Juniper Dynamic Routing enables network devices to learn and update routing information dynamically, which is very important and critical in large networks.
In this section, we will learn about the architecture of dynamic routing protocols and implement a simple OSPF routing protocol as an example in vSRX devices.
Dynamic Routing Fundamental
Dynamic Routing Aadvantages
To be able to forward a traffic in a network to a destination, then all routers in the path must know the route to the destination. When a router does not know the route to the destination, it will discard the traffic.
In large networks, it’s difficult to manually configure the route to each destination, but that’s not the only problem.
A bigger problem is that if a link in the network goes down, you have to update every route through that link to a different path.
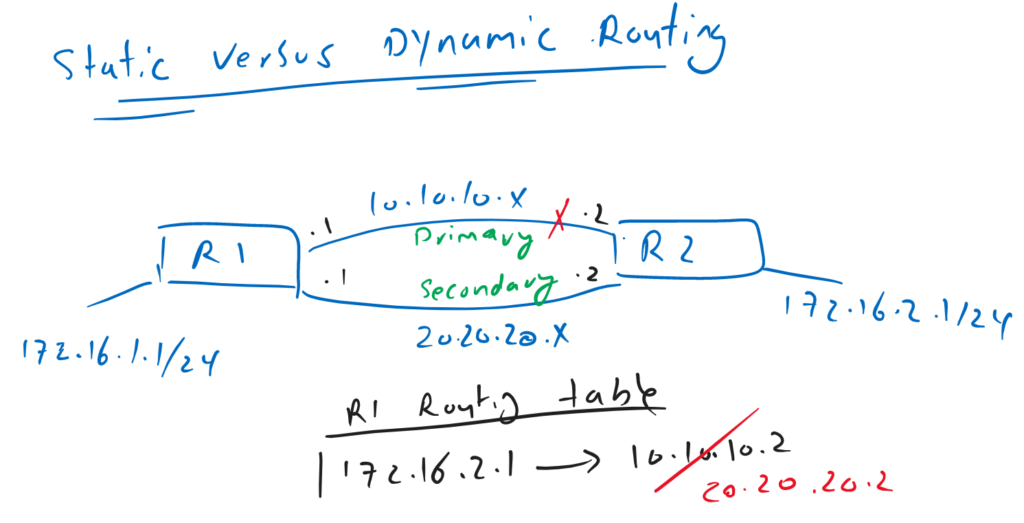
In this figure, both routers R1 and R2 already know the route to the destination networks connected to themself. For example router R1 already know the route to destination 172.16.1.0/24, 10.10.10.0/24 and 20.20.20.0/24 which are connected to router R1.
But they also must know the route to the loopback address of another router. In other words router R1 must know the route to destination 172.16.2.0/24 connected to router R2 and router R2 must also know the route to destination 172.16.1.0/24 connected to router R1.
Both router R1 and R2 have one primary route and also a secondary route to the loopback connected to another router for the time that primary route fails.
However, it can be difficult to statically update these routes every time a link goes down and comes back up.
in Dynamic routing, not only the best routing information are updated dynamically in all routers but whenever a link fails or is connected again, it will update the routing information dynamically.
Compare Dynamic Routing protocols
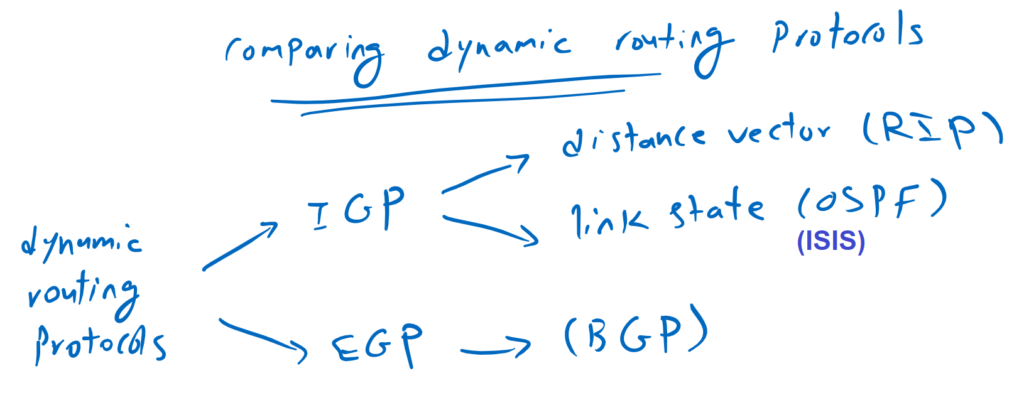
To have an overview of different routing protocols, there are two types of dynamic routing protocols.
one typically used “between” autonomous systems, known as the EGP (External Gateway Protocol). The only protocol currently used between autonomous systems and over the Internet is BGP.
