Cisco FTD Network Discovery gives the capability to collects data on your organization’s network.
Which hosts exists on your network? IP address and MAC address of hosts on your network, operating system running on each host and also clients and web applications running on each host are the most important information retrieved by network discovery feature.
Network Discovery is not just for monitoring network traffic, but we can later predefine a host profile and then compare if any hosts on the network are violating the profile.
Cisco FTD Network Discovery Policy Configuration
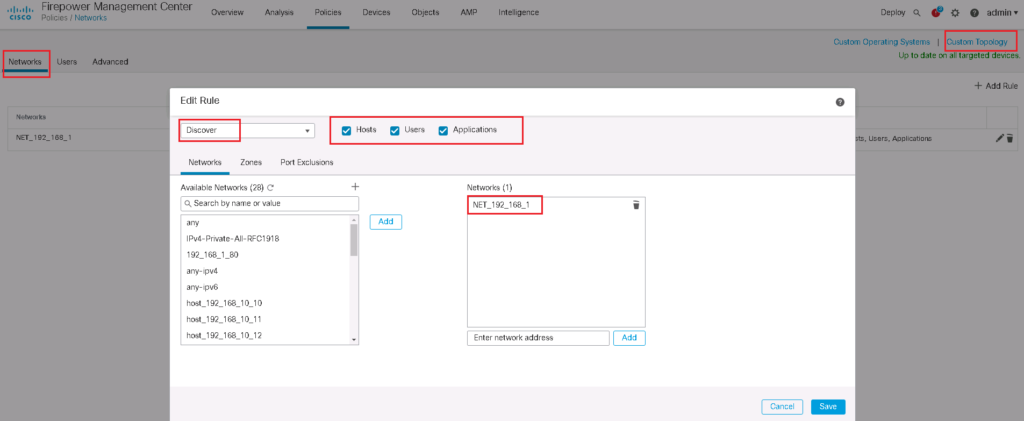
To create a discover rule, go to “Policies -> Network Discoveries -> Networks -> Add Rule”.
Through discovery rules specify which networks and ports to monitors to generate discovery data and the zones to which the policy is deployed. you can configure also whether hosts, applications, and non-authoritative users are discovered. You can exclude some networks and zones from discovery.
Users are discovered based on the protocols listed in users tab.
The option I change usually in the Advanced tab is to enable “Capture Banners” which monitor the header of protocols like FTP and Telnet to get user, OS and some other information.
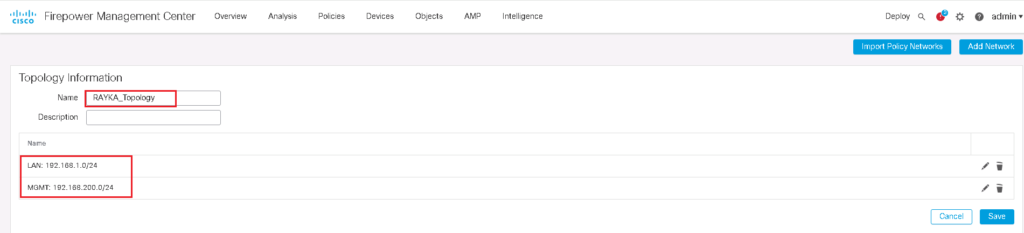
You can also give your topology information through custom topology tab.
Monitor Network Discovery MAP
In “Analysis -> Hosts -> Network Map”, you can monitor information based on hosts or based on topology.
Information can be discovered passive or active. With passive monitoring only traffic passing through the FTD is monitored but with active monitoring you can scan hosts by NMAP tool to discover more information.
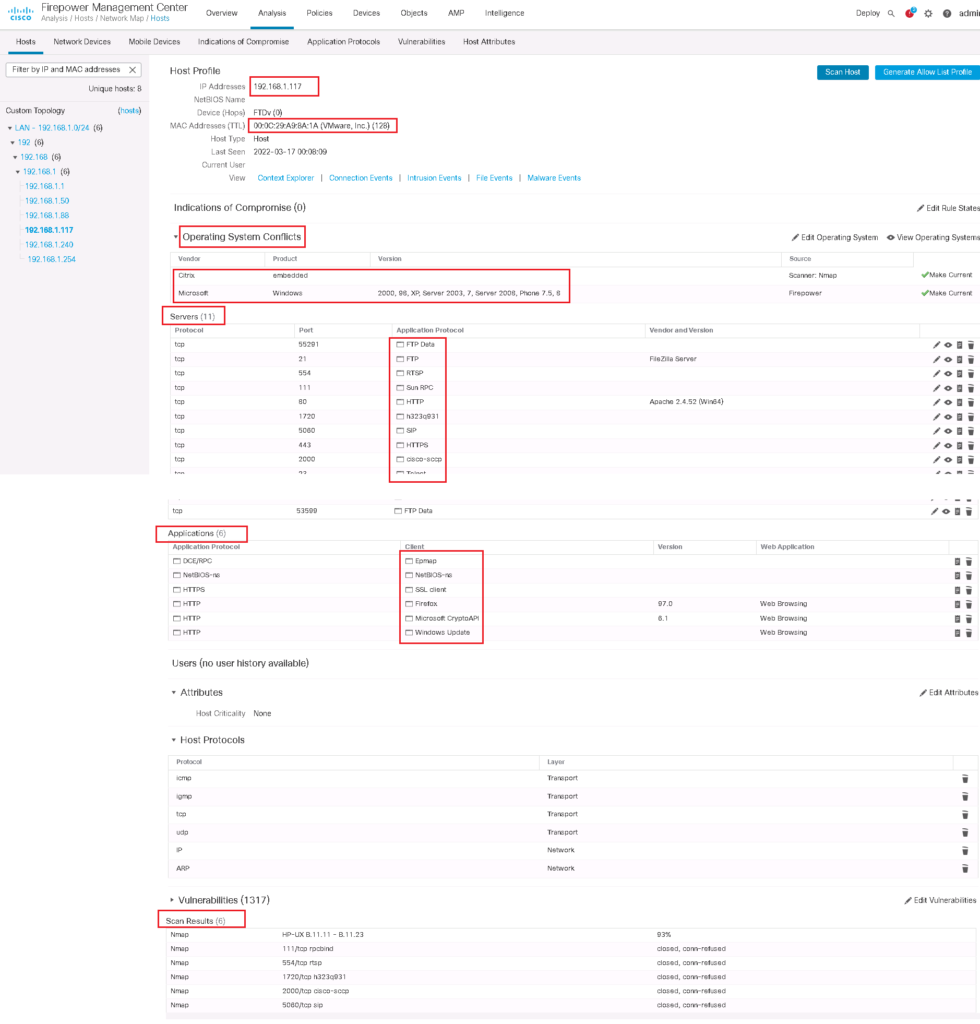
As you can see, discovered information is classified in a few main sections. Above you can see the IP address and MAC Address.
