Cisco Firepower Active Directory integration is a prerequisite for identity-based access control. In this section, you will learn how to integrate Cisco FMC with Active Directory. In the next section, we continue the discussion to enable identity-based access control in the network.
Cisco Firepower Active Directory Integration Configuration
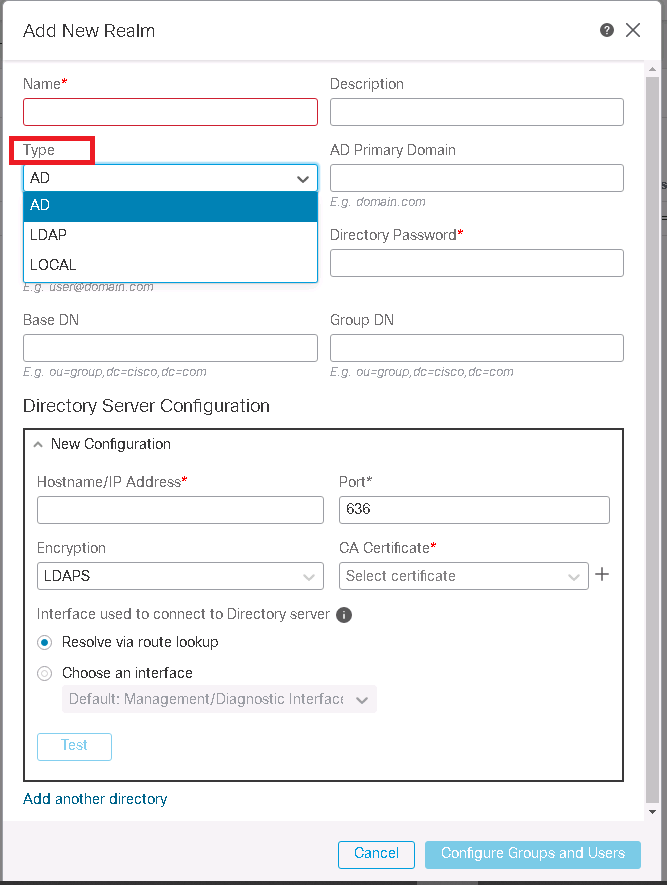
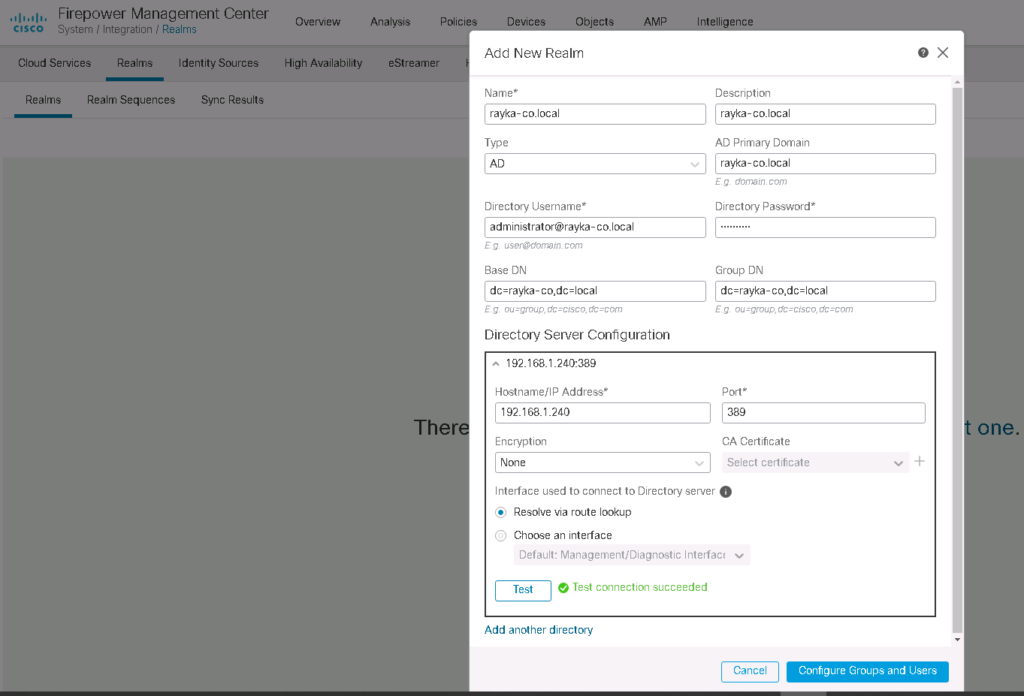
In System -> Integration -> Realms -> Add Realm, we add a new Realm.
