Application dynamic parameters are specially generated by web applications primarily for security purposes, to prevent vulnerabilities such as SQL injection, XSS, and CSRF attacks. F5 AWAF has robust capabilities to protect web applications against tampering with these dynamic parameters, ensuring security of your web applications. In this section, we will demonstrate how F5 AWAF effectively mitigates the risks associated with dynamic parameter tampering.
Dynamic Parameter Tampering and Protection
Application Dynamic Parameter demonstartion
To better understand the concept of dynamic parameters in web applications, let’s look at a real example in the DVWA Web Application.
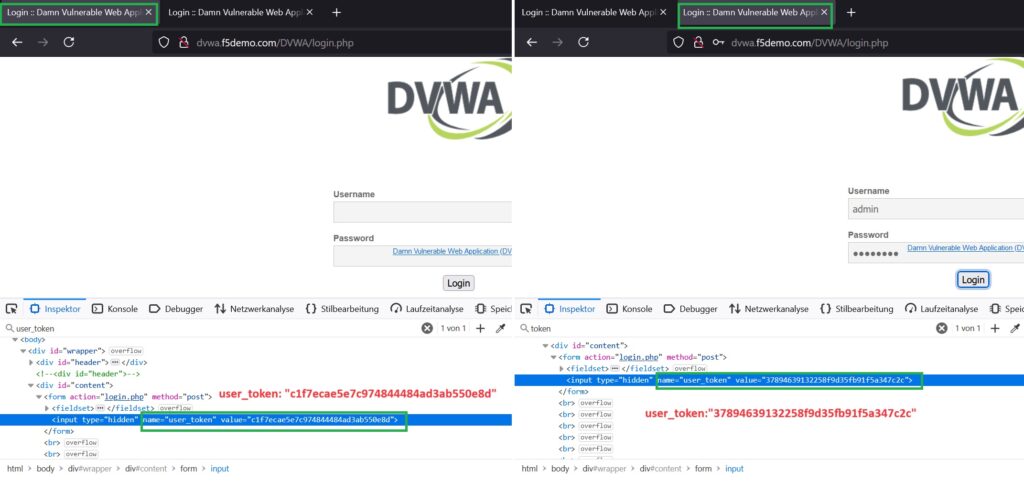
When you navigate to the login page in DVWA, a user token is dynamically generated for each session by the web application. This user token helps protect the application against CSRF and other related vulnerabilities.
I will open the login page in two different browser tabs and then inspect the content of the page to find the user token. As you can see, a unique user token is generated dynamically for each session. This dynamic parameter is what we are going to demonstrate how to protect against tampering with F5 AWAF in this section.
prepare Security Policy
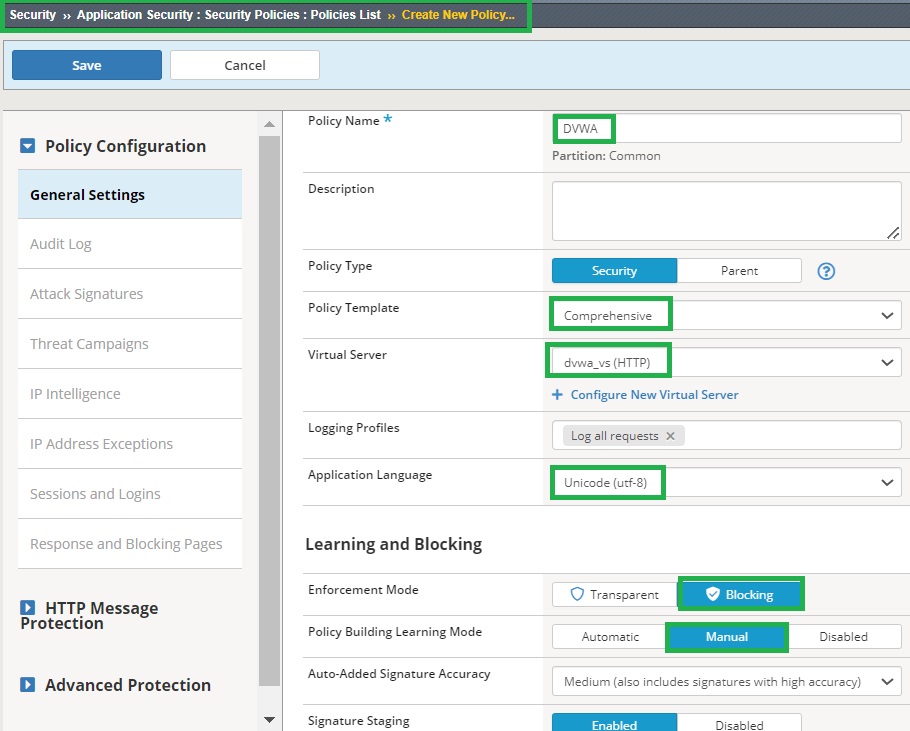
To protect against dynamic parameter tampering, we will configure a security policy using a comprehensive or any other general security templates. We will set the enforcement mode to “blocking” to ensure that tampering attempts are blocked. Additionally, we will change the learning mode to “manual” as automatic learning will be covered in a dedicated lesson later.
