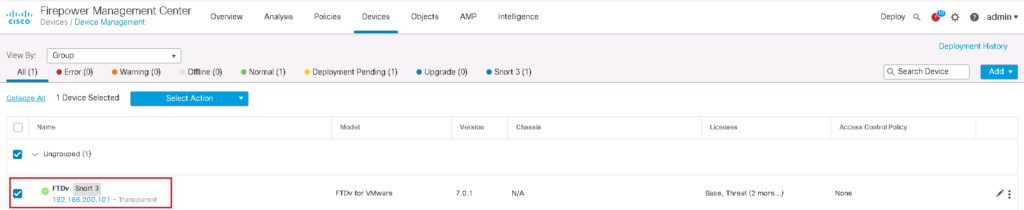
Cisco FTD Transparent Mode is another way of inserting a firewall in the network. In transparent mode, FTD is mostly like a switch and does not need an IP address to be assigned in each interface and also does not take part in the network routing.
Cisco Refrence: Transparent or Routed Firewall Mode for Firepower Threat Defense
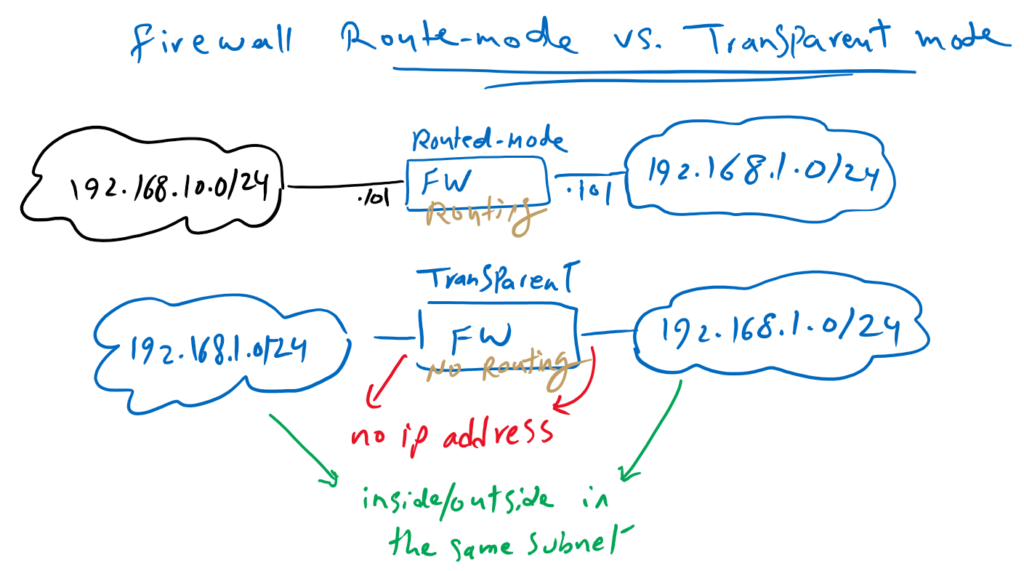
Cisco FTD Transparent Mode vs Routed Mode
In this Topology, I have tried to show the differences between firewall in routing mode or transparent mode.
So far we have implemented all our configurations in a firewall in a route mode. I selected routed mode for the firewall configurations since it is used more as a transparent mode. but the configurations are the same in both modes, except for a few points that I will point them out.
In routed-mode, firewall is configured like a router in the network. All interfaces must have an IP address and firewall must take part in traffic routing. Each interface in firewall is located in different subnet.
In our topology that we implemented from the beginning of the course, the inside interface is on the 192.168.10.0/24 subnet and the outside interface is on 192.168.1.0/24.
In transparent mode, firewall is configured like a switch and no IP address is assigned to any interface except for the firewall itself.
In our example, inside and outside interfaces are in the same subnet, 192.168.1.0/24, and traffic is switched (not routed) through the firewall for the inspection.
