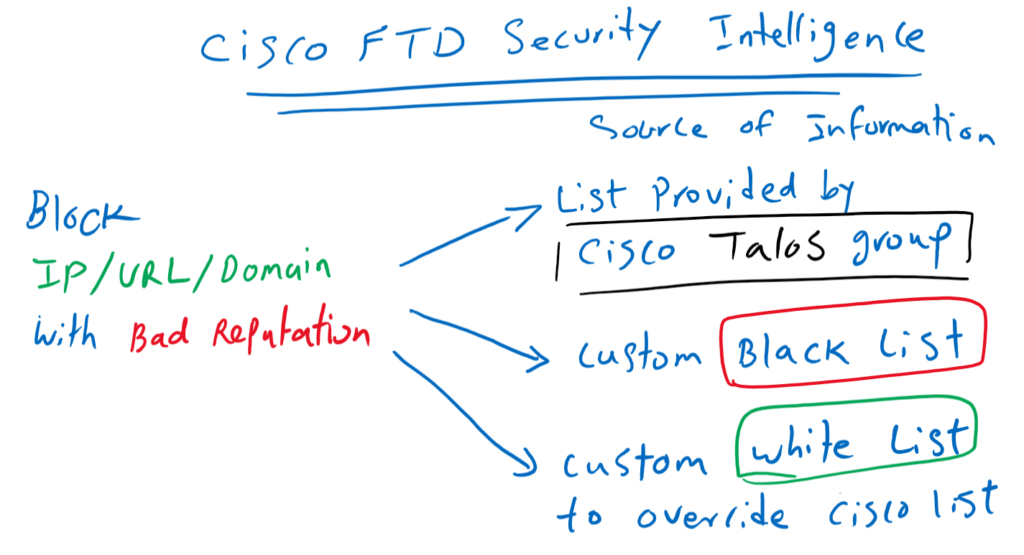
Cisco FTD Security Intelligence is used to black IPs, URLs and Domains with bad reputation. It uses mainly a database created by cisco Talos Security Group which periodically update the list of malicious senders and contents.
In this section, we will talk about security intelligence to block IPs and URLs with bad reputation. Blocking malicious domains will be discussed in the next video since the process is somehow different.
what is Cisco FTD security intelligence?
The main task of security intelligence is to protect you from malicious content on the Internet without doing a deep traffic inspection and just based on their reputation collected by cisco security Talos group.
You can also create your custom blacklist to filter based on your own list or the list provided by third party companies.
This is also possible to whitelist an IP, URL or a domain that was by mistake blocked from one of the provided lists.
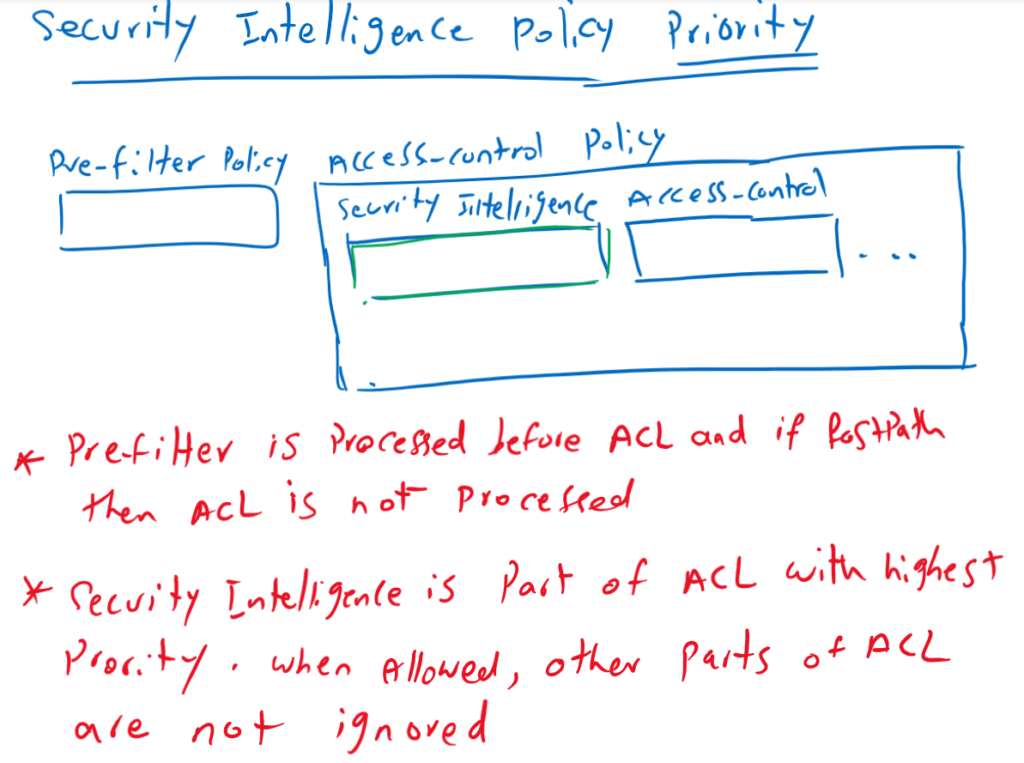
Security Intelligence Policy priority
Security Intelligence is an first level of access control, before FTD performs more resource-intensive deep inspection. it improves performance by quickly excluding traffic that has bad reputation and does not require inspection.