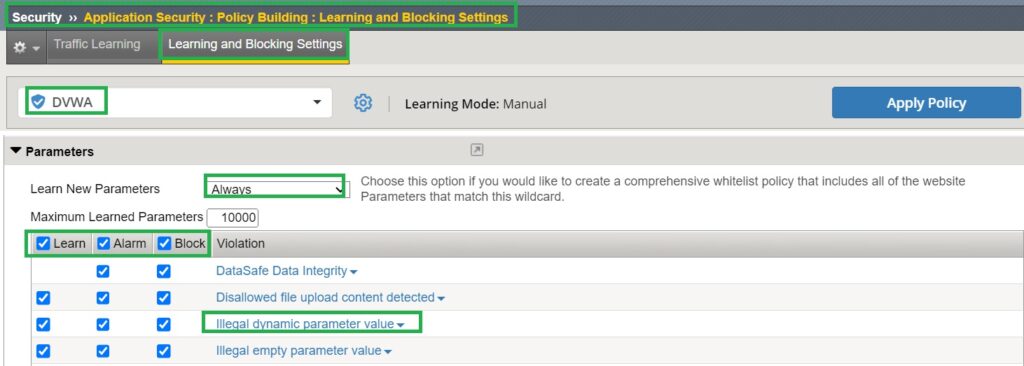
Then we go to the section learning and blocking setting, where almost all security components are configured.
In the “Parameters” section, we change the learning mode to “Always” so that all parameters are learned independently. We also enable “Learn”, “Alarm”, and “Block” for all parameter violations, specifically “Illegal Dynamic Parameter Value” , which we demonstrate in this section.
Next, we will log in to DVWA so that F5 AWAF can learn the new parameters transferred through this page.
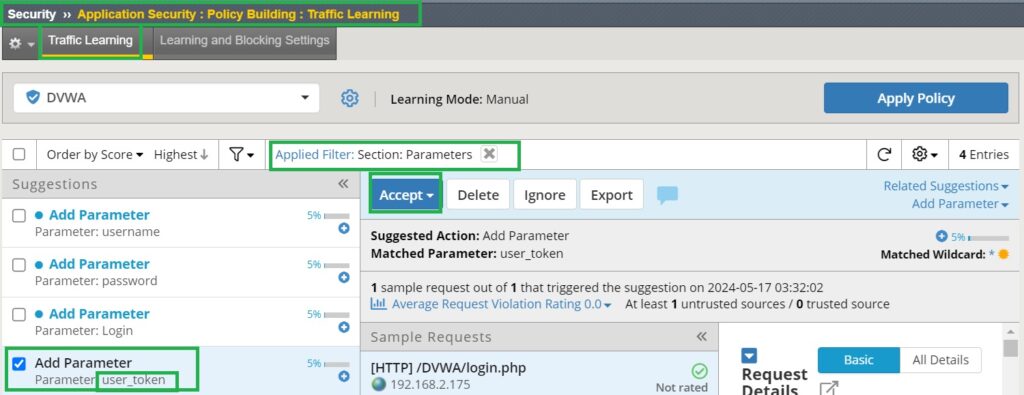
Now, if you check traffic learning in the section “Security > Application Security > Policy Building > Traffic Learning” and filter to show only learned parameters, you will find the “user_token” parameter listed among the learning suggestions. We will accept and enforce this parameter as a legitimate parameter to the list of web application parameters.
