Cisco FTD High Availability makes two FTD devices to be failover that means if primary device fails, the secondary device takes over to forward the traffic.
Cisco FTD High Availability Fundamentals
FTD supports Active/Standby failover, where only active device forward the traffic. When a failover occurs, standby unit becomes active to take over the traffic.
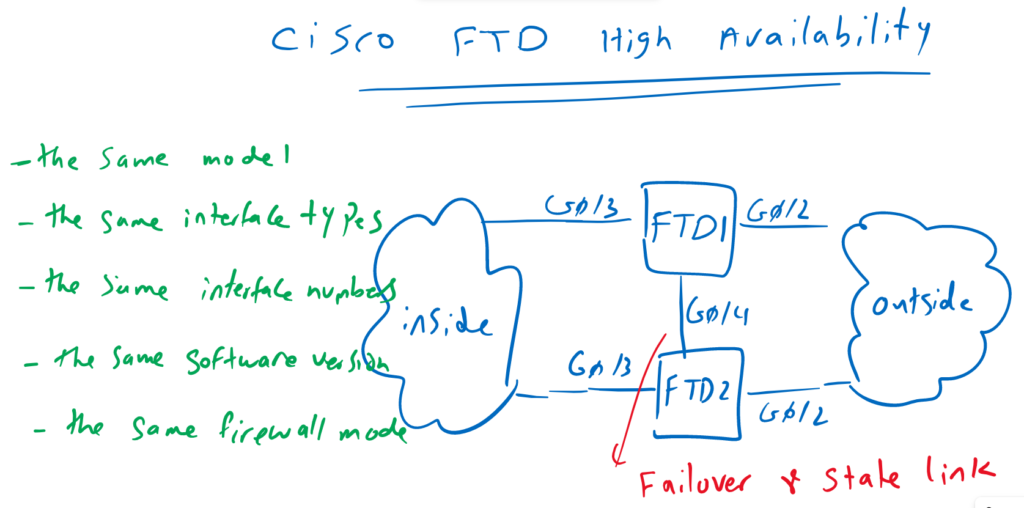
Configuring FTD HA requires that two identical FTD devices connected to each other through a dedicated failover link and, optionally, a state link. The same link can be used for both failover link and state link.
identical devices means that FTD devices must be the same model with the same interface type and number of interfaces. Software version and Firewall mode must also be the same.
Over failover link, status of each device is monitored and the configuration is also synchronized.
Over state link, connection state information like session table and NAT table are synchronized, so that if a failover occurs, existing connections are not disrupted.
Cisco FTD High Availability Configuration
I have already have an active FTD with transparent firewall mode and inline IPS mode in the network.
To configure HA, I have already installed a new FTDv without any configuration.
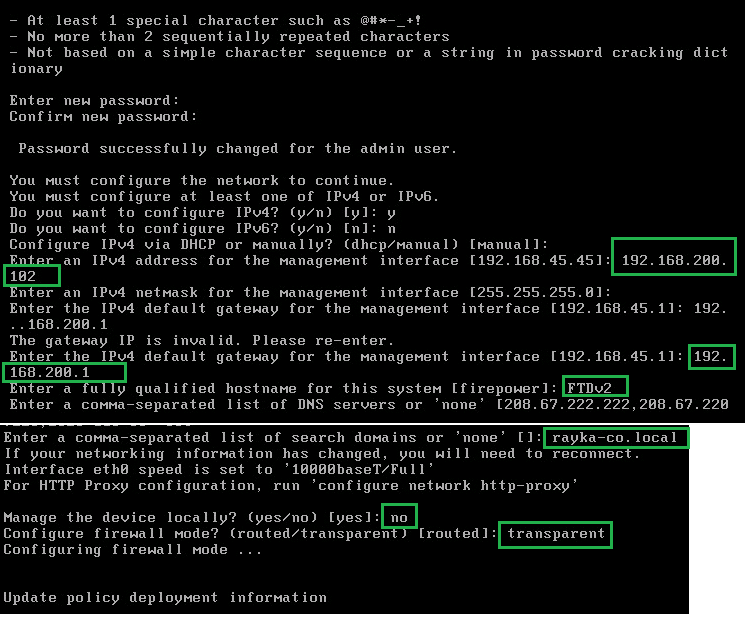
We login with default admin/Admin123 credential and we will setup the second FTD like the first FTD as transparent mode.