Comparing Security Intelligence and pre-filter Policy
To compare with pre-filter policy, pre-filter policy hast higher priority and it is not part of access control modules. It is used to fast forward a type of traffic and ignoring any access control modules and rules.
But with security intelligence, traffic that doesn’t have a bad reputation and isn’t part of a blacklist is processed by other access control modules and rules before allowing the traffic.
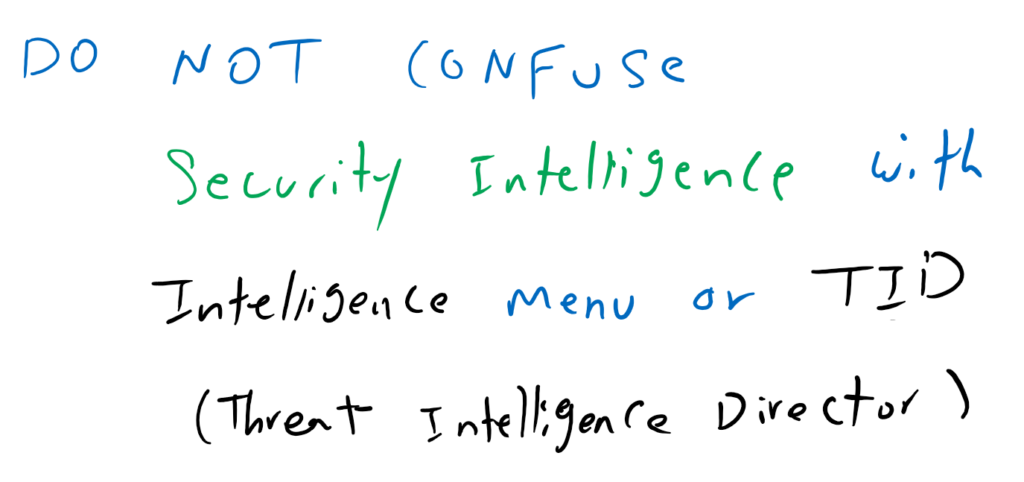
Security Intelligence versus TID
In FMC there is menu with the name of “intelligence” or a reputation list with the name of TID (Threat Intelligence Director). However it does mostly the same as security intelligence but it is a different feature and we will talk about it the next few videos.
Configure Cisco FTD Security Intelligence
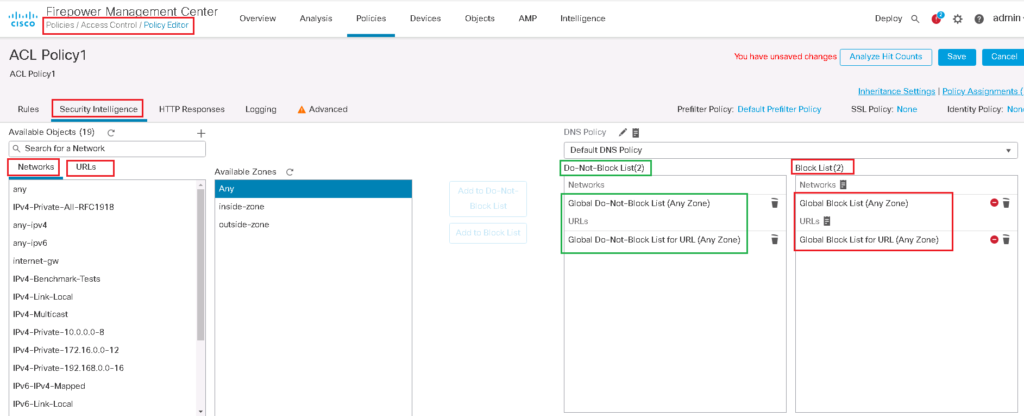
Security intelligence is enabled by default and you can find it in “security intelligence” tab in access control policy.
