Juniper SRX VPN Cryptography understanding is the prerequisite to understand the IPsec VPN concept and configuration that we will discuss in the next sections.
In this section, we will have an overview of basic cryptography concepts such as encryption, authentication, and integrity.
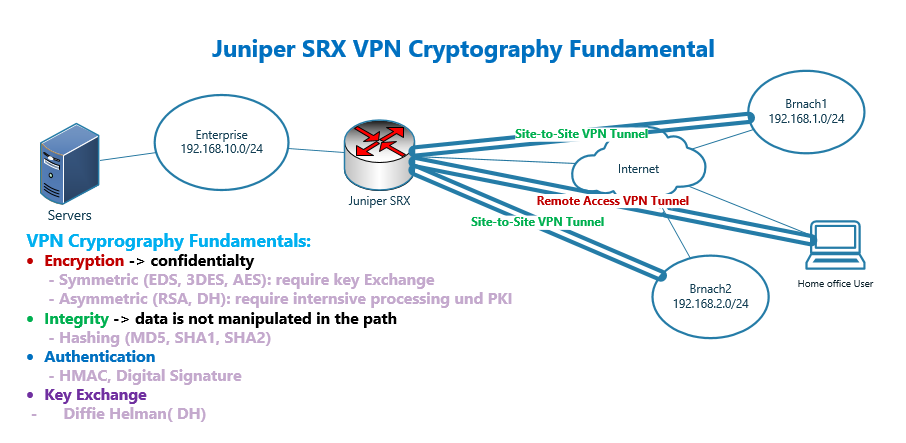
Juniper SRX VPN Cryptography Fundamental
Creating VPN connections is the most common solution to secure the connections over public transport such as the Internet.
VPN connection creates confidentiality to ensure traffic is not intercepted by unauthorized persons.
We can also make sure that the traffic are not manipulated on the path, ensuring data integrity.
In long-distance network communication, the other side of communication is ofcourse not beside us. the question is then how we can know who we are talking to? Peer and data origin authentication is the mechanism to ensure of the origin of the data and whether the correct sender is sending the data traffic.
With authentication we can also make sure that the content of traffic is not manipulated in the path. In other words, integrity of data is also guaranteed.
We have two types of VPN communication, site to site and remote access VPN.
With site-to-site VPN, communication between two or more locations in the enterprise are secured.
With remote access VPN, home office and telemetry users are securely connected to the enterprise from anywhere on the Internet.
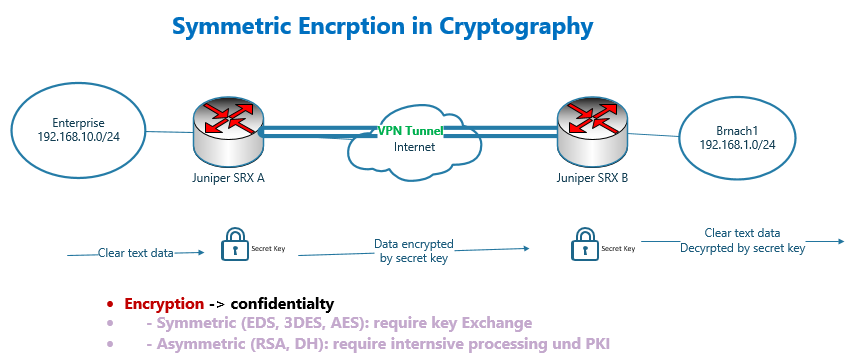
Creating Confidentiality with Encryption in Cryptography
As we have already explained, with confidentiality only authorized parties can read the content of the traffic and this is achieved by encrypting the traffic.
We have two types of encryption. Symmetric and asymmetric encryption.
Symmetric Encryption Algorithms
Usually, symmetric encryption is used to encrypt traffic because symmetric encryption algorithms are more efficient compared to asymmetric encryption algorithms.
DES, 3DES and AES are the most common encryption algorithms used in secure communications. DES is least secure and AES is the most secure method.
With symmetric encryption schemes, two sides of the communication must have the same key. The sender uses the key to encrypt the traffic and the receiver uses the same key to decrypt the traffic.
The “encryption/decryption key”, called “secret key” must be negotiated through a secure channel using key exchange algorithms, before starting secure communication.
