F5 AWAF provides robust cookie tampering protection, ensuring that hackers cannot alter the contents of cookies. This prevents session hijacking and the exposure of sensitive information.
In this section, we will demonstrate how F5 AWAF effectively prevents cookie tampering in web applications, enhancing overall security.
Protect web applications against Cookie Tampering with F5 AWAF
Before we dive into demonstrating cookie tampering and how to prevent it using F5 AWAF, let’s first review the meaning and usage of cookies in web applications.
What are cookies and cookie attributes?
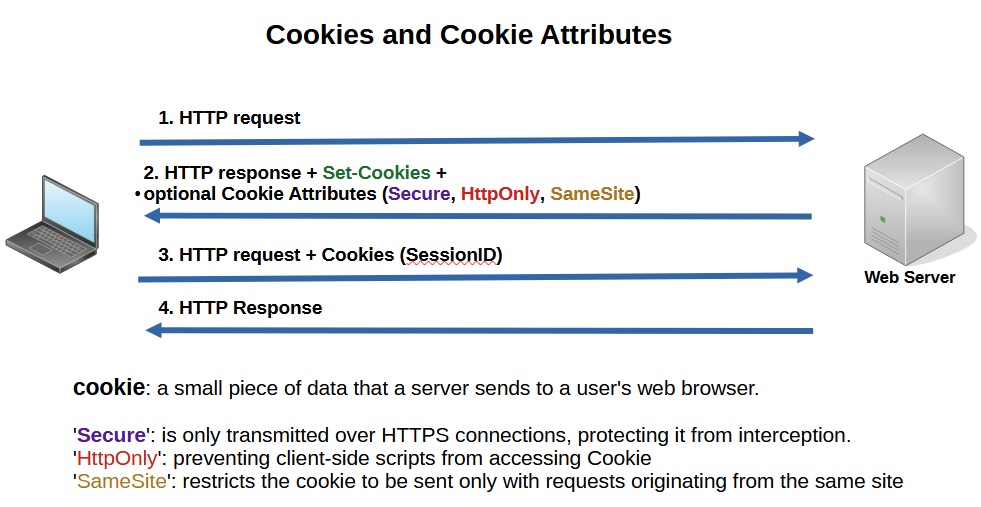
A cookie in web applications is a small piece of data that a server sends to a user’s web browser. The browser may store the cookie and send it back to the server with subsequent requests. Cookies are used to manage state and track information about the user’s interactions with a web application.
A server can add several attributes to a cookie, such as ‘Secure‘, ‘HttpOnly‘, and ‘SameSite‘, which provide specific instructions to the client side:
The ‘Secure‘ attribute ensures that the cookie is only transmitted over secure HTTPS connections, protecting it from interception.
The ‘HttpOnly‘ attribute makes the cookie inaccessible via JavaScript, preventing client-side scripts from accessing it and thereby reducing the risk of XSS (Cross-Site Scripting) attacks.
The ‘SameSite‘ attribute restricts the cookie to be sent only with requests originating from the same site, helping to prevent CSRF (Cross-Site Request Forgery) attacks.
Demonstration of cookie tampering
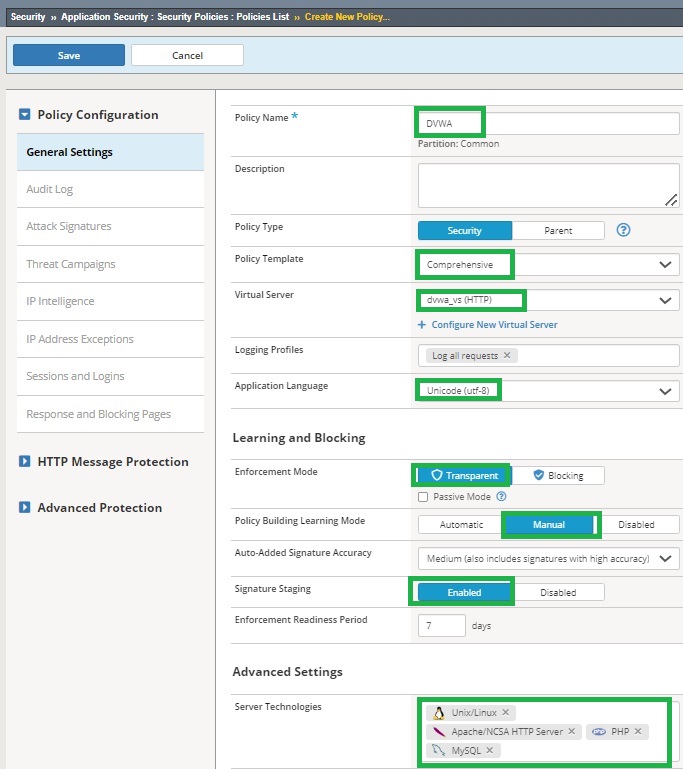
To start the demonstration, we first create a security policy using a comprehensive security template. We set the enforcement mode to transparent initially to ensure that no traffic is blocked at the beginning.