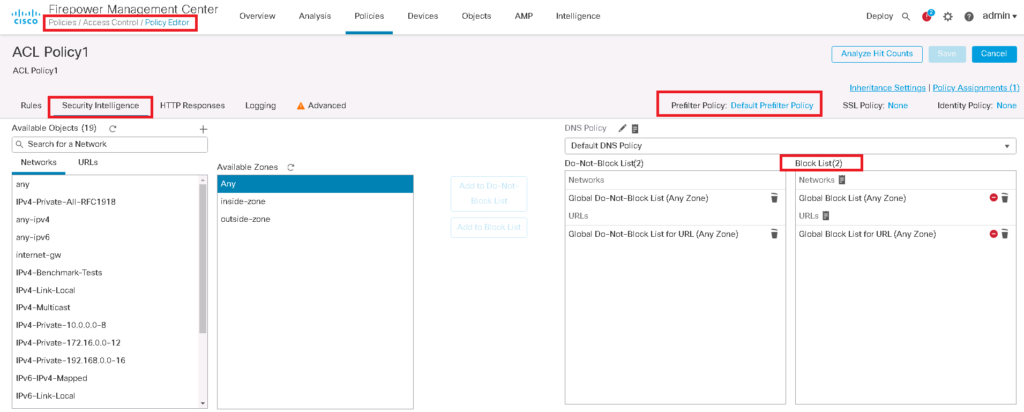
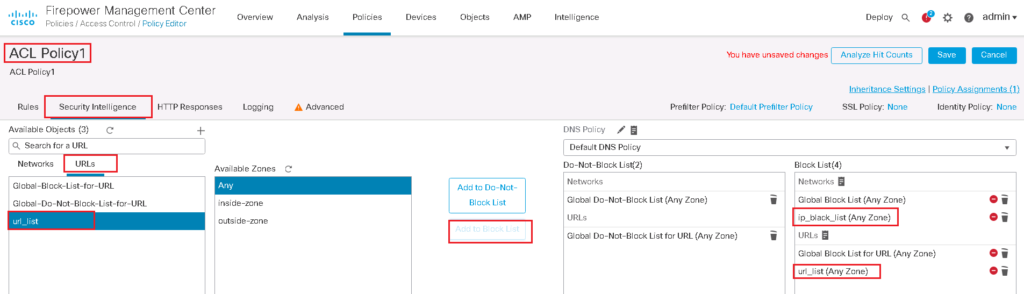
As you can see, there are two types of resources that security intelligence can block. “Networks” which contain IP addresses and “URLs”, which of course contain URLs.
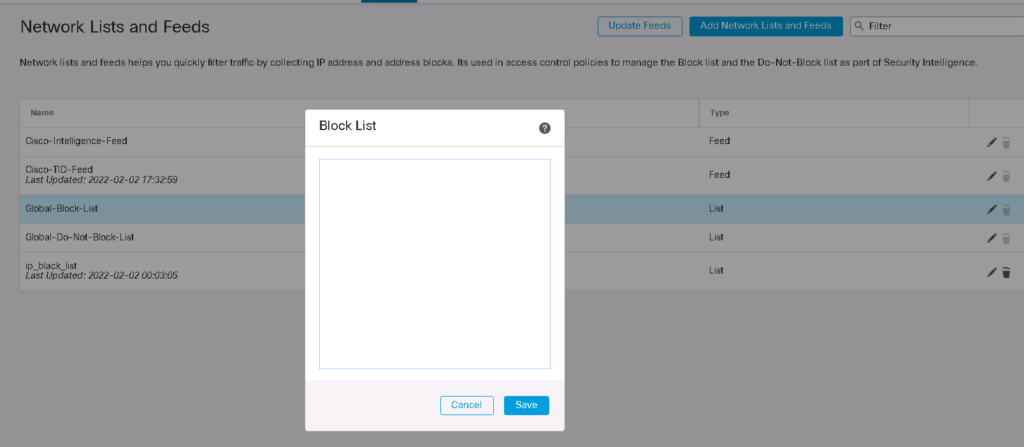
Any IP addresses in “Global Black List” and any URLS in “Global Black List for URL” are blocked. By default there is no IP or URL in this list. I will show you in a few minutes how these list will be updated.
