Juniper SRX global security policy gives the capability to write policies to control traffic but independent of the zone-pairs. Global policy can be also used to be applied to multiple zone-pairs at once.
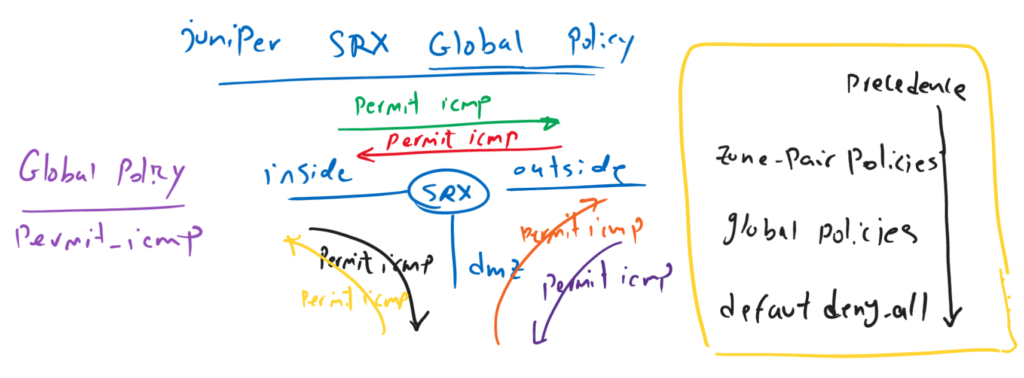
It is important to notice that global policy is processed after normal inter-zone policy and before default deny-all policy.
SRX Global Security Policy Fundamental
Here shows why we need global security policy.
When you need to give the same policy between all or some zone-pairs, it is possible to configure the policy for each zone-pair separately. Or the other option is to use global policy.
In this example, we want to permit ICMP between all zone-pairs. There are three zones and six zone-pairs. It means that we have to configure the same policy in all six zone-pairs.
With global policy, it is possible to assign a single policy independent of zone-pairs, in other words between all zone-pairs, or it is also possible to assign it to more than one zone-pair at once.
Here, with global policy, we configure one “permit-icmp” policy only in global policy.
Global policy will be processed after zone-pair policy and before default “deny-all” policy.
SRX Global Security Policy Configuration
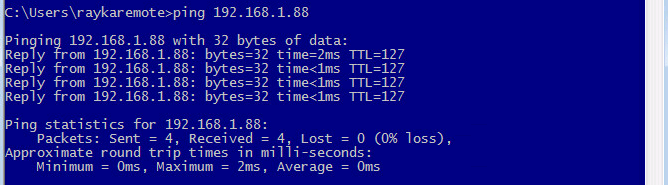
current status of inside to outside security policy
This is the policy that we have configured in the previous section.
set security policies from-zone inside to-zone outside policy PERMIT-WEB match source-address NET_192_168_10_0__24
set security policies from-zone inside to-zone outside policy PERMIT-WEB match destination-address any
set security policies from-zone inside to-zone outside policy PERMIT-WEB match application junos-http
set security policies from-zone inside to-zone outside policy PERMIT-WEB then permit
...
set security policies from-zone inside to-zone outside policy PERMIT-ICMP match source-address NET_192_168_10_0__24
set security policies from-zone inside to-zone outside policy PERMIT-ICMP match destination-address any
set security policies from-zone inside to-zone outside policy PERMIT-ICMP match application junos-icmp-all
set security policies from-zone inside to-zone outside policy PERMIT-ICMP then permit
set security policies from-zone inside to-zone outside policy PERMIT-ICMP then log session-init
set security policies from-zone inside to-zone outside policy PERMIT-ICMP then count
set security policies from-zone inside to-zone outside policy DENY-ALL match source-address any
set security policies from-zone inside to-zone outside policy DENY-ALL match destination-address any
set security policies from-zone inside to-zone outside policy DENY-ALL match application any
set security policies from-zone inside to-zone outside policy DENY-ALL then reject
set security policies from-zone inside to-zone outside policy DENY-ALL then log session-init
set security policies from-zone inside to-zone outside policy DENY-ALL then countAs you can see ICMP is permitted from inside to outside policy.
we can check the connectivity to make sure that ICMP is actually permitted.
delete “PERMIT-ICMP” and explicit “DENY-ALL” policies from inside-outside policies
We are going to move “PERMIT-ICMP” and explicit “DENY-ALL” policies from zone-pair inside-outside to global policy.
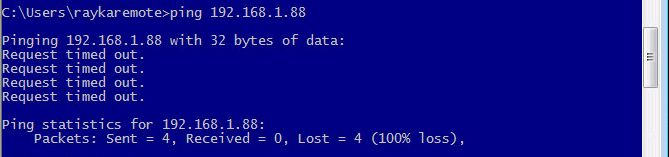
In the first step, I delete these two policies from zone-pair and check the ping connectivity again.
rayka# delete security policies from-zone inside to-zone outside policy DENY-ALL
[edit]
rayka# show | compare
[edit security policies from-zone inside to-zone outside]
- policy DENY-ALL {
- match {
- source-address any;
- destination-address any;
- application any;
- }
- then {
- reject;
- log {
- session-init;
- }
- count;
- }
- }[edit]
rayka# delete security policies from-zone inside to-zone outside policy PERMIT-ICMP
warning: statement not found
[edit]
rayka# show | compare
[edit security policies from-zone inside to-zone outside]
- policy PERMIT-ICMP {
- match {
- source-address NET_192_168_10_0__24;
- destination-address any;
- application junos-icmp-all;
- }
- then {
- permit;
- log {
- session-init;
- }
- count;
- }
- }As we expect there is no more ping connectivity.
