Juniper SRX series and security features are the topics which will be discussed in this section.
Juniper SRX devices are classified based on the location that will be used, like LAN, data center, branch offices and virtual environment.
Juniper SRX is primarily a firewall and therefore supports the features that are supported in firewall in any other vendor like traffic filtering, NAT, VPN and some new or next-generation features like user based filtering, application firewall and UTM features like antivirus and antispam.
Juniper SRX series devices
Juniper SRX devices are primarily Juniper firewall devices and there are many models based on the location where we will be using them. Branch office, campus, data center and service provider infrastructure and virtual environment are the location as you can see on the Juniper website.
Juniper SRX series devices for branch offices
The branch offices usually use SRX 300 series devices, such as SRX300, SRX320, SRX340, SRX345 and SRX 380, which consolidate security features, SD-WAN, routing and also switching in a one small device.
SRX300 series firewall devices throughput varies between 1 Gbps and 10 Gbps.
SRX1500 with firewall throughput of 5 Gbps can also be used in branch offices in addition to distributed enterprise campus and small and midsized data centers.
SRX550 with 7 Gbps firewall throughput is ideal for medium and large branch offices.
Juniper SRX series devices for enterprise campus environment
Enterprise campus environment usually use SRX 4000 series devices, such as SRX4100, SRX4200, and SRX4600 in which firewall throughput varies from 22.5 Gbps to 400 Gbps.
SRX1500 with 5 Gbps firewall throughput can also be used in distributed enterprise campus and small and midsized data centers.
Juniper SRX series devices for data center environment
Data center and service provider infrastructures usually use SRX 5000 series devices, such as SRX5400, SRX5600, and SRX5800 in which firewall throughput varies from 270 Gbps to 1 Tbps.
SRX4600 with 400 Gbps firewall throughput can also be used in private enterprise clouds, campus networks, and public cloud infrastructures.
Juniper SRX series devices for virtual environment
vSRX and cSRX are two types of SRX device for virtual environment.
vSRX is a virtual machine SRX which is used in private and public cloud environments.
Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, IBM Cloud, and Oracle Cloud environments, all of them support vSRX.
cSRX with 13.5 Gbps firewall throughput is a container-based SRX which is used in container and microservice environments.
Juniper SRX security features
In continue, we will discuss the main features of a Juniper SRX device that will be covered in this course. But before that, let’s answer the question of where a Juniper SRX device is usually located on the network.
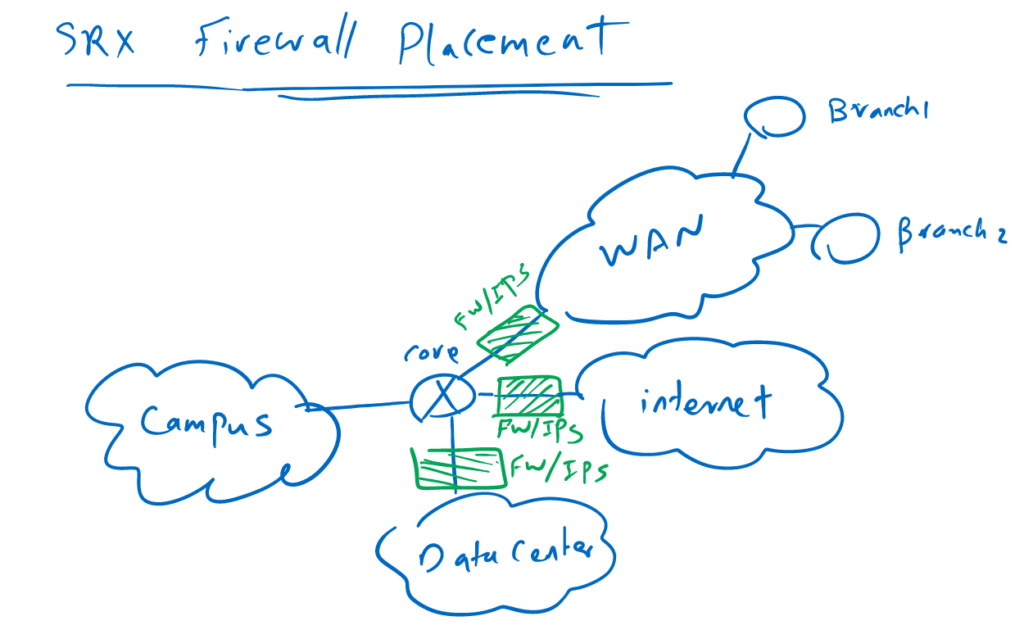
The main task of a Juniper SRX is to control traffic between different sections of the network. Therefore, it can be configured between different sections of the network where the traffic has to be inspected.
For example, it can be placed at the edge of the network to control traffic between the campus and the Internet or branch offices.
or it can be configured at the edge of the data center to control all traffic incoming and outgoing of the data center.