Also any IP addresses in “Global Do-Not-Black List” and any URLS in “Global Do-Not-Black List for URL” will be exempted from blocking even if they are in dynamic Talos or any other black lists. It is because some resources are blocked in dynamic list by mistake.
Security intelligence Lists and Feeds as Objects
But where is the main dynamic cisco Talos security group black list? And how it can be updated?
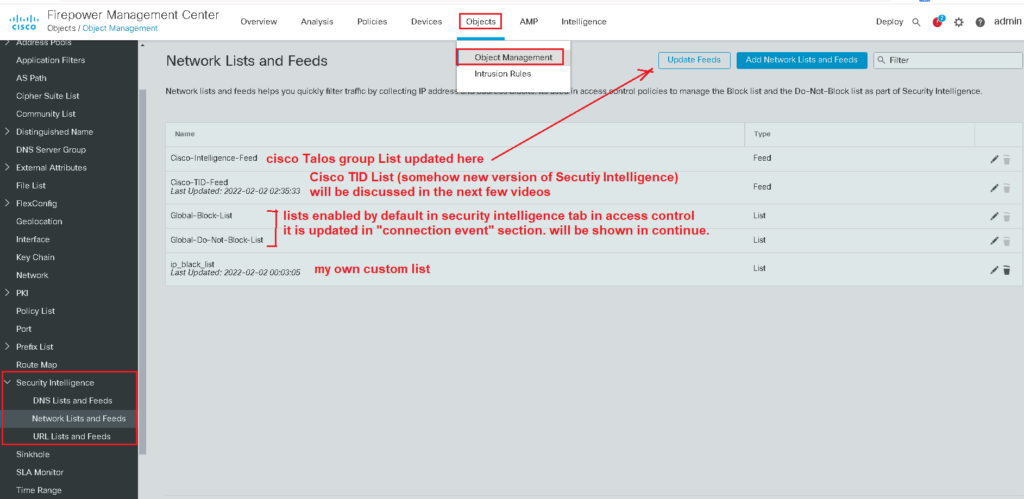
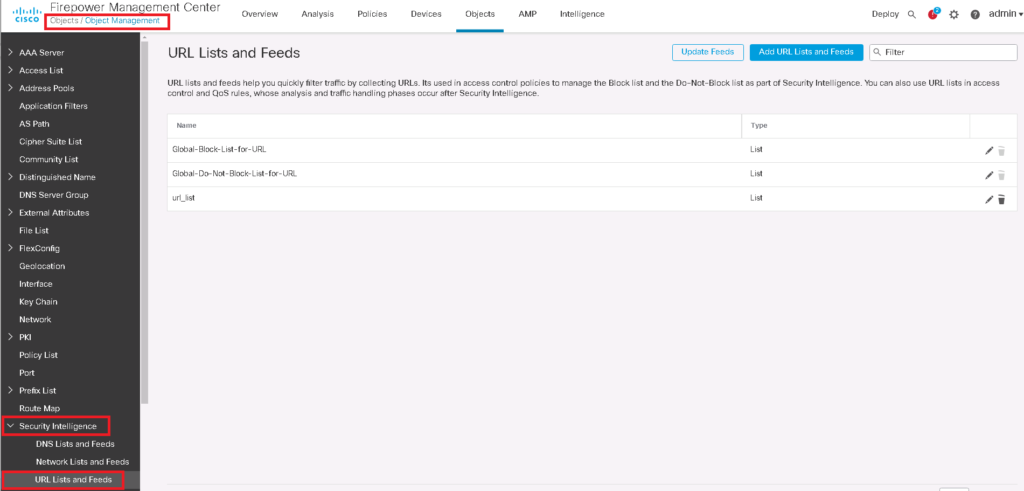
cisco Talos security group black list or any custom list can be updated and configured, preferably through “Object Management” in “Objects” menu. Here you can find “Security Intelligence” section.
“DNS Lists and Feeds”, “Network Lists and Feeds” and “URL Lists and Feeds” are three sub-sections in “Security Intelligence” section.
For example in “Network Lists and Feeds”, “Cisco-Intelligence-Feed” is the black list created and updated by cisco security Talos group and it an be updated with “Updated Feeds” button. You cannot see the content of the feed, but you can just update it.
Cisco-TID-Feed is “Threat Intelligence Director” feed with similar usage but more flexibility which we will talk about in the next few videos. It also can also be updated with “Updated Feeds” button.
