Junos SNMPV3 configuration is the discussion of this section. With the SNMP protocol, we can monitor network devices and servers remotely. SNMP is the most common monitoring protocol used in the networks.
SNMPv2c is the most widely used version of SNMP, which will be discussed first. SNMPv3 is the most secure version of SNMP, which is discussed next.
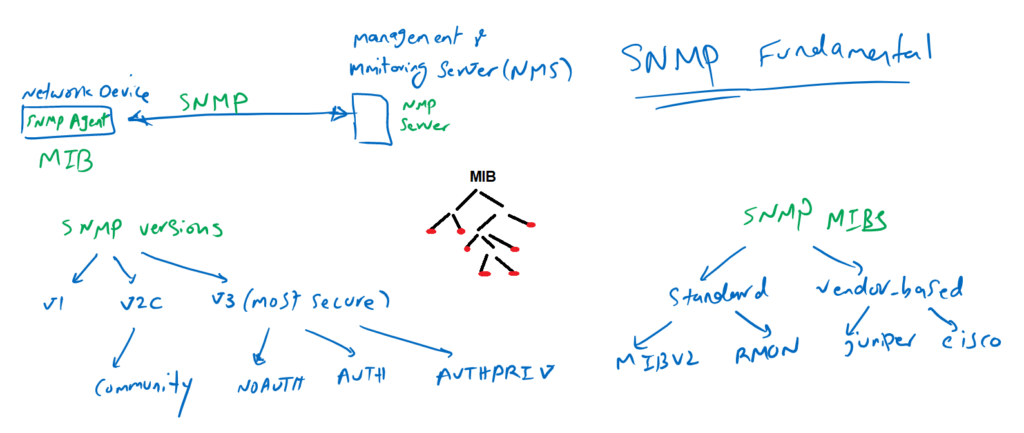
SNMP Protocol Fundamental
As mentioned earlier, SNMP is the most commonly used monitoring protocol in networks for monitoring hardware and software components of network devices and servers.
With SNMP, you can monitor CPU usage, memory usage, disk space usage, device fan status, interface bandwidth usage, interface error status and many other components.
Today nearly all devices supports SNMP and you can monitor them with monitoring software.
To monitor a device, it must support SNMP MIBs. SNMP MIB is the collection of information that we can monitor or manage. They have a hierarchical structure and leaf of MIB tree are the information that we can finally monitor or manage. Each leaf has a specific ID called the SNMP OID (Object Identifier).
There are many MIBs available. Some of them are standard and some of them are vendor-specific. Depending on the vendor and the device, it may support some of these MIBs.
Some of the OIDs in the MIB are just for reading information, but some OIDs support to be changed. For example, OIDs related to CPU usage and memory usage are read-only and you can only monitor the status of these information. But OIDs related to the IP address of the interface can also be changeable. This means that you can change the IP address of an interface via the SNMP protocol.
The SNMP protocol is not famous for configuration change and management purpose and it is mainly used for monitoring purposes. There are many SNMP software with incredible graphs for monitoring network devices. these softwares are called NMS (Network Management & Monitoring System).
The most common version of SNMP is SNMPv2c, which added a password, in other words community, for security compare to version 1 but the password transferred clear text through the network and it is still insecure.
With SNMPv3 you have the option of authenticating and encrypting all SNMP queries and data.
There are three versions of SNMPv3, NOAUTH, where we don’t use authentication and encryption capability of SNMPv3.
AUTH, where we authenticate any SNMP communication, but SNMP data are transmitted in clear text.
And the most secure, AUTHPRIV, where all SNMP communication are authenticated and all SNMP data are also transmitted encrypted.
Juniper SNMP MIB structure
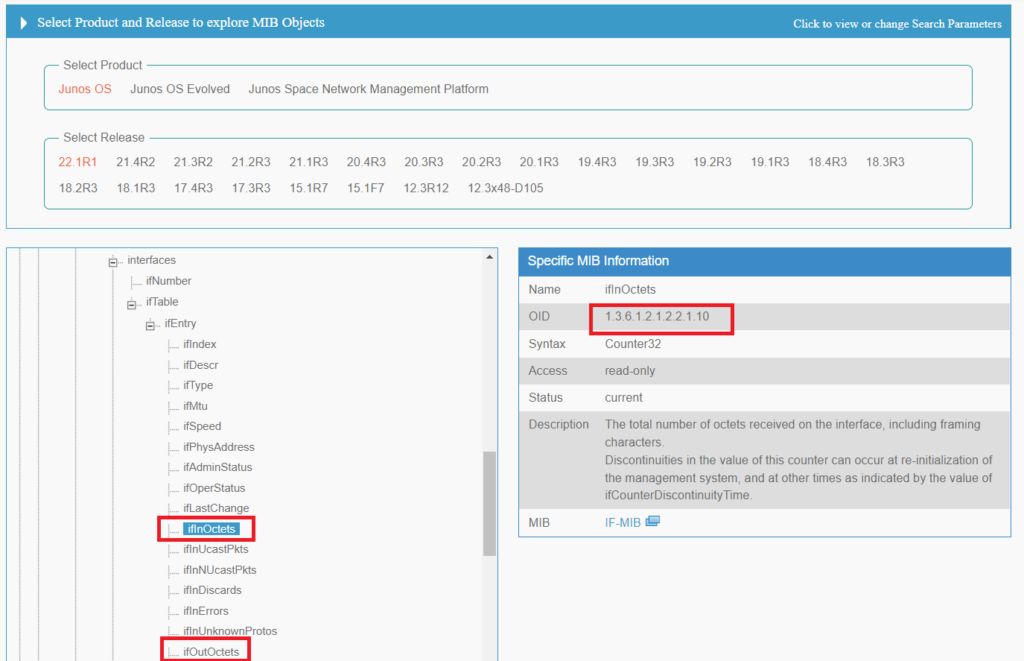
To get an idea of Juniper’s SNMP MIB structure, let’s take a look at it.
