Cisco FTD Overview and Features
Cisco FTD (Firepower Threat Defense) is a Cisco Next Generation Firewall and IPS solution for securing networks and applications. It also includes many other security features that are introduced in this section as an introduction.
Cisco FTD Overview
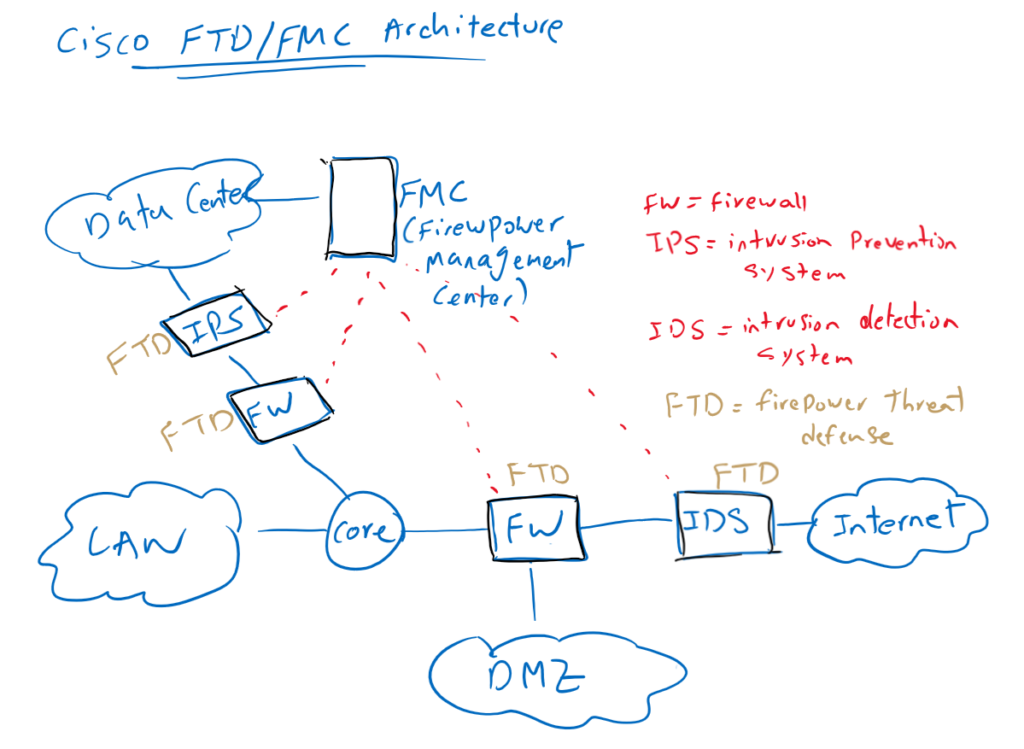
You may have different security solutions in different parts of the network. In our topology there is an IDS solution for analyzing the incoming data traffic to the enterprise before they are inspected by firewall. The IDS solution outside of the network is typically used to only monitor and analyze traffic and not to prevent intrusions.
Then a firewall at the edge of the enterprise network is used to control and allow traffic based on enterprise policies. Only IP addresses, port numbers and applications that are needed in enterprise are allowed and all others are discarded.
Edge firewall is also used to isolate traffic from different zones. For example, incoming traffic destined for DMZ zone must never enter the company’s LAN or data center area. Servers that need to be accessible over the Internet are usually hosted in the DMZ part of the network which is isolated by firewall.
Usually special firewalls and IPS are used in the data center. IPS in the data center are often configured in prevention mode to prevent any intrusion into internal servers.
All of these security solutions and many other solutions can be implemented with the Cisco FTD physical or virtual solution.
All physical and virtual FTD appliances can be centrally managed through Cisco FMC (Firepower Management Center), which is the focus of this course.