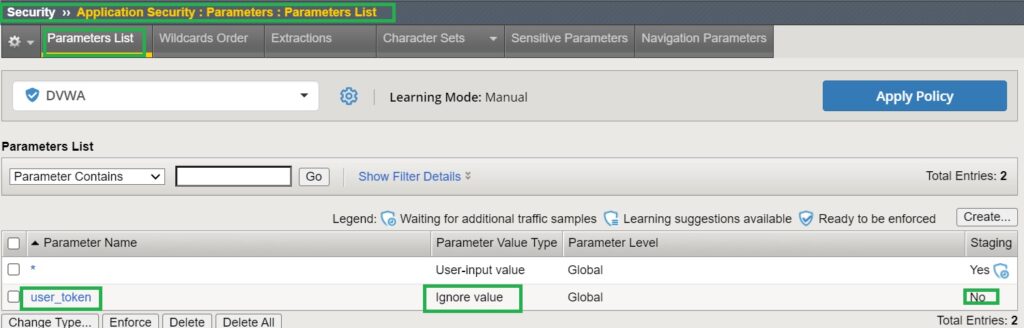
You can review the newly learned and enforced parameter in the section ‘Security > Application Security > Parameters > Parameters List‘. By default, the content value type is not considered unimportant and will be ignored.
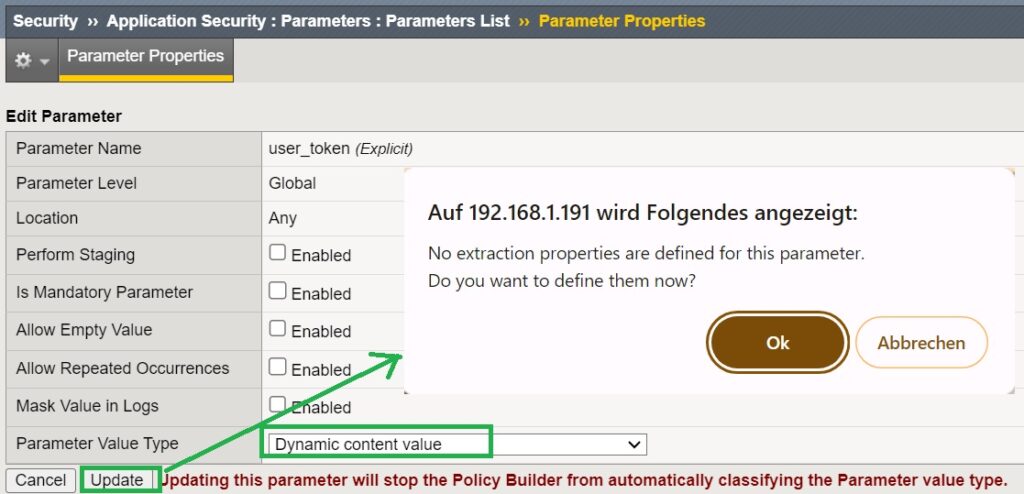
When changing the content value type from ‘ignore value‘ to ‘Dynamic content value‘, you will be prompted to configure an extraction property. This step assists F5 AWAF to know where this traffic should be monitored, enhancing its ability to protect against tampering.