A realm consists of one or more LDAP or Microsoft Active Directory servers. We have to configure a realm to perform user and user group queries. After configuring realm, FMC can download a list of users and groups from the servers. Then we have the option to configure identity policy.
There are three types of realm supported by Cisco FMC. Active Directory, LDAP and Local. We configure Active Directory in our Example.
After we add realm, we have the option the test the connectivity between FMC and configured Directory Source. as you can see the test result is successful.
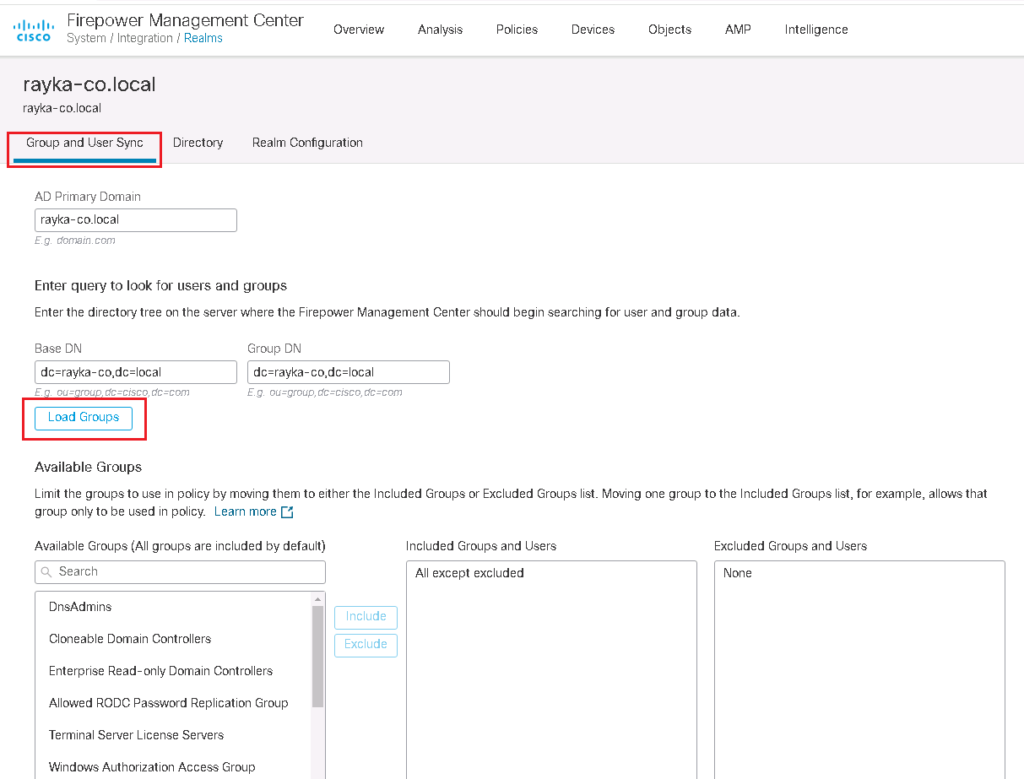
After realm configuration, we can load active directory groups and include or exclude the group which will be used in Cisco FMC or will not be used. by default all users and groups are included.