Cisco FTD Transparent Firewall Fundamental
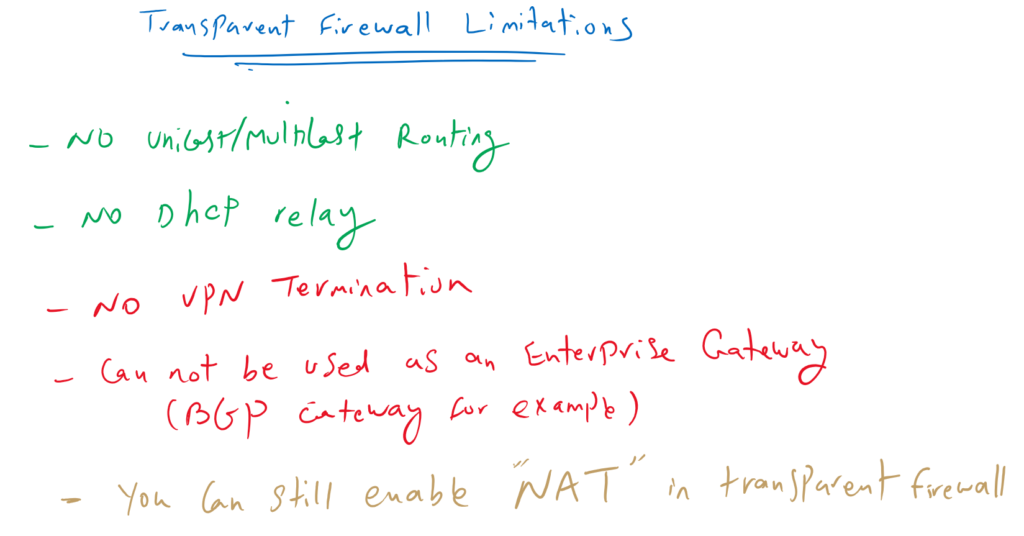
Cisco FTD Transparent Firewall Limitations
In a transparent firewall we have some limitations. But actually all of them are not always limitation but we do not need them at all. For example unicast and multicast routing is not supported in transparent firewall but sometimes it is not a limitation. We do not need them at all.
But some of them can be counted as a limitation. For example a firewall in routed-mode can also be used as a VPN server. but a firewall in transparent mode can not be a VPN server.
Firewall in a transparent mode cannot be used also as an Enterprise BGP gateway.
So depending on the application of the firewall, if it is used as Enterprise Gateway or just as a firewall in data canter, we can choose to use routed mode or transparent mode.
It is also interesting to know that you can still enable NAT feature in transparent mode firewall.
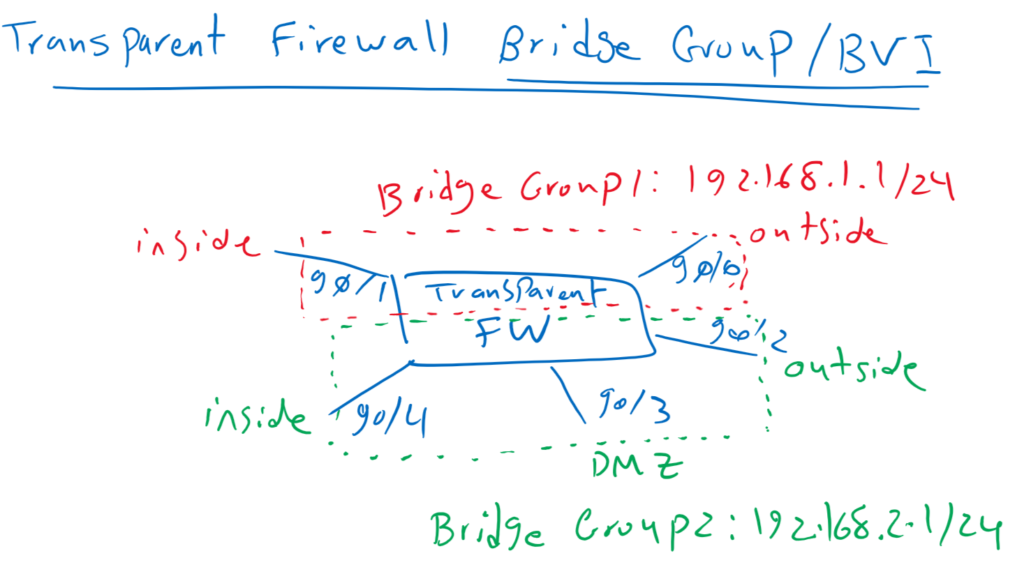
Bridge Group and BVI in Cisco FTD Transparent Firewall
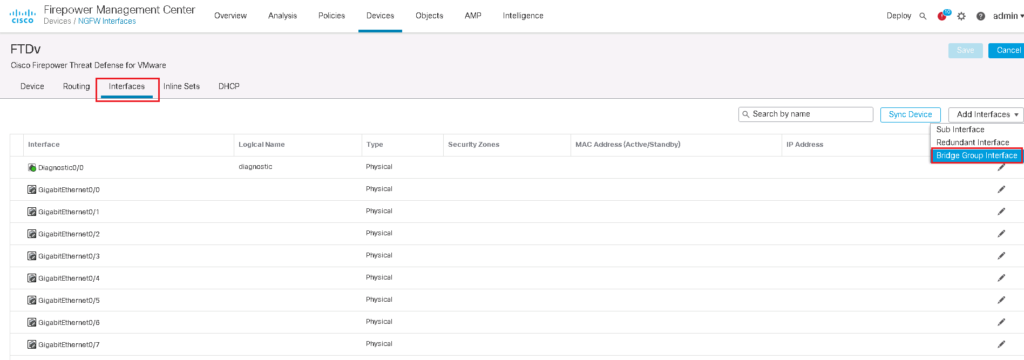
