F5 AWAF XSS protection detects and blocks malicious script injections in trusted web pages like comment sections, forums, login forms, and profile pages. This section demonstrates an XSS attack in the DVWA web application and its mitigation using the F5 AWAF module.
XSS Attacks and F5 AWAF Protection
An XSS (Cross-Site Scripting) attack is a security vulnerability where attackers inject malicious scripts into web content that is then delivered to and executed in