Nornir Napalm getter and Send Commands are two methods to send monitoring and troubleshooting commands to network devices in napalm plugin.
Nornir Napalm getters are vendor independent show commands common to all supported vendors and it is invented by Napalm. This is the topic of this section.
Nornir napalm send command is normal CLI command that we send to network devices when no getter is provided and it is the topic of the next section.
We also discuss the structured output of Napalm getter and CLI commands and how it differs from Netmiko and Scrapli plugin.
Nornir Napalm Features
In the previous sections, we learned how to send monitoring and configuration commands via the nornir netmiko and nornir scrapli plugin.
In this section, you will learn how to send monitoring commands through the Nornir Napalm plugin.
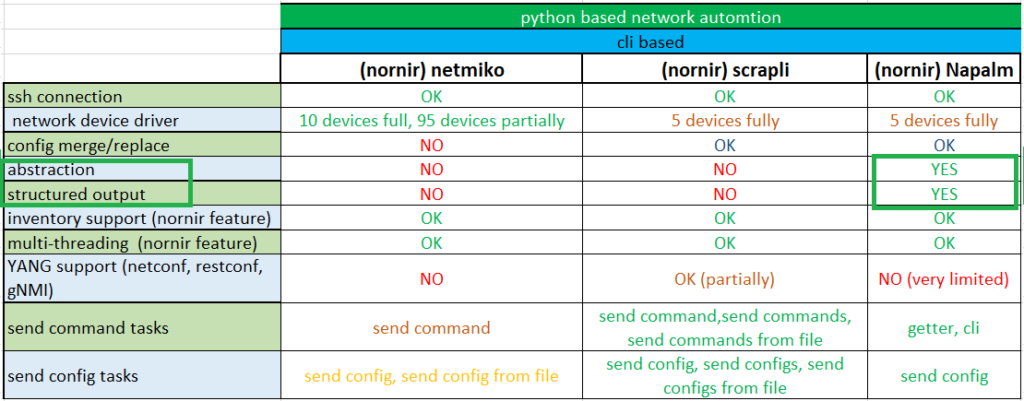
There are two main differences in sending monitoring commands in Nornir Napalam with what we learned in Netmiko and Scrapli plugins, namely vendor independent (abstraction) and structured output.
By vendor independent I mean you can send the same monitoring command for all supported vendors.
For example you do not need to use “show ip interface brief” for cisco devices and “show interface terse” for juniper devices.
By structured output I mean that you don’t need to use a regular expression to find a specific parameter from the output of a show command. They are easily accessible through the Python dictionary structure.
Nornir Napalm Getters
In Napalm plugin there are some getters instead of show commands which is invented by Napalm.
You can use the same getters to send monitoring commands to all supported vendors. In the background, the getter commands are translated into vendor-specific monitoring commands.
Note that Napalam getters are limited to only the most applicable and important monitoring commands and only a few vendors.
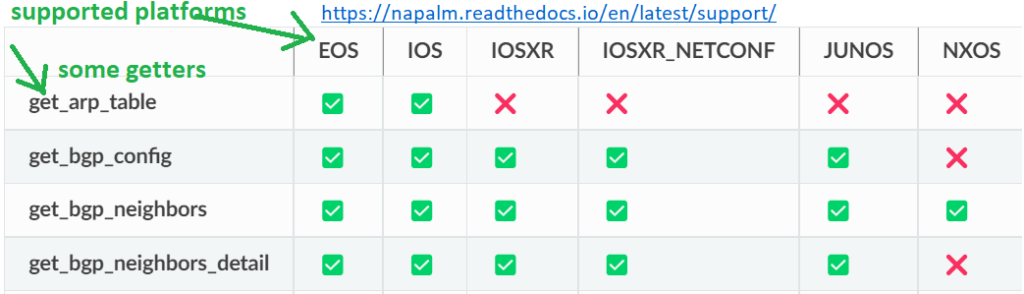
Arista EOS, Cisco IOS, IOS XR and NXOS and JUNOS are the supported napalm vendors.
You can see, supported getters and supported platforms in this link.
For the monitoring commands that are not supported by getters, we send normal vendor-based CLI commands, which are implemented in the next section.
NAPALM Structured Output
The other important feature of Napalm plugin is that the output of monitoring commands is returned in structured JSON format, which helps to find any parameter easily from the output without using regular expressions.
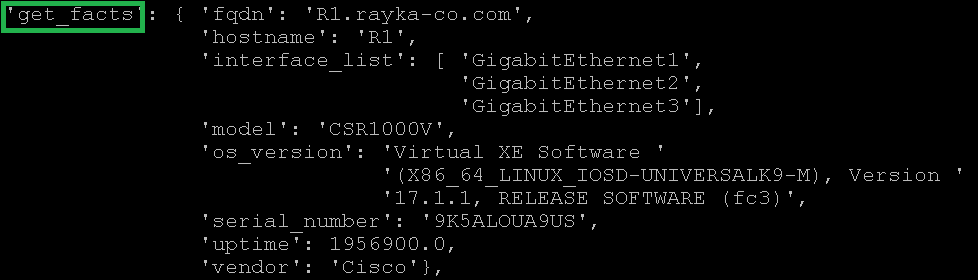
This figure shows an example structured output where you can easily extract important information like device name, list of interfaces and serial number via Python dictionary data structure.
Parsing the structured output to extract the required parameters will be discussed in the next two sections.
Nornir Napalm Getter Example
Before implementing an example from nornir napalm getter project, let’s have a look into the tasks supported by nornir napalm plugin and details of napalm getter project.
NAPALM Getter Task
If we look at nornir napalm project in GitHub source, three tasks are the most important tasks supported by this project.