Then Operating System Information is displayed. it may gather information which cannot decide about operating system. It is named “Operating System Conflicts”. You can give the operating system manually by “Edit Operating System”.
In Server section, it list the services which the host listen on and the details of services. For example FileZilla FTP Server and Apache HTTP Server is displayed here.
In Applications section, you can monitor which applications are installed in the host.
In scan result section you can monitor information actively retrieved by NMAP. This section is displayed when NMAP is already active for the host
NMAP for Active Discovery
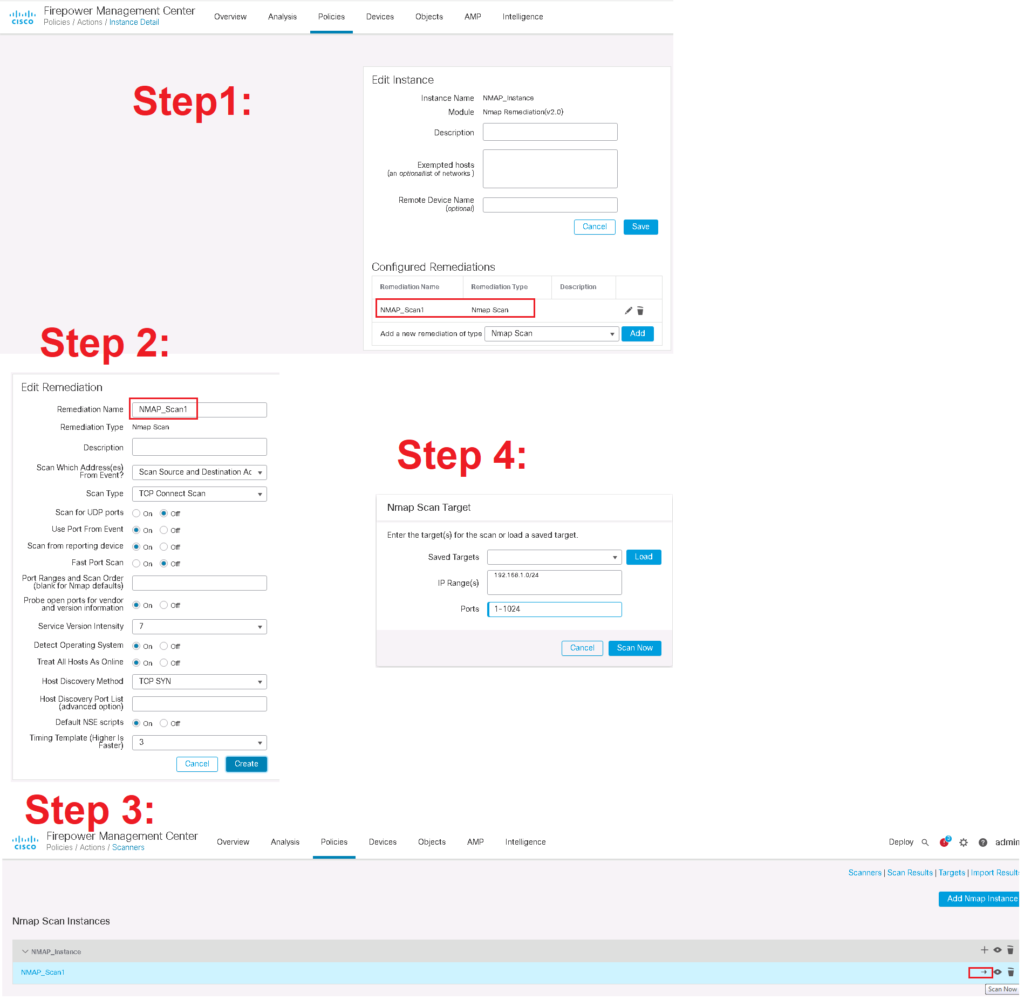
In “Policies -> Actions -> Scanners”, you can configure a new NMAP instance with specific parameters to scan a range of IP addresses.