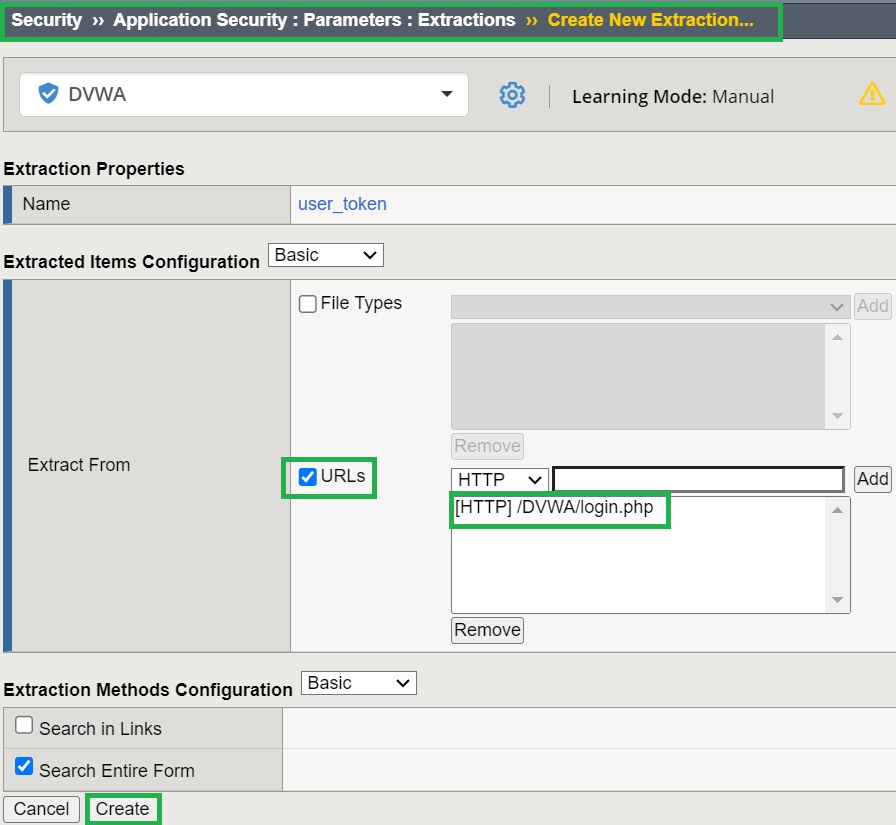
I will specify the URL with the protocol ‘HTTP‘ and path ‘/DVWA/login.php‘ as the extraction method to locate this parameter.
demonstrate Dynamic Parameter Tampering
Now, I will open the DVWA login page and proceed to enable the proxy with interception for the domain ‘f5demo.com‘. Detailed instructions for this process are discussed in lessons ‘5. F5 AWAF Lab Preparation Part 4 – mitmproxy Configuration as Web Debugging and Interception Demonstration‘ and ‘15. F5 AWAF Cookie Tampering Protection‘, so I won’t repeat them here.
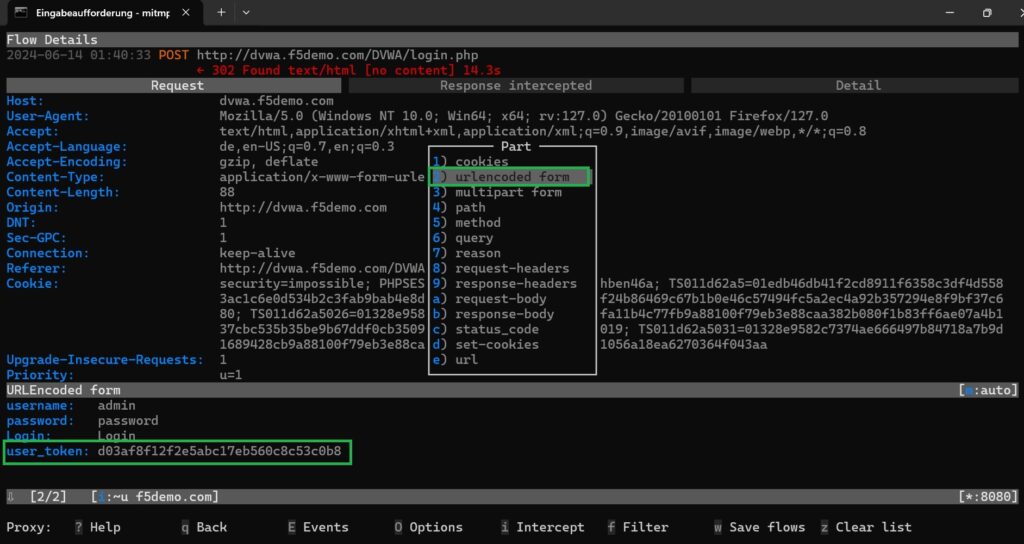
Afterward, we attempt to log in using the username ‘admin’. However, the page does not load because the traffic is intercepted by mitmproxy.