Juniper SRX as a Firewall
Being a firewall is the main task of a Juniper SRX to control traffic between any two zones.
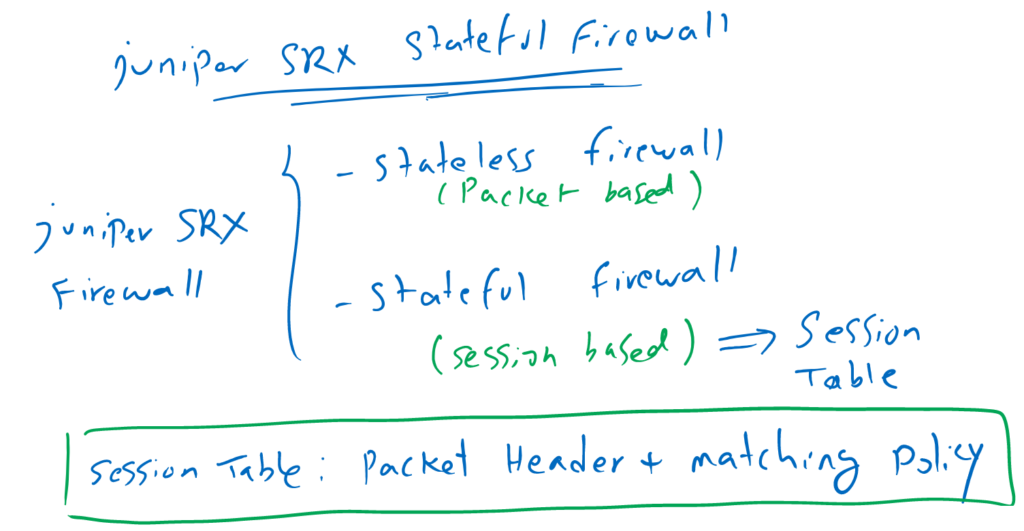
Firewall can be stateless or stateful and it is usually configured as a stateful traffic filter device.
In a stateless firewall, every packet is separately inspected with different policies to decide if the packet must be discarded or is allowed to be forwarded.
But with stateful firewall only the first packet of every new session will be inspected with different configured policies. If the packet is allowed, then the header of the packet and also the polices matching the packet will be added to the session table.
Every other packet related to this session, incoming and outgoing will not be inspected any more with the policies, it will be behaved exactly like the first packet and only the session table will be updated according to the header of latest packet related to this session.
Stateful firewall provide us, both, better security and better performance.
NAT in juniper SRX
NAT is another important application of any firewall.
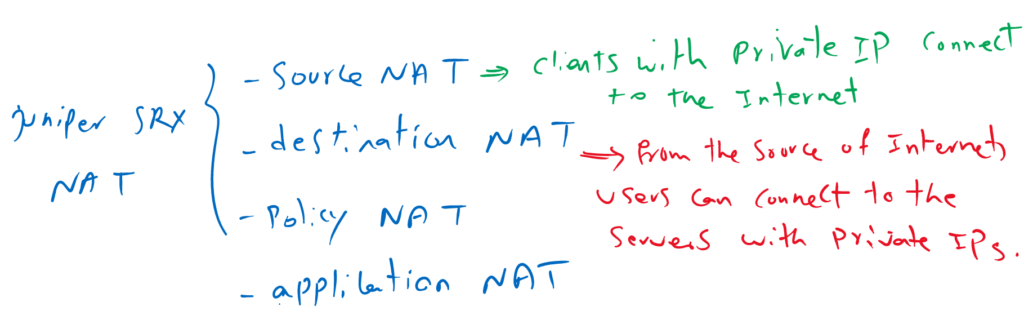
There are two main types of NAT, source NAT and destination NAT.
With source NAT, many clients with private address range can connect to the internet with having just a few public IP addresses.
With destination NAT, clients over the internet are able to connect to the servers located in the enterprise network which have private IP addresses.
There are some other types of NAT like policy NAT and application NAT which will be discussed through the course.