The task “napalm_get” to send vendor-independent monitoring commands or getters to network devices.
The task “napalm_cli” to send normal cli commands to network devices when there is no getter for a specific command.
And finally the task “napalm_configure”, to send configuration commands to network devices.
If we look at the details of the task “napalm_get”, it needs two necessary arguments, the name of the task and a list of getters that we can find in this link.
def napalm_get( task: Task, getters: List[str], getters_options: GetterOptionsDict = None, **kwargs: Any ) -> Result: """ Gather information from network devices using napalm
There are about 30 getters to use for cisco, juniper and arista devices.
Between these getters, probably “get_facts” which gives the most important information of the device, “get_interfaces”, “get_interafces_ip” and “get_config” which are self-explanatory are the main getters defined in Napalm and we will run in our example python code.
Preparing Nornir plugins, Inventory and Configuration
To implement a Nornir napalm getter example, ensure that the required nornir, nornir-utils, and nornir-napalm plugins are installed.
sudo apt-get update
sudo apt-get install python3 python3-venv python3-pip
python3 -m pip install nornir
python3 -m pip install nornir-napalm
python3 -m pip install nornir-utilsInventory files are as in the previous sections and only one device, R1, with IP address 192.168.1.11 and as a member of cisco group is defined in the “hosts.yaml” inventory file.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ cat hosts.yaml --- R1: hostname: "192.168.1.11" # username: "rayka" # password: "rayka-co.com" groups: - cisco
In the “groups.yaml” inventory file, every device member of cisco group has its platform defined as “ios”.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ cat groups.yaml --- cisco: platform: ios
And finally in “defaults.yaml”, the default values of username, password and platform is configured.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ cat defaults.yaml --- username: "rayka" password: "rayka-co.com" platform: "ios"
Nornir configuration file is also as usual. Inventory files are defined and multithreading is enabled.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ cat config.yaml --- inventory: plugin: SimpleInventory options: host_file: "hosts.yaml" group_file: "groups.yaml" defaults_file: "defaults.yaml" runner: plugin: threaded options: num_workers: 10
NAPALM Getter Automation Code Example
This is the python code to use getter to send monitoring command to network devices.
With the use of “getters” parameter and “napalm_get” task from nornir napalm plugin, we send “get_facts”, “get_interfaces”, “get_interfaces_ip” and “get_config” from network devices.
from nornir import InitNornir from nornir_napalm.plugins.tasks import napalm_get from nornir_utils.plugins.functions import print_result nr = InitNornir(config_file="config.yaml") def nornir_napalm_get_example(task): task.run(task=napalm_get, getters=["get_facts", "get_interfaces", "get_interfaces_ip", "get_config"]) results=nr.run(task=nornir_napalm_get_example) print_result(results)
The other interesting point of nornir napalm is JSON structured output which can be parsed easily to access any parameter without using regular expression.
Let me run the script and see the result.
majid@majid-ubuntu:~/devnet/pyhton_nornir/2023/5.nornir_napalm$ python3 5.1.nornir_napalm_get_commands.py
nornir_napalm_get_example*******************************************************
* R1 ** changed : False ********************************************************
vvvv nornir_napalm_get_example ** changed : False vvvvvvvvvvvvvvvvvvvvvvvvvvvvvv INFO
---- napalm_get ** changed : False --------------------------------------------- INFO
{ 'get_config': { 'candidate': '',
'running': '!\n'
'\n'
'!\n'
'version 17.1\n'
'service timestamps debug datetime msec\n'
'service timestamps log datetime msec\n'
'! Call-home is enabled by Smart-Licensing.\n'
'service call-home\n'
...
'get_facts': { 'fqdn': 'R1.rayka-co.com',
'hostname': 'R1',
'interface_list': [ 'GigabitEthernet1',
'GigabitEthernet2',
'GigabitEthernet3'],
'model': 'CSR1000V',
'os_version': 'Virtual XE Software '
'(X86_64_LINUX_IOSD-UNIVERSALK9-M), Version '
'17.1.1, RELEASE SOFTWARE (fc3)',
'serial_number': '9K5ALOUA9US',
'uptime': 1956900.0,
'vendor': 'Cisco'},
'get_interfaces': { 'GigabitEthernet1': { 'description': '',
'is_enabled': True,
'is_up': True,
'last_flapped': -1.0,
'mac_address': '00:0C:29:F1:1E:47',
'mtu': 1500,
'speed': 1000.0},
'GigabitEthernet2': { 'description': '',
'is_enabled': False,
'is_up': False,
'last_flapped': -1.0,
'mac_address': '00:0C:29:F1:1E:51',
'mtu': 1500,
'speed': 1000.0},
'GigabitEthernet3': { 'description': '',
'is_enabled': False,
'is_up': False,
'last_flapped': -1.0,
'mac_address': '00:0C:29:F1:1E:5B',
'mtu': 1500,
'speed': 1000.0}},
'get_interfaces_ip': { 'GigabitEthernet1': { 'ipv4': { '192.168.1.11': { 'prefix_length': 24}}}}}The output of getter “get_facts” gives basic fundamental information like device name, the list of interfaces, device model, OS version, serial number, uptime and vendor of the device.
Any of these information are easily accessible through python code. The next two sections, we will discuss how to parse the output of napalm getter and CLI commands.
The output of “get_interfaces” list interfaces and their layer 1 and layer 2 information like MAC address, MTU and physical status.
The output of “get_interfaces_ip” list layer 3 interfaces and their IP addresses.
And finally “get_config” display the configuration of the device but in the format of structured JSON.
You can download nornir napalm code examples from this link.