We will talk about key exchange algorithms in a few minutes.
Asymmetric Encryption Algorithms
Asymmetric encryption is another type of encryption, which is less efficient than symmetric encryption.
The advantage of asymmetric encryption is that it does not require a secure channel for keys to be exchanged between parties. In other words, public key can be easily exchanged between parties.
Asymmetric encryption is not typically used to encrypt large amounts of data, but rather to encrypt small pieces of data, due to efficiency issue.
The most common application of asymmetric encryption are “key exchange” and “digital signature”, which we’ll talk about in a few minutes.
With asymmetric encryption, each side has its own public and private key. The property of these keys are important because whatever is encrypted with the public key is decrypted with its own private key and vice versa.
The public key is not secret and can easily be transmitted without a secure channel, but the private key must be protected.
The data is encrypted using the other party’s public key, therefore only the other party can decrypt the data using its own private key, which is protected by itself.
RSA and DH are the most common asymmetric encryption algorithms.
DH or “Diffie Helman” is used to negotiate and exchange secret keys, which will be used in symmetric encryption.
RSA is mostly used to generate Digital Signature which is used in peer and data origin authentication.
In a few minutes, we will talk more about these two concepts.
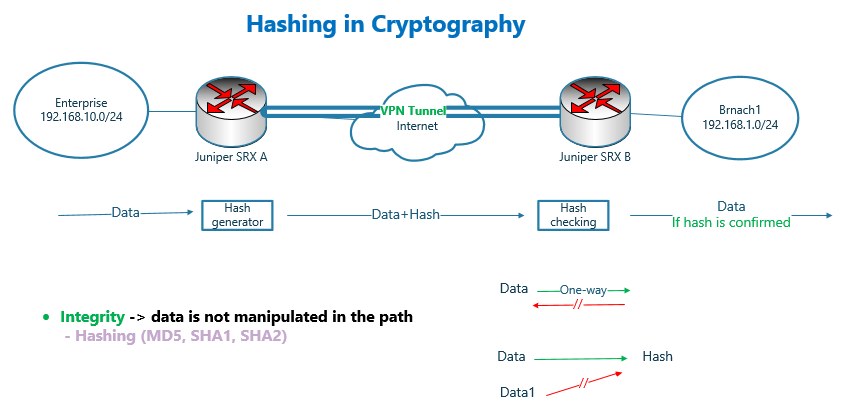
Integrity in Cryptography
What is integrity in cryptography?
In remote secure communication, it is not only important to encrypt data to ensure it cannot be intercepted by unauthorized users, but it is also important to know what we are receiving and what is being sent are the same and data has not been changed on the path.
In other words, integrity of data must be guaranteed.
It is done through hashing algorithm. MD5, SHA1 and SHA2 are the most common hashing algorithms. MD5 is the least secure and SHA2 is the most secure hashing algorithm.
To ensure the integrity of the data, a hash of the data is generated and added to the data. The receiver recalculates the hash of the data and compares it to the attached hash. If they match, it means data on the path is not being manipulated.
What is hash? Hash is a small piece of data generated based on data. But it has some special properties.
One of the most important property is that with a given data and hash it is not easy or somehow impossible to generate other data with the same hash.
Or the other property of the hash is that the hash is one-way. This means that we cannot retrieve the data itself from the hash.
If you are thinking that an attacker can easily alter the data and replace the hash with a new hash, receiver may not notice that the data has changed.
You think absolutely right. In a few minutes you will see the solution.
Authentication in Cryptography
Authentication is another important concept in cryptography which gives two main services.
First we can make sure who is on the other side of the communication and also make sure that data really comes from another side of the communication and no one else is inserting data into the communication channel. This is called “peer authentication” and “data origin authentication”.
Second, we can ensure that data in the path is not manipulated. Since integrity alone could not handle it for us. And the attacker could change both data and hash at the same time without noticing the receiver. This is called “data integrity”.
How is it implemented? There are two main methods. HMAC and Digital signature.
HMAC is based on “Hashing algorithms” and also an “authentication key”. Notice that authentication key is a different key than secret key which we use in symmetric encryption.
Authentication with HMAC
How authentication is implemented with HMAC?