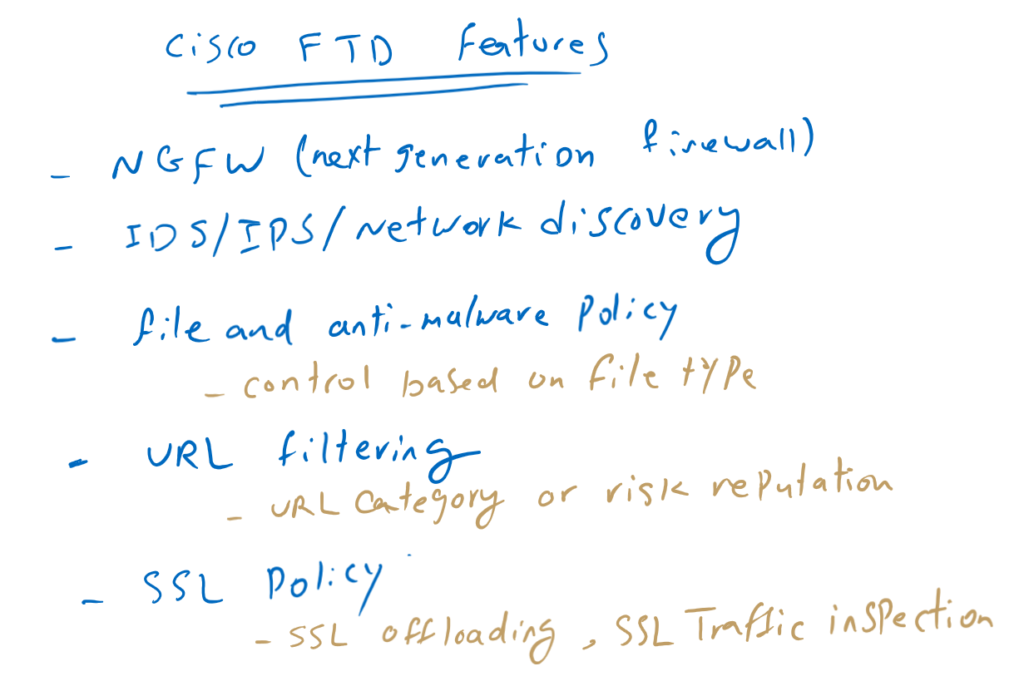
Cisco FTD Features
Before going into the implementation details of Cisco FTD/FMC solution, it is not bad to have an idea of the features that are supported in this solution.
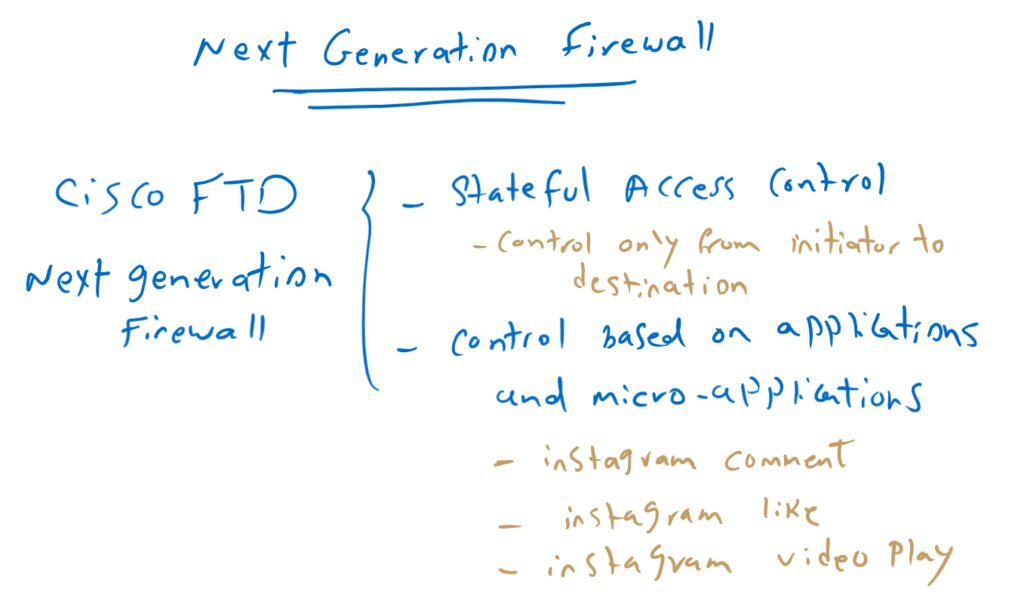
Next Generation Firewall (NGFW):
The next generation firewall allows us to control inbound and outbound traffic between each pair of zones based on enterprise policy. Only IP addresses, port numbers, applications, and micro-applications that the enterprise requires are allowed. All other traffic is discarded.
