Juniper SRX IDP (Intrusion Detection and Prevention) gives the capability to inspect network traffic to make sure that they are not malicious or intrusions.
In this section we will learn how to download and install IDP signatures and how they are used in security policies.
Juniper SRX IDP Fundamental
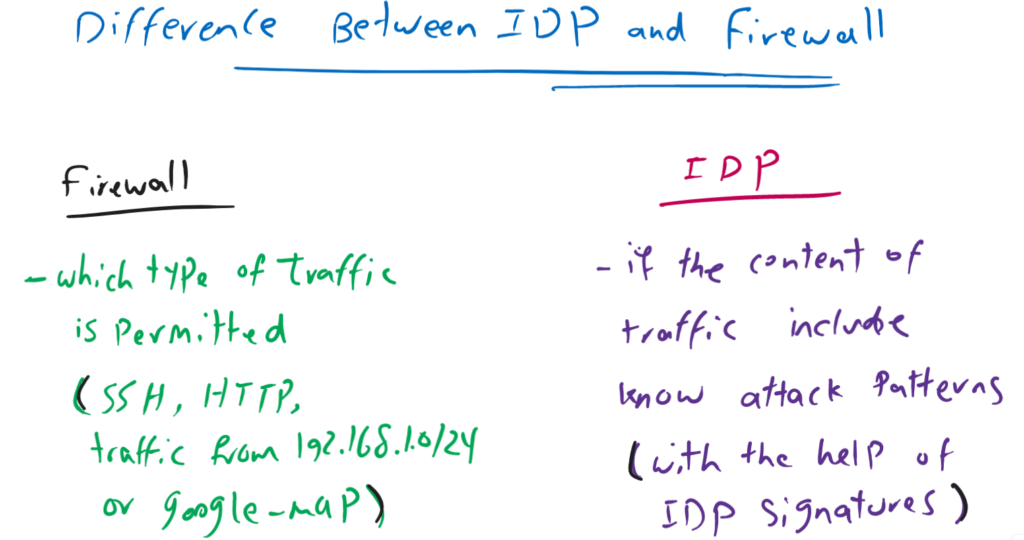
As the first point, you may ask, what is the difference between Firewall and IDP feature.
By Juniper SRX firewall, that we have learned in the previous section and implemented through security policies, you can configure which type of traffic are allowed or not allowed to be forwarded. But you cannot make sure if they are healthy or malicious.
But Juniper SRX IDP feature inspect the traffics to make sure that they don’t include known attack pattern which are already provided by Juniper as IDP signatures.
As an example, to better understand the difference between Firewall and IDP, suppose that firewall permit SSH Traffic, HTTP traffic, traffic originated from a specific subnet or a specific micro-application like google-map.
But the firewall cannot make sure if the content of these traffic are malicious or healthy. This is exactly what IDP want to detect with the help of IDP signatures.
IDP signatures include , known attack patterns and they are updated periodically exactly like antivirus.
Both firewall and IDP are implemented through Juniper SRX security policies, that we will see in a few minutes.
Juniper SRX IDP Configuration
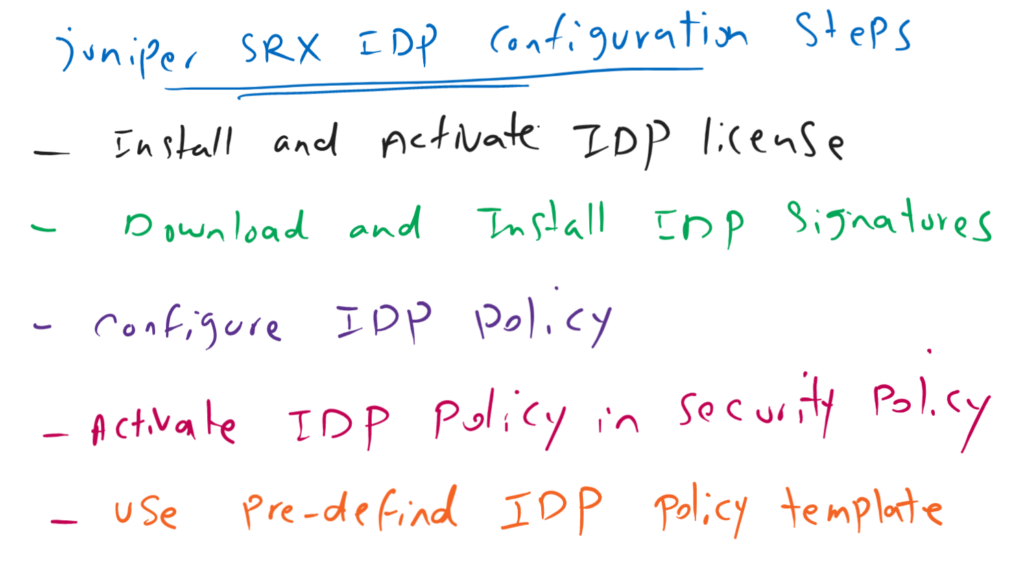
For the configuration of Juniper SRX IDP, we have to first enable IDP license. Download and Install IDP signatures. Configure IDP policies and activate IDP policies in security policies.
