F5 DNS Express is a high-speed secondary authoritative DNS server for answering DNS queries from a transferred zone.
Additionally, it is less vulnerable to attacks because it does not run a full BIND DNS service.
This is what we are going to discuss and implement in a few sections.
F5 BIG-IP DNS Express Configuration
F5 BIG-IP DNS Lab preparation
In the F5 BIG-IP LTM course, I have explained the basic steps to prepare, license and configure F5. You can access this lesson for free and I suggest that you review it and set up a virtual F5 device in a lab environment before continuing with this lesson.
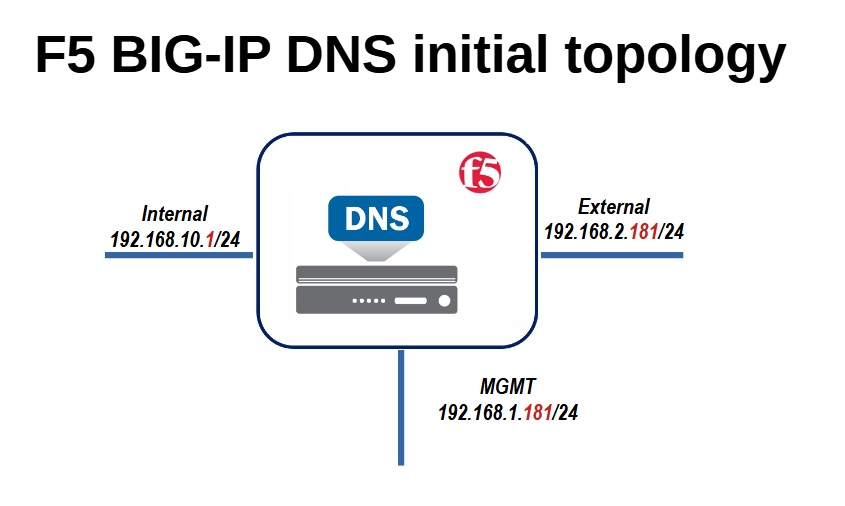
This is the topology of F5 BIG-IP DNS connectivities. F5 has three interfaces, management with the IP address 192.168.1.181, external interface with IP address 192.168.2.181 and internal interface with IP address 192.168.10.1.
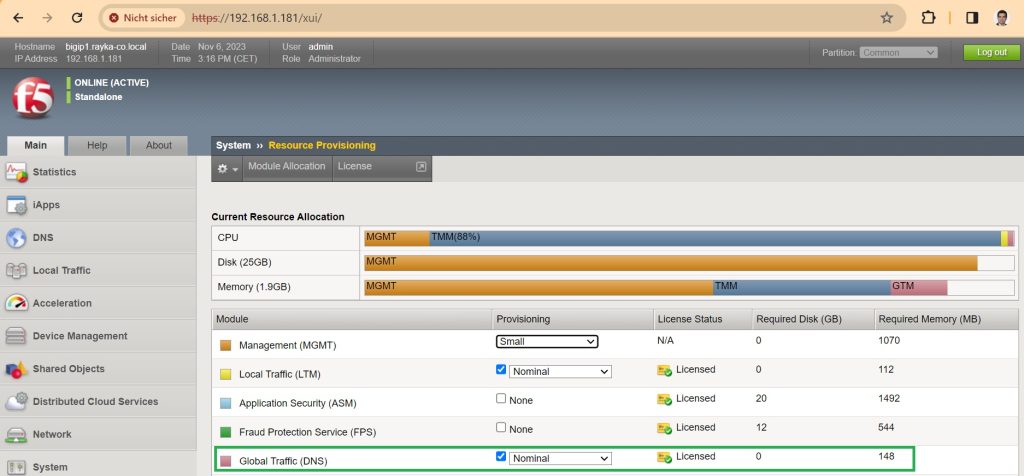
To use F5’s DNS features, we also need to activate the Global Traffic (DNS) license in the resource provisioning section.
Microsoft Windows Server as the primary authoritative DNS server
Another requirement for implementing DNS Express is the availability of a primary authoritative DNS server for a zone, which F5 takes on the role of the secondary DNS server.
In this section we will use the Microsoft DNS server as the primary authoritative DNS server, but in the next sections we will also learn how to use the local F5 Bind server as the primary authoritative DNS server.
