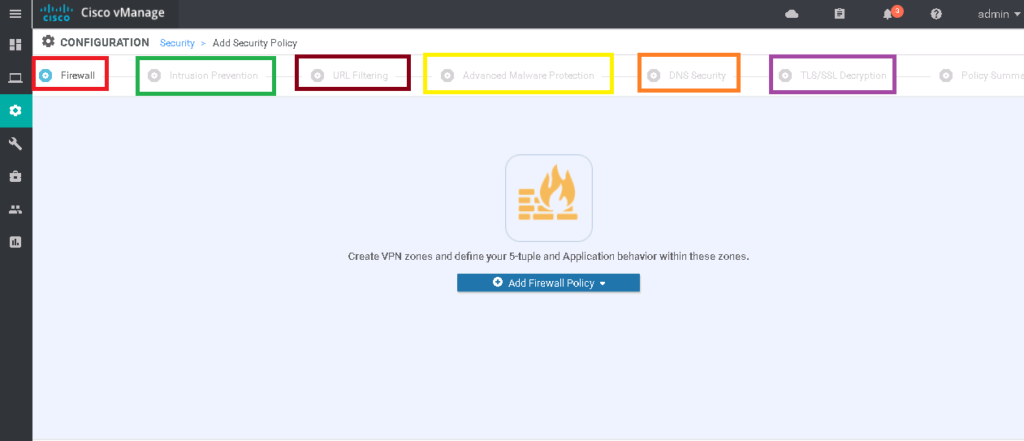
Cisco SD-WAN Security Policy offers us native built-in SD-WAN security features such as zone-based firewall, intrusion prevention system (IPS), URL filtering, anti-malware protection, DNS security and TLS/SSL decryption to be implemented directly in WAN edge routers.
Cisco SD-WAN Security Policy Oveview
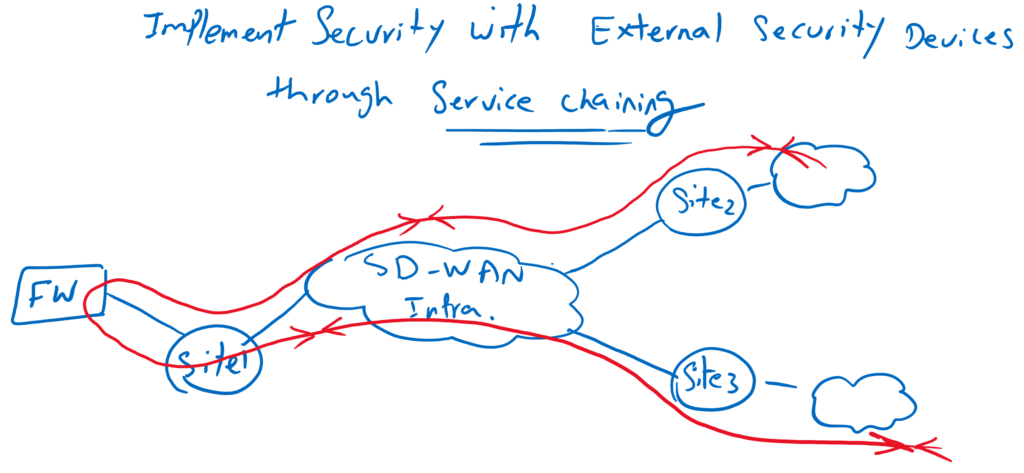
Cisco SD-WAN Service Chaining
In the previous section we learned how to bring and use non-SD-WAN security devices to secure SD-WAN traffic through service chaining.
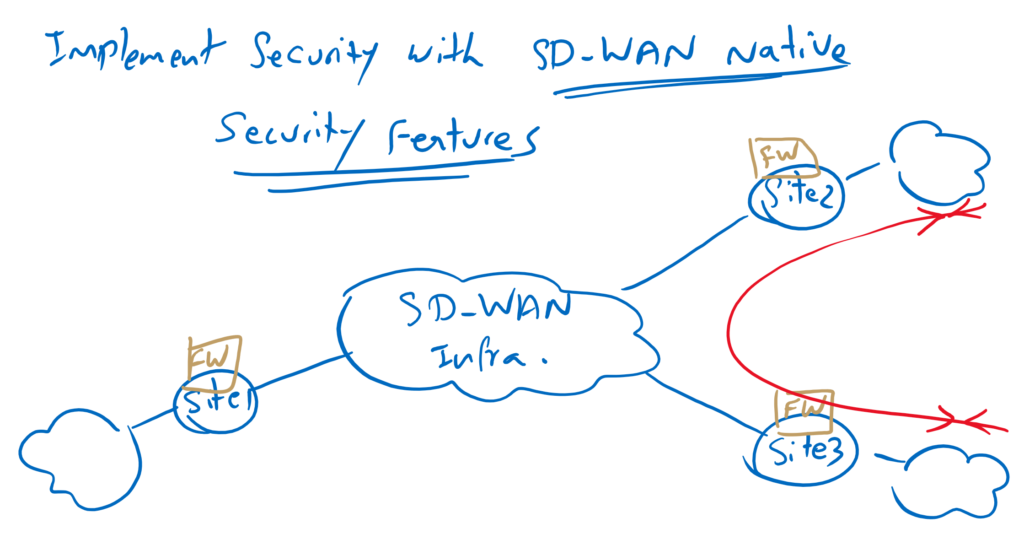
Cisco SD-WAN Native Security Features
However, a simpler design is to use native SD-WAN security features built into WAN edge routers. in WAN edge routers we have almost all of security features that are required in WAN edge routers. they are added in vManage through a “security application image file” and “advantage” license.