Actually it is not easy to configure an IDP policy. because of that, we can use pre-defined IDP policy template and customize them whenever necessary. This is also what we will see in this section.
Juniper SRX IDP License check
For the first step of IDP configuration, you have to make sure that you have the required IDP licanse.
With the command “request system license add terminal”, you can install the license.
With the command “show system license”, you can make sure that the license is installed and valid.
rayka# run show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 30 days
idp-sig 0 1 0 30 days
appid-sig 1 1 0 26 days
av_key_sophos_engine 0 1 0 30 days
wf_key_websense_ewf 0 1 0 30 days
Virtual Appliance 1 1 0 35 days
remote-access-ipsec-vpn-client 0 2 0 permanent
remote-access-juniper-std 0 2 0 permanent
Licenses installed:
...Download and Install Juniper SRX IDP Signatures
For the next step, we have to download and install IDP signatures.
With the command “request security idp security-package download check-server”, we check if juniper server is available to download signatures.
With the command “request security idp security-package download”, you can start to download the signatures.
With adding “status” keyword at the end of download command, you can check the status of download progress.
After downloading, with the command “request security idp security-package install”, you can install download signatures.
And finally with adding “status” keyword at the end of install command, you can check the status of installation progress.
rayka# run request security idp security-package download check-server
Successfully retrieved from(https://signatures.juniper.net/cgi-bin/index.cgi).
Version info:3516(Detector=12.6.130200828, Templates=3516)
[edit]
rayka# run request security idp security-package download
Will be processed in async mode. Check the status using the status checking CLI
[edit]
rayka# run request security idp security-package download status
In progress: Downloading ...
[edit]
rayka# run request security idp security-package download status
Done;Successfully downloaded from(https://signatures.juniper.net/cgi-bin/index.cgi).
Version info:3516(Tue Aug 9 14:15:29 2022 UTC, Detector=12.6.130200828)
[edit]
rayka# run request security idp security-package install
Will be processed in async mode. Check the status using the status checking CLI
[edit]
rayka# run request security idp security-package install status
In progress:Installing AI ...
[edit]
rayka# run request security idp security-package install status
Done;Attack DB update : successful - [UpdateNumber=3516,ExportDate=Tue Aug 9 14:15:29 2022 UTC,Detector=12.6.130200828]
Updating control-plane with new detector : successful
Updating data-plane with new attack or detector : not performed
due to no active policy configured.Configure SRX IDP Policy
To configure your custom IPS policy, first we have to create an IDP policy and then activate it in any of security policy rules.
It is not easy to create an IDP policy. to see why, let’s try it together and then see then what is the solution.
With the command “set security idp idp-policy TEST rulebase-ips rule 1”, we can start to create the first rule of a new policy with the name of TEST.
As security policy, “match” and “then” keywords are the most important parameters in each rule in IPS policy.
rayka# set security idp idp-policy TEST rulebase-ips rule 1 ?
Possible completions:
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
description Rule description
> match Rule match criteria
terminal Set/Unset terminal flag
> then
rayka# set security idp idp-policy TEST rulebase-ips rule 1 match ?
Possible completions:
application Specify application or application-set name to match
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
> attacks Match attack objects
+ destination-address Match destination address
+ destination-except Don't match destination address
from-zone Match from zone
+ source-address Match source address
+ source-except Don't match source address
to-zone Match to zoneJuniper SRX IDP Policy, “match” options
With “match” keyword, we can match the traffic based on source and destination zone, source and destination IP address and source and destination IP address except. “except” is used when we want to ignore some addresses from being inspected by the rule. For example IP address from NOC or SOC machines.
