Juniper SRX Active Directory Integration is a prerequisite for implementing user-based access control.
In this section, you will learn how Juniper SRX retrieves users and groups information from Active Directory and how to determine each user’s current IP address.
Then we’re ready to implement a user-based firewall or access control in the next section.
Juniper SRX Active Directory Integration Fundamental
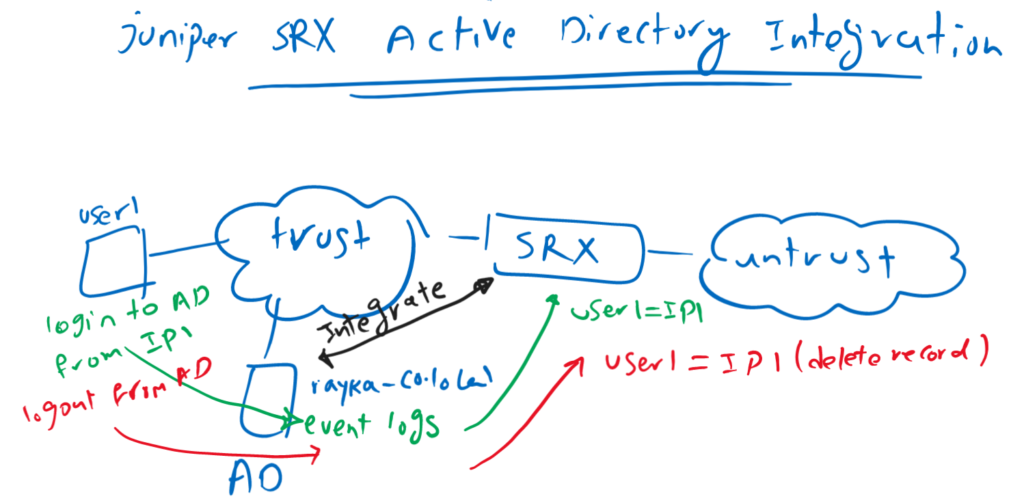
As I mentioned in the introduction, this section is dedicated to integrating SRX devices with Active Directory.
With the integrating SRX device with active directory, not only pulls user and group information from Active Directory into SRX device. but also get updated information regarding the IP address of each user.
Whenever a user logs in or out of the Active Directory, a log event is generated in the Windows event log database. SRX reads these information to update itself regarding the IP address of each user.
Configuration to integrate Juniper SRX to Active Directory
The configuration has two step.
In the first step, we have to connect SRX with active directory with giving the IP address od domain controller, LDAP server and username and password. In my scenario, domain controller and LDAP server are the same.
set services user-identification active-directory-access domain rayka-co.local user administrator
set services user-identification active-directory-access domain rayka-co.local user password QWEdsa@123
set services user-identification active-directory-access domain rayka-co.local domain-controller DC1 address 192.168.1.240
set services user-identification active-directory-access domain rayka-co.local user-group-mapping ldap base DC=rayka,DC=local
set services user-identification active-directory-access domain rayka-co.local user-group-mapping ldap address 192.168.1.240
set services user-identification active-directory-access authentication-entry-timeout 30
set services user-identification active-directory-access wmi-timeout 120In he second step, we configure an access profile to LDAP server to get user and group information which is necessary to implement user-based access control.
In access profile, we configure authentication method which is LDAP, the IP address of LDAP server, username and password to query the information and base distinguished name to query the information.
I configure administrator user for both integrating SRX with active directory and query the information.
set access profile Active-Directory authentication-order ldap
set access profile Active-Directory authentication-order password
set access profile Active-Directory ldap-options base-distinguished-name DC=rayka,DC=local
set access profile Active-Directory ldap-options search search-filter sAMAccountName=
set access profile Active-Directory ldap-options search admin-search distinguished-name CN=Administrator,CN=Users,DC=rayka,DC=local
set access profile Active-Directory ldap-options search admin-search password QWEdsa@123
set access profile Active-Directory ldap-server 192.168.1.240 no-tls-certificate-checkmonitor and test SRX integration with Active Directory
Before monitoring and testing, you should know that I have already installed active directory with the domain name “rayka-co.local”. a user with username “majid”, I have created. And a computer with IP address “192.168.1.99” is joined to the active directory.
Active directory configuration and joining the computer to the active directory is out of the scope of this course.
To monitor status of SRX integration with active directory, we use the command “show services user-identification active-directory-access domain-controller status extensive”.
The output shows if SRX is connected with active directory correctly or not.
rayka# run show services user-identification active-directory-access domain-controller status extensive
Domain: rayka-co.local
Domain controller: DC1
Address: 192.168.1.240
Status: Connected
[edit]
rayka# With the command “show services user-identification authentication-table authentication-source active-directory”, you will see which username with which IP address is logged into active directory. as mentioned earlier, these information are retrieved from active directory event log database.
rayka# run show services user-identification authentication-table authentication-source active-directory
Logical System: root-logical-system
Domain: rayka-co.local
Total entries: 3
Source IP Username groups(Ref by policy) state
fe80::b537:e484:19bb:7e44 administrator Valid
192.168.1.99 majid Valid
192.168.1.250 administrator Valid
You can also retrieve user information from the IP address with the command “show services user-identification authentication-table ip-address 192.168.1.99”.
As you can see this IP Address is connected to the username “majid”. It also shows user the latest access of the user to the active directory.
rayka# run show services user-identification authentication-table ip-address 192.168.1.99
Logical System: root-logical-system
Domain: rayka-co.local
Source-ip: 192.168.1.99
Username: majid
State: Valid
Source: wmic
Access start date: 2022-08-16
Access start time: 20:25:33
Age time: 30