Update Global Block List
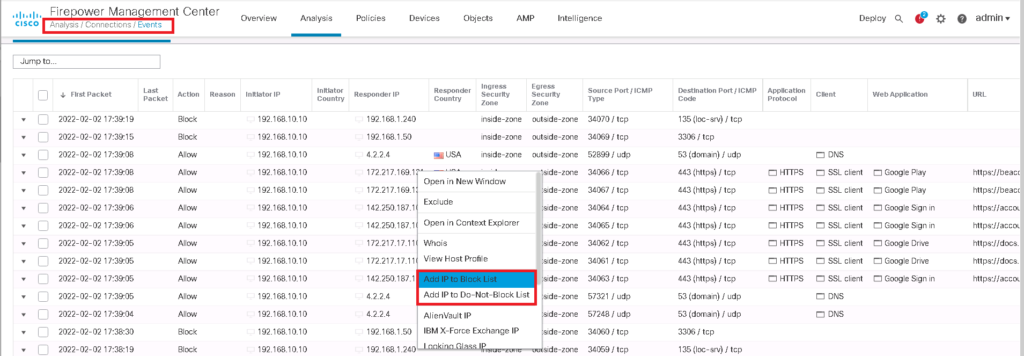
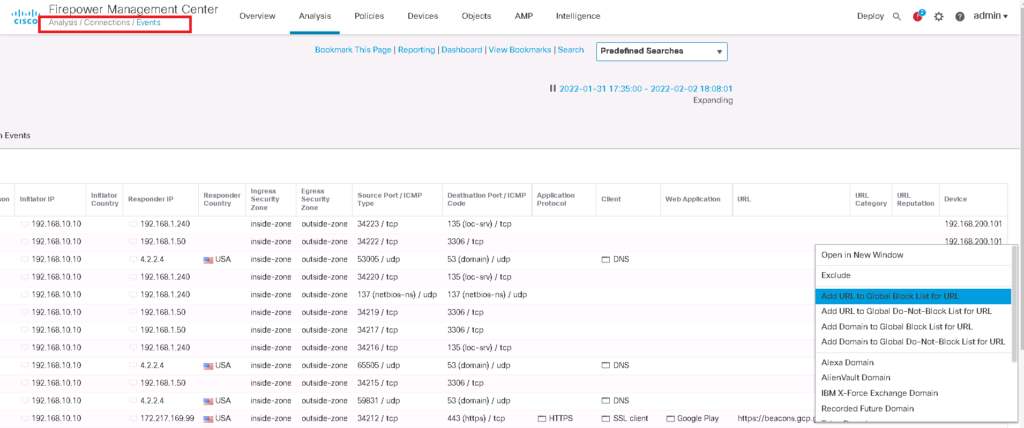
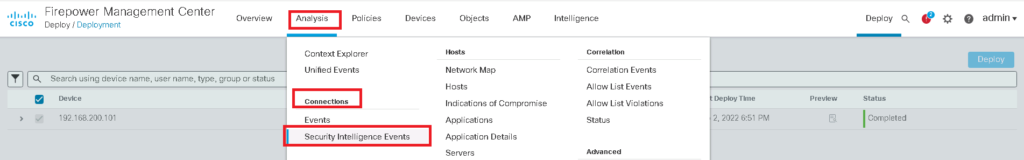
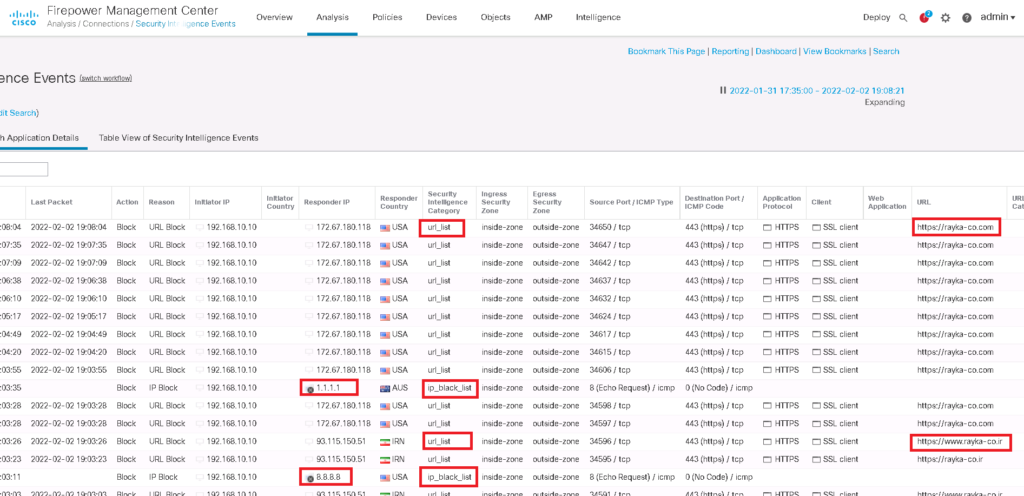
“Global-Black-List” and “Global-Do-Not-Black-List” are the lists that are empty by default and you can update them through connection events. You have to just “right click” over any IP address in connection events and then choose “Add IP to Block List” or “Add IP to Do-Not-Block List” that you think must be added in black list or must be added in whitelist and override dynamic feeds.