The other type is used “inside” autonomous systems known as IGP (Interior Gateway Protocol).
We have two types of IGP routing protocols. One type updates routing information based on distance vector algorithm. The most well-known routing protocol in this category is RIP, which is deprecated and no longer used.
The other type is based on the link-state algorithm. The most well-known routing protocols in this category are OSPF and IS-IS, both of which are well known and widely used.
Compare Distance Vector and Link State Algorithms
I believe that it is difficult to understand the difference between “distance vector” and “link state” algorithm fully. If you do not have enough experience working with them.
But just to have an overview:
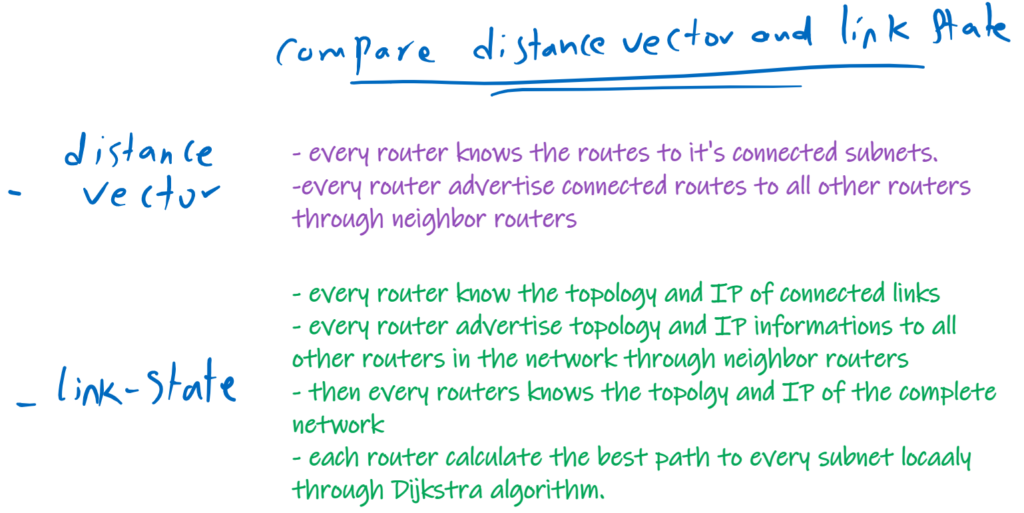
In distance vector routing protocols, every router advertise the routes to it’s connected subnets to the neighbour routers. Then neighbour routers know also the routes to those networks. Neighbour routers also advertise learned routes to their own neighbours and so on. In this way , all routers in the network learn the routes to every subnets in the network.
In link state routing protocols, the topology of the connected links and also IP information are advertised to all routers in the networks through neighbour routers. in a way that every router knows the complete topology of the network. Then each router, calculate the best route to every subnet with the help graph Dijkstra algorithm, locally.
Juniper Dynamic Routing configuration
Although we don’t know much about the detailed concept and configuration of the routing protocol but in this section I will implement a simple OSPF protocol to see the advantage of dynamic routing protocols.
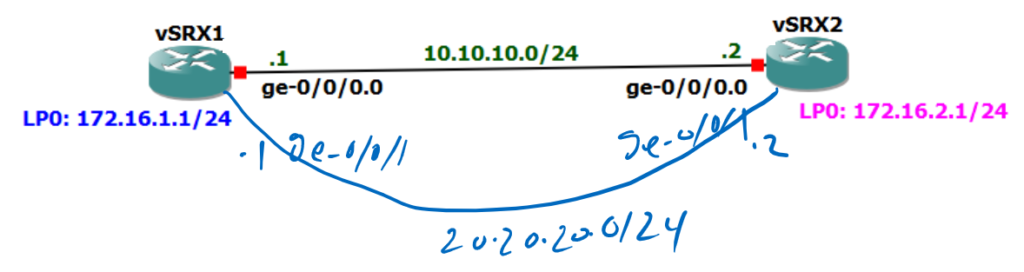
This is the topology that we have prepared in the previous sections. Two vSRX routers, vSRX1 and vSRX2 are connected to each other through interfaces ge-0/0/0 and ge-0/0/1 and with IP subnets 10.10.10.0/24 and 20.20.20.0/24.
vSRX has a loopback interface with IP address 172.16.1.1/24 and vSRX2 has also a loopback interface with IP address 172.16.2.1/24 which can not see each other until the routing between these two routers are correctly configured.
All interfaces are in “trust” zone. and therefore there is no need to configure any policy to permit the traffic between interfaces.
