F5 DNS iRule allows you to inspect incoming DNS queries and change the response based on the query type or content, or even redirect requests to different servers based on custom logic.
F5 DNS iRule Fundamental
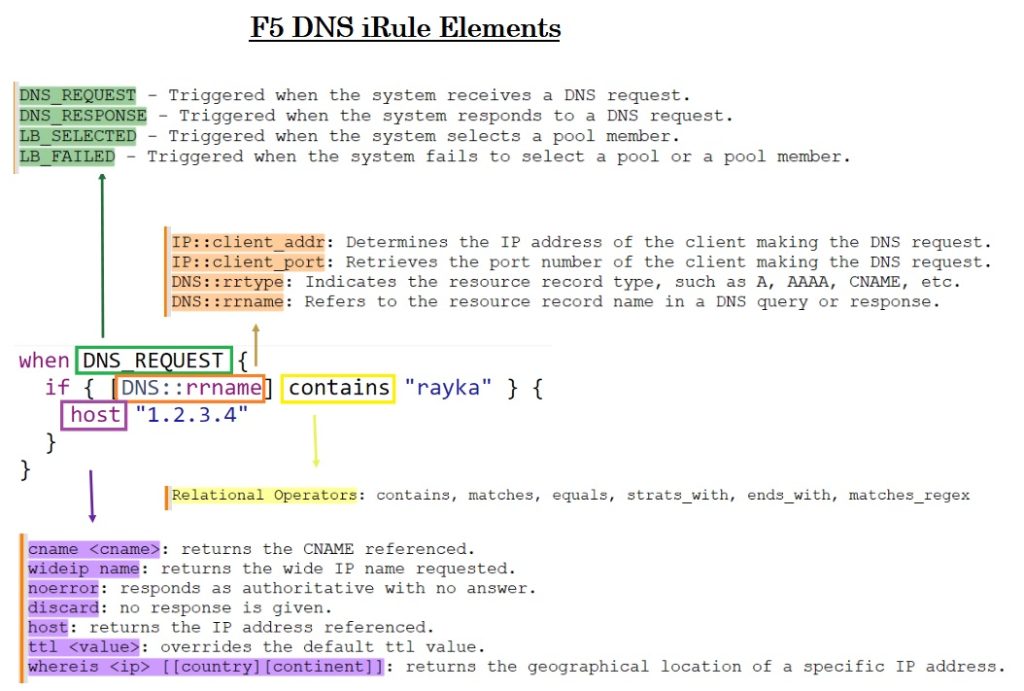
This figure tries to show you the concept of F5 DNS iRule with a practical example.
An F5 DNS iRule allows you to direct incoming DNS traffic based on specific conditions. It typically consists of three main sections:
1. Event: This specifies when the iRule should be triggered, such as on a DNS query or response.
2. Condition: The iRule evaluates certain conditions, which could be based on the client’s IP address, the type of DNS resource record, or the name of the resource record.
3. Action: Depending on the conditions, the iRule can alter the default behavior of DNS traffic. Actions can include discarding the DNS packet, resolving a request to a specific A record, or changing the pool that handles the request.
In this iRule:
• The “when DNS_REQUEST” event is triggered on incoming DNS requests.
• The condition checks whether the DNS resource record name contains the keyword “rayka”.
• If the condition is met, the DNS request is resolved to a specific IP address.
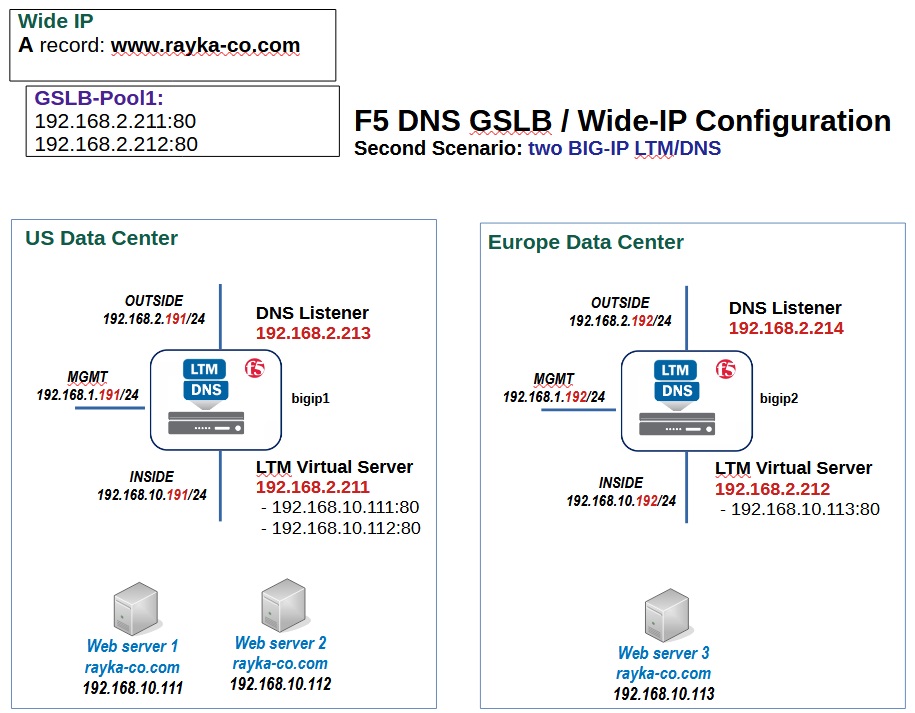
Current Topology
In the latest topology, we have configured a wide IP named “www.rayka-co.com” with Type-A record that has a single pool with two LTM virtual servers 192.168.2.211 and 192.168.2.212.