Then the IP address will be automatically added to “Global-Black-List” and “Global-Do-Not-Black-List”.
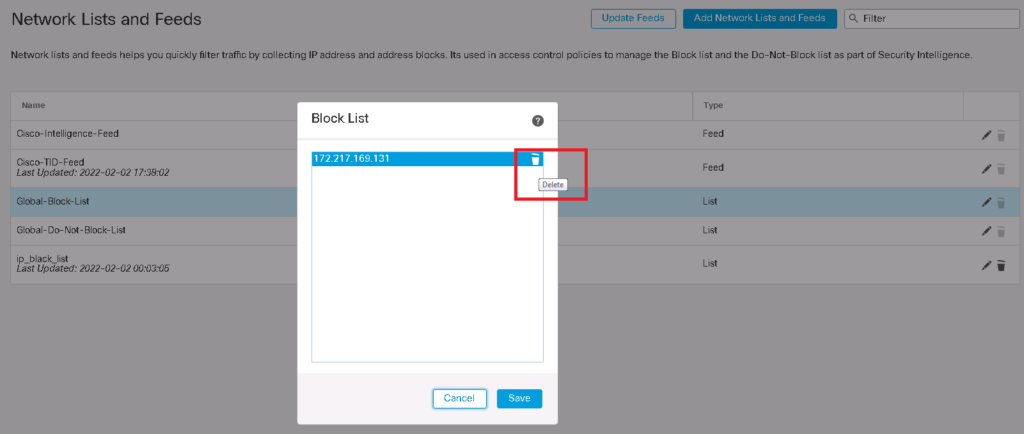
It is but possible to delete a record directly from “Global-Black-List” and “Global-Do-Not-Black-List” objects.
Add Security Intelligence Custom List
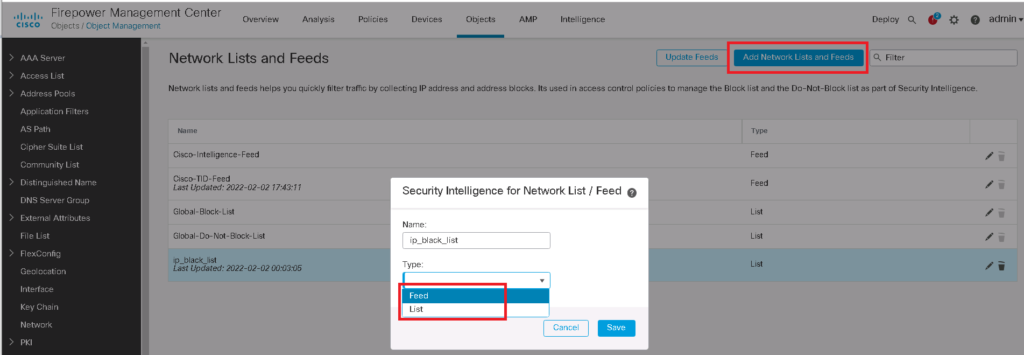
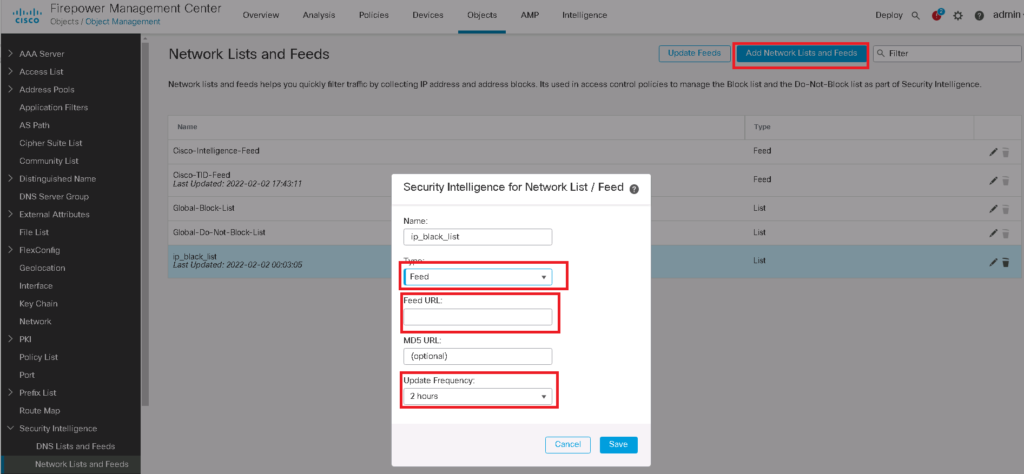
You can also add your custom list. Just click “Add Network Lists and Feeds”. There are two options to add a custom list. “Feed” and “List”.