To implement transparent firewall, we have to configure bridge group and add interfaces in bridge group. Each bridge group is like one isolated switch. For each bridge group we have to configure a Bridge Virtual Interface (BVI). Firewall uses BVI IP address as the source address for packets originating from the bridge group. The BVI IP address must be on the same subnet as the bridge group member interfaces. you can create up to 250 bridge groups, with 4 interfaces per bridge group.
In our topology, we use our physical firewall as two transparent firewall with creating two bridge groups. GE0/0 and G0/1 are added to the first bridge group as inside and outside interface. First bridge group is used in datacenter as an example. The IP address of BVI Interface in the first bridge group is configured as 192.168.1.1/24.
Second bridge group includes three interface GE0/2, GE0/3 and GE0/4 as inside, outside and dmz zones. It will be used as enterprise edge firewall. The IP address of BVI Interface in the second bridge group is configured as 192.168.2.1/24.
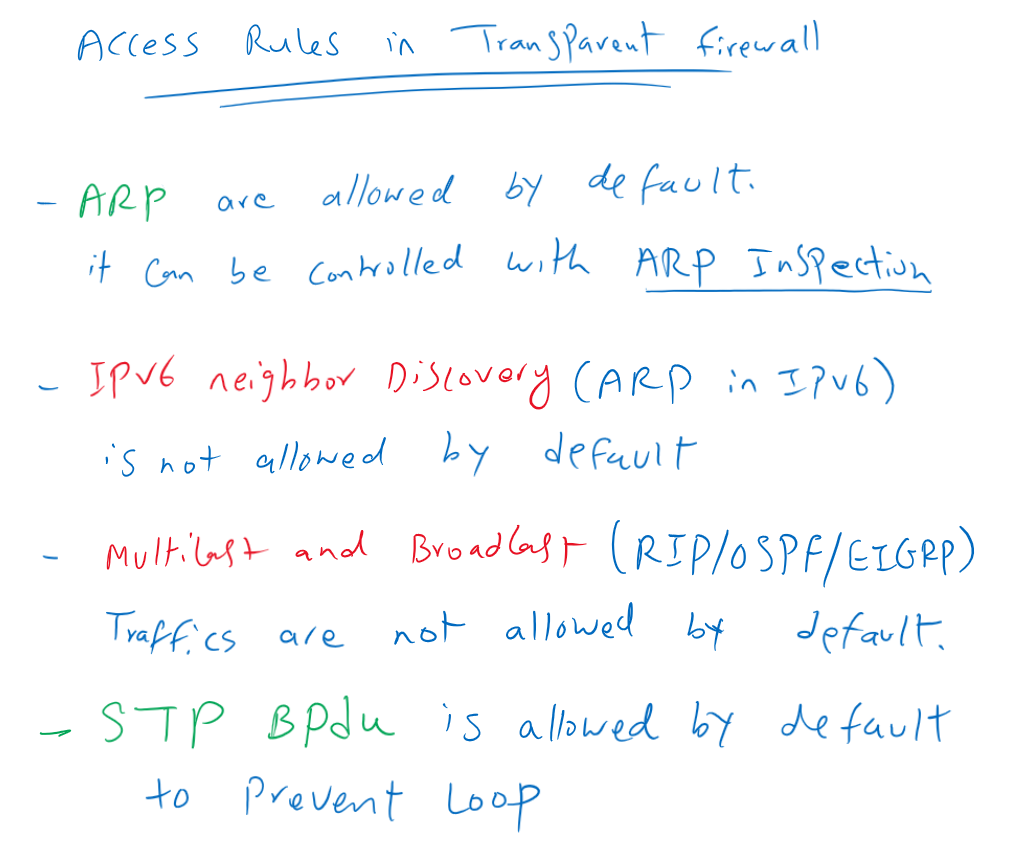
Access Rules in Cisco FTD Transparent Firewall
There are also some points regarding configuring access rules in transparent firewall. Notice that ARP is allowed by default in all directions in transparent firewall but it can be controlled by ARP inspection.
