Nornir Napalm validate task is used to automate compliance check of configuration of network devices.
Compliance check means to make sure that the network device have compatible configuration for example in DNS and NTP servers.
Compliance Check Meaning?
Compliance Checking is another important network automation application that allows you to quickly verify which network devices have an incompatible configuration.
For example, you want to ensure that all devices on the network are pointing to the correct NTP and DNS servers.
Nornir Napalm validate task is exactly to automate compliance checking.
Nornir "napalm_validate" to check compliance
If we review the details of the nornir napalm “napalm_validate” task in the github source, we use a source file with “src” parameter as a validation source to check the compliance of configuration.
def napalm_validate( task: Task, src: Optional[str] = None, validation_source: ValidationSourceData = None, ) -> Result: """ Gather information with napalm and validate it: http://napalm.readthedocs.io/en/develop/validate/index.html Arguments: src: file to use as validation source validation_source (list): data to validate device's state Returns: Result object with the following attributes set: * result (``dict``): dictionary with the result of the validation * complies (``bool``): Whether the device complies or not """
Nornir Napalm Compliance Check Code Example
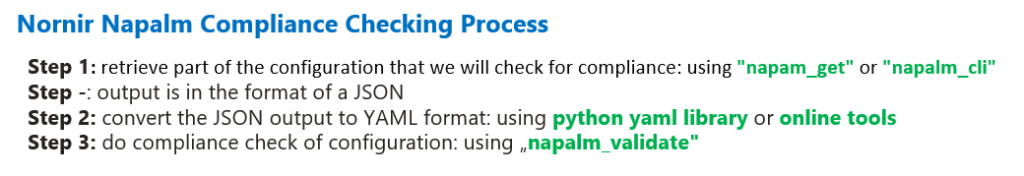
To perform the compliance check, we first need to prepare a YAML file as a validation source.
To prepare a YAML validation source file, we retrieve part of the configuration that we will check for compliance in network devices through napalm getters or CLI commands.
As we have already seen, the output is in the format of a JSON.
The source validation file must be in YAML format, so we need to convert the JSON output to YAML format. It is done usually through python YAML library or online tools.
Finally we use “napalm_validate” task with prepared validation source file to check compliance of configuration in network devices.
Step 1: Get NTP Configuration using "get_ntp_servers" getter
As an example, now we will perform an NTP configuration compliance check.
In the first step, we get NTP part of the configuration using “napalm_get” and “get_ntp_servers” getter.
This is the script that we have prepared in the first lesson of nornir napalm module, “10. Nornir Napalm Getter Code Example”.
from nornir import InitNornir from nornir_napalm.plugins.tasks import napalm_get from nornir_utils.plugins.functions import print_result nr = InitNornir(config_file="config.yaml") def nornir_napalm_get_example(task): task.run(task=napalm_get, getters=["get_ntp_servers"]) results=nr.run(task=nornir_napalm_get_example) print_result(results)
Now we run the script to get NTP part of the configuration in the format of JSON.
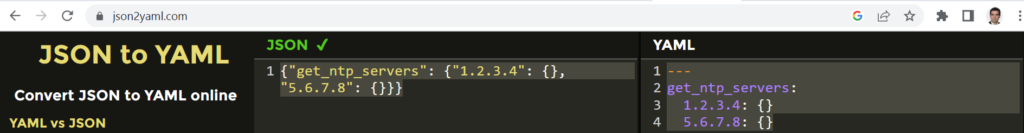
{'get_ntp_servers': {'1.2.3.4': {}, '5.6.7.8': {}}}Step 2: Convert JSON to YAML
This is the output of NTP configuration in the format of JSON which must be converted into YAML format.
We use the online website “json2yaml.com” to convert the configuration to YAML format.
When I wanted to convert JSON to YAML, I noticed that we need to use “double quotes” instead of ‘single quotes’. Therefore I have changed all single quotes to double quotes.
{"get_ntp_servers": {"1.2.3.4": {}, "5.6.7.8": {}}}Now we can change it via online web tool “json2yaml.com”.
This is the configuration output I the format of YAML.
--- get_ntp_servers: 1.2.3.4: {} 5.6.7.8: {}
Probably we want to check compliance of many parts of the configuration, then we have a list configuration that must be check. In other words, the configuration must be in the format of a list.
Therefore we change the key value to the format of a list with inserting hyphen, “-”, in front of each part of the configuration, here “get_ntp_servers” key.
--- - get_ntp_servers: 1.2.3.4: {} 5.6.7.8: {}
Step 3: use Nornir Napalm Validate to check Compliance
Now we can compliance checking or validate the configuration using the prepared YAML validation source file.
This is the simple script that I have already prepared to validate NTP configuration. It uses “napalm_validate” with “ntp.yaml” as a source that we have already prepared.
from nornir import InitNornir from nornir_napalm.plugins.tasks import napalm_validate from nornir_utils.plugins.functions import print_result nr = InitNornir(config_file="config.yaml") def nornir_napalm_compliance_validation_check(task): task.run(task=napalm_validate, src="ntp.yaml") results = nr.run(task= nornir_napalm_compliance_validation_check) print_result(results)
If we run the script, it is expected that the configuration is compliant since the source file is generated from device running configuration.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ python3 5.8.nornir_napalm_compliance_validation.py
nornir_napalm_compliance_validation_check***************************************
* R1 ** changed : False ********************************************************
vvvv nornir_napalm_compliance_validation_check ** changed : False vvvvvvvvvvvvvv INFO
---- napalm_validate ** changed : False ---------------------------------------- INFO
{ 'complies': True,
'get_ntp_servers': { 'complies': True,
'extra': [],
'missing': [],
'present': { '1.2.3.4': { 'complies': True,
'nested': True},
'5.6.7.8': { 'complies': True,
'nested': True}}},
'skipped': []}
^^^^ END nornir_napalm_compliance_validation_check ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^As you can the result shows that the configuration of devices complies with the source YAML file.
For each server also shows that the compliance check is true.
To also see when the configuration doesn’t comply, let’s change one of the NTP servers in the device configuration and run the script again.
R1(config)#no ntp server 1.2.3.4
R1(config)#ntp server 1.2.3.14
R1(config)#do sh runn | sec ntp
ntp server 5.6.7.8
ntp server 1.2.3.14majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ python3 5.8.nornir_napalm_compliance_validation.py
nornir_napalm_compliance_validation_check***************************************
* R1 ** changed : False ********************************************************
vvvv nornir_napalm_compliance_validation_check ** changed : False vvvvvvvvvvvvvv INFO
---- napalm_validate ** changed : False ---------------------------------------- INFO
{ 'complies': False,
'get_ntp_servers': { 'complies': False,
'extra': [],
'missing': ['1.2.3.4'],
'present': { '5.6.7.8': { 'complies': True,
'nested': True}}},
'skipped': []}
^^^^ END nornir_napalm_compliance_validation_check ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^As you can see it doesn’t match this time because one of the NTP servers configured in the device doesn’t match with what is configured in the source validation file.