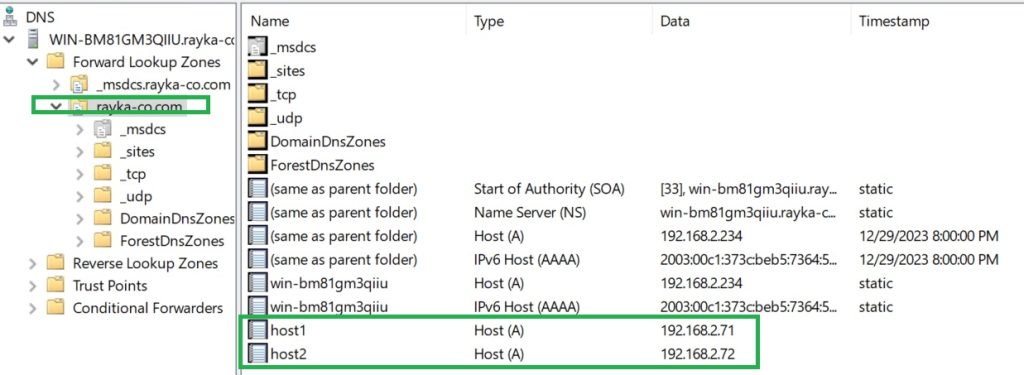
Microsoft DNS server is installed automatically for the domain „rayka-co.com“, when I installed the domain controller on the Windows server. Just as a test, I added two A records, host1 and host2, with the IP addresses 192.168.2.71 and 192.168.2.72.
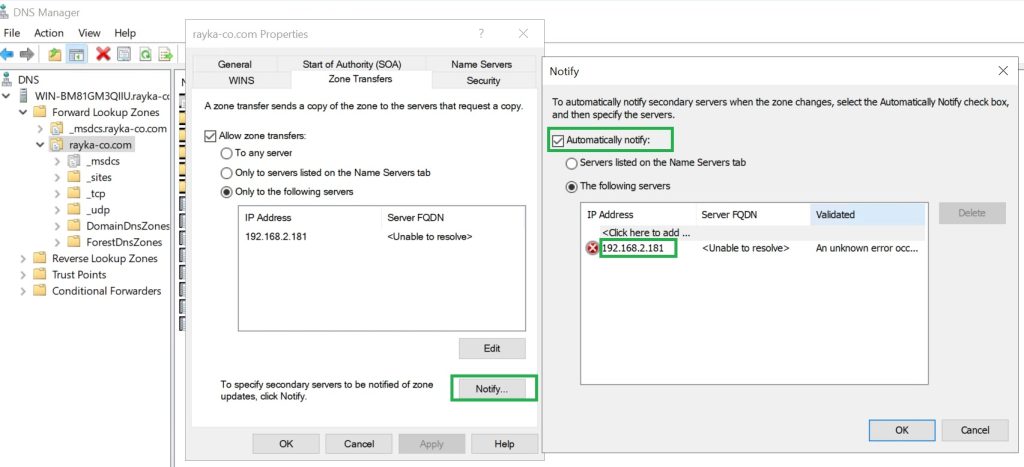
To use F5 as a secondary DNS server, we need to transfer the zone from the Microsoft DNS server to the F5 device. This is possible if we allow zone transfer in Microsoft DNS server.