But notice that the equivalent of ARP in IPv6 (neighbour discovery packet) is not allowed by default and it must be allowed explicitly when required.
In addition to ARP, BPDU is also allowed by default to prevent any loop in the network.
Multicast and Broadcast packets are also not allowed by default. So routing protocols traffic are discarded by default and we have to permit them if two routers are neighbours over transparent firewall.
Cisco FTD Transparent mode Configuration
Currently our firewall is configured in routed-mode.
to change it to transparent firewall we have to take the following steps.
- Delete FMC manager in FTD and also FTD in FMC manager
- Configure FTD as Transparent Firewall
- Add FMC Manager in FTD and also FTD in FMC Manager
- Create Bridge Group and BVI in Transparent Firewall and Add interfaces in Bridge Group
- Configure Default Gateway in Bridge Group if required
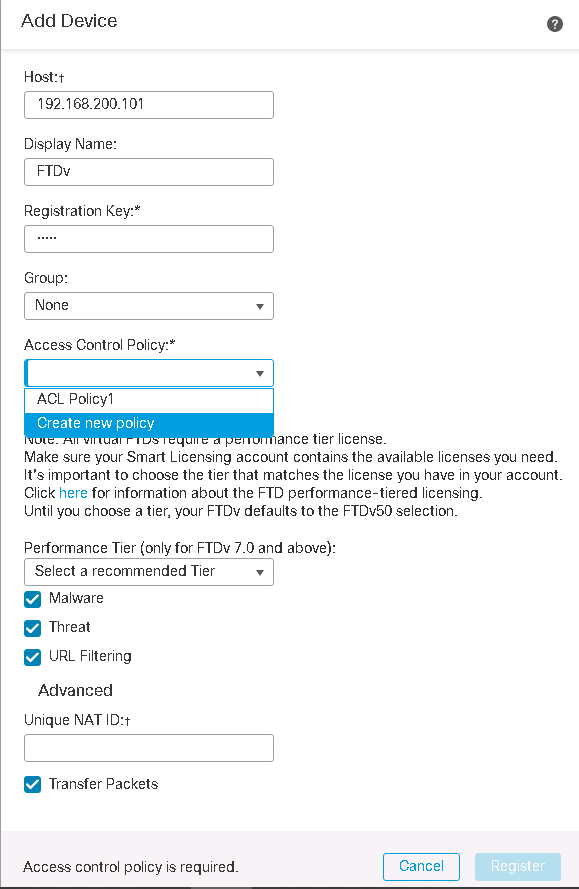
- Configure Access Control Policy and Rules
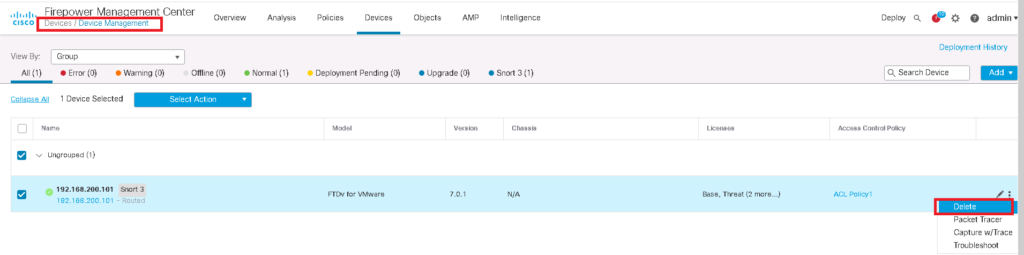
Delete FMC manager in FTD and also FTD in FMC manager
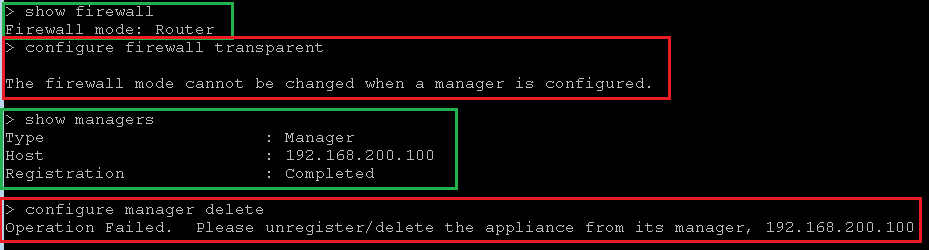
If you want to change the firewall mode from routed mode to transparent mode, you will receive error if it is already connected to FMC manager.