With the “Feed” option you specify a URL address at which FTD can retrieve the list and also dynamically update it.
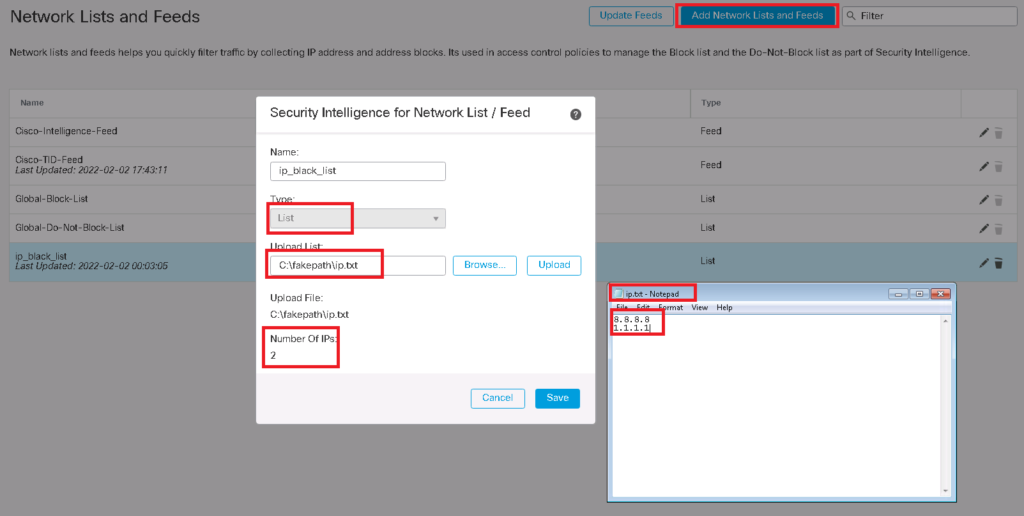
With “List” option you give the list and update it manually. In our example I give the list manually with browsing “ip.txt” file which include two IP addresses. “8.8.8.8” and “1.1.1.1”
Security Intelligence URL Lists and Feeds
The same rules apply to “URL Lists and Feeds”. With “Update Feeds”, the list created by Talos Group will be updated.
You can add a new URL to “Global-Black-List-for-URL” and “Global-Do-Not-Black-List-for-URL” through connection events like what we have done for IP addresses.
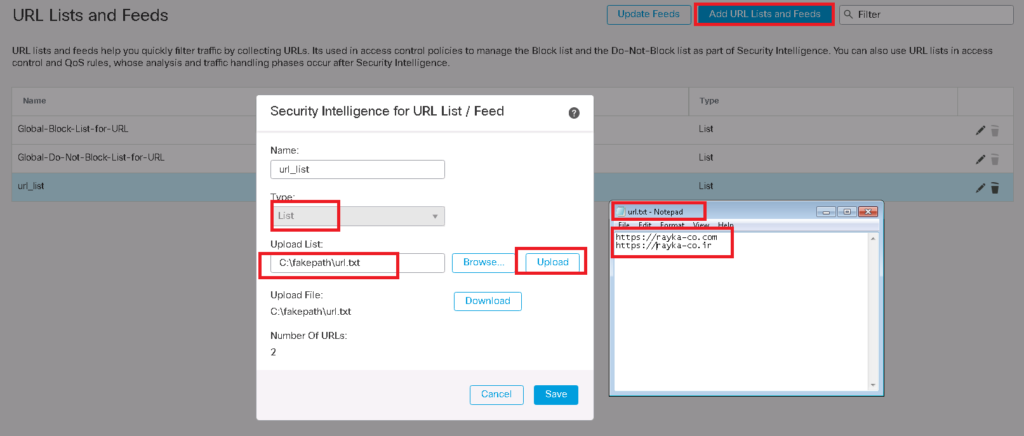
You can also add your custom URL list. Just click “Add URL Lists and Feeds”. Like custom network list, there are two options to add a custom list. “Feed” and “List”.