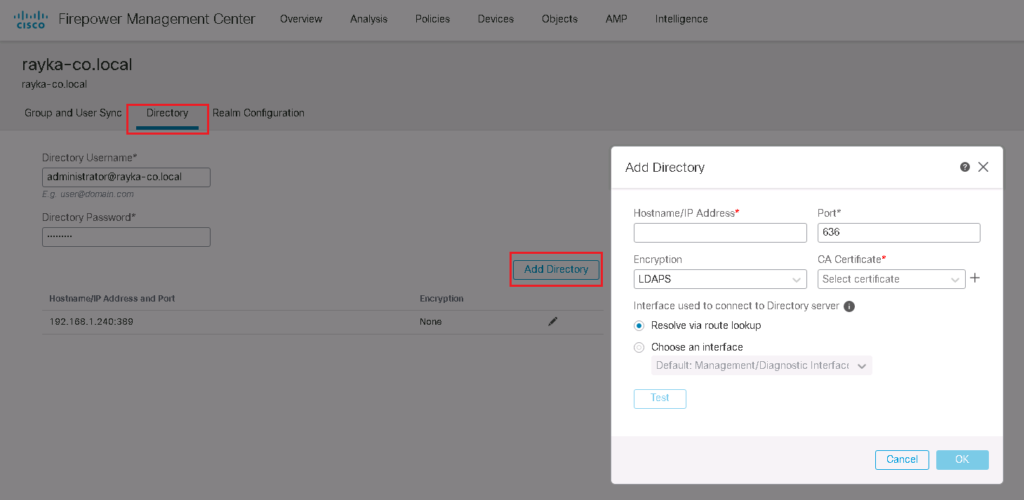
In Directory tab, we have the option to add multiple server or domain controller.
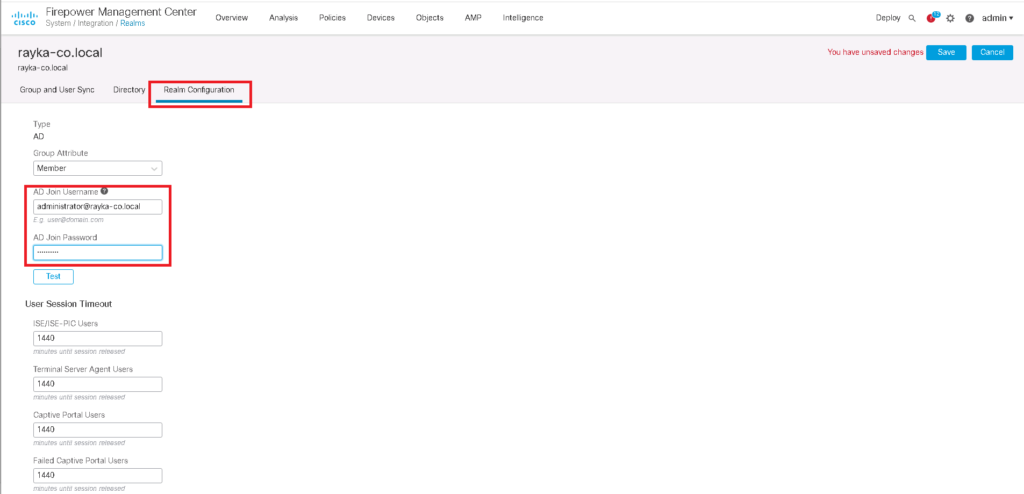
In “Realm Configuration” tab, you can add username and password that FMC can join to the Active Directory.
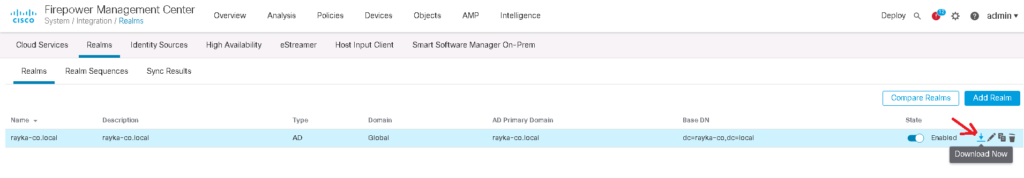
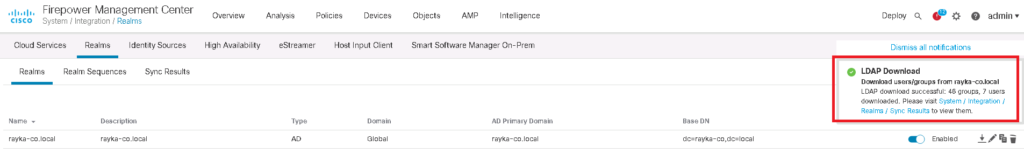
After finishing the configuration, we have the option to download the latest users and group information from Active Directory.
In “Sync Results” tab, you can make sure if Active Directory Information are up to date.