In “apps.juniper.net”, you can download and explore Juniper MIB structure. Based on the software and it’s version, SNMP MIB can be somehow different.
One of the most important OID is to monitor the bandwidth usage of an interface, which uses standard MIB2 and its OID for incoming traffic is 1.3.6.1.2.1.2.2.1.10 and OID for outgoing traffic is 1.3.6.1.2.1.2.2. 1.16.
Junos SNMP configuration (SNMPv2c and SNMPv3)
Now it is the time to configure SNMP in Juniper device. At first we configure SNMPv2c and in the next step we will configure SNMPv3
Junos SNMPv2c Configuration
For SNMPv2 configuration, the only required configuration is to give a password which is called SNMP community.
But to make it more secure, you can configure SNMP community to be read-only. Therefore it is not possible to change anything in the network through SNMP community but still it is possible to read important information through this protocol.
The other security step in SNMPv2c is to limit SNMP queries from specific sources. I limit the source to the IP range 192.168.0.0/16.
[edit]
rayka@vSRX1# run show configuration | match snmp | display set
set snmp community rayka authorization read-only
set snmp community rayka clients 192.168.0.0/16
[edit]
rayka@vSRX1# To check the SNMP , we can check it through any SNMP software. but here I check it with my Debian machine using the “snmpwalk” command to query the SNMP MIB tree or a specific OID.
majid@192-168-1-111:~$ snmpwalk -v 2c -c rayka 192.168.1.101
iso.3.6.1.2.1.1.1.0 = STRING: "Juniper Networks, Inc. vsrx internet router, kernel JUNOS 22.1R1.10, Build date: 2022-03-16 10:04:45 UTC Copyright (c) 1996-2022 Juniper Networks, Inc."
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.2636.1.1.1.2.129
iso.3.6.1.2.1.1.3.0 = Timeticks: (319732039) 37 days, 0:08:40.39
iso.3.6.1.2.1.1.4.0 = ""
iso.3.6.1.2.1.1.5.0 = STRING: "vSRX1.rayka-co.com"
iso.3.6.1.2.1.1.6.0 = ""
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
....
majid@192-168-1-111:~$ snmpwalk -v 2c -c rayka 192.168.1.101 iso.3.6.1.2.1.2.2.1.1.5
iso.3.6.1.2.1.2.2.1.1.5 = INTEGER: 5As I have said earlier, the most important OID in network devices is to monitor interface bandwidth. To check bandwidth usage of a specific interface, first we have to find the index of that interface with the command “show interfaces ge-0/0/0 extensive”.
Then we use the “snmpwalk” command to query the interface bandwidth OID, that I introduced earlier, for that specific interface. The output of the command shows the current number of incoming or outgoing bytes on that interface.
[edit]
rayka@vSRX1# run show interfaces ge-0/0/0 extensive | grep SNMP
Interface index: 136, SNMP ifIndex: 510, Generation: 139
Interface flags: SNMP-Traps Internal: 0x4000
Logical interface ge-0/0/0.0 (Index 73) (SNMP ifIndex 520) (Generation 139)
Flags: Up SNMP-Traps 0x4004000 Encapsulation: ENET2
finger ftp tftp ident-reset http https ike netconf ping reverse-telnet reverse-ssh rlogin rpm rsh snmp snmp-trap ssh telnet traceroute
[edit]
rayka@vSRX1#
!
majid@192-168-1-111:~$ snmpwalk -v 2c -c rayka 192.168.1.101 .1.3.6.1.2.1.2.2.1.16.520
iso.3.6.1.2.1.2.2.1.16.520 = Counter32: 3924596
!
majid@192-168-1-111:~$ snmpwalk -v 2c -c rayka 192.168.1.101 .1.3.6.1.2.1.2.2.1.10.520
iso.3.6.1.2.1.2.2.1.10.520 = Counter32: 59975780
majid@192-168-1-111:~$ Junos SNMPv3 Configuration
To configure SNMPv3:
Step1: we create a user in the first step.