We have to isolate FTD and FMC from each other. First FTD must be removed in FMC and then FMC has to be removed in FTD.
> show firewall
Firewall mode: Router
> configure firewall transparent
The firewall mode cannot be changed when a manager is configured.
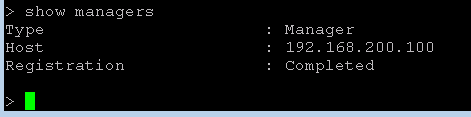
> show managers
Type : Manager
Host : 192.168.200.100
Registration : Completed
> configure manager delete
Operation Failed. Please unregister/delete the appliance from its manager, 192.168.200.100Configure FTD as Transparent Firewall
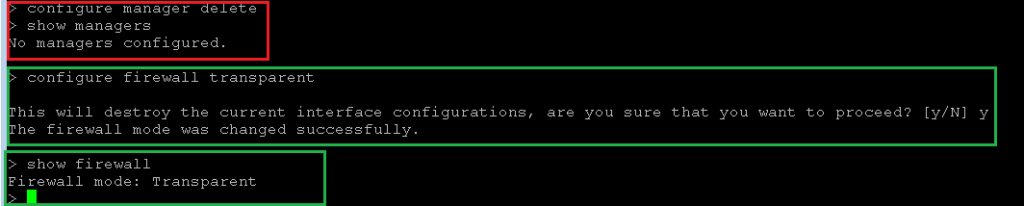
Now that we have isolated FMC and FTD from each other, with “configure firewall transparent” command, we change the firewall from routed mode to transparent mode.
With “show firewall” command, we can check if the firewall is in transparent mode or routed mode.
# after deleting FTD from FMC
>
> configure manager delete
> show managers
No managers configured.
> configure firewall transparent
This will destroy the current interface configurations, are you sure that you want to proceed? [y/N] y
The firewall mode was changed successfully.
> show firewall
Firewall mode: TransparentAdd FMC Manager in FTD and also FTD in FMC Manager
After changing firewall mode to transparent mode, now we connect FMC and FTD once again to each other.