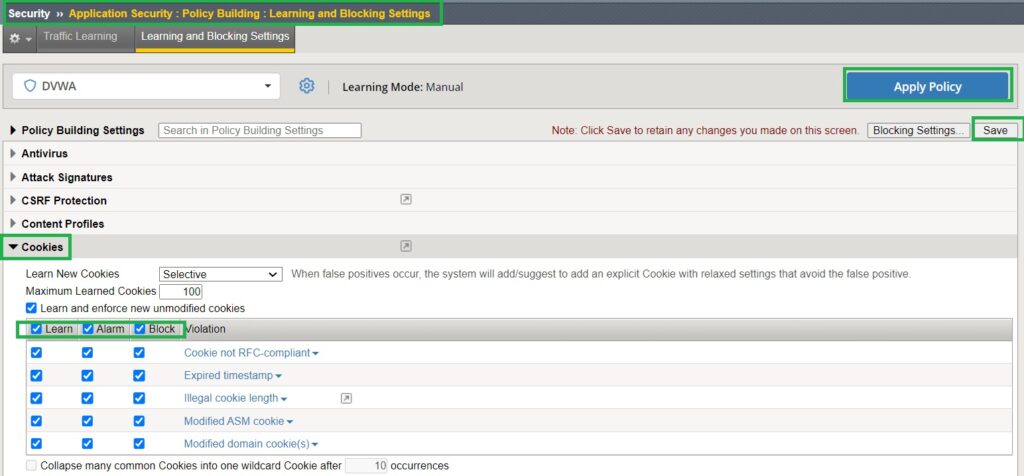
In the next step, we navigate to the ‘Learning and Blocking Settings‘ section, where most security policy components are configured.
In the ‘Cookie‘ section, we notice that the learning mode is set to ‘Selective‘. This setting ensures that when a false positive related to a cookie occurs, the system will add an explicit policy for the new cookie.
We also enable ‘learn‘, ‘alarm‘, and ‘block‘ for all cookie violations, especially for ‘Modified ASM cookie‘ and ‘modified domain cookie(s)‘ which we demonstrate in this section.
While web application servers typically utilize their own cookies, known as domain cookies, for managing sessions, storing user preferences, and other purposes, F5 AWAF introduces its own cookies to offer enhanced security and additional features. These cookies, referred to as ASM cookies, provide application-agnostic features that improve the security of the web applications.
Then we log in to the DVWA web application.