VPN in juniper SRX
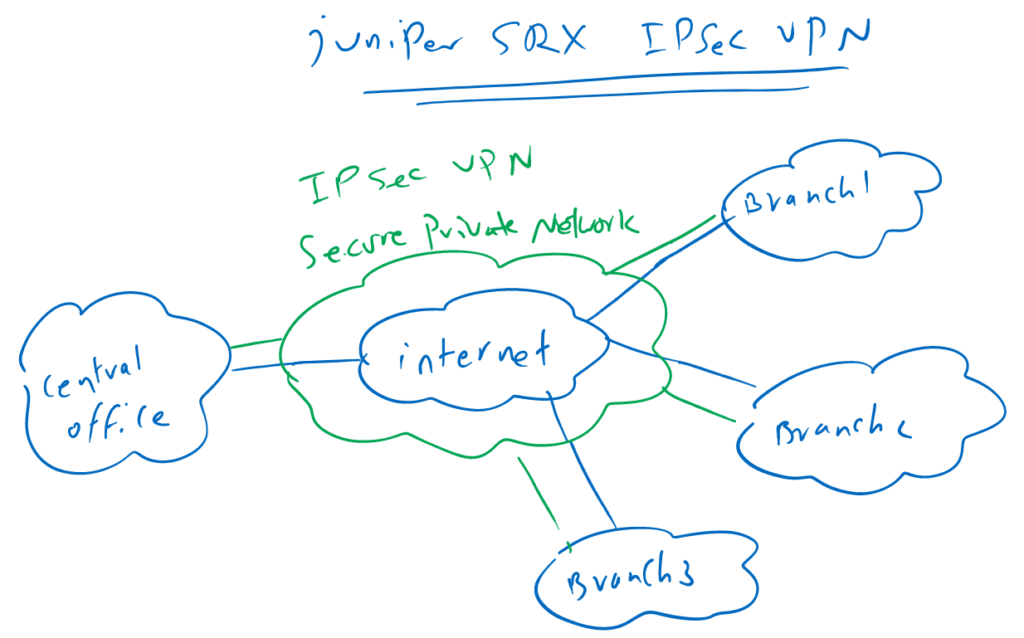
Implementing IPsec VPN in juniper SRX devices allows creating a private and secure network over public networks like internet.
This is one of the topics that we will discuss throughout this course.
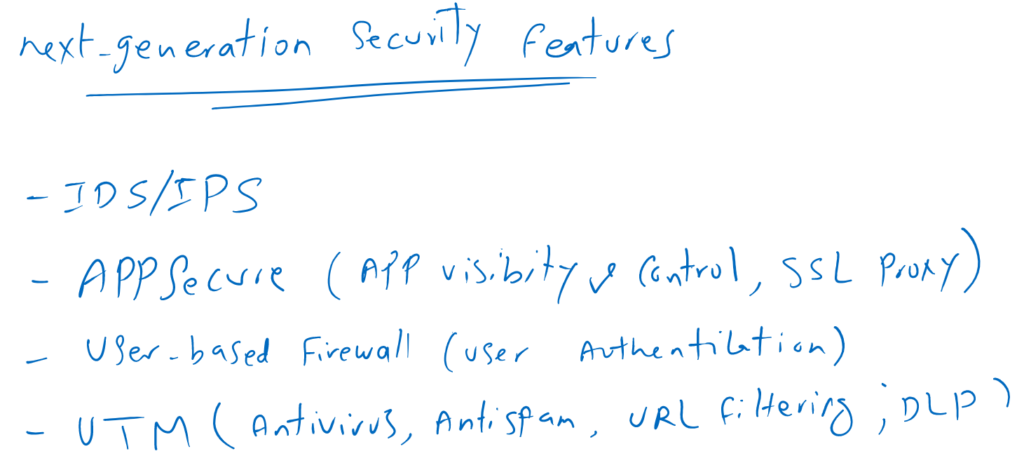
Juniper SRX next-generation security features
In the recent years, some features have been added in juniper SRX and also in the firewalls of other vendors which are called next-generation security features.
User-based traffic filtering, Application firewall called AppSecure in juniper SRX, Intrusion detection and prevention (IDS/IPS) and UTM features like antivirus, antispam and URL filtering sare some of these features which are called next-generation security features.
What is new in all next-generation security features is that they can inspect, monitor and control application layer traffic in addition to low layers information.
IDS/IPS in juniper SRX
IDS/IPS is a feature to detect and prevent attacks in the network traffic.
This is done usually through pre-configured signatures that matches known attacks. Signatures must be periodically updated like what we do for anti-virus signatures.
AppSecure in juniper SRX
Another feature in the category of next-generation firewall is AppSecure which means control and visibility in application layer.
For example with this feature you can control if the users are allowed to add a video in Instagram or Facebook or if they are allowed to call with WhatsApp.
This is also true in monitoring and visibility of traffic in application layer.
SSL Proxy and SSL inspection is another feature in AppSecure classification which allows us to inspect encrypted https websites and SSL applications.
User-based Firewall in juniper SRX
Another feature in the category of next-generation firewall is user-based firewall.
Normally when we want to give an access or control traffic of a specific user in the firewall, we identify the users based on their IP address. that means the IP address of the user must be fixed and not allowed to be changed.
with this new features, user based firewall, it is possible to control traffic based on user name even if the IP address of user is changing during the day.
UTM in juniper SRX
Another feature in the category of next-generation firewall is called UTM.
Some the most important features in the category of UTM are antivirus, antispam and URL filtering. It also prevent the users from uploading critical information like customers email addresses and phone numbers out of the enterprise.
These are the most important features that exist not only in juniper SRX security device but also in other vendors. We will learn some of these features in this course and the others in the upcoming juniper security courses