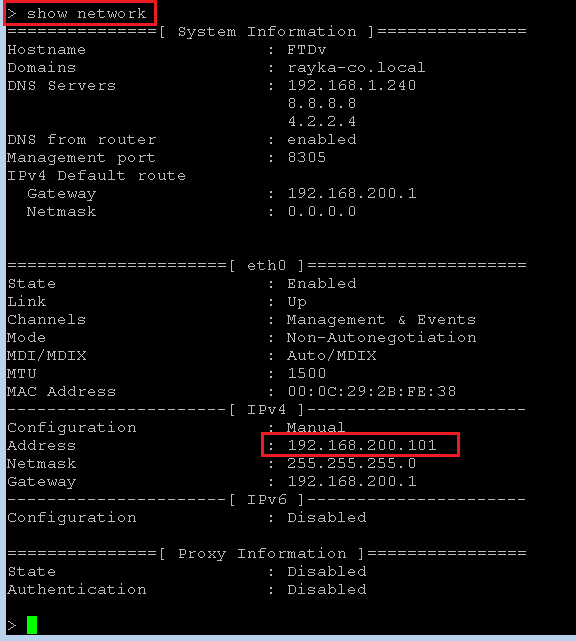
Before that, let’s review FTD network configuration that we have configured in initial step.
With “show network” command, all initial configurations are displayed.
> show network
management-data-interface Show configuration of management data interface
<cr>
> show network
===============[ System Information ]===============
Hostname : FTDv
Domains : rayka-co.local
DNS Servers : 192.168.1.240
8.8.8.8
4.2.2.4
DNS from router : enabled
Management port : 8305
IPv4 Default route
Gateway : 192.168.200.1
Netmask : 0.0.0.0
======================[ eth0 ]======================
State : Enabled
Link : Up
Channels : Management & Events
Mode : Non-Autonegotiation
MDI/MDIX : Auto/MDIX
MTU : 1500
MAC Address : 00:0C:29:2B:FE:38
----------------------[ IPv4 ]----------------------
Configuration : Manual
Address : 192.168.200.101
Netmask : 255.255.255.0
Gateway : 192.168.200.1
----------------------[ IPv6 ]----------------------
Configuration : Disabled
===============[ Proxy Information ]================
State : Disabled
Authentication : DisabledIf you remember, we have configured FTD OOB management interface with IP address 192.168.200.101 and FMC with IP address 192.168.200.100.