Instead of calculating hash based on only data, in HMAC, hash is calculated based on the mixture of data and authentication key.
And then data is sent along with the hash value and without authentication key.
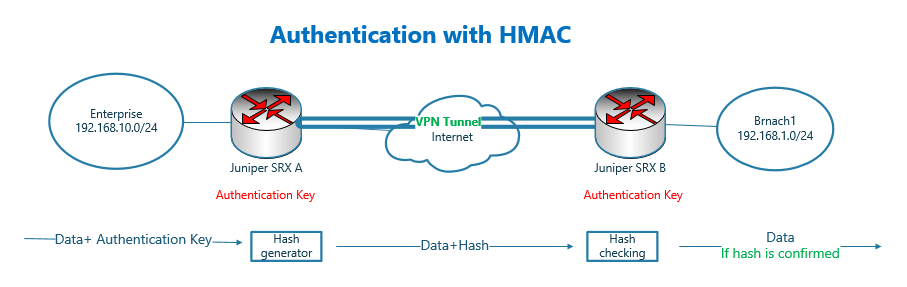
In the receiver, the hash is again recalculated in the same way and compared to the attached hash. If they are the same, it means the data in the path has not changed. It also means that the data comes from the originating sender since he has the authentication key.
The problem of HMAC is that both party must know the authentication key beforehand. Usually “authentication key” is configured manually in both parties.
based on hashing algorithm used in HMAC the name of authentication method is called, HMAC-MD5 or HMAC-SHA1.
Notice that “authentication key” is different from “secret key” which is used in symmetric encryption. “Secret key” is negotiated dynamically through Diffie-Helman Algorithm. But “authentication key” is usually configured manually.
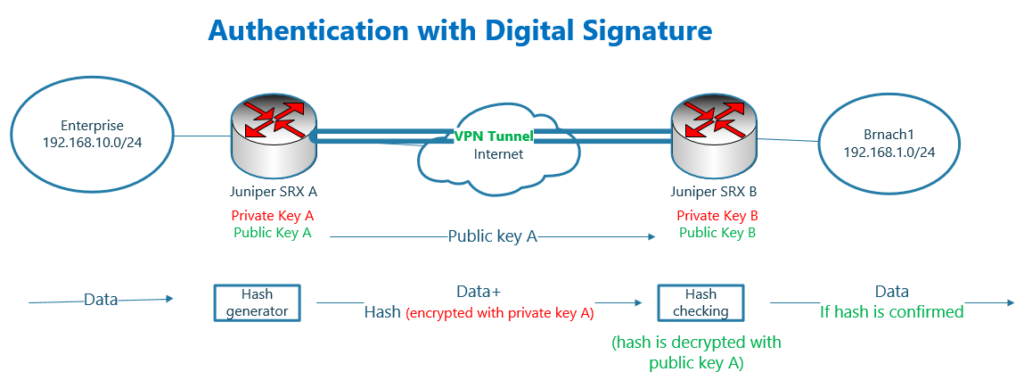
Authentication with Digital Signature
The other method of authentication is to use “digital signature”. Actually, this is the best authentication method, but due to the complexity of implementation, it is used in more professional organizations.
It is complex because it requires PKI infrastructure.
With digital signature, hash is calculated only based on data. Then the hash is encrypted with sender private key. Hash encrypted with sender private key is called “digital signature”.
Data along with digital signature is send through the network. The receiver, decrypt the attached hash with sender public key. Recalculate the hash and compare it with decrypted hash.
If they match, then it shows that data is not manipulated on the path. It also means that data is coming really from originating sender. Because the hash is decrypted with sender’s public key and the equivalent private key can only be with the sender.
With this method, the sender’s public key is sent via a certificate, which requires a PKI infrastructure and the discussion is outside the scope of this section.
Key Exchange in Cryptography
Key exchange is another important basic concept in cryptography.
Key exchange and negotiation is required in symmetric encryption, where both parties need the same key and the key needs to be updated periodically.
The Diffie-Hellman algorithm, which uses an asymmetric encryption scheme, is used to negotiate and update the secret key used in symmetric encryption.
This algorithm has many versions and group 2 and group 5 are usually used for IPsec VPN communication.