ISATAP tunneling is an IPv6 migration mechanism that enables IPv6 communication over an IPv4-only infrastructure. It is specifically designed to establish IPv6 communication between endpoints, unlike 6to4, which facilitates IPv6 communication between sites. While ISATAP, like 6to4, is largely considered obsolete today, studying it can still provide valuable insights into multipoint dynamic VPN solutions.
ISATAP Fundamental
If you recall from the previous lesson, I mentioned that in all IPv6-over-IPv4 multipoint VPN solutions, there is a relationship between IPv4 and IPv6 addresses. When traffic is generated to an IPv6 destination, the IPv4 address of destination or destination gateway is extracted from the destination IPv6 address, and a dynamic point-to-point tunnel is created.
In ISATAP, a common /64-bit prefix is shared among all hosts that want to communicate over an IPv4 infrastructure. The next 32 bits are fixed as „0000:5EFE“, and the final 32 bits are derived from the host’s IPv4 address.
| ISATAP Address Structure | ||
|---|---|---|
| 64 bits | 32 bits | 32 bits |
| IPv6 Prefix (shared by all ISATAP hosts) | Fixed Value: 0000:5EFE | Host's IPv4 Address |
| 2001:0DB8:AC10:: | 0000:5EFE | 192.0.2.1 mapped as hexadecimal |
In other words, all nodes in the same ISATAP tunnel share the same subnet, with the only difference being the last 32 bits, which are extracted from each node’s IPv4 address.
This tunneling method does not support NAT. Therefore, nodes must either:
Be in the same autonomous system and reachable via private IPv4 addresses, or
Use public IPv4 addresses if they need to communicate over the IPv4 Internet.
ISATAP Tunneling demonstration
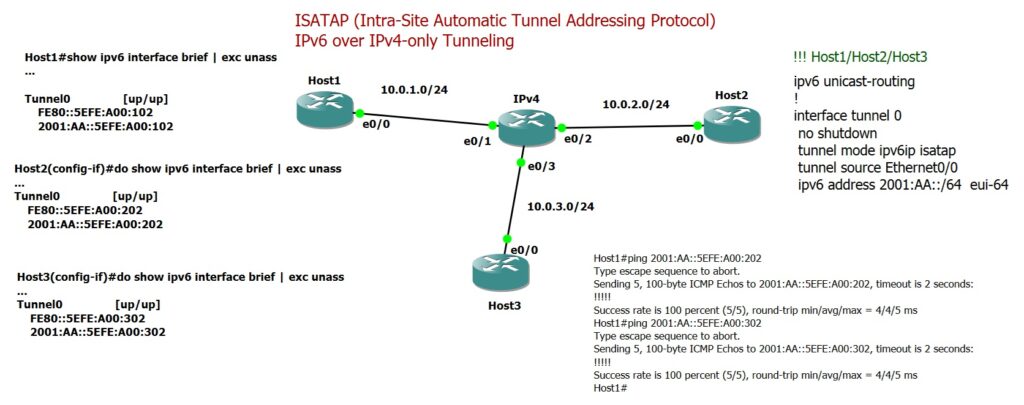
To better understand how ISATAP tunneling works, I have prepared a topology with three nodes connected via an IPv4 infrastructure. In this setup, I am using Cisco routers as hosts. These nodes are configured to communicate with each other using IPv6 over the IPv4 network.
We define a /64 prefix to serve as the ISATAP prefix and then enable ISATAP tunneling on each host. In this example, the prefix 2001:AA::/64 is used. An ISATAP tunnel is configured on each host, and the IPv6 address of the tunnel interface is assigned using the command:
ipv6 address 2001:AA::/64 eui-64
In ISATAP, the EUI-64 mechanism does not derive the interface identifier of the IPv6 address from the MAC address. Instead, it uses the ISATAP mechanism, which generates the interface identifier by combining the fixed value 5EFE with the hexadecimal equivalent of the IPv4 address of the node.
!!! Host1/Host2/Host3 ipv6 unicast-routing ! interface tunnel 0 no shutdown tunnel mode ipv6ip isatap tunnel source Ethernet0/0 ipv6 address 2001:AA::/64 eui-64
Using the command show
ipv6 interface brief, we can verify how the IPv6 address is automatically generated on ISATAP tunnel interfaces.
Host1#show ipv6 interface brief | exc unass
...
Tunnel0 [up/up]
FE80::5EFE:A00:102
2001:AA::5EFE:A00:102
Host2(config-if)#do show ipv6 interface brief | exc unass
...
Tunnel0 [up/up]
FE80::5EFE:A00:202
2001:AA::5EFE:A00:202
Host3(config-if)#do show ipv6 interface brief | exc unass
...
Tunnel0 [up/up]
FE80::5EFE:A00:302
2001:AA::5EFE:A00:302
Finally, we will use the ping command to test IPv6 connectivity between the three hosts over the IPv4 infrastructure.
Host1#ping 2001:AA::5EFE:A00:202 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:AA::5EFE:A00:202, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
Host1#ping 2001:AA::5EFE:A00:302 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:AA::5EFE:A00:302, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms Host1#
Great insights, thanks for sharing!
Network Engineering Services