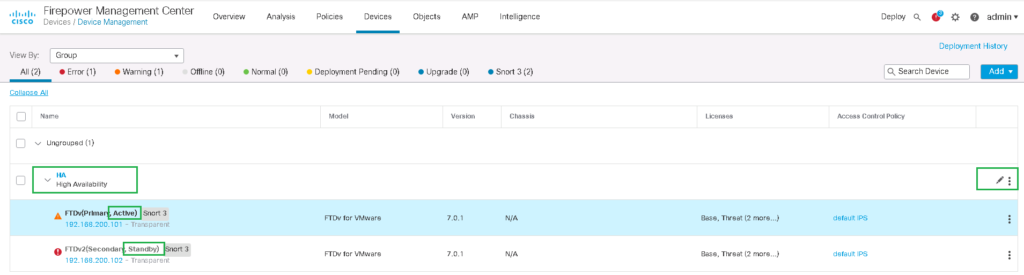
The management IP address of first FTD is 192.168.200.101. we configure the management IP address of second FTD as 192.168.200.102.
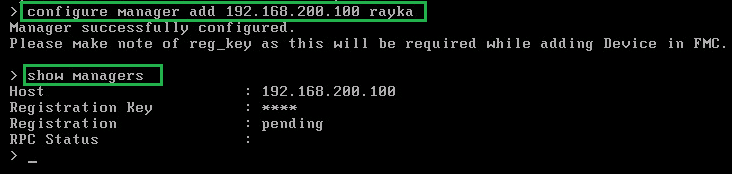
Then we will configure the second FTD to connect to existing FMC, with IP address 192.168.200.100 with “configure manager add 192.168.200.100 rayka” command.
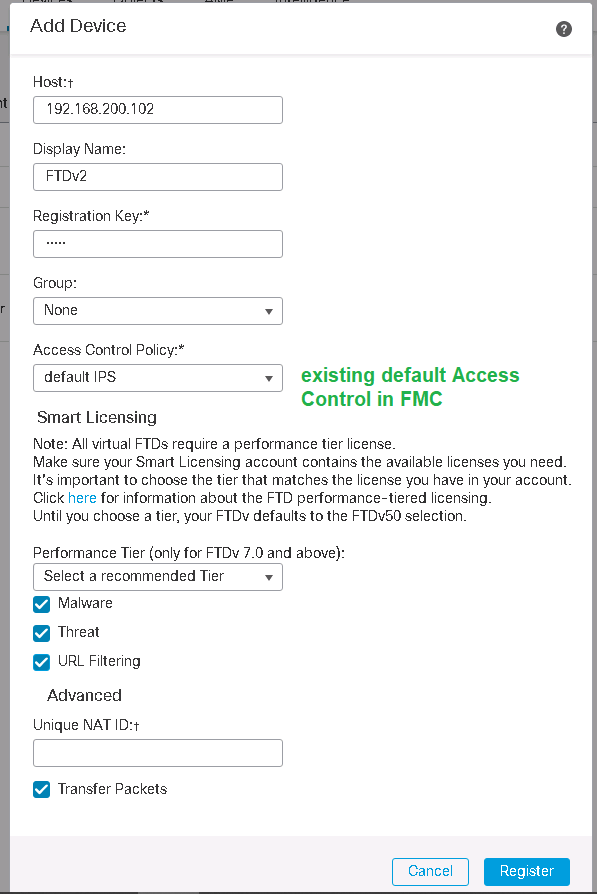
We also add also new FTD with IP address of 192.168.200.102 in existing FMC.
Devices -> Device Management -> Add -> Device
Then make sure that all the changes are deployed.