We can also match based on attacks pre-defined in signatures or custom attacks. We have to configure “match attacks predefined-attacks ?”, to see the list of attacks.
There are thousands of pre-defined attacks or attack-groups. It is not easy to select between these attacks or attack-groups.
[edit]
rayka# set security idp idp-policy TEST rulebase-ips rule 1 match attacks ?
Possible completions:
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
+ custom-attack-groups Custom attack groups
+ custom-attacks Custom attacks
+ dynamic-attack-groups Dynamic attack groups
+ predefined-attack-groups Predefined attack groups
+ predefined-attacks Predefined attacks
[edit]
rayka# set security idp idp-policy TEST rulebase-ips rule 1 match attacks predefined-attacks ?
Possible completions:
<value> Predefined attacks
APP:2WIRE-DSL-VULN
APP:ABB-NETSCANHOST-OF
APP:ACCELLION-FILE-TRANSFER
APP:ACRONIS-TRU-IMG-ECO-SRV-DOS
APP:ADOBE-CF-DIR-TRAV
APP:ADOBE-COLDFUSION-WEBSOCKET
APP:ADOBE-FLASH-MEDIA-SRVR
APP:ADOBE-FLASH-RTMP-RCE
APP:AFP-LEN-OF
APP:AGENTX-RECEIVE-INT-OF
APP:AGENTX-RECEIVE-OF
APP:ALTN-WORLDCLIENT-MEM
APP:AMANDA:AMANDA-ROOT-OF1
....The list of pre-defined attack groups can also be seen with the command “show security idp attack attack-list predefined-group ?”.
rayka# run show security idp attack attack-list predefined-group ?
Possible completions:
<predefined-group> Predefined group name
"APP - All"
"APP - Critical"
"APP - Info"
"APP - Major"
"APP - Minor"
...In a few minutes, we will see how we can easily activate existing recommended IPS policy.
Juniper SRX IDP Policy, “then” options
With “then” keyword, we can choose which action must be taken for each attack.
For the action, there are some options that is actually not easy to decide which action for which attack is suitable.
rayka# set security idp idp-policy TEST rulebase-ips rule 1 then action ?
Possible completions:
> mark-diffserv Mark differentiated services codepoint (DSCP)
> class-of-service Classification of traffic based on class-of-service
no-action No action
ignore-connection Ignore
drop-packet Drop packet
drop-connection Drop connection
close-client Close client
close-server Close server
close-client-and-server Close client and server
recommended RecommendedTh most important actions are “drop packet” and “drop-connection” which drop a single packet or drop any packet in an existing session.
The actions “close client”, “close-server” and “close-client-and-server” are another important action which send TCP-reset packet to the client, to the server or to the both sides.
But there is another option ”recommended”, which means, for each attack, there is a recommended action which mostly is a best choice when we can not decide which can be correct action.
download and install SRX pre-defined IDP Policy-Templates
As you have noticed, it is not east at all, to configure custom IDP policy.
Fortunately, Juniper has created some pre-defined IDP policy-templates that we can use them easily in security policies or tune them when needed.
rayka# run request security idp security-package download policy-templates
Will be processed in async mode. Check the status using the status checking CLI
[edit]
rayka# run request security idp security-package download status
In progress: Downloading ...
[edit]
rayka# run request security idp security-package download status
Done;Successfully downloaded from(https://signatures.juniper.net/cgi-bin/index.cgi).
Version info:3516
[edit]
rayka# run request security idp security-package install policy-templates
Will be processed in async mode. Check the status using the status checking CLI
[edit]
rayka# run request security idp security-package install status
Done;policy-templates has been successfully updated into internal repository
(=>/var/run/scripts/commit/templates.xsl)!
[edit]
rayka# set system scripts commit file templates.xsl
[edit]
rayka# commit
commit completeTo use juniper pre-defined IDP policy templates, we have to download and install them.
With the command “request security idp security-package download policy-templates”, we can start to download them.
With the command “request security idp security-package download status”, we can check the status of download.
