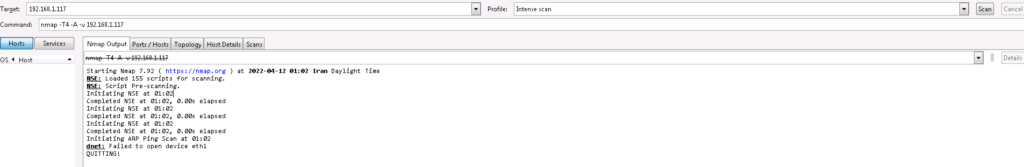
To check the result of policy, I scan the network with NMAP software.
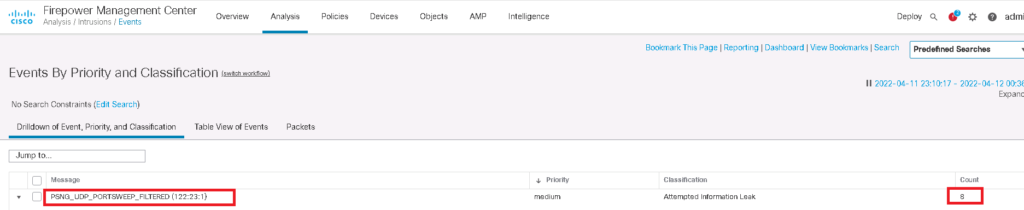
then we can check if it is filtered and detected in intrusion events.
Analysis -> Intrusion -> Events