Cisco SD-WAN Security Policy Configuration
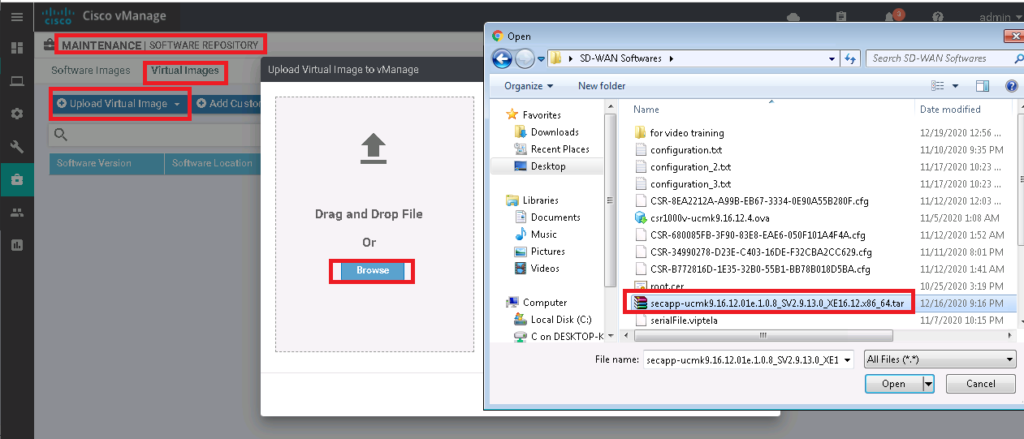
To start configuring, first we have to upload security application image through software repository.
MAINTENANCE -> SOFTWARE REPOSITORY -> Virtual Images -> Upload Virtual Image -> vManage -> secapp-ucmk9.16.12.01e.1.0.8_SV2.9.13.0_XE16.12.x86_64.tar
I am not going to test a specific scenario to show cisco SD-WAN security features since security concepts are independent of SD-WAN infrastructure. I just want to show how they are implemented in a Cisco SD-WAN environment.
First of all we need to make the lists that we will likely need to refer to them in security rules. As an example, I’ll create a ZONE list and a data-prefix list that are mostly needed to configure rules. Zoning is required to implement zone-based firewall.
CONFIGURATION -> SECURITY -> Custom Options -> Lists -> Zones -> New Zone List
Zone List Name: VPN10_ZONE
Add VPN: 10
Zone List Name: VPN11_ZONE
Add VPN: 11
!
!
CONFIGURATION -> SECURITY -> Custom Options -> Lists -> Data Prefix -> New Data Prefix List
Data Prefix List Name: NET_172_11
Add Data Prefix: 172.11.0.0/16
Data Prefix List Name: NET_172_16
Add Data Prefix: 172.16.0.0/16Zone-based Firewall
The zone-based firewall is certainly the most important security feature which is used in the SD-WAN infrastructure.
However, we have already implemented access list in Cisco SD-WAN environment, but the zone-based firewall is very different since it is stateful and we don’t have to inspect both directions.
as I have said earlier, for zone-based firewall, zoning is required. Firewall rules are applied in zone-pair. I will not discuss the details of zoning and zone-pair in cisco SD-WAN training.
Just as an example, I will add a rule in this section
CONFIGURATION -> SECURITY -> Add Security Policy -> Custom
!
Section: Firewall -> Add Firewall Policy -> Create New
Apply Zone Pairs
Source Zone: VPN11_ZONE
Destination Zone: VPN10_ZONE
Name: VPN11_to_VPN10_FW
Description: VPN11_to_VPN10_FW
Add Rules:
Default Action: Drop
Source Data prefix: NET_172_11
Destination Data prefix: NET_172_16
Destination Ports: 23
Protocol: 6 (TCP)
Log: SetIntrusion Prevention System
IPS is designed to detect and prevent intrusions into the network. We don’t have many options to fine-tune the IPS rules and signatures. We can only define how aggressively our IPS should be implemented. The default option is balanced. We also have the options “connectivity”, which is less aggressive in terms of security, and “security”, which is more aggressive.