After download, we can install pre-defined IDP policy templates with the command “request security idp security-package install policy-templates”.
With the command “request security idp security-package install status”, we can check the status of installation process.
When installation process is successful, it shows that a file with the name of “templates.xsl” is stored in local repository.
Finally with command “set system scripts commit file templates.xsl”, we can load IDP policy templates into the configuration.
explore pre-defined IDP Policy-Templates
Now if use the command “set security idp idp-policy ?” in configuration mode, you will see that more than 10 IDP policy is created in the juniper SRX.
rayka# set security idp idp-policy ?
Possible completions:
<policy-name> IDP policy name
Web_Server IDP policy name
DMZ_Services IDP policy name
DNS_Service IDP policy name
File_Server IDP policy name
Getting_Started IDP policy name
IDP_Default IDP policy name
Server-Protection IDP policy name
Server-Protection-1G IDP policy name
Client-Protection IDP policy name
Client-Protection-1G IDP policy name
Client-And-Server-Protection IDP policy name
Client-And-Server-Protection-1G IDP policy name
Recommended IDP policy nameThe name if each policy shows the target of that policy.
For example, IDP policy with the name of “Web_Server” must be used to protect web servers.
With the name of other IDP policies, like “DMZ_Services”, “DNS_Service”, “File_Server” , we can also understand somehow what they do and in which policy they should e activated.
With the command “show security idp”, you can see the details of each pre-defined idp policy.
rayka# show security idp
idp-policy Web_Server {
/* This template policy is designed to protect commonly used HTTP servers from remote attacks. */
rulebase-ips {
rule 1 {
/* This rule drops all packets that should not occur on a clean network, and can be used by attackers to evade IDSs. This rule is necessary to harden the IDP against evasion attempts. */
match {
from-zone any;
source-address any;
to-zone any;
destination-address any;
application default;
attacks {
predefined-attack-groups [ "IP - Major" "IP - Critical" "TCP - Critical" "TCP - Major" ];
}
}
then {
action {
drop-packet;
}
notification {
log-attacks;
...For example in the first rule of “Web_Server” idp policy, any packets including attacks in the category of “IP – Major”, “IP – Critical”, “TCP – Critical” and “TCP – Major” are dropped and a log notification is generated.
deploy Juniper SRX IDP Policy in Security Policy
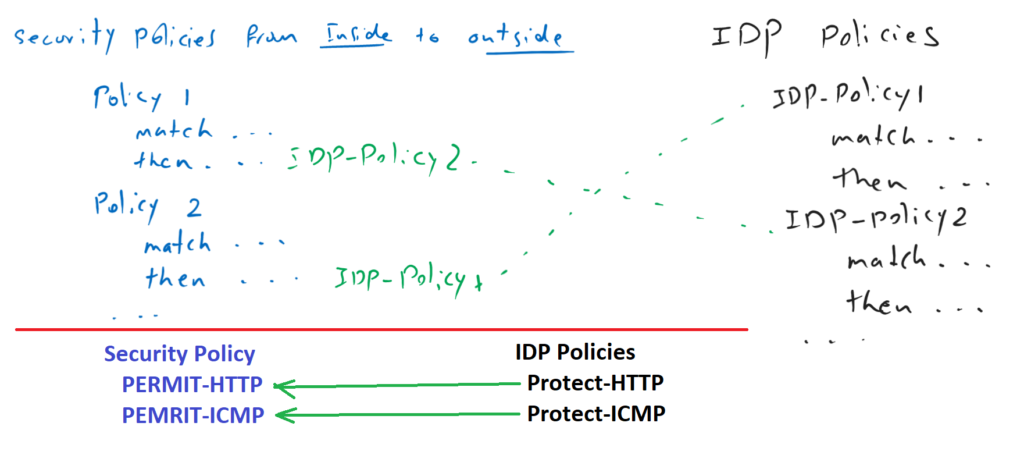
Now that we know pre-defined IDP policies or we have configured our custom IDP policies, how they can be activated.
Fortunately , you can activate IDP policy in the same security policies that we have configured in the previous sections. Therefore there is a unified security policy for firewall and IPS configuration.
for each security policy, you can choose a separate IDP policy from the list of IDP policies to protect that specific traffic.
for example, for policy which permit HTTP traffic, you can use an IDP policy which protect HTTP traffic. And for the policy that permit ICMP traffic you can choose an IDP policy which protect ICMP traffic.
