Cisco Firepower Correlation Policy is to take an action against threats in real time when threats are not detected by IPS signatures since it a zero day attack and there is no signature for it or the behaviour is not normal in our network.
what is Firepower Correlation Policy?
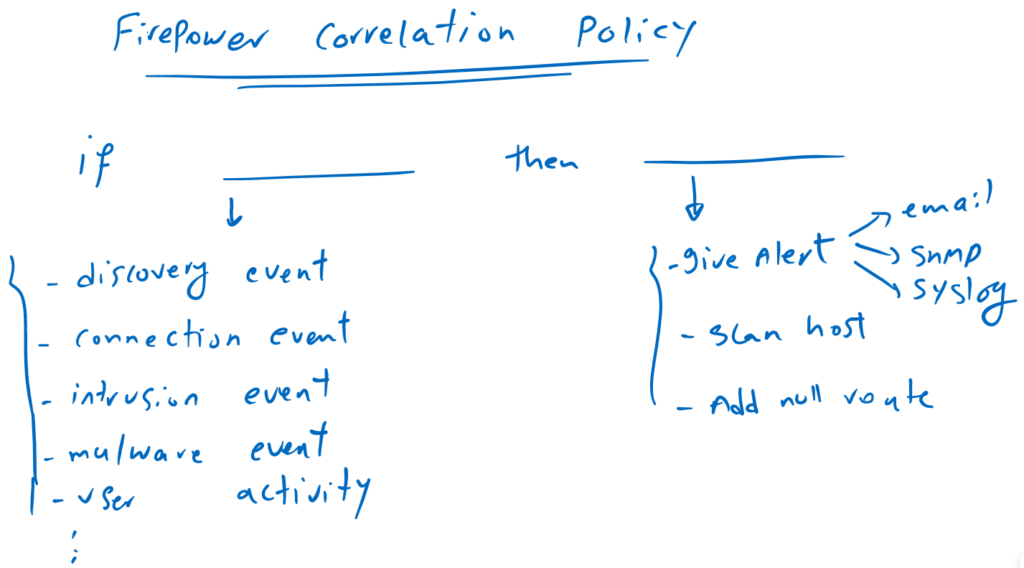
Cisco Firepower Correlation Policy is actually an “if…then…” rule that allows you to match based on many events on the network and then take appropriate action against it.
To give you some examples:
you can match based on discovery event. For example if a new host is discovered in the network or a new application is installed in any host or a new port is open in any host.
You can match based on intrusion events. For example if a specific SID or GID is matched. If an intrusion event is triggered by a specific country.
You can match based on user activity. For example a new user is detected in the network or a user logs into a host.
You can match based on malware events. For example if a malware is detected in a host or on the network
You can match based on connection events. For example if a specific access policy rule is matched by a specific IP address or username.
You can also match if a traffic profile changes or another correlation event is triggered.
As you have noticed, you have many options to match a specific behaviour on the network.
You can further narrow down the behaviour by creating simple or complex conditions based on specific IP, MAC, user or host types.
For the action, you don’t have many options other than sending an alert by sending an email, an SNMP or syslog message, scanning the suspicious host with Nmap tools, or blocking the suspicious IP by configuring a null route in a Router in the path.
Firepower Correlation Policy Sample Configuration
To configure a sample correlation policy:
if a new host in the subnet 192.168.0.0/16 is discovered and it send traffic more than 1 Byte then it must be blocked immediately.
Configure response (then) section of Firepower Correlation Policy
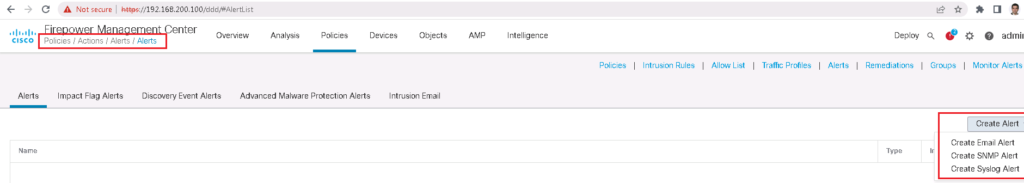
We first configure the response action.
Responses are configured through policies -> actions.
We can configure, an email, snmp or alert to be sent as an action.