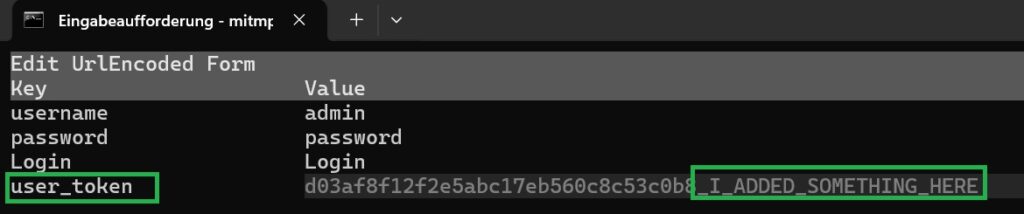
In mitmproxy, we modify the ‘user_token‘ header field in the HTTP POST request by adding or appending something to it, and then we resume the traffic.
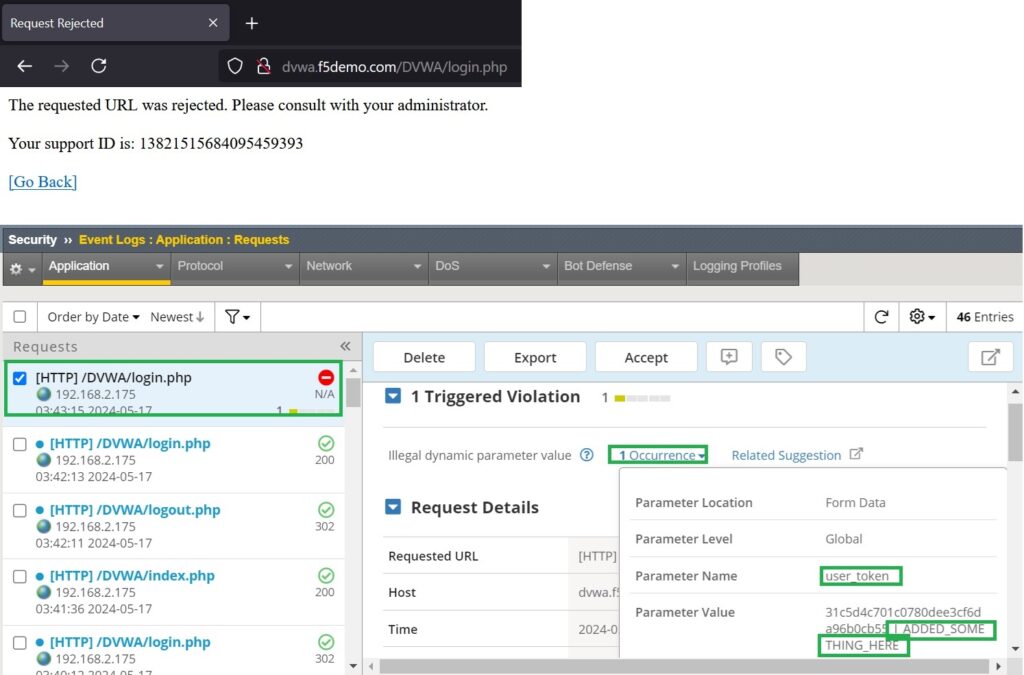
Now we observe that the traffic is blocked by F5 AWAF. Checking the event log under ‘Security > Event Logs > Application::Requests‘, you’ll find that the traffic is blocked due to a ‘illegal dynamic parameter value‘ violation, as expected.
Therefore, we have successfully protected against application dynamic parameter tampering using F5 AWAF.