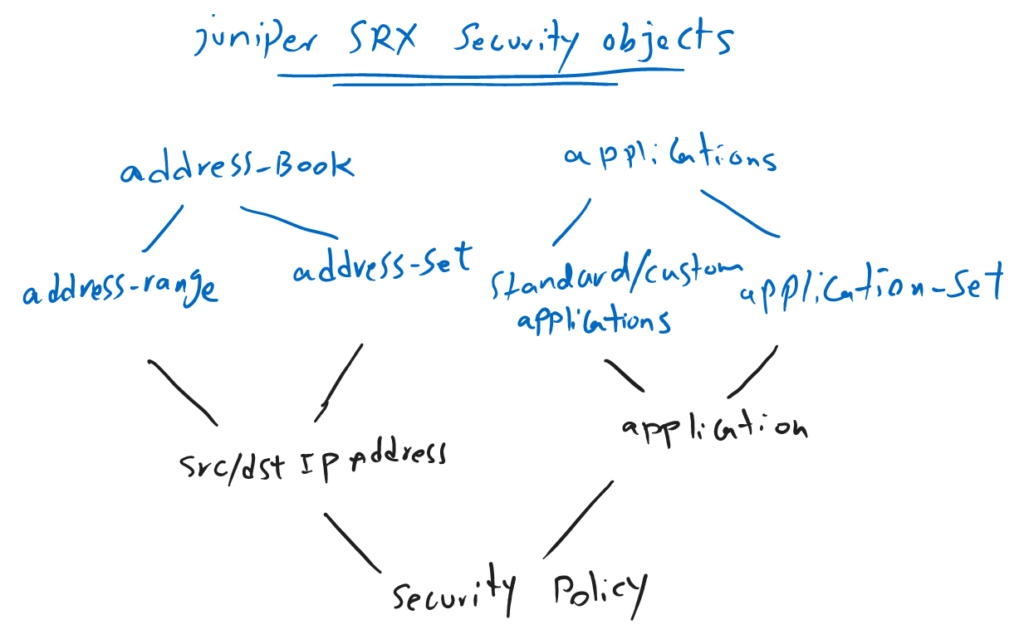
Juniper SRX applications and application-set objects are another required object in security policies.
In other words, when you configure a security policy, in addition to source address and destination address, the name of the application is also required to be configured.
Source address and destination address must be already configured in address book that we have discussed in the previous section. the application name must be also already configured in the list of applications.
Juniper SRX application and application-set objects
When swe configure a security policy, to match a traffic, we have to specifiy the source and destination IP address and also application type of the interresting traffic.
The source and destination IP address must be taken from address and address-set entries configured in address-book.
And the application type must also be taken from the standard or custome application or application-set list.
Standard application list are already configured by the juniper itself.
We can configure new enterprise custom applications when thay are not in the list of standard application list.
Juniper Standard Application List
by default, there is a big list of applications that are already configured by juniper itself. You can see the list, by the command “show configuration groups junos-defaults applications”. As you can see, the name of all applications configured by the juniper itself are started by “junos-“ keyword.
rayka# run show configuration groups junos-defaults applications
##
## protect: groups junos-defaults
##
#
# File Transfer Protocol
#
application junos-ftp {
application-protocol ftp;
protocol tcp;
destination-port 21;
}
#
# Trivial File Transfer Protocol
#
application junos-ftp-data {
application-protocol ftp-data;
protocol tcp;
destination-port 20;
}
application junos-tftp {
application-protocol tftp;
protocol udp;
destination-port 69;
}
#
# Two-Way Active Measurement Protocol
#
application junos-twamp {
application-protocol twamp;
protocol tcp;
destination-port 862;
}
#
# Real Time Streaming Protocol
#
application junos-rtsp {
application-protocol rtsp;
protocol tcp;
destination-port 554;
}
#
# Network Basic Input Output System - networking protocol used on
# Windows networks session service port
#
application junos-netbios-session {
protocol tcp;
destination-port 139;
}
application junos-smb-session {
protocol tcp;
destination-port 445;
}
application junos-ssh {
protocol tcp;
destination-port 22;
}
....Most of the standard applications are already configured by Juniper itself, and we don’t need to reconfigure them unless the enterprise application doesn’t follow the default rules.
