What is F5 AWAF? This lesson explores the features of the F5 Advanced Web Application Firewall (AWAF), formerly known as ASM.
We will examine how this security solution provides web applications with comprehensive protection against a spectrum of cyber threats, particularly those listed in the OWASP Top 10.
Additionally, we will draw comparisons between the capabilities of F5 AWAF and an application firewall/IPS solutions as a network engineer, highlighting the unique advantages that F5 AWAF offers in the area of web security.
OWASP Top 10 and F5 AWAF security solution
First, we will examine the OWASP Top 10 cyber threats to understand the most critical security risks to web applications. Following that, we’ll delve into the features of F5 AWAF and discuss how it safeguards web applications against these prevalent threats.
OWASP Top Ten Security Threats
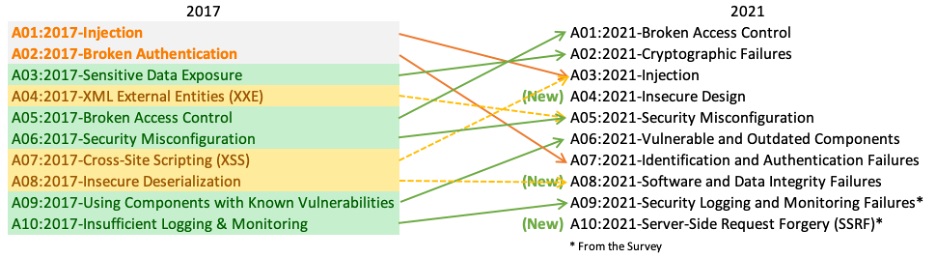
OWASP (Open Web Application Security Project) is a non-profit organization which is known for its OWASP Top 10, a list of the ten most critical web application security risks.
The latest version of the OWASP Top 10 is from 2021. The next update, the OWASP Top 10:2024, is currently in the data collection phase and is scheduled to be released in September 2024.
Let’s take a quick look at the top ten security threats classified by OWASP.
1. Broken Access Control: is a security vulnerability that occurs when a web application doesn’t properly enforce restrictions on what authenticated users are allowed to do. This means users might access data or perform actions they shouldn’t be able to, such as viewing sensitive files, modifying other user’s data, or accessing admin functions.
2. Cryptographic Failures: mean that sensitive data is not protected through encryption or other methods, which can lead to data theft or manipulation.
3. Injection: is sending untrusted data as part of a command or query in order to execute unintended commands or access unauthorized data. The most common example is SQL injection, where an attacker inserts malicious SQL commands into fields that expect user input, such as login forms or search boxes.
4. Insecure Design: This category is about errors in the design of software. Examples include storing credentials without proper security, exposing sensitive information through error messages, and failing to properly separate different areas of a program, which could potentially give attackers access beyond their privileges.
5. Security Misconfiguration: occurs when security settings are not properly defined, implemented, or managed, such as not patching known vulnerabilities, using the default configuration, enabling unnecessary ports, services, and pages and misconfiguring permissions.
6. Vulnerable and Outdated Components: refers to the use of outdated or vulnerable software components without updating and patching.
7. Identification and Authentication Failures: This involves weaknesses in user identity verification processes, which can allow attackers to impersonate legitimate users.
8. Software and Data Integrity Failures: refers to code and infrastructure that does not provide protection against unauthorized changes, which can lead to malicious code or data manipulation. Some examples include downloading code without verifying its integrity or not verifying data authenticity, which allows attackers to manipulate data.
9. Security Logging and Monitoring Failures: refers to a lack of logging and monitoring, which allows attacks to go unnoticed and breaches may not be detected in a timely manner.
10. Server-Side Request Forgery (SSRF): This occurs when an attacker can send crafted requests from a vulnerable web application to other systems, often leading to unauthorized actions.
F5 AWAF security features
Now let’s look at F5 AWAF’s security features to see how this solution can help protect against security threats.
In fact, there are many security features that help protect web applications, but I have listed some of them that will be discussed or implemented throughout the course.
Attack signatures: is a set of rules or patterns that identify potential known attacks on web applications. When traffic comes into the application, the system compares it against these signatures to detect malicious activities.
Geolocation enforcement (whitelist or blacklist): allows administrators to control access to web applications based on the geographic location (country) of the user.
IP intelligence (known malicious IP addresses): blocking client requests from IP addresses with known bad reputations. It utilizes a database maintained by Webroot’s IP Reputation service, which lists IP addresses identified for malicious activities such as attacks or exploits.
Cookie security: It prevents unauthorized changes to cookies. The most common example is to ensure that session cookies set by the web application are not modified on the client side.
Data Guard: Prevents leakage of confidential information from web applications. This involves scanning responses for sensitive information such as credit card numbers or social security numbers and either blocking or masking this information with asterisks (****). It can be configured to protect custom patterns using regular expressions to check specific file types or content types.
Login Enforcement: protect web applications from brute force attacks by monitoring and controlling access attempts. It tracks the number of failed login attempts and can block or challenge users based on predefined conditions. It also protect important pages to be accessed only by authenticated users.
File type protection: manage the types of files that can be uploaded to or from your web application.