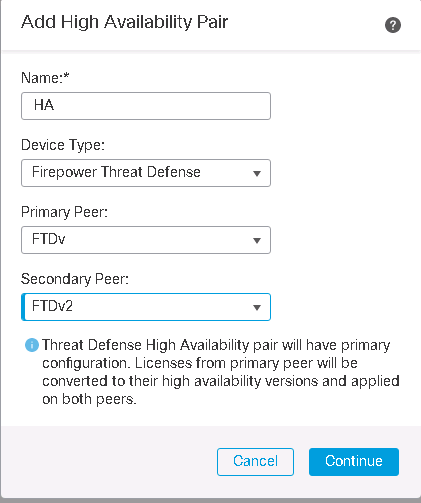
The we will add the second FTD as HA in Devices -> Device Management -> Add -> High Availability
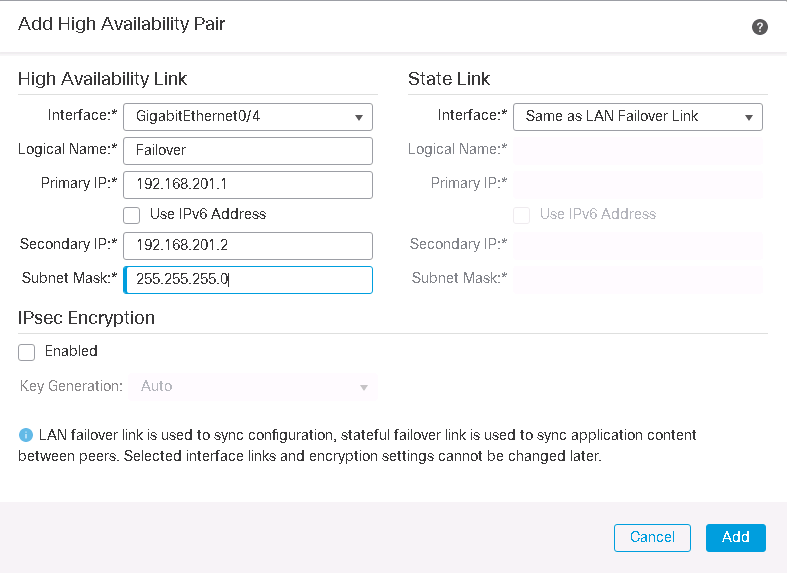
In High availability configuration, I choose Gi0/4 as both failover link and state link. I configure 192.168.201.1 in primary side and 192.168.201.2 in secondary side of failover link.
then both devices will appear under a HA configuration showing the high availability configuration. You cannot configure each device separately, you can only configure HA that publish the configuration in both devices.
If we click over HA, we can monitor or edit HA settings. In this section, failover link and state link properties are displayed. It show also which interfaces are monitored.
we can also change failover trigger criteria. By default if one of monitored interfaces are down then failover will take place. Peer and also interface poll timers and hold timers can be changed from seconds to milliseconds to reduce reaction time.
I change as example, the timers as follows:
Peer Poll Time: 1 sec, Peer Hold Time: 3 sec, Interface Poll Time: 5 sec
Check the operation of Cisco FTD High Availability
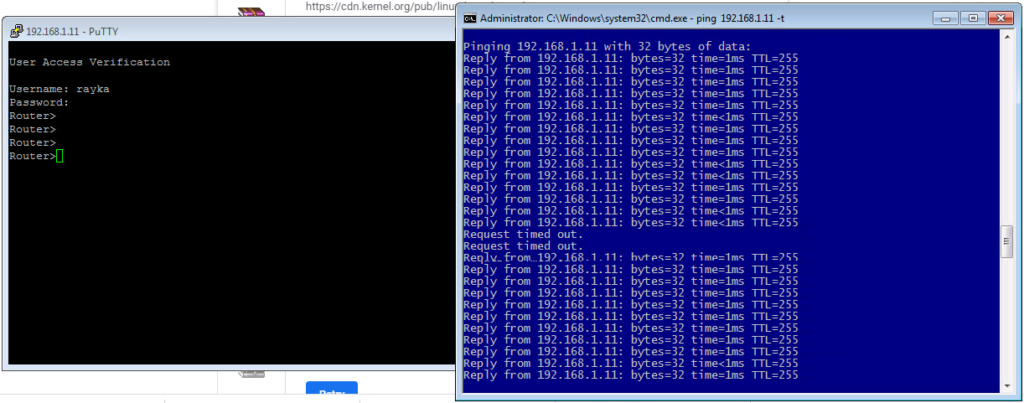
To check if FTD HA works, I will ping and also telnet from inside to outside. Then I disconnect one of the monitored links of active FTD.
It is expected that the second FTD device will be new active device and after a short time, the ping reply will be back. It is also expected that telnet connection will not be disrupted.
Hi thanks for sharing I just have a question here.
When you state inline IPS mode, do you mean that inline sets are configured in your FTDs? Does HA work also when using inline sets?
Hi.
thank you for your message.
with inline IPS mode, exactly I mean as you said.
there is no limitation to run HA when configuring inline set. configurations and stated are replicated through failover and stat links.
Thanks. Majid
Thank you.
Just one omore question based on your experience. Is it possibe for the inside vlan to be different from the outside vlan? While in HA.
Switch access Vlan 10 → (inside) FTD (outside) → switch access vlan 20
Mr. AssadPoor Thank you For content, i have one question is it possible we have active/active FTD?
As far as I know, this wasn’t possible because it requires multiple contexts. But I’m not up to date.