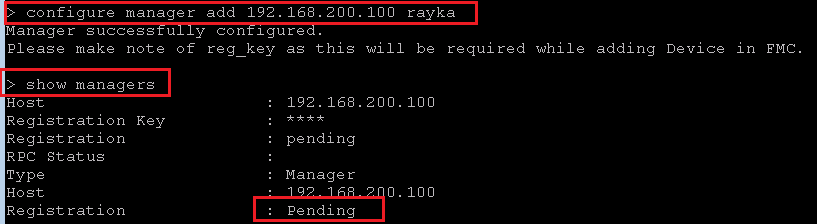
With “configure manager add” command, we add FMC in FTD. We also add FTD in FMC as we have learned in the lesson “2. Cisco FTD Installation Guide (Version 7.0.1)”.
> configure manager add 192.168.200.100 rayka
Manager successfully configured.
Please make note of reg_key as this will be required while adding Device in FMC.
> show managers
Host : 192.168.200.100
Registration Key : ****
Registration : pending
RPC Status :
Type : Manager
Host : 192.168.200.100
Registration : Pending
>> show managers
Type : Manager
Host : 192.168.200.100
Registration : CompletedCreate Bridge Group and BVI in Transparent Firewall and Add interfaces in Bridge Group
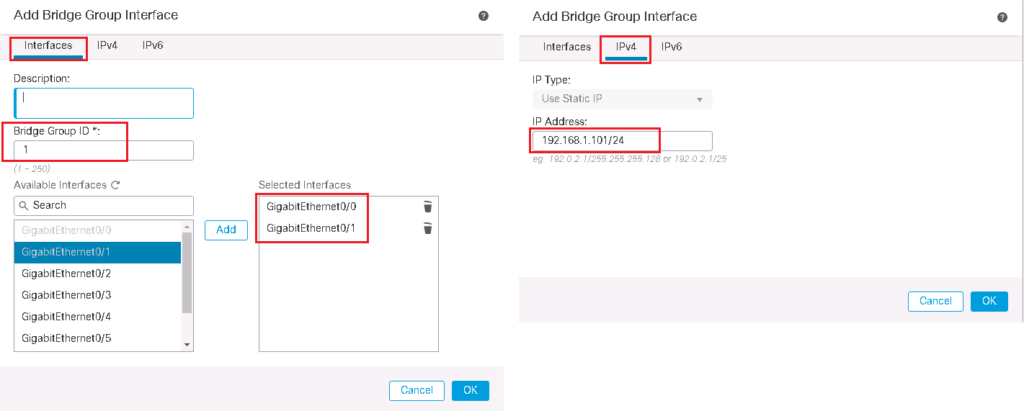
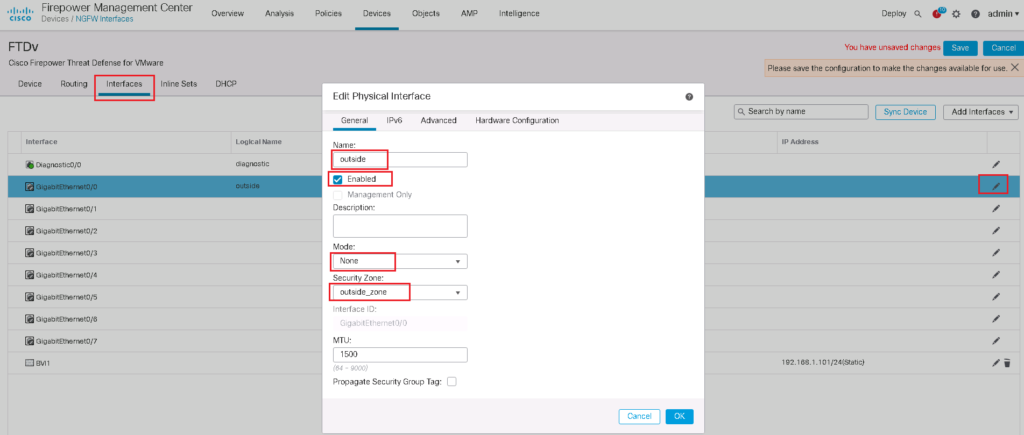
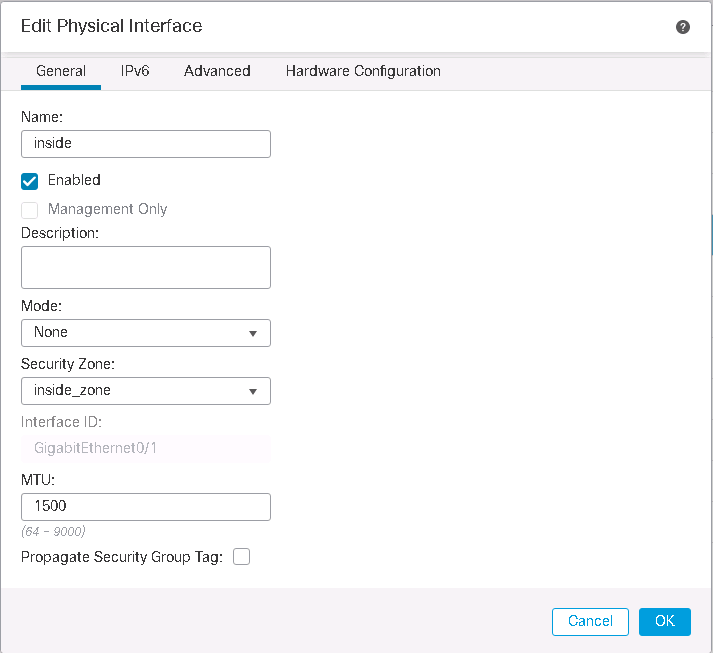
In the next step we will add bridge group and bridge virtual interface. We choose bridge group id 1. we add interfaces GE0/0 and GE0/1 into bridge group as outside and inside interface like what we have configured in routed mode.
The IP address of 192.168.1.101 Is assigned to BVI (bridge group virtual interface) which is in the same subnet as links connected to bridge group.
We have to also enable interfaces added to the bridge group.