URL protection: allows you to configure allowed or disallowed HTTP or HTTPS URLs in the security policy.
Parameter protection: In a web application, a parameter is a piece of data that can be passed between different parts of the application or between the client and server. Parameters are often used in the context of URLs, forms, or function calls within the application’s code. with this features it protects web application with enforcing checks on parameters against a set of rules for things like illegal parameter value length and illegal meta characters in values.
HTTP header and methods protection: ensuring that only legitimate and expected HTTP methods (like GET, POST, HEAD) and headers are used in requests.
Brute force protection: is designed to safeguard web applications from brute force attacks.The feature works by tracking the number of failed login attempts to configured login URLs. If the system detects a high rate of failed logins or a certain threshold is reached, it considers it an attack.
Cross-Site Request Forgery (CSRF) protection: These attacks exploit the trust a web application has in a user’s browser, tricking the browser into executing unwanted actions in a web application where the user is authenticated. The CSRF protection feature works by inserting custom JavaScript into response pages, which adds a unique token to each URI and form submission. This token must be present and valid for subsequent requests to be accepted by the server. If a request lacks the correct token, it’s considered a CSRF attack and is blocked, thereby preventing unauthorized commands from being executed.
XML and JSON protection: It ensures that the structure and content of XML and JSON requests comply with the expected format, preventing common attacks such as XML External Entity (XXE) and JSON threats. JSON Injection is a type of attack where malicious code is injected into JSON data. XML External Entity (XXE) occurs when an attacker exploits XML parser to include hostile external entities during the processing of XML documents.
User tracking: is monitoring and collecting data on user behavior and activities. This information is used to improve user experience.
Session tracking: It tracks user sessions using login pages, session IDs, or unique DeviceIDs for each client. This feature helps identify users or sessions that may be involved in an attack such as session hijacking.
Web scraping protection (extract data from websites): protect web applications from unauthorized data extraction methods using various methods such as bot detection, excessive session creation from a single IP address, or high data volume transfer.
DoS protection: is designed to protect web applications from denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks. It is based on monitoring transaction rates on the client side or latency on the server side, ensuring resource-intensive URLs are protected, using machine learning to learn application behavior, and continuously monitoring server health.
Positive/negative security model: negative secutity model allows all transactions except those identified as threats or attacks. It utilizes attack signatures to detect and prevent common vulnerabilities like web injections and cross-site scripting (XSS). Positive Security Model blocks all traffic by default, only allowing transactions that are known to be valid and safe. when used together, they can provide a robust defense for web applications against a wide range of security risks.
Audit logging and reporting: logs every significant event or change within the AWAF, which is essential for monitoring security events and can be critical for diagnosing problems.
Web App Vulnerability Scanner Integration: AWAF can integrate with various vulnerability assessment tools like HP WebInspect, IBM AppScan, and Qualys. It uses the results from these scanners to suggest updates to the security policy. In cases where Policy Builder decisions might conflict with scanner results, administrators have the flexibility to determine the final security policy settings.
Comparing F5 AWAF and an Application Firewall/IPS as a network Engineer
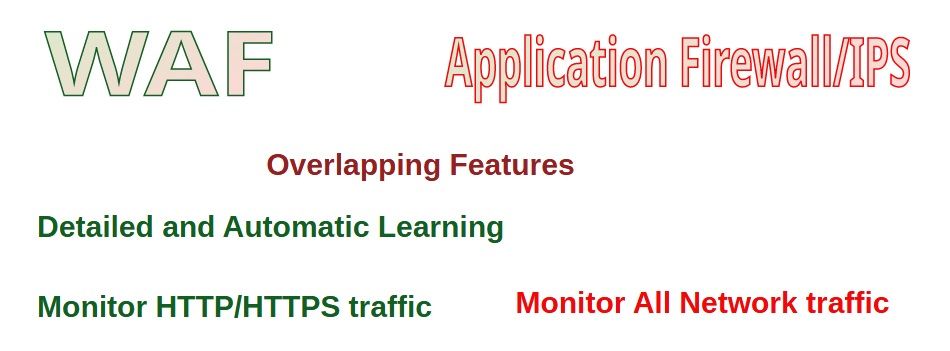
As a network engineer, you are probably interested to know the capabilities that a WAF device brings to our infrastructure compared to an application firewall/IPS. That is the difference I feel as the author of this article.
Both systems have overlapping features like attack detection based on attack signature, data leakage protection, IP intelligence, DoS protection, and file protection. However, the learning capability of F5 AWAF provides an additional layer of security by enabling it to respond to new and evolving threats with more agility.
This feature allows the AWAF to understand what constitutes normal traffic for a specific web application, which can include allowed URLs, file types, parameters, cookies, HTTP headers, HTTP methods and many other web application components.
The automatic learning of F5 AWAF considers several factors to determine the normal behavior of web application traffic. among them includes How often a particular type of request occurs, Whether the requests originate from inside or outside the network, likelihood of each request being an attack and the HTTP codes generated by the application in response to requests, which indicates the health and status of the application request.
On the other side, application Firewall/IPS monitors all network traffic but a WAF analyzes only HTTP/HTTPS traffic.