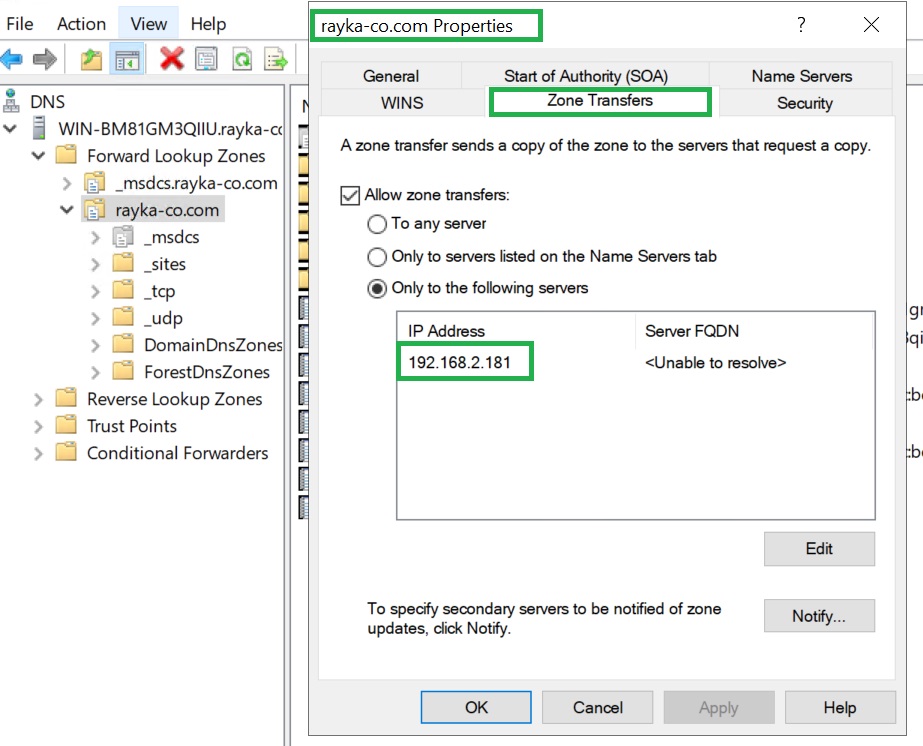
Under “Zone > Properties > Zone Transfers” we can allow zone transfers generally or to specific IP addresses.
In my lab environment, the IP address of the Microsoft DNS server is “192.168.2.234” and is located in the external interface of the F5 device. Therefore, I add the external F5 interface IP address “192.168.2.181” to be allowed for zone transfer.
We also need to enable a notification to be sent to the secondary F5 DNS server whenever Microsoft’s primary DNS server changes.
Under “Zone > Properties > Zone Transfers > Notify”, we add the IP addresses of F5 external interface, so that any changes to the primary DNS server are notified to the secondary F5 DNS server.
F5 DNS Express configuration
Now we can start with the DNS Express configuration in the F5 device.
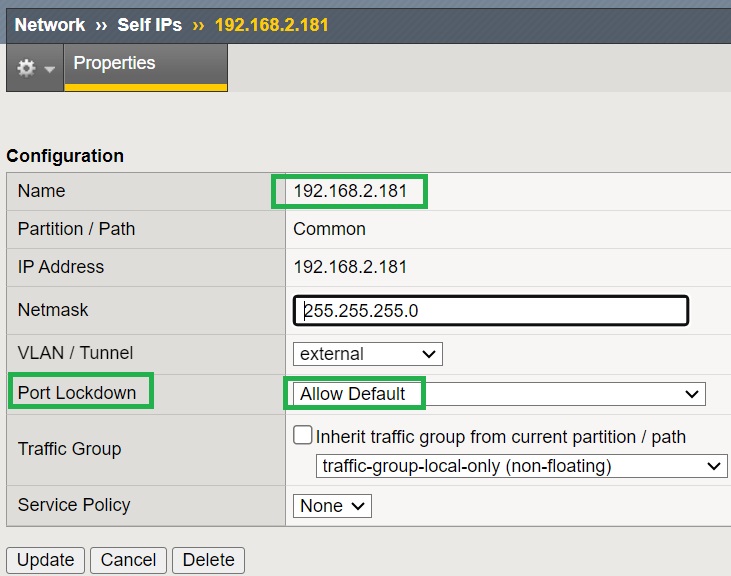
Enable port Lockdown as Allow Default
In my lab environment, I change “Port Lockdown” of the external interface to “Allow Default” to enable zone transfer and receiving name server change notifications in the external interface.
Selecting “Allow Default” will allow traffic with destination port 53 from both TCP and UDP on the external interface.