!!! vSRX1
rayka@vSRX1# run show configuration | display set | grep interface
set security zones security-zone trust interfaces ge-0/0/0.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces lo0.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services all
set interfaces ge-0/0/0 unit 0 family inet address 10.10.10.1/24
set interfaces ge-0/0/1 unit 0 family inet address 20.20.20.1/24
set interfaces lo0 unit 0 family inet address 172.16.1.1/24
...
!!! vSRX2
rayka@vSRX2# run show configuration | display set | grep interface
set security zones security-zone trust interfaces ge-0/0/0.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces lo0.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services all
set interfaces ge-0/0/0 unit 0 family inet address 10.10.10.2/24
set interfaces ge-0/0/1 unit 0 family inet address 20.20.20.2/24
set interfaces fxp0 unit 0 family inet address 192.168.200.102/24
set interfaces lo0 unit 0 family inet address 172.16.2.1/24We are going to run dynamic OSPF routing protocol between these two vSRX routers. to do that, we enable OSPF in all three interface ge-0/0/0, ge-0/0/1 and loopback0 in area 0. We have to also enable OSPF as host-inbound traffic to be allowed.
We haven’t talked about the topic, “area”, in OSPF routing protocols yet. But don’t worry, it won’t affect our discussion.
!!! vSRX1/vSRX2
set protocols ospf area 0.0.0.0 interface ge-0/0/0.0
set protocols ospf area 0.0.0.0 interface ge-0/0/1.0
set protocols ospf area 0.0.0.0 interface lo0.0
set security zones security-zone trust interfaces ge-0/0/0.0 host-inbound-traffic protocols ospf
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic protocols ospfWhen the OSPF is configure, it is expected that neighbour routers can detect each other. You can check it with the command “show ospf neighbor” in operational mode.
rayka@vSRX2# run show ospf neighbor
Address Interface State ID Pri Dead
10.10.10.1 ge-0/0/0.0 Full 172.16.1.1 128 31
20.20.20.1 ge-0/0/1.0 Full 172.16.1.1 128 35
[edit]
rayka@vSRX2# As you can see in both interfaces, ge-0/0/0 and ge-0/0/1, OSPF neighborship are created.
Now it is expected that two routes for the destination loopback interfaces are created through ge-0/0/0 and ge-0/0/0/1 in the routing tables. You can check routing table and routes learned through OSPF with the command “show route protocol ospf” in operational mode.
rayka@vSRX2# run show route protocol ospf
inet.0: 11 destinations, 11 routes (11 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
172.16.1.0/24 *[OSPF/10] 00:41:49, metric 1
to 10.10.10.1 via ge-0/0/0.0
> to 20.20.20.1 via ge-0/0/1.0
172.16.1.1/32 *[OSPF/10] 00:41:49, metric 1
to 10.10.10.1 via ge-0/0/0.0
> to 20.20.20.1 via ge-0/0/1.0
224.0.0.5/32 *[OSPF/10] 00:57:38, metric 1
MultiRecv
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
[edit]
rayka@vSRX2# As you can see there are two routes to the loopback interface of other routers through, once through ge-0/0/0 and the other through ge-/0/0/1.
With checking forwarding table, you can check , through which route, the traffic will be forwarded. This can be done with the command “show route forwarding-table destination” in operational mode.
rayka@vSRX2# run show route forwarding-table destination 172.16.1.1
Routing table: default.inet
Internet:
Destination Type RtRef Next hop Type Index NhRef Netif
172.16.1.1/32 user 0 20.20.20.1 ucst 569 4 ge-0/0/1.0
....
As you can see the traffic is forwarded through interface ge-0/0/1.
Now we disable the interface ge-0/0/1 in one of two routers. Traffic is expected to be dynamically rerouted to another interface.
[edit]
rayka@vSRX2# set interfaces ge-0/0/1 disable
[edit]
rayka@vSRX2# commit
commit complete
[edit]
rayka@vSRX2# run show route forwarding-table destination 172.16.1.1
Routing table: default.inet
Internet:
Destination Type RtRef Next hop Type Index NhRef Netif
172.16.1.1/32 user 0 10.10.10.1 ucst 564 4 ge-0/0/0.0
....And if it enabled again, traffic will be rerouted again to the previous path.
rayka@vSRX2# delete interfaces ge-0/0/1 disable
[edit]
rayka@vSRX2# commit
commit complete
[edit]
rayka@vSRX2# run show route forwarding-table destination 172.16.1.1
Routing table: default.inet
Internet:
Destination Type RtRef Next hop Type Index NhRef Netif
172.16.1.1/32 user 0 20.20.20.1 ucst 569 4 ge-0/0/1.0
....