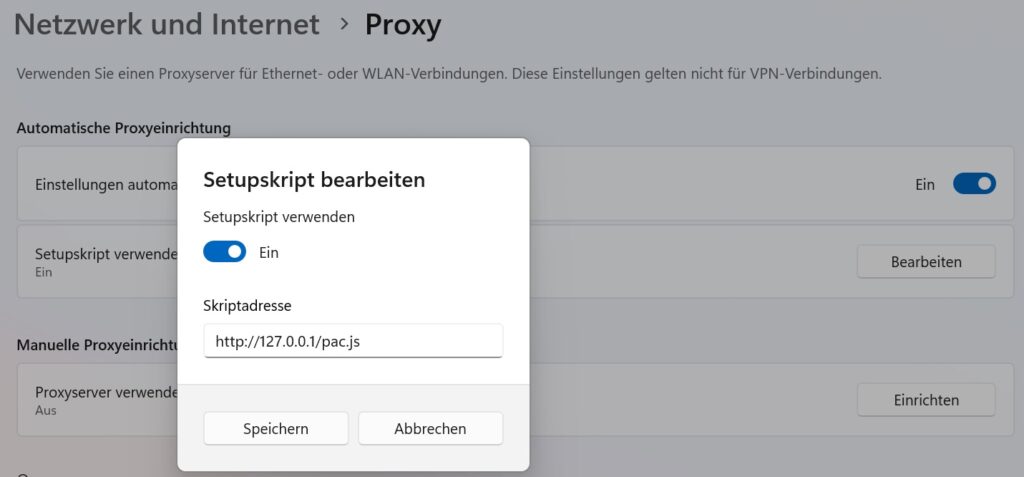
Now, we’ll enable the proxy so that all web traffic related to f5demo.com is routed through mitmproxy.
In the previous lessons, we have covered configuring the Windows proxy to ensure that traffic from specific web applications is forwarded through the web proxy.
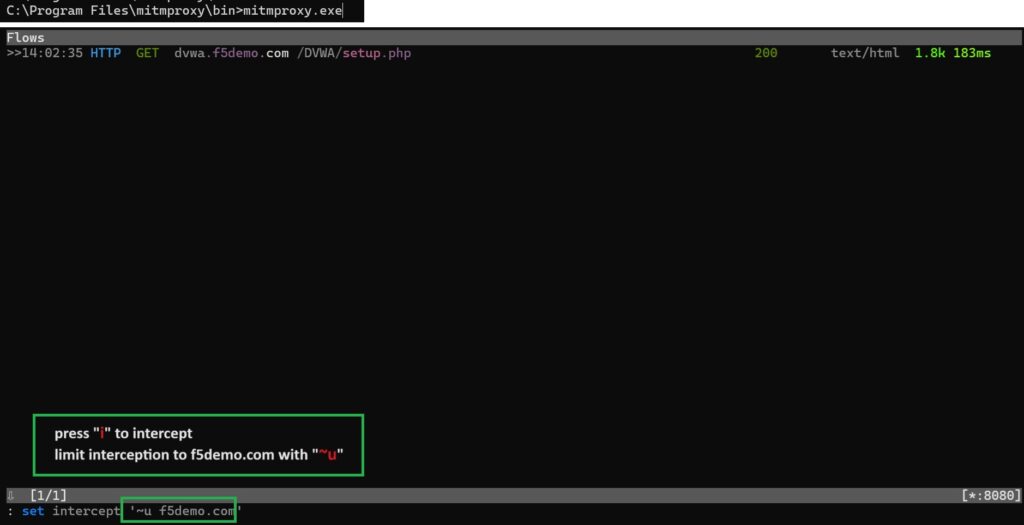
We run mitmproxy and crawl a page in the DVWA web application to make sure that the traffic is routed through the mitmproxy.
With “i” we enable interception to manipulate traffic and with “~u” we limit interception to traffic destined for f5demo.com.
Now if we click on a link in the DVWA web application, it will not open because it is intercepted by mitmproxy.
The traffic intercepted by mitmproxy is shown in red.