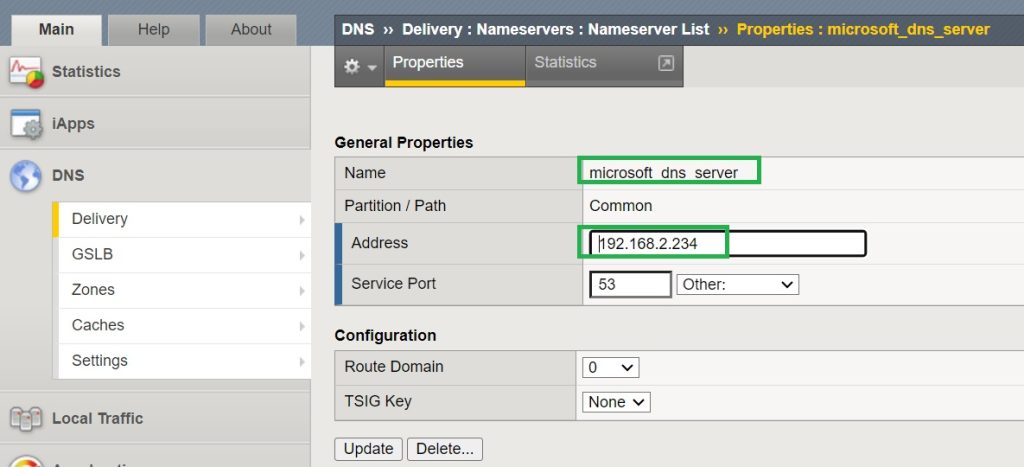
Add Microsoft name server in F5 DNS
In the next step we need to add the Microsoft name server to the F5 DNS name server list.
This is done in the “DNS > Delivery > Nameservers > Nameserver List” section.
Add a zone as a secondary zone in F5 DNS
Microsoft DNS server is the primary authoritative DNS server for the “rayka-co.com” domain. Now we add F5 DNS as a secondary authoritative DNS server for this domain in the F5 device.
Under “DNS > Zones > Zone List” section, we add a new zone for the domain “rayka-co.com”.
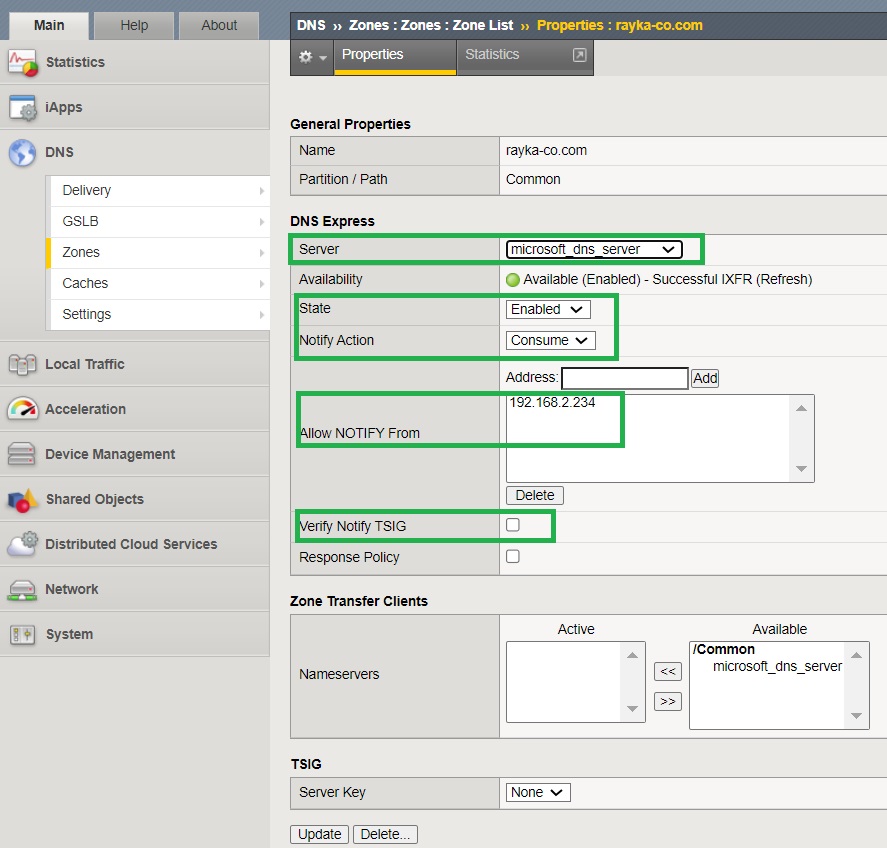
We add Microsoft DNS server that we have already configured, as the primary DNS server.
We choose “Consume” as the “Notify Action” to receive and use notifications of primary DNS server changes.
