F5 LTM Profile simple Example
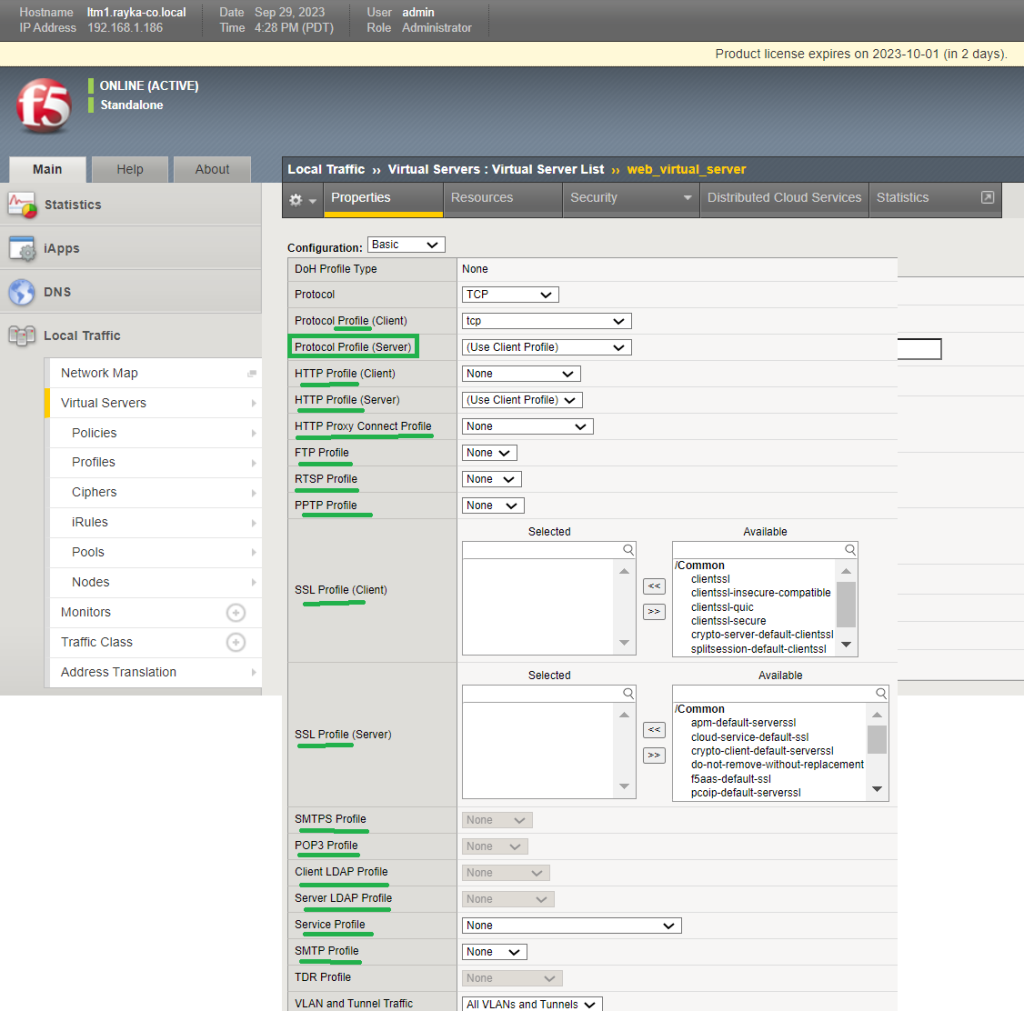
When you check the configuration of a virtual server in F5 LTM, you see many profiles that can be assigned to the virtual server.