We also have the option to configure whether potential intrusions only be detected and logged or be prevented, since there is always a false positive probability.
We also need to configure which VPNs need to be affected by each IPS rule.
Section: Intrusion Prevention -> Add Intrusion Prevention Policy -> Create New
Target
VPNs: 10,11
Policy Name: IPS_Balanced
Signature Set: Balanced
Inspection Mode: ProtectionURL Filtering
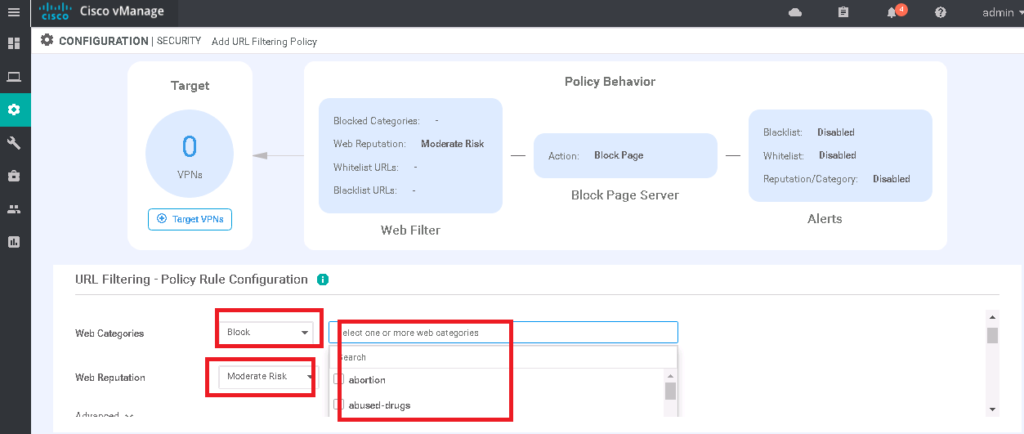
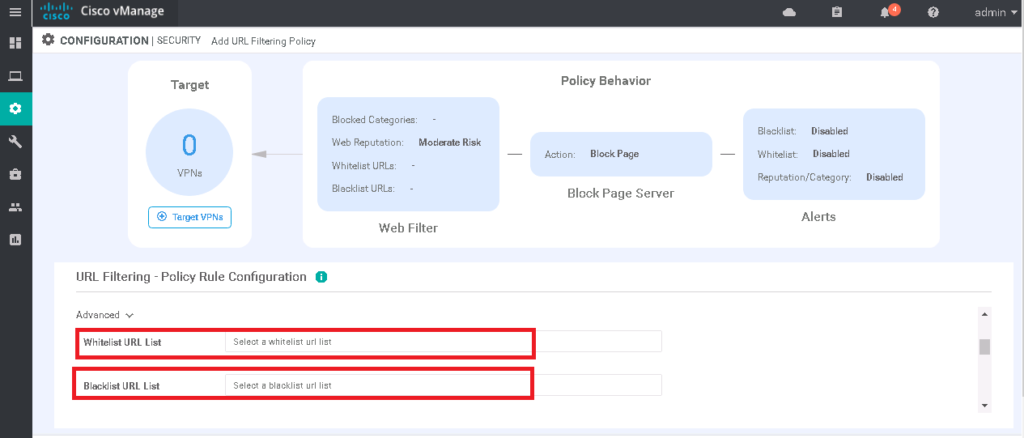
With URL filtering, you can permit or block based on web category or web reputation. Also we can control based on blacklist or whitelist that we may already configured in the list.
Apply Security Policy to Device
Also there are some other security features like anti-malware protection, DNS security and also SSL/TLS inspection which can be implemented in cisco SD-WAN infrastructure.
We have to choose a name for our policy then apply it to a device or group of devices through device template.
CONFIGURATION -> SECURITY -> Add Security Policy -> Custom
!
Section: Firewall -> Add Firewall Policy -> Create New
Apply Zone Pairs
Source Zone: VPN11_ZONE
Destination Zone: VPN10_ZONE
Name: VPN11_to_VPN10_FW
Description: VPN11_to_VPN10_FW
Add Rules:
Default Action: Drop
Source Data prefix: NET_172_11
Destination Data prefix: NET_172_16
Destination Ports: 23
Protocol: 6 (TCP)
Log: Set
!
Section: Intrusion Prevention -> Add Intrusion Prevention Policy -> Create New
Target
VPNs: 10,11
Policy Name: IPS_Balanced
Signature Set: Balanced
Inspection Mode: Protection
...
!
Section: Policy Summary
Security Policy Name: cEdge1_Security_Policy
Security Policy Description: cEdge1_Security_PolicyCONFIGURATION -> TEMPLATES -> Device -> CSR1000v_Device_Template_cEdge1 -> Edit
Section: Additional TEMPLATES
Security Policy: cEdge1_Security_Policy