we call it next generation firewall because not only does it support stateful access control, but we can also easily filter based on many applications and micro-applications that were not easy to configure in the old version of Cisco ASA firewall. Cisco FTD is the mix of Cisco ASA and Sourcefire Firepower solution purchased by Cisco Company.
By stateful access control, we control traffic only from initiator to destination. Reverse traffic will be automatically allowed since the session is already created and the state of session is recorded in the memory.
The next generation firewall allows us to control traffic based on application and micro-applications. For example, we can not only control whether Instagram is allowed, but also whether likes or comments or the playing of videos is allowed on Instagram.
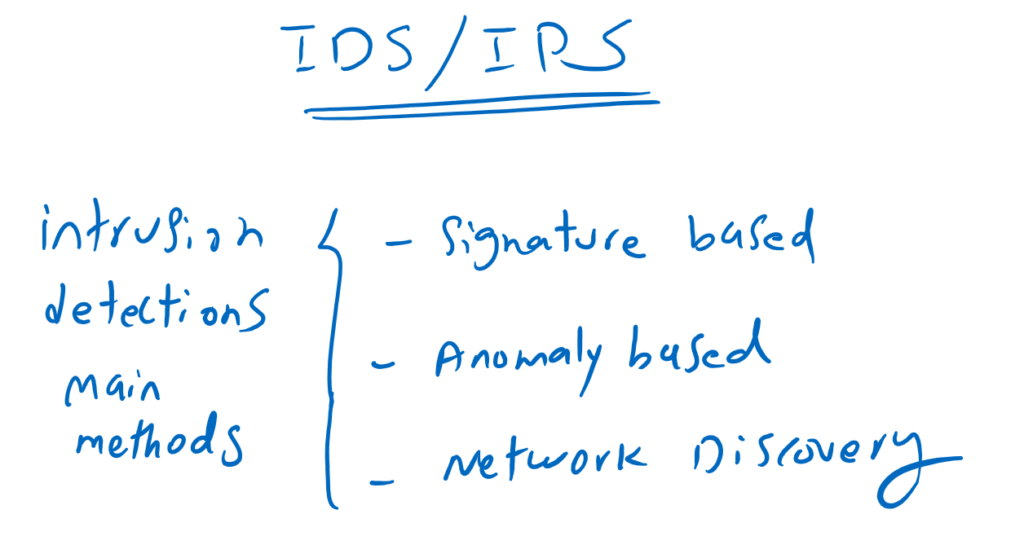
IPS/IDS/Network Discovery:
With Cisco FTD IDS/IPS, many intrusions are detected and prevented based on signatures and anomalies. Intrusions which are known are detected based on signatures but zero attacks are normally detected based on anomaly behaviors.
IPS not only prevent intrusions but always is listening and learning enterprise traffic. Anomalies are traffic that is new behavior that appears to be attack. Of course, there can be many false detection (false positive) with anomaly-based detection. normal traffic which will be detected as attack.
With Cisco FTD network discovery, all or specific part of traffic can be analyzed to find out what is happening on the network based on the host. Which device is connected? Is it a cell phone or a desktop? Exactly which cell phone or desktop model is sending the data traffic. what applications are installed on each host. What traffic is sent and received in each host. Network discovery answers all of these questions.
Cisco FTD Malware and File Policy:
Cisco FTD gives you the ability to control any type of file to be monitored or filtered, whether it is malicious or not. You can also forward them to anti-malware engines to make sure they are not malicious before they will be sent to the final users.
Cisco FTD URL Filtering:
With URL filtering, you can not only filter or allow a specific URL, but also control URLs based on the website category. For example, all drug related websites are in a specific category that can be filtered at once.