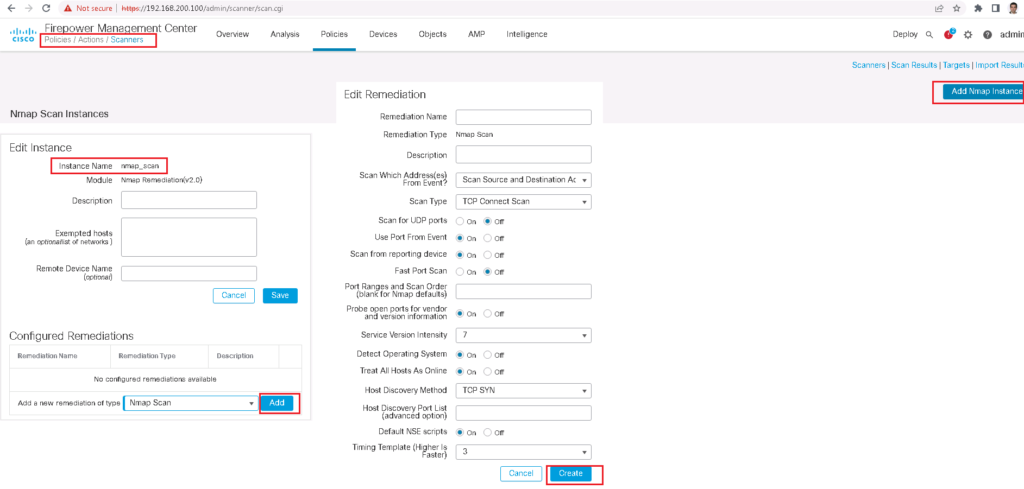
It is also possible to scan a host when a certain behaviour is met.
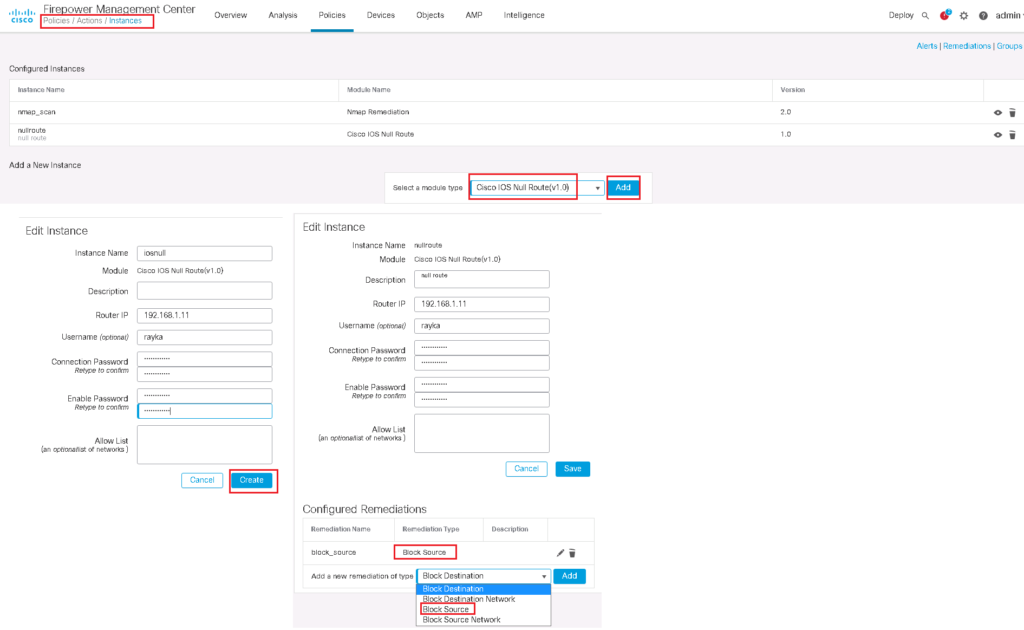
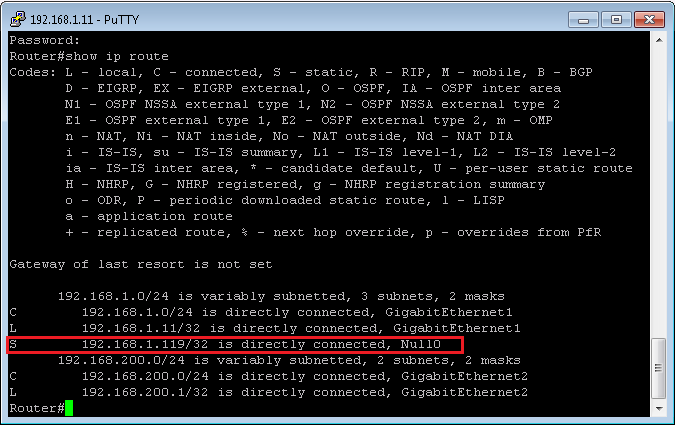
But in our example, we are asked to block a new host as an action. In Firepower, an IP address is blocked by adding a route in a router in the path with null as the next-hop address.