Create Global Policy
Now we move “PERMIT-ICMP” policy and explicit “DENY-ALL” policy to global policy.
set security policies global policy PERMIT-ICMP match source-address any
set security policies global policy PERMIT-ICMP match destination-address any
set security policies global policy PERMIT-ICMP match application junos-icmp-ping
set security policies global policy PERMIT-ICMP then permit
set security policies global policy PERMIT-ICMP then log session-init
rayka# show | compare
[edit security policies]
+ global {
+ policy PERMIT-ICMP {
+ match {
+ source-address any;
+ destination-address any;
+ application junos-icmp-ping;
+ }
+ then {
+ permit;
+ log {
+ session-init;
+ }
+ }
+ }
+ }set security policies global policy DENY-ALL match source-address any
set security policies global policy DENY-ALL match destination-address any
set security policies global policy DENY-ALL match application any
set security policies global policy DENY-ALL then reject
set security policies global policy DENY-ALL then log session-init
rayka# show | compare
[edit security policies global]
policy PERMIT-ICMP { ... }
+ policy DENY-ALL {
+ match {
+ source-address any;
+ destination-address any;
+ application any;
+ }
+ then {
+ reject;
+ log {
+ session-init;
+ }
+ }
+ }
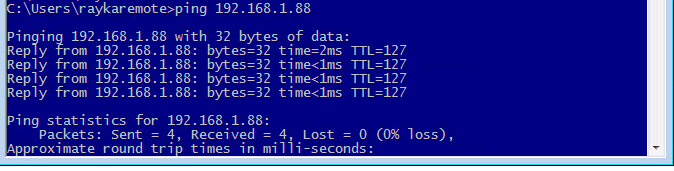
And check the connectivity again. We expect that ping connectivity comes back.
Monitor Firewall Log File, Live
In the previous section we have created a log file with the name of FIREWALL to keep all traffic connectivity.
set system syslog file FIREWALL any any
set system syslog file FIREWALL match RT_FLOW_SESSIONWe have also activated log action in “PERMIT-ICMP” policy.
Now with the command “monitor start”, I can check the content of the log file, live. Therefore any icmp traffic over SRX from inside to outside will be displayed live.
rayka# run monitor start FIREWALL
[edit]
rayka#
*** FIREWALL ***
Aug 5 11:57:30 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.121/1->192.168.1.88/58 0x0 icmp 192.168.10.121/1->192.168.1.88/58 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP(global) inside outside 345316 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 5 11:57:31 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.121/1->192.168.1.88/59 0x0 icmp 192.168.10.121/1->192.168.1.88/59 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP(global) inside outside 345317 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 5 11:57:32 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.121/1->192.168.1.88/60 0x0 icmp 192.168.10.121/1->192.168.1.88/60 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP(global) inside outside 345320 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 5 11:57:33 RT_FLOW: RT_FLOW_SESSION_CREATE: session created 192.168.10.121/1->192.168.1.88/61 0x0 icmp 192.168.10.121/1->192.168.1.88/61 0x0 N/A N/A N/A N/A 1 PERMIT-ICMP(global) inside outside 345322 N/A(N/A) ge-0/0/1.0 UNKNOWN UNKNOWN UNKNOWN N/A N/A -1 N/A N/A N/A Off root N/A N/A
Aug 5 11:57:38 RT_FLOW: RT_FLOW_SESSION_DENY: session denied 192.168.10.121/19848->192.168.1.50/3306 0x0 None 6(0) DENY-ALL(global) inside outside UNKNOWN UNKNOWN N/A(N/A) ge-0/0/1.0 No Rejected by policy 345323 N/A N/A -1 N/A N/A N/A N/A N/A
Aug 5 11:57:38 RT_FLOW: RT_FLOW_SESSION_DENY: session denied 192.168.10.121/52241->192.168.1.240/53 0x0 junos-dns-udp 17(0) DENY-ALL(global) inside outside UNKNOWN UNKNOWN N/A(N/A) ge-0/0/1.0 No Rejected by policy 345324 N/A N/A -1 N/A N/A N/A N/A N/A
...
[edit]
rayka# run monitor stop With “monitor stop” command, monitoring live log messages will be stopped.
permit SSH in global policy in Multiple Zones and move the policy
And in the last example, I want to add another policy to permit SSH traffic but when the traffic from inside zone or trust zones are forwarded to outside zone or untrust zone.
Actually this is another application of global policy which can be applied to multiple policy.
set security policies global policy PERMIT-SSH match source-address any
set security policies global policy PERMIT-SSH match destination-address any
set security policies global policy PERMIT-SSH match application junos-ssh
set security policies global policy PERMIT-SSH match from-zone trust
set security policies global policy PERMIT-SSH match from-zone inside
set security policies global policy PERMIT-SSH match to-zone untrust
set security policies global policy PERMIT-SSH match to-zone outside
set security policies global policy PERMIT-SSH then permit
set security policies global policy PERMIT-SSH then log session-init
rayka# show | compare
[edit security policies global]
policy DENY-ALL { ... }
+ policy PERMIT-SSH {
+ match {
+ source-address any;
+ destination-address any;
+ application junos-ssh;
+ from-zone [ trust inside ];
+ to-zone [ untrust outside ];
+ }
+ then {
+ permit;
+ log {
+ session-init;
+ }
+ }
+ }To assign a policy to multiple zones, “from-zone” or “to-zone” keywords can be added as a match condition in global policy.
The last point in this section is when we add a new policy in SRX, it will be added as a last rule.
In our example, it will be located after “DENY-ALL” rule. In other words, it will never match the traffic since all traffic are matched with “DENY-ALL” rule.
Therefore we have to move the new “PRMIT-SSH” before “DENY-ALL” rule.
It can be done with keyword “insert” and “before”.
insert security policies global policy PERMIT-SSH before policy DENY-ALL