We also have the option to filter based on risk reputation. Any website can have a reputation in which how much they can be risky. We can filter all URLs with high risk reputation at once.
SSL Policy:
With SSL policy, we can decrypt SSL traffic to inspect the content of traffic. this can be possible when firewall replace server certificate with its own certificate to be trusted by internal users.
SSL policy also allows us to implement SSL offloading. With SSL offloading, internal servers are published through SSL tunnel. but inbound SSL traffic are decrypted at the firewall, and traffic between firewall and internal servers can be non-SSL traffic which reduce final server overhead.
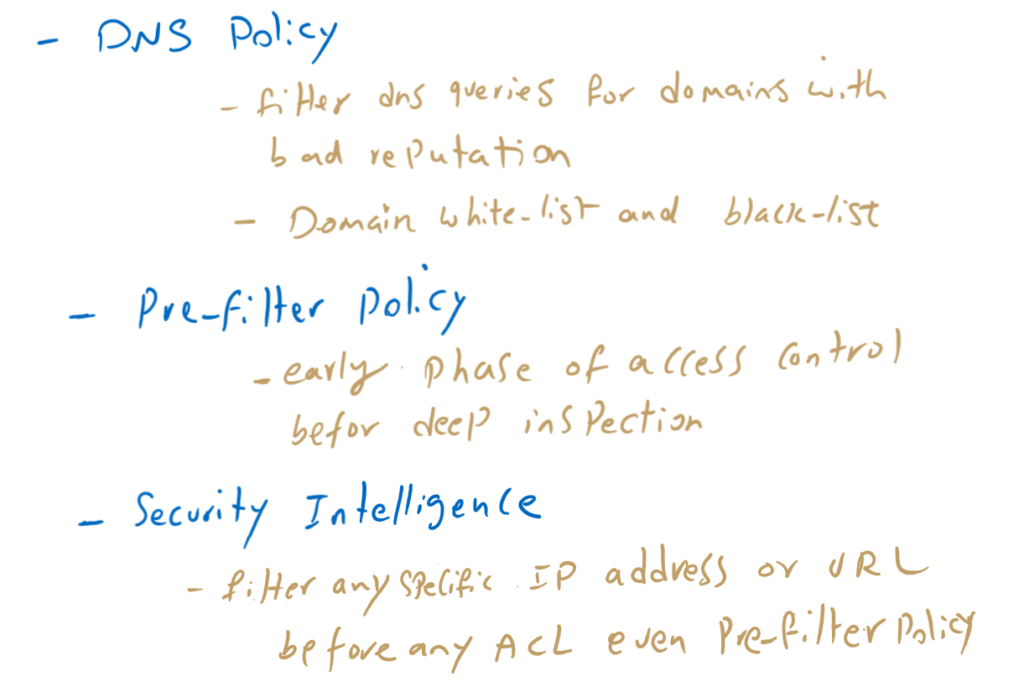
Cisco FTD DNS Policy:
With Cisco FTD DNS policy, DNS queries will be inspected and any DNS query to domains with bad reputation will be dropped.
You can also define your own domain blacklist and white list.
Pre-filter policy:
The pre-filtering policy allows us to discard some of traffic before firewall inspect it deeply which reduce Cisco FTD overhead. For example, if you want to filter inbound Telnet traffic from Internet as a whole, you can write the policy in pre-filtering section to discard it as soon as possible before it gets into the deep inspection engine.
Cisco FTD security Intelligence Policy:
With cisco FTD security intelligence, you can filter based on IP address and also URL before access control policy even before pre-filter policy which reduce cisco FTD overhead when you want to filter a specific IP address or URL.
Cisco FTD Identity Policy:
With Cisco FTD Identity Policy, you can write ACL rules based on identity instead of IP address. mapping of Identity and IP address are automatically resolved through Active Directory or Cisco ISE pxGrid technology.
These are not the only features supported by Cisco FTD. There are many other features in Cisco FTD like NAT, VPN, High Availability and so on. I will try to discuss and implement all these features except VPN which will be discussed in a different course.