Juniper SRX application firewall provides the capability to control traffic at application layer.
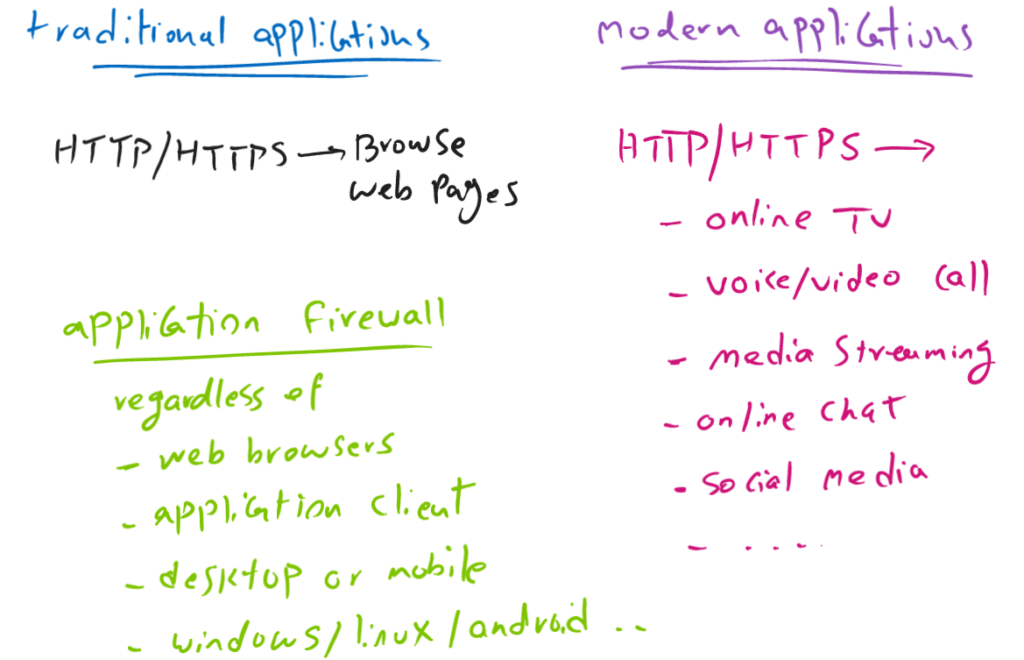
In the traditional firewall that we have configured so far, we have had the ability to control traffic only at Layer 3 and Layer 4.
Application layer traffic control is possible using application signatures prepared by Juniper.
Application Firewall Fundamental
In the past, when we allowed HTTP or HTTPS through traditional firewall, user could only browse internet webpages.
But today mostly all applications are running over HTTP and HTTPS protocols. For example social media applications, online TV, video on demand streaming, chat applications, voice and video call and many other application are running over HTTP and HTTPS protocols.
Therefore just with a traditional firewall, which control traffic at layer 3 and layer 4, you are not able to control theses complex applications.
With application firewall, for each application a special signature is configured which looks at application layer header and data information.
With application signatures, we are able to identify applications, regardless of the operating system or platform on which those applications run.
For example, it doesn’t matter if you’re making a Google Meet video call over web browser, through the application client, or through mobile apps. Application signatures must be able to recognize this application.
Juniper SRX Application Firewall Configuration
Enable, Download and Install application firewall signatures
To enable application firewall , first we have to install application identification feature license.
With command “request system license add terminal”, we can add the license to enable application firewall.
user@vsrx> request system license add terminal
[Type ^D at a new line to end input,
enter blank line between each license key]
JUNOS123456 aaaaaa bbbbbb cccccc dddddd eeeeee ffffff
cccccc bbbbbb dddddd aaaaaa ffffff aaaaaa
aaaaaa bbbbbb cccccc dddddd eeeeee ffffff
cccccc bbbbbb dddddd aaaaaa ffffff
JUNOS123456: successfully added
add license complete (no errors)With command “show system license”, you can make sure that “appid-sig” signature license is valid on your SRX device.
rayka# run show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 30 days
idp-sig 0 1 0 30 days
appid-sig 1 1 0 29 days
av_key_sophos_engine 0 1 0 30 days
wf_key_websense_ewf 0 1 0 30 days
Virtual Appliance 1 1 0 39 days
remote-access-ipsec-vpn-client 0 2 0 permanent
remote-access-juniper-std 0 2 0 permanent
...Then you are ready to download application signatures from juniper website.
With command “request services application-identification download”, you can download application signatures from juniper website.
With adding “status” keyword, at the end of above command, the status of download will be shown.
rayka# run request services application-identification download
Please use command
"request services application-identification download status" to check download status
[edit]
rayka# run request services application-identification download status
Fetching/Uncompressing https://signatures.juniper.net/xmlupdate/280/ApplicationGroups/3515/application_groups2.xml.gz
[edit]
rayka# run request services application-identification download status
Fetching/Uncompressing https://signatures.juniper.net/xmlupdate/280/Applications/3515/applications2.xml.gz
[edit]
rayka# run request services application-identification download status
Fetching/Uncompressing https://signatures.juniper.net/xmlupdate/280/Libqmprotocols/1.530.2-40/libqmprotocols.tgz
[edit]
rayka# run request services application-identification download status
Downloading application package 3515 succeeded.Then with command “request services application-identification install”, you can install downloaded application signatured into the device.