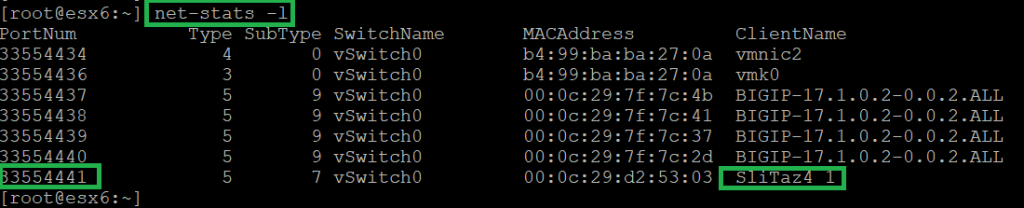
net-stats -l
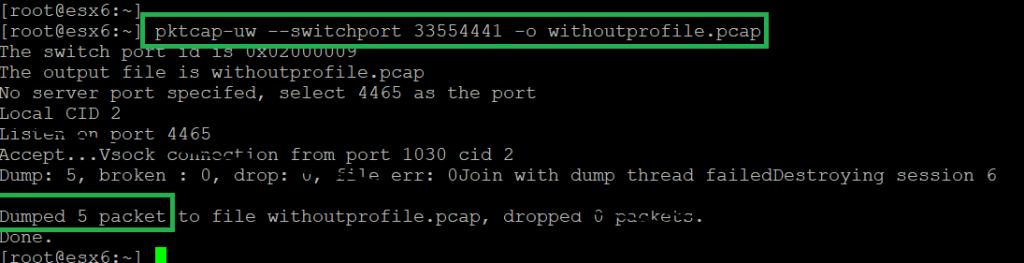
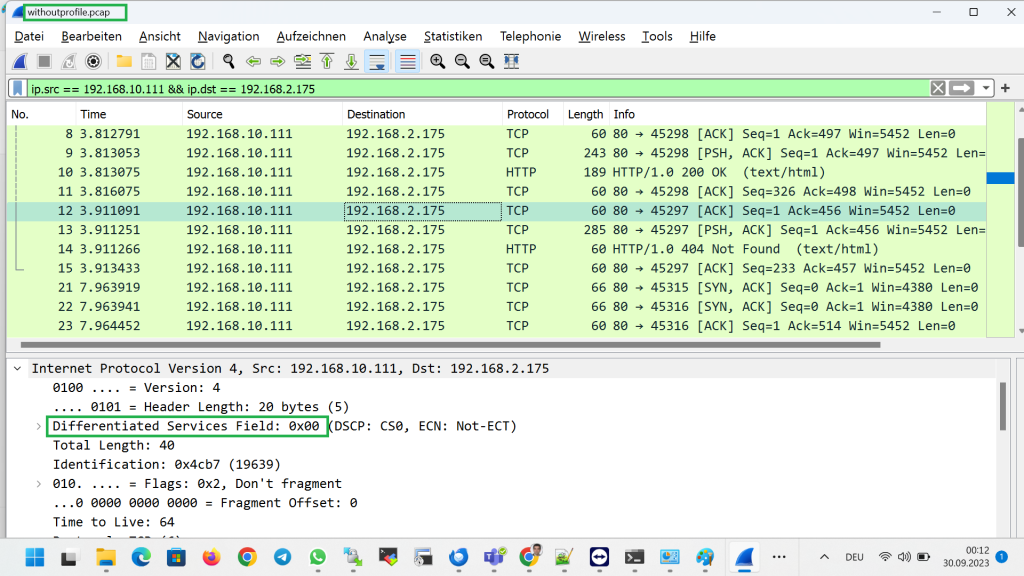
Now we request access to the web server through virtual IP address and then use the “pktcap-uw” command with the “–switchport” option to capture comings and goings from the first web server. We save the output of the capture in a file called “withoutprofile.pcap”.
Therefore, we can download the capture file and check the contents of the packets using wireshark software.
pktcap-uw --switchport 33554441 -o withoutprofile.pcap
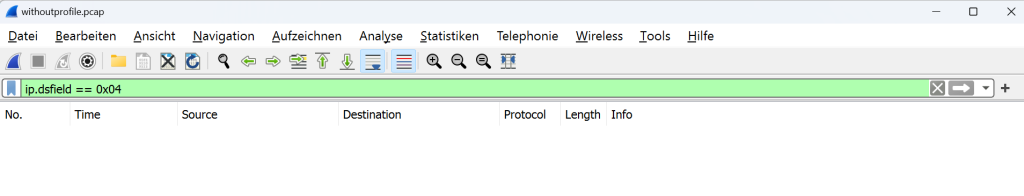
if we check DSCP field captured traffic, you can see that they are all “0x00”, which is the default value.