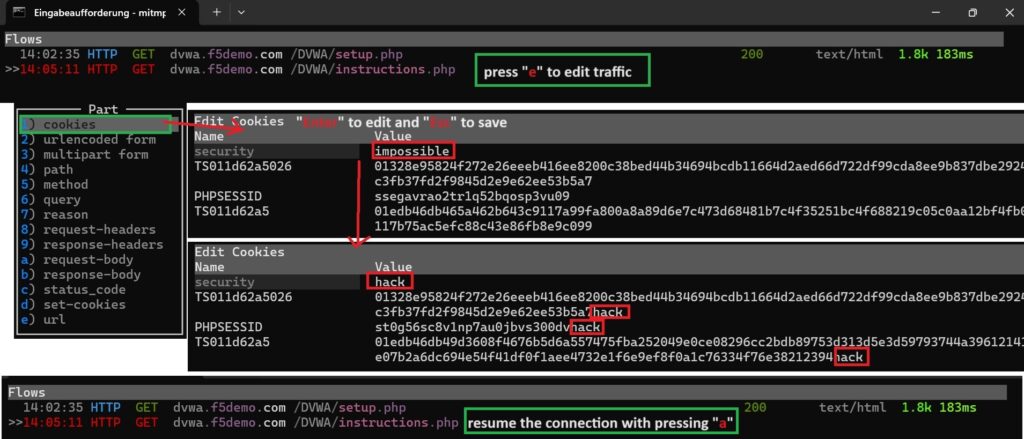
By pressing “e” and selecting “cookies” we edit the content of the cookies in the HTTP request.
By pressing “Enter” you can make changes in each cookie. After editing, select “Esc” to save the cookie change.
After editing with “a” we continue the traffic.
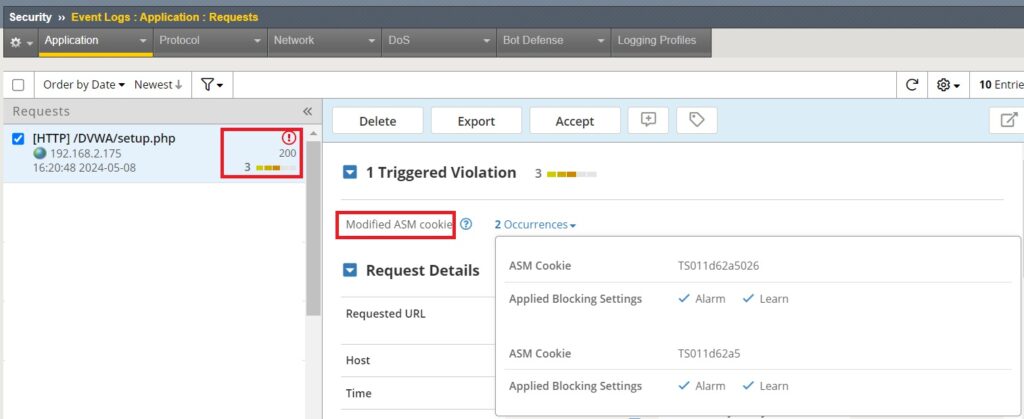
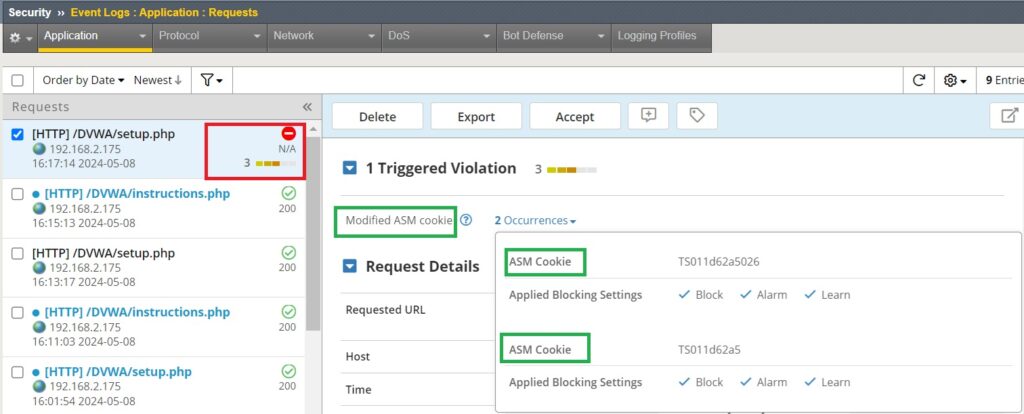
If we now check the security event log, you will notice that a “modified cookie” violation with violation rating 3 has already been generated.
If you remember, at the beginning we created the security policy. We changed the enforcement mode to transparent, so the violation is not blocked.