With adding “status” at the end of the above command, the status of installation will be displayed.
[edit]
rayka# run request services application-identification install
Please use command
"request services application-identification install status" to check install status
[edit]
rayka# run request services application-identification install status
Checking compatibility of application package version 3515 ...
[edit]
rayka# run request services application-identification install status
Cleaning up legacy configurations in Junos configuration ...
[edit]
rayka# run request services application-identification install status
Installed
Application package (3515) and Protocol bundle successfullyapply Juniper SRX Application Firewall in Unified Security Policy
Starting from Junos version 18.2.R1, you can use application policy and traditional policy in the same command set which is call “unified security policy”.
To inspect a traffic in application layer, you have to just “match dynamic-application” in your security policy.
As an example if you match “match dynamic-application junos:google”, you will see that a long list of google applications can be configured. Between them there are google maps and google photos and many other applications.
rayka# set security policies from-zone inside to-zone outside policy TEST match dynamic-application ?
Possible completions:
<system-applications> Specify dynamic application or dynamic application group to match
[ Open a set of values
any Any dynamic application
junos:01NET 01net website, a French high-tech news site.
junos:050PLUS 050 plus is a Japanese embedded smartphone application dedicated to audio-conferencing.
junos:0ZZ0 0zz0 is an online solution to store, send and share files
junos:10050NET China Railcom group web portal.
....
rayka# set security policies from-zone inside to-zone outside policy TEST match dynamic-application junos:google
^
'junos:google' is ambiguous.
Possible completions:
<system-applications> Specify dynamic application or dynamic application group to match
junos:GOOGLE This signature detects SSL connections to Google.com. Google is a company best known for their search engine but offers many clo
junos:GOOGLE-ACCOUNTS This signature detects SSL access to the Google Accounts server. A Google Account is a user account that provides access to Goog
junos:GOOGLE-ADS This signature detects SSL access to DoubeClick. DoubleClick is an advertisement service that was purchased by Google in 2007.
junos:GOOGLE-ANALYTICS-TRACKING This signature detects Google Analytics Tracking.
junos:GOOGLE-API Google APIs is a set of application programming interfaces (APIs) developed by Google which allow communication with Google Serv
junos:GOOGLE-APPENGINE Google App Engine is a platform as a service (PaaS) cloud computing platform for developing and hosting web applications in Goog
junos:GOOGLE-BLOG blog.google is the public blog of Google (products, news, ...).
junos:GOOGLE-BOOKS On-line file storage and sharing web-service by Google. Important: most of the traffic is encrypted with generic Google certific
...
junos:GOOGLEBOT Web crawler (spider) used by the Google Search engine. This plug-in will classify the bot HTTP requests, but the ixEngine won't
junos:GOOGLETALK This signature detects the Google Talk client using the Jabber (XMPP) protocol.For each application you can see the detail of application signature with the command “show services application-identification application detail”.
rayka# run show services application-identification application detail junos:GOOGLE-MAPS
Application Name: junos:GOOGLE-MAPS
Application type: GOOGLE-MAPS
Description: Google Maps can be used to calculate routes and to look at maps. The encrypted traffic is classified as google. This plug-in also classifies
the traffic destined to the Google Location service or third-party applications using its API, to locate a device.
Application ID: 57
Priority: high
Order: 0
Disabled: No
Cacheable: No
Configurable: Yes
Activation Date: 2008-05-20
Last Modified: 2020-09-21
Number of Parent Group(s): 1
Application Groups:
junos:web
Application Tags:
group-tags : web
group-tags : map-service
group-tags : aetls
risk : 2
subcategory : miscellaneous
category : Web
Underlying consolidated Protocols/ports application is dependent on:
Protocols:
Protocol: junos:WINDOWS-AZURE / 1288
Protocol: junos:UDP / 216
Protocol: junos:TCP / 205
...URL filtering based on application Firewall
With application signatures, the is also another important capability that you can filter websites or URLs based on their category.
To see the list of category, you need to match based on URL category with the command “match url-category ?”
rayka# set security policies from-zone inside to-zone outside policy TEST match url-category ?
Possible completions:
<custom-category> Specify name of url category to match
<system-category> Specify name of url category to match
Enhanced_Abortion
Enhanced_Abused_Drugs
Enhanced_Adult_Content
Enhanced_Adult_Material
Enhanced_Advanced_Malware_Command_and_Control
Enhanced_Advanced_Malware_Payloads
Enhanced_Advertisements
Enhanced_Advocacy_Groups
Enhanced_Alcohol_and_Tobacco
Enhanced_Alternative_Journals
Enhanced_Application_and_Software_Download
Enhanced_Bandwidth
...
Enhanced_Web_and_Email_Marketing
Enhanced_Web_and_Email_Spam
Enhanced_Website_Translation
[ Open a set of values
any Any url category
none Not apply the url categoryControl HTTPS Traffic
Probably you notice that when you implement application firewall I the juniper SRX, it does not work for most applications.
This is because most applications run over HTTPS which are encrypted and it is not easy to detect if it is a google map or google earth application running over HTTPS.
To resolve the problem , we have to configure SSL proxy in juniper SRX device which allows to decrypt and control the traffic before they are delivered to the clients on the network.
This is not the discussion of this section.