It must be configured for each user how securely the user can query OIDs. NOAUTH, AUTH, or AUTHPRIV.
Suppose we choose the most secure version of SNMv3, AUTHPRIV, which has both authentication and encryption.
For authentication a password must be configured. For encryption, an encryption key must be configured.
[edit]
rayka@vSRX1# set snmp v3 usm local-engine user USER1 authentication-md5 authentication-password rayka-co.com
[edit]
rayka@vSRX1# set snmp v3 usm local-engine user USER1 privacy-des privacy-password rayka-co.com
[edit]
rayka@vSRX1# Step2: In the second step we specify to which group the user belongs to.
[edit]
rayka@vSRX1# set snmp v3 vacm security-to-group security-model usm security-name USER1 group GROUP1
[edit]
rayka@vSRX1# Step 3: In the third step, we configure a view that restricts a part of the OID tree that users can access to it.
OID “.1” means that the entire MIB tree is accessible to users.
[edit]
rayka@vSRX1# set snmp view SNMPVIEW oid .1 include
[edit]
rayka@vSRX1#Step 4: in the last step, we specify the group in shich have the right to access to the information specified in the view.
[edit]
rayka@vSRX1# set snmp v3 vacm access group GROUP1 default-context-prefix security-model any security-level privacy read-view SNMPVIEW
[edit]
rayka@vSRX1# We do not have to forget “host-inbound-traffic system-services snmp”. We have still did not talk about this topic but I have configured all system services to be allowed in previous sections.
[edit]
rayka@vSRX1# run show configuration security | match host-inbound | display set
set security zones security-zone untrust host-inbound-traffic system-services all
set security zones security-zone untrust host-inbound-traffic protocols all
[edit]
rayka@vSRX1# let’s review our final SNMP configuration.
[edit snmp]
rayka@vSRX1# show | display set
set snmp v3 usm local-engine user USER1 authentication-md5 authentication-key "$9$0/KY1IcM8XdwYMWxdws4oCtpOBEcylMLx9A0Ihcle8X7d24GDi.mTDj9A0ORElKMLdb4oGDjqKMikqPQz9ApO1hcylMLxKv"
set snmp v3 usm local-engine user USER1 privacy-des privacy-key "$9$Se-leWdbsoZUdVYoZGiHIEhyrvWLxdwY1RSeMWx7bs2oDimfT3nCf51RSyKvxNdwoJiHmf5FNdTzF6At1RhylMWLxdwYN-"
set snmp v3 vacm security-to-group security-model usm security-name USER1 group GROUP1
set snmp v3 vacm access group GROUP1 default-context-prefix security-model any security-level privacy read-view SNMPVIEW
set snmp view SNMPVIEW oid .1 include
set snmp community rayka authorization read-only
set snmp community rayka clients 192.168.0.0/16
[edit snmp]
rayka@vSRX1# Now we can check SNMPv3 connectivity through “snmpwalk” tool.
majid@192-168-1-111:~$ snmpwalk -v 3 -l authPriv -u USER1 -a md5 -A rayka-co.com -x des -X rayka-co.com 192.168.1.101
iso.3.6.1.2.1.1.1.0 = STRING: "Juniper Networks, Inc. vsrx internet router, kernel JUNOS 22.1R1.10, Build date: 2022-03-16 10:04:45 UTC Copyright (c) 1996-2022 Juniper Networks, Inc."
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.2636.1.1.1.2.129
iso.3.6.1.2.1.1.3.0 = Timeticks: (320248626) 37 days, 1:34:46.26
iso.3.6.1.2.1.1.4.0 = ""
iso.3.6.1.2.1.1.5.0 = STRING: "vSRX1.rayka-co.com"
iso.3.6.1.2.1.1.6.0 = ""
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
iso.3.6.1.2.1.2.1.0 = INTEGER: 38
iso.3.6.1.2.1.2.2.1.1.1 = INTEGER: 1
iso.3.6.1.2.1.2.2.1.1.4 = INTEGER: 4
iso.3.6.1.2.1.2.2.1.1.5 = INTEGER: 5
iso.3.6.1.2.1.2.2.1.1.6 = INTEGER: 6
iso.3.6.1.2.1.2.2.1.1.7 = INTEGER: 7
iso.3.6.1.2.1.2.2.1.1.8 = INTEGER: 8
iso.3.6.1.2.1.2.2.1.1.9 = INTEGER: 9
iso.3.6.1.2.1.2.2.1.1.10 = INTEGER: 10
iso.3.6.1.2.1.2.2.1.1.11 = INTEGER: 11
iso.3.6.1.2.1.2.2.1.1.12 = INTEGER: 12
iso.3.6.1.2.1.2.2.1.1.13 = INTEGER: 13
iso.3.6.1.2.1.2.2.1.1.17 = INTEGER: 17
iso.3.6.1.2.1.2.2.1.1.18 = INTEGER: 18
iso.3.6.1.2.1.2.2.1.1.21 = INTEGER: 21
....