Here I add a manual list which includes two URL addresses , “rayka-co.ir” and “rayka-co.com”.
Monitoring Cisco FTD Security Intelligence
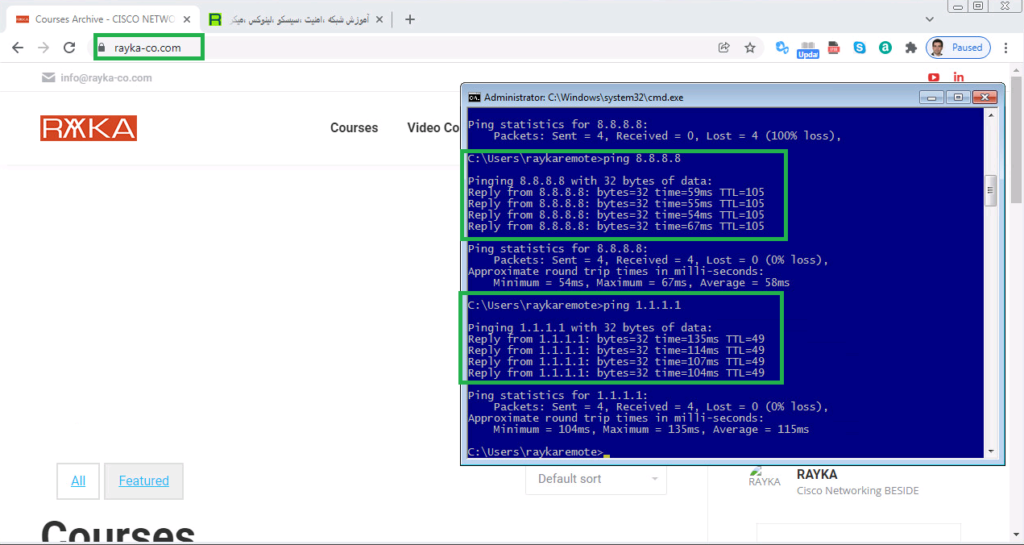
Before applying my custom network and URL lists to security intelligence, I will check to make sure that the connections to these address are already open.
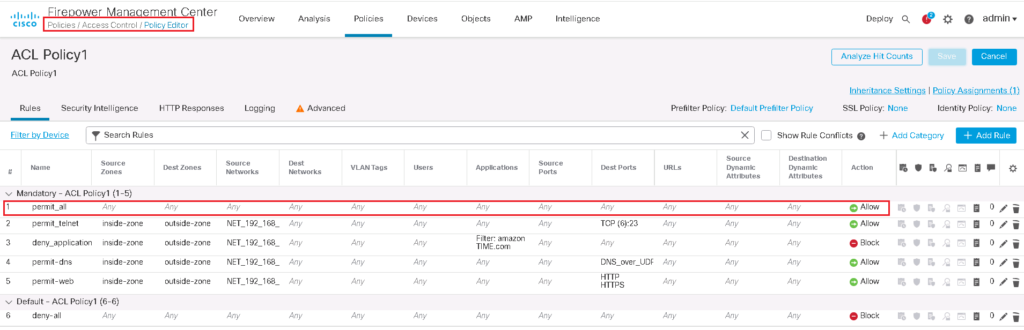
But to make sure that we are not effected by pre-filter policy and also ACL Policy, I will restore pre-filter policy to “Default Prefilter Policy” which has no rules. We will also add “permit all” rule in top of ACL policy to permit every traffic.
Now we can test the connectivity to URLS, “https://rayka-co.ir” and “https://rayka-co.com” and also ping the IP addresses “8.8.8.8” and “1.1.1.1”.
Now we can enable our custom lists in Security Intelligence. then we check the connectivity and also the logs to make sure our security intelligence policy is working properly.