We add the primary DNS server address “192.168.2.234” as a server that is allowed to send notifications to F5 DNS.
We also uncheck “Verify Notify TSIG” so that receiving signed notification and zone transfer is not a requirement.
In the upcoming section, we will discuss how we can enable TSIG key for secure zone transfer between primary DNS server and F5 DNS Express feature.
When configuring the DNS Express zone, F5 DNS is expected to send a zone transfer request and the Microsoft DNS server sends the zone information to F5 DNS.
monitor and troubleshoot zone transfer
method1
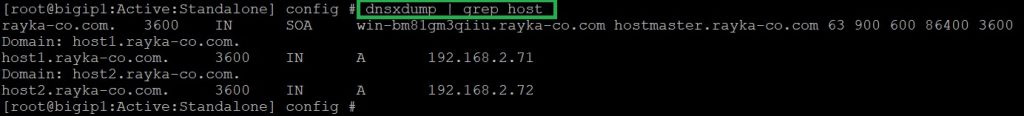
To ensure that zone information is transferred from the Microsoft DNS server to the F5 DNS, we can use the Linux shell command “dnsxdump” to see exactly what information is transferred.
To force the zone transfer, it is enough that we disable and re-enable the DNS Express zone in F5 DNS so that F5 DNS sends a new zone transfer request and the Microsoft DNS server sends zone information again.
[root@bigip1:Active:Standalone] config # dnsxdump ... Domain: . Domain: com. Domain: rayka-co.com. rayka-co.com. 600 IN A 192.168.2.234 rayka-co.com. 3600 IN NS win-bm81gm3qiiu.rayka-co.com rayka-co.com. 600 IN AAAA 2003:c1:373c:beb5:7364:5517:e858:a9cb rayka-co.com. 3600 IN SOA win-bm81gm3qiiu.rayka-co.com hostmaster.rayka-co.com 34 900 600 86400 3600 Domain: _msdcs.rayka-co.com. _msdcs.rayka-co.com. 3600 IN NS win-bm81gm3qiiu.rayka-co.com ... Domain: forestdnszones.rayka-co.com. forestdnszones.rayka-co.com. 600 IN A 192.168.2.234 forestdnszones.rayka-co.com. 600 IN AAAA 2003:c1:373c:beb5:7364:5517:e858:a9cb ... -= DB Stats =- RR Count: 24 Name Count: 33 RR Count by Type: A: 4 NS: 2 SOA: 1 AAAA: 4 SRV: 13 [root@bigip1:Active:Standalone] config #
method2
Another way to monitor and troubleshoot zone transfer is to monitor the output of the LTM log file located in “/var/log/ltm”.
We do this by using “tail -f /var/log/ltm” to display LTM real-time log information.
[root@bigip1:Active:Standalone] config # tail -f /var/log/ltm ... Nov 6 13:35:09 bigip1.rayka-co.local info systemd-journal[423]: Suppressed 99 messages from /system.slice/httpd.service Nov 6 13:57:17 bigip1.rayka-co.local notice zxfrd[6166]: 0153102c:5: AXFR Transfer of zone rayka-co.com with SOA Serial 34 from 192.168.2.234 succeeded. Nov 6 14:10:23 bigip1.rayka-co.local warning chmand[4311]: 012a0004:4: CHMAN request (from bigpcapq37B6-539) for tag:19 failed Nov 6 14:10:23 bigip1.rayka-co.local notice tmm[10887]: 013e0000:5: Re-enabling general logging; held 19 messages. Nov 6 14:10:23 bigip1.rayka-co.local notice tmm[10887]: 013e0000:5: Tcpdump starting locally on 127.1.1.1:2 from 127.1.1.254:57056 Nov 6 14:10:23 bigip1.rayka-co.local notice tmm[10887]: 013e000b:5: Tcpdump starting DPT providers:Noise Provider Nov 6 14:11:23 bigip1.rayka-co.local notice tmm[10887]: 013e0002:5: Tcpdump stopping on 127.1.1.1:2 from 127.1.1.254:57056 Nov 6 14:12:17 bigip1.rayka-co.local notice zxfrd[6166]: 0153102c:5: IXFR Transfer of zone rayka-co.com with SOA Serial 36 from 192.168.2.234 succeeded.