For example, let’s check what is default configuration of http and https configured by juniper. You can check it with command “show configuration groups junos-defaults applications application junos-http” or “show configuration groups junos-defaults applications application junos-https”
[edit]
rayka# run show configuration groups junos-defaults applications application junos-http
##
## protect: groups junos-defaults
##
protocol tcp;
destination-port 80;
inactivity-timeout 300;
[edit]
rayka# run show configuration groups junos-defaults applications application junos-https
##
## protect: groups junos-defaults
##
protocol tcp;
destination-port 443;
[edit]
rayka# If you run a http application that runs on port 8080 instead of port 80. Or an https application running on port 8443 instead of 443. Then we need to add the custom application to the Juniper Applications list.
In a few minutes, we will se how we add a custom application into application list.
If you notice at the configuration of applications by the juniper, you see that most of them are matched by protocol number and destination port.
But there are some applications that can not be recognized just with protocol number and port number since they run over dynamic ports. The most famous ones are ftp.
You can see the configuration of ftp application detection by the command “show configuration groups junos-defaults applications application junos-ftp” or show configuration groups “junos-defaults applications application junos-ftp-data”.
[edit]
rayka# run show configuration groups junos-defaults applications application junos-ftp-data
##
## protect: groups junos-defaults
##
application-protocol ftp-data;
protocol tcp;
destination-port 20;
For these application, application-protocol must be inspected. in other words for the detection of dynamic applications, the header of application layer must be inspected.
Add custom applications in application list of juniper SRX
To add a custom application, in addition to protocol number, destination port and application-protocol, we have also the options ether-type, source-port and icmp-code and icmp-type that we can see with command “set applications application TEST ?”.
rayka# set applications application TEST ?
Possible completions:
application-protocol Application protocol type
+ apply-groups Groups from which to inherit configuration data
+ apply-groups-except Don't inherit configuration data from these groups
description Text description of application
destination-port Match TCP/UDP destination port
do-not-translate-A-query-to-AAAA-query Knob to control the translation of A query to AAAA query
do-not-translate-AAAA-query-to-A-query Knob to control the translation of AAAA query to A query
ether-type Match ether type
icmp-code Match ICMP message code
icmp-type Match ICMP message type
icmp6-code Match ICMP6 message code
icmp6-type Match ICMP6 message type
inactivity-timeout Application-specific inactivity timeout (4..86400 seconds)
protocol Match IP protocol type
rpc-program-number Match range of RPC program numbers
source-port Match TCP/UDP source port
> term Define individual application protocols
uuid Match universal unique identifier for DCE RPC objects
[edit]the option term is used when there are more than one option to match an application. For example if a http application runs over both port 80 and 8080.
rayka# set applications application TEST term 1 ?
Possible completions:
<[Enter]> Execute this command
alg Application Layer Gateway
destination-port Match TCP/UDP destination port
icmp-code Match ICMP message code
icmp-type Match ICMP message type
icmp6-code Match ICMP6 message code
icmp6-type Match ICMP6 message type
inactivity-timeout Application-specific inactivity timeout (4..86400 seconds)
protocol Match IP protocol type
rpc-program-number Match range of RPC program numbers
source-port Match TCP/UDP source port
uuid Match universal unique identifier for DCE RPC objects
| Pipe through a command
[edit]Let’s also check once the list of protocols and application-protocol.
rayka# set applications application TEST protocol ?