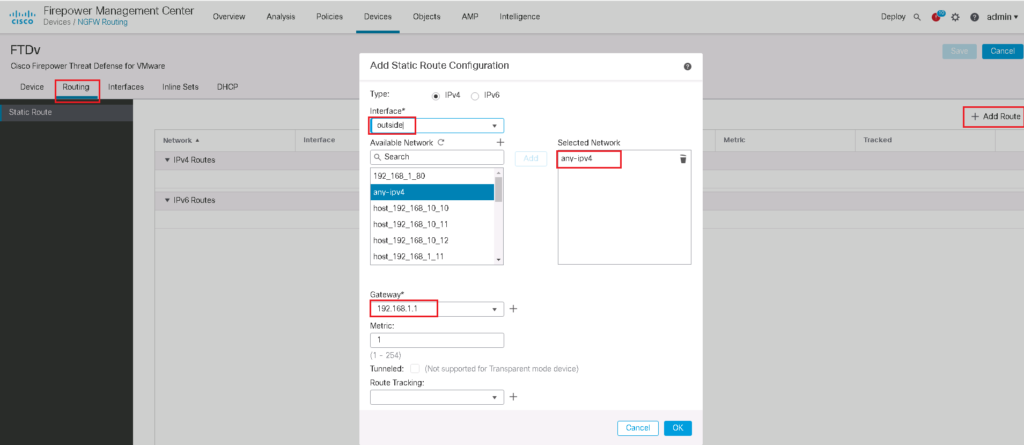
Configure Default Gateway in Bridge Group
If you need to have internet connectivity in FTD itself, we add default gateway into the bridge group.
Configure Access Control Policy and Rules
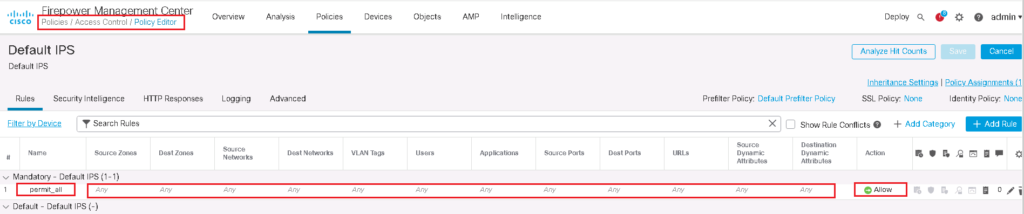
Then we add access control policy and rules like what we add in routed mode firewall except for a few differences.
Do not forget that in transparent firewall, ARP traffic and also BPDU are permitted by default. Broadcast and multicast traffic are not allowed by default.
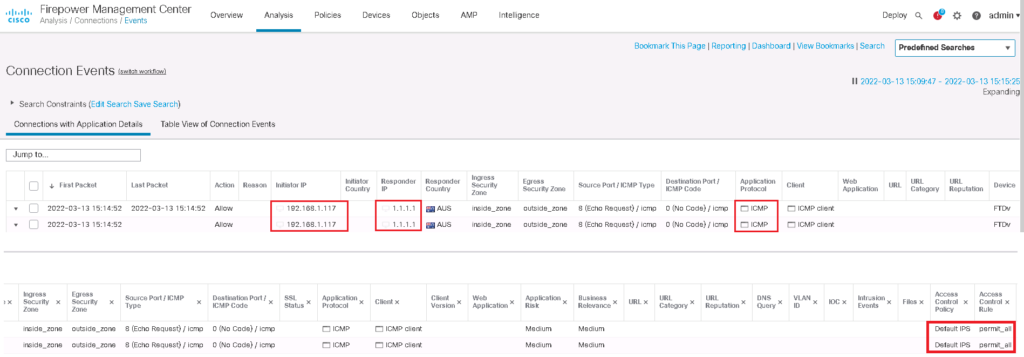
For our example I add a r ule to permit all traffic.
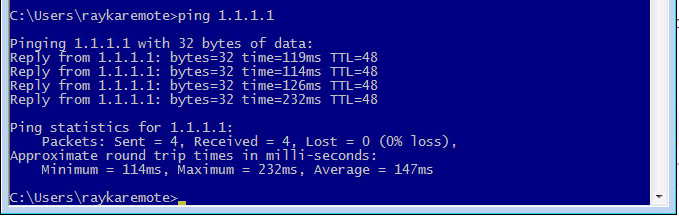
check connectivity over transparent firewall
To make sure that everything works as we expect, we check the connectivity from a computer in inside zone to a destination in outside zone.