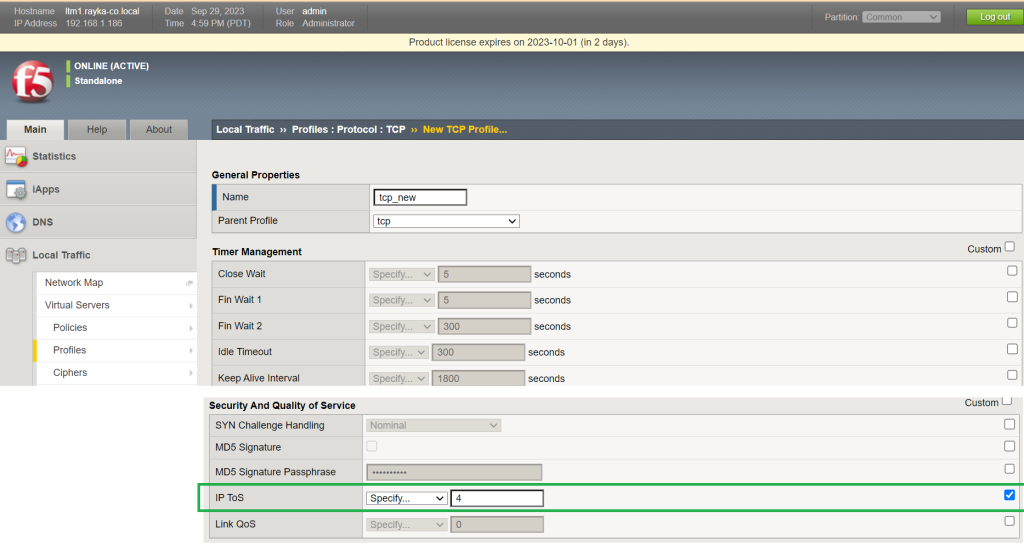
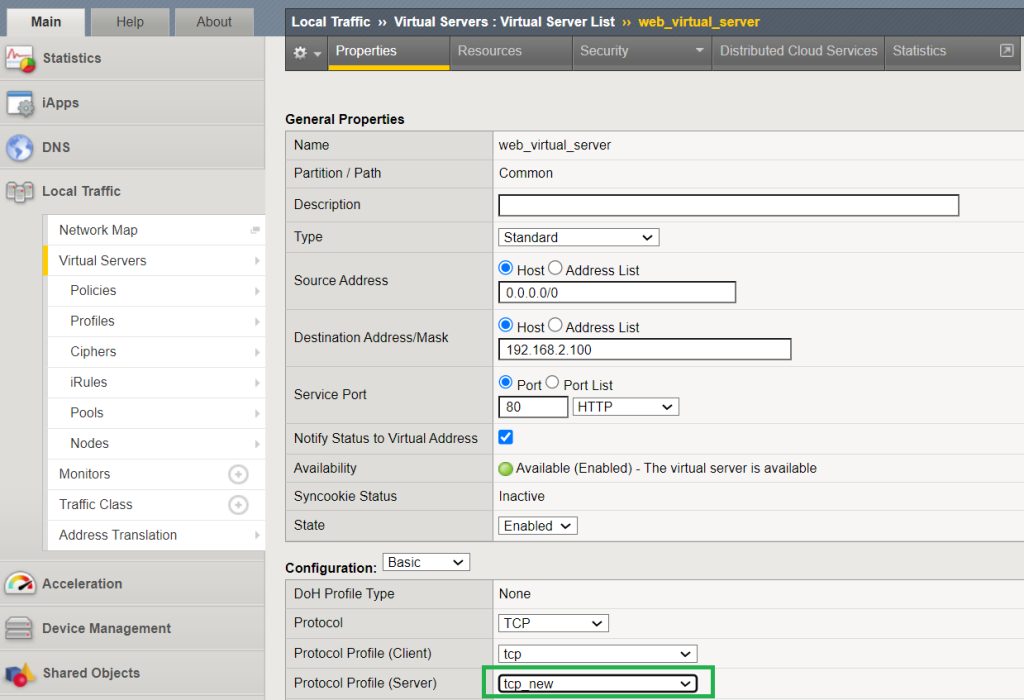
In the next step, we assign the new profile to the virtual server.