Possible completions:
<number> Numeric protocol value (1 .. 255) or 0 for any protocol
ah IP Security authentication header
egp Exterior gateway protocol
esp IPSec Encapsulating Security Payload
gre Generic routing encapsulation
icmp Internet Control Message Protocol
icmp6 Internet Control Message Protocol Version 6
igmp Internet Group Management Protocol
ipip IP in IP
ospf Open Shortest Path First
pim Protocol Independent Multicast
rsvp Resource Reservation Protocol
sctp Stream Control Transmission Protocol
tcp Transmission Control Protocol
udp User Datagram Protocol
[edit]
rayka# set applications application test application-protocol ?
Possible completions:
dns Domain Name Service
ftp File Transfer Protocol
ftp-data File Transfer Protocol Data Session
gprs-gtp-c GPRS Tunneling Control Plane
gprs-gtp-u GPRS Tunneling User Plane
gprs-gtp-v0 GPRS Tunneling Version 0
gprs-sctp GPRS Stream Control Protocol
http Hypertext Transfer Protocol
https Hypertext Transfer Protocol
ignore Ignore application type
ike-esp-nat IKE/ESP with NAT
imap Internet Mail Access Protocol
imaps Internet Mail Access Protocol Over TLS
mgcp-ca MGCP-CA
mgcp-ua MGCP-UA
ms-rpc Microsoft RPC
none None
pop3 Post Office Protocol 3 Protocol
pop3s Post Office Protocol 3 Protocol Over TLS
pptp Point-to-Point Tunneling Protocol
q931 Q.931
ras RAS
realaudio RealAudio
rsh Remote Shell
rtsp Real Time Streaming Protocol
sccp Skinny Client Control Protocol
sip Session Initiation Protocol
smtp Simple Mail Transfer Protocol
smtps Simple Mail Transfer Protocol Over TLS
sqlnet-v2 Oracle SQL*Net Version 2
ssh Secure Shell Protocol
sun-rpc Sun Microsystems RPC
talk Talk Program
telnet Telnet Protocol
tftp Trivial File Transfer Protocol
twamp Two Way Active Meaurement Protocol
[edit]
Custom application Configuration Example
In this example, we create two custom applications, CUSTOM-WEB matching port 8080 instead of 80 and CUSTOM-SECURE-WEB matching port 8443 instead of port 443.
With “application-set”, exactly like “address-set” in address book we can match multiple application at once. Therefore instead of writing multiple lines in security policy to match multiple applications, we can match all those applications at once.
application-set CUSTOM-WEB-SET is created to match both CUSTOM-WEB and CUSTOM-SECURE-WEB.
rayka# run show configuration | display set | grep applications
set applications application CUSTOM-WEB protocol tcp
set applications application CUSTOM-WEB destination-port 8080
set applications application CUSTOM-WEB inactivity-timeout 300
set applications application CUSTOM-SECURE-WEB protocol tcp
set applications application CUSTOM-SECURE-WEB destination-port 8443
set applications application-set CUSTOM-WEB-SET application CUSTOM-WEB
set applications application-set CUSTOM-WEB-SET application CUSTOM-SECURE-WEB
[edit]
rayka#
rayka# show | compare
[edit]
+ applications {
+ application CUSTOM-WEB {
+ protocol tcp;
+ destination-port 8080;
+ inactivity-timeout 300;
+ }
+ application CUSTOM-SECURE-WEB {
+ protocol tcp;
+ destination-port 8443;
+ }
+ application-set CUSTOM-WEB-SET {
+ application CUSTOM-WEB;
+ application CUSTOM-SECURE-WEB;
+ }
+ }And finally, let’s check how juniper standard applications or custom applications can be called in a security policy.
rayka# set security policies from-zone inside to-zone outside policy TEST match application ?
Possible completions:
<applications> Specify application or application-set name to match
CUSTOM-SECURE-WEB [applications application <*>]
CUSTOM-WEB [applications application <*>]
CUSTOM-WEB-SET [applications application-set <*>]
[ Open a set of values
any [applications application <*>]
junos-aol [applications application <*>]
...As you can see our custom applications and application-set is also available in this list of applications.