The default Wide IP load balancing algorithm is round-robin. Therefore, querying the name “www.rayka-co.com” is expected to return one of these two IP addresses 192.168.2.211 or 192.168.2.12.
In the following, we will use iRule to change the DNS behavior for specific DNS queries..
F5 DNS iRule Example 1
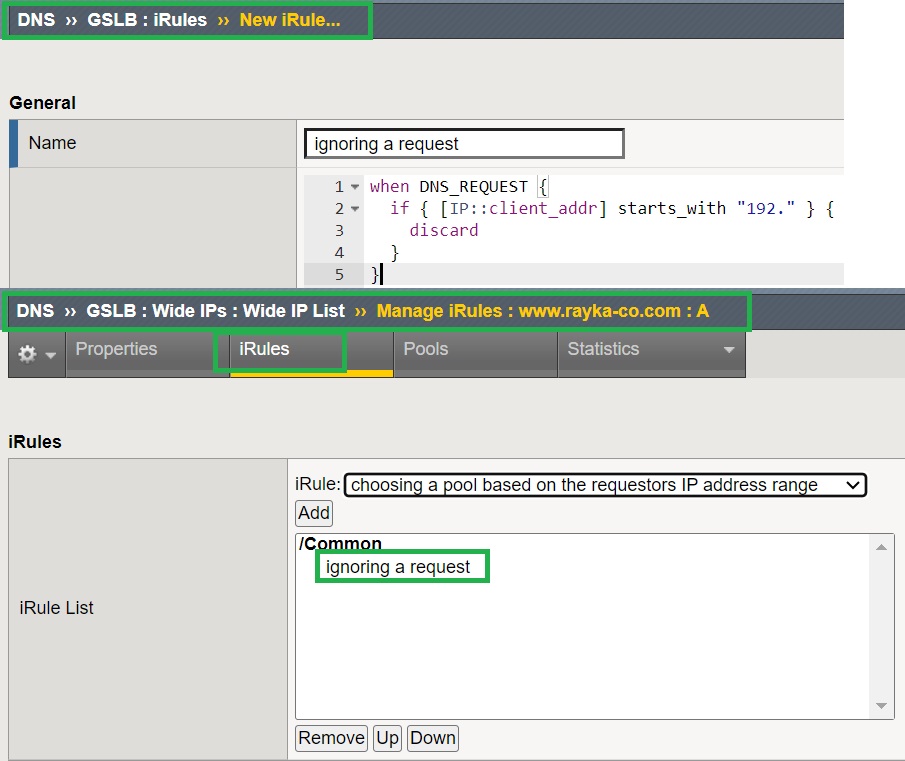
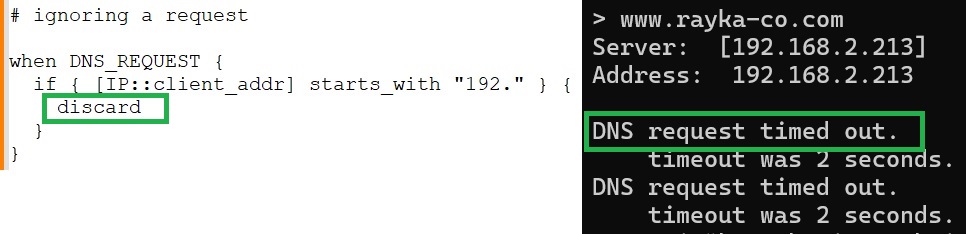
In the first example, we write an iRule to ignore DNS requests if they come from an IP address that starts with “192”.
Client IP address is detected using „IP::client_addr“ condition command. We use „discard“ command action to ignore the request.
First we rite the iRule code in the section “DNS > GSLB > iRules“. Then we assign the iRule to Wide IP name.