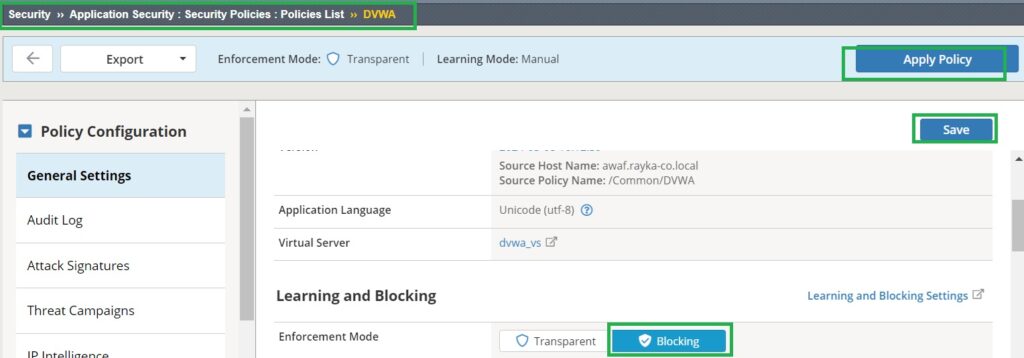
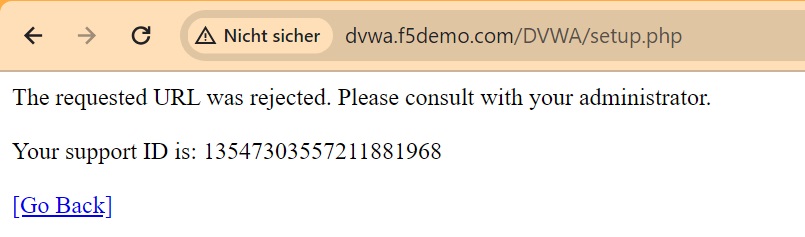
If we change the enforcement mode to blocking and perform the same process of cookie tampering, you will be blocked from accessing the web application.
F5 AWAF cookies learning and their properties
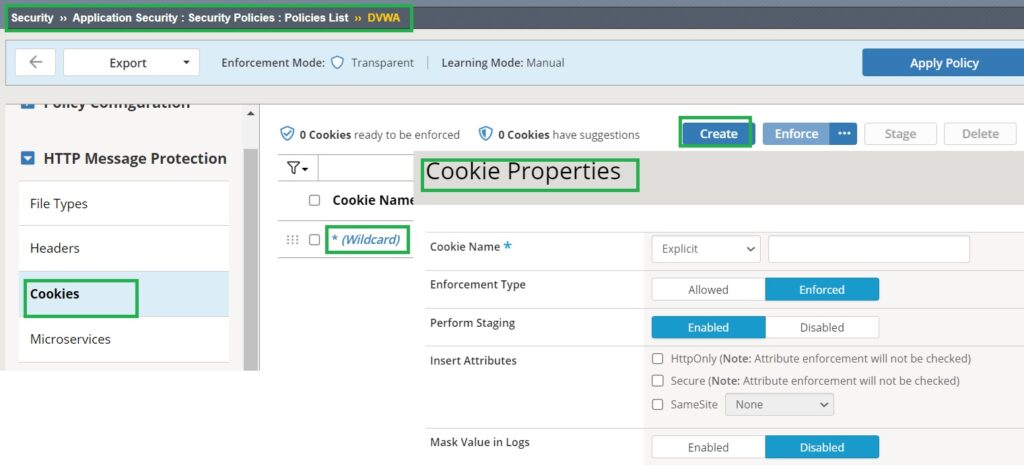
F5 AWAF maintains a list of learned cookies within the security policy under the “HTTP Message Protection” and “Cookies” sections.
Initially, only a wildcard cookie is present, enforcing the same security policy for all cookies. However, this list of cookies can be learned manually or automatically, similar to other HTTP components previously discussed.
For each cookie, administrators have the flexibility to configure various properties, including the enforcement type and staging mode, as we’ve discussed extensively.
Additionally, F5 AWAF offers the option to automatically insert its own ‘HttpOnly‘, ‘Secure‘, and ‘SameSite‘ attributes. We have just given the definition and usage of each of these attributes.