To enable IDP policy into unifies security policy, we use the keyword “application-services idp-policy”, after “permit” command in security policy.
rayka# set security policies from-zone inside to-zone outside policy PERMIT-HTTP then permit application-services idp-policy ?
Possible completions:
<idp-policy> Specify idp policy name
Client-And-Server-Protection [security idp idp-policy]
Client-And-Server-Protection-1G [security idp idp-policy]
Client-Protection [security idp idp-policy]
Client-Protection-1G [security idp idp-policy]
DMZ_Services [security idp idp-policy]
DNS_Service [security idp idp-policy]
File_Server [security idp idp-policy]
Getting_Started [security idp idp-policy]
IDP_Default [security idp idp-policy]
Recommended [security idp idp-policy]
Server-Protection [security idp idp-policy]
Server-Protection-1G [security idp idp-policy]
Web_Server [security idp idp-policy]In front of “application-services” keyword, there are also other application services in addition to idp-policy that can be activated in unified security policy like “ssl-proxy” or “packet-capture”.
rayka# set security policies from-zone inside to-zone outside policy PERMIT-HTTP then permit application-services ?
Possible completions:
advanced-anti-malware-policy Specify advanced-anti-malware policy name
> application-traffic-control Application traffic control services
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
gtp-profile Specify GPRS Tunneling Protocol profile name
icap-redirect Specify icap redirect profile name
idp Intrusion detection and prevention
idp-policy Specify idp policy name
packet-capture Capturing traffic related to this policy
redirect-wx Set WX redirection
reverse-redirect-wx Set WX reverse redirection
sctp-profile Specify Stream Control Protocol profile name
> security-intelligence Generate security intellegence feeds
security-intelligence-policy Specify security-intelligence policy name
> ssl-proxy SSL proxy services
> uac-policy Enable unified access control enforcement of policy
utm-policy Specify utm policy name
> web-proxy Web proxy servicesAs an example, let’s activate the IDP policy “Recommended” in the first policy, “PERMIT-HTTPS” in security policy and see the final configuration.
rayka# set security policies from-zone inside to-zone outside policy PERMIT-HTTPS then permit application-services idp-policy Recommended
[edit]
rayka# show | compare
[edit security policies from-zone inside to-zone outside policy PERMIT-HTTPS then permit]
+ application-services {
+ idp-policy Recommended;
+ }
[edit]
rayka# show security policies from-zone inside to-zone outside policy PERMIT-HTTPS
match {
source-address any;
destination-address any;
application junos-https;
dynamic-application any;
}
then {
permit {
application-services {
idp-policy Recommended;
}
}
log {
session-init;
}
}As you can see, “application-services idp-policy Recommended” is added inside permit action in PERMIT-HTTPS security policy.
monitor SRX IDP Policy status
To monitor status of IDP policies, we can use the command “show security idp status”, which show statistics of packets, flow and sessions inspected by IPS policy engiene.
rayka# run show security idp status
Intelligent Inspection State Details:
State: Inactive
Intelligent offload State Details:
State: Active
State of IDP: Default, Up since: 2022-08-01 14:21:30 UTC (1w2d 08:08 ago)
Packets/second: 1 Peak: 19 @ 2022-08-10 22:29:50 UTC
KBits/second : 1 Peak: 27 @ 2022-08-10 22:29:50 UTC
Latency (microseconds): [min: 0] [max: 0] [avg: 0]
Packet Statistics:
[ICMP: 0] [TCP: 40] [UDP: 0] [Other: 0]
Flow Statistics:
ICMP: [Current: 0] [Max: 0 @ 2022-08-10 22:15:17 UTC]
TCP: [Current: 14] [Max: 16 @ 2022-08-10 22:29:50 UTC]
UDP: [Current: 0] [Max: 0 @ 2022-08-10 22:15:17 UTC]
Other: [Current: 0] [Max: 0 @ 2022-08-10 22:15:17 UTC]
Session Statistics:
[ICMP: 0] [TCP: 7] [UDP: 0] [Other: 0]
Number of SSL Sessions : 0
Policy Name : idp-policy-unified
Running Detector Version : 12.6.130200828