The profile will be assigned to the section, „Protocol Profile (Server)“.
Therefore, in this section, we could change the behavior of a specific traffic passing through the virtual server using the LTM profile.
LTM profile in tmsh
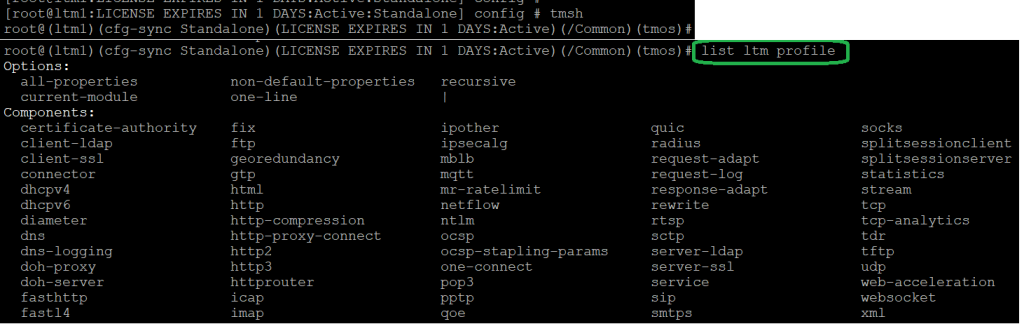
now let’s check to see what is the tmsh version of ltm profile.
With the command „list ltm profile“, we can check the list of supported LTM profiles.
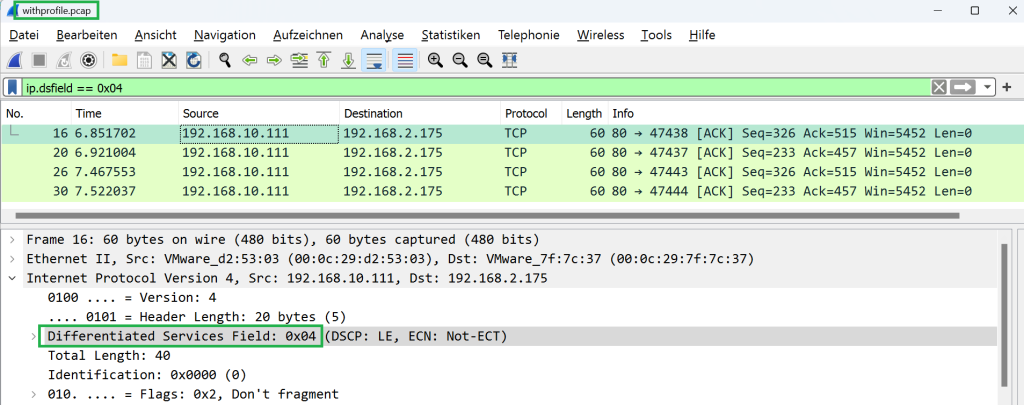
In the output we can also see the new tcp profile created in this section.
root@(ltm1)(cfg-sync Standalone)(LICENSE EXPIRES IN 1 DAYS:Active)(/Common)(tmos)# list ltm profile ... ltm profile tcp tcp_new { app-service none defaults-from tcp ip-tos-to-client 4 } root@(ltm1)(cfg-sync Standalone)(LICENSE EXPIRES IN 1 DAYS:Active)(/Common)(tmos)#
And with the command „list ltm virtual“, we can check how profile is assigned to to the virnetual server.
root@(ltm1)(cfg-sync Standalone)(LICENSE EXPIRES IN 1 DAYS:Active)(/Common)(tmos)# list ltm virtual ltm virtual web_virtual_server { creation-time 2023-09-13:16:01:22 destination 192.168.2.100:http ip-protocol tcp last-modified-time 2023-09-29:17:03:23 mask 255.255.255.255 pool we_server_pool profiles { tcp { context clientside } tcp_new { context serverside } } serverssl-use-sni disabled source 0.0.0.0/0 translate-address enabled translate-port enabled vs-index 3 }