The output like „AXFR Transfer of zone rayka-co.com with SOA Serial XYZ from XYZ succeeded“, must appear in the output.
method3
The “tcpdump” utility is another method to ensure that zone information is transferred to the F5 DNS Express zone.
I use the command “tcpdump -nni external -s0 host 192.168.2.234 and port 53” to capture port 53 traffic to and from the Microsoft DNS server in the external F5 interface.
When you disable and enable the DNS Express zone, a new zone transfer occurs between the primary and secondary DNS servers.
[root@bigip1:Active:Standalone] config # tcpdump -nni external -s0 host 192.168.2.234 and port 53 ... 16:56:11.541085 IP 192.168.2.181.54002 > 192.168.2.234.53: Flags [S], seq 1738666053, win 29200, options [mss 1460,sackOK,TS val 2860489620 ecr 0,n op,wscale 3], length 0 out slot1/tmm0 lis= port=1.2 trunk= 16:56:11.541529 IP 192.168.2.234.53 > 192.168.2.181.54002: Flags [S.], seq 432401409, ack 1738666054, win 65535, options [mss 1460,nop,wscale 8,sac kOK,TS val 495294 ecr 2860489620], length 0 in slot1/tmm0 lis= port=1.2 trunk= 16:56:11.541731 IP 192.168.2.181.54002 > 192.168.2.234.53: Flags [.], ack 1, win 3650, options [nop,nop,TS val 2860489621 ecr 495294], length 0 out slot1/tmm0 lis= port=1.2 trunk= ...
method4
The command „show ltm dns zone rayka-co.com“ is another method to see if zone information is transferred between the primary and secondary DNS servers.
The output shows the number of records of different types transferred between two DNS servers.
root@(bigip1)(cfg-sync Standalone)(Active)(/Common)(tmos)# show ltm dns zone rayka-co.com | grep -A 3 Status
Status
Availability : available
State : enabled
Reason : Successful AXFR
root@(bigip1)(cfg-sync Standalone)(Active)(/Common)(tmos)#
root@(bigip1)(cfg-sync Standalone)(Active)(/Common)(tmos)# show ltm dns zone rayka-co.com | grep -A 5 "Resource Records" Resource Records (24 total) SRV 13 A 4 AAAA 4 NS 2 SOA 1 root@(bigip1)(cfg-sync Standalone)(Active)(/Common)(tmos)#
Primary DNS zone change notification
The other method is to add a listener in the F5 DNS to answer the requests from the “rayka-co.com” zone. Then we make requests and send them to the DNS Express zone. We expect that we get the correct answer.
Creating listener in F5 DNS will be discussed in the next section.
Primary DNS zone change notification
When the primary DNS server changes, we have configured it to send a dns notification to the secondary DNS server.
To make sure it works, we make a change to the primary Microsoft DNS server and then perform a tcpdump to ensure a notification is sent to the secondary DNS Express.
[root@bigip1:Active:Standalone] config # tcpdump -nni external -s0 host 192.168.2.234 and port 53
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on external, link-type EN10MB (Ethernet), capture size 65535 bytes 18:02:31.979167 IP 192.168.2.234.62387 > 192.168.2.181.53: 0 notify [b2&3=0x2400] [1a] SOA? rayka-co.com. (117) in slot1/tmm0 lis= port=1.2 trunk= 18:02:32.066448 IP 192.168.2.181.53 > 192.168.2.234.62387: 0 notify NotAuth- 0/0/0 (30) out slot1/tmm0 lis= port=1.2 trunk=
In the output of tcpdump we can see that a notification is sent to F5 DNS.
F5-DNS is expected to have sent a zone transfer request upon receiving a DNS change notification.
But in my lab environment, F5 DNS does not send a Zone transfer request to the Microsoft DNS server and I have to manually disable and re-enable the DNS Express zone to force a zone request to be sent.
At the time of writing, I couldn’t find a solution to this problem.
What we learn next
In this section, we learned how to implement F5 DNS as a secondary authoritative DNS server using DNS Express.
In the following section, you will learn how to create a DNS listener to query a second F5 DNS server.
We’ll learn how to use the local F5 BIND service as the primary authoritative DNS server and how to use the TSIG key for signed zone transfer between the primary and secondary DNS servers.