# ignoring a request when DNS_REQUEST { if { [IP::client_addr] starts_with "192." } { discard } }
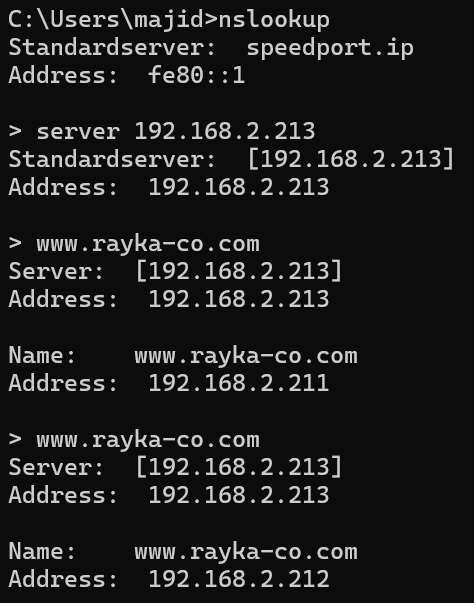
Now let’s check what is the DNS response when the client IP address matches the condition.
F5 DNS iRule Example 2
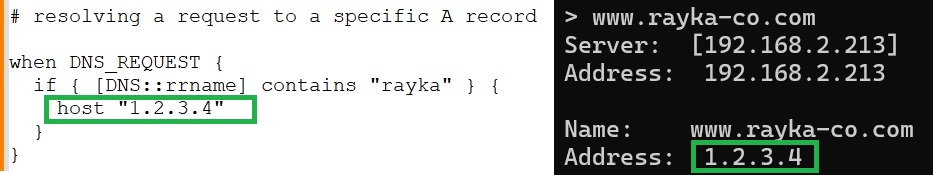
In the second example, we modify the DNS response to return a specific IP address if the DNS query contains the name “rayka”.
The requested name in the DNS query is detected using the “DNS::rrname” conditional command. We use the „contain“ operator to find a keyword in the query name.
The “host” action command is used to returns a specific IP address in response to the request.
# resolving a request to a specific A record when DNS_REQUEST { if { [DNS::rrname] contains "rayka" } { host "1.2.3.4" } }
We then check the name “www.rayka-co.com” to make sure it is working properly.
F5 DNS iRule Example 3
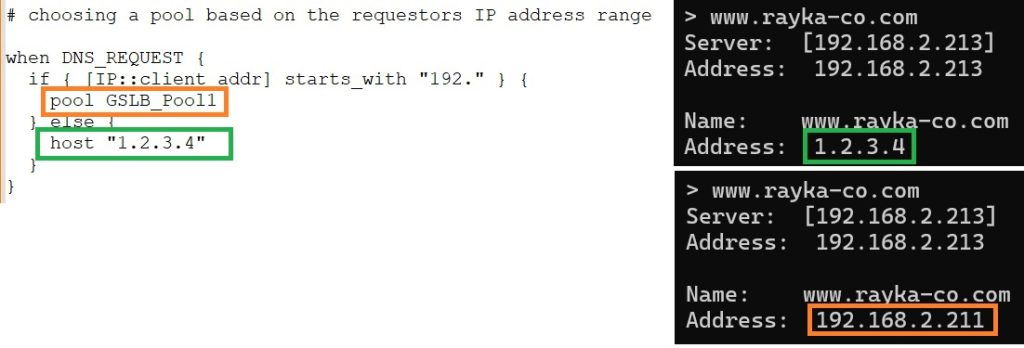
In the third example, if the DNS query that sends the client IP address is started with a specific number, the DNS response will come from a specific pool, otherwise it will resolve to a specific IP address.
What is new in this example is the use of the action command “pool” to resolve the DNS query from a specific pool.
# choosing a pool based on the requestors IP address range when DNS_REQUEST { if { [IP::client_addr] starts_with "192." } { pool GSLB_Pool1 } else { host "1.2.3.4" } }
Then we check once when the client IP address meets the first condition and once when it meets the second condition.
F5 DNS iRule Example 4
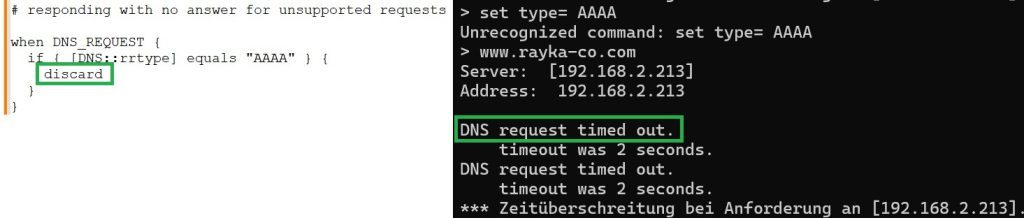
The final example discards an unsupported AAAA IPv6 request. It uses “DNS::rrtype” to detect the request type.
# responding with no answer for unsupported requests when DNS_REQUEST { if { [DNS::rrtype] equals "AAAA" } { discard } }
We then send a DNS query of type AAAA to ensure that we do not receive a DNS response.