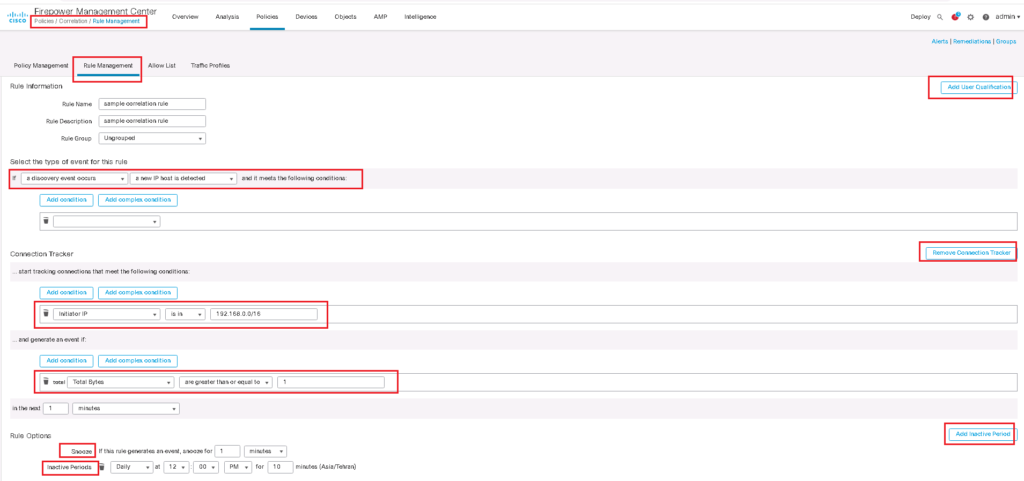
Configure match (if) section of Firepower Correlation Policy
In the second step we create a rule for the match (if) section of correlation policy in policies -> correlation -> Rule Management -> Create Rule
We have many options in if section of correlation policies as we have explained earlier. I choose when “a discovery event occurs” and “a new IP host is detected”.
I can further narrow down the behaviour with adding a simple or complex condition to track only for a particular IP or MAC address.
Just to test, I add connection Tracker module, so that after the rule’s initial criteria are met, to track the connection if the new detected host is in the range of 192.168.0.0/16 and create a correlation event when the new host is sending more than 1 Byte traffic.
We can also add User Qualification module to track certain users or groups of users in the network.
When a correlation rule triggers, a snooze period causes that rule not to trigger again for a specified interval. I choose 1 minute for snooze period.
And finally, we can Add inactive periods. During inactive periods, correlation rules do not trigger.
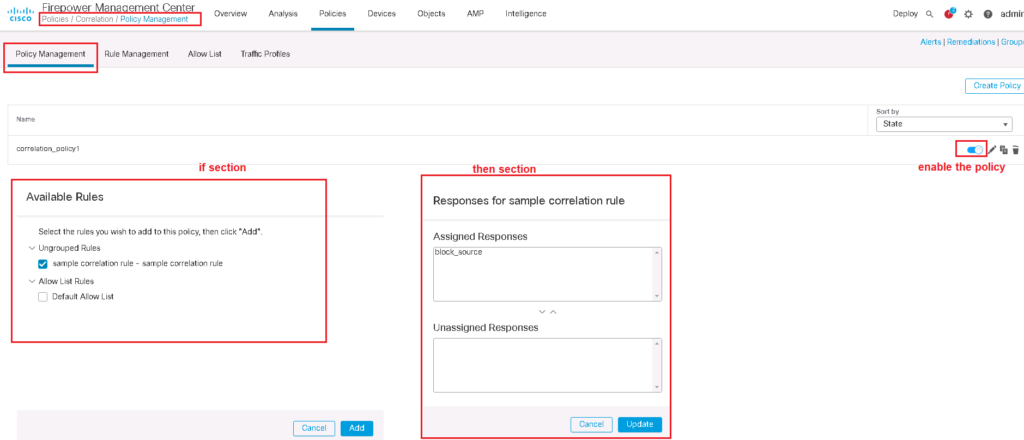
Firepower Correlation Policy Configuration
Now that we’ve created “if” and also “then” section of the correlation policy, we can tie them together using correlation policy In policies -> correlation -> Policy Management -> Create Policy.
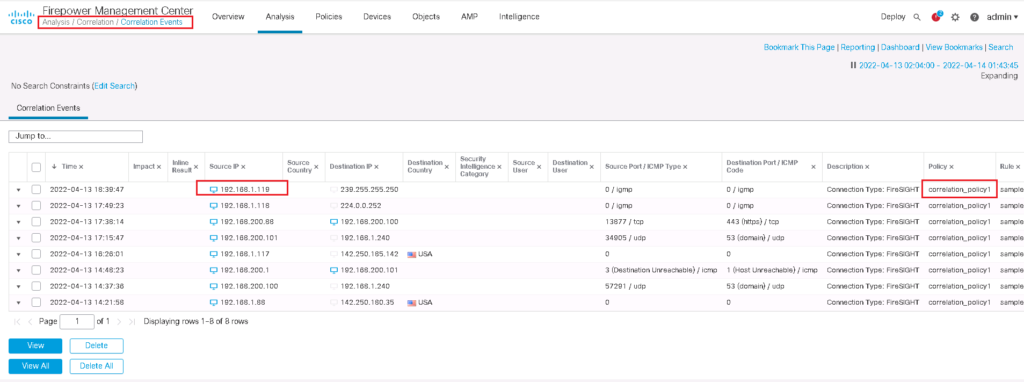
Monitor Firepower Correlation Policy Result
To check the result of firepower correlation policy, I change the IP address of a host behind FTD to 192.168.1.119 and create some sample traffic.
Then we expect that a correlation event is generated and also a null route is added to the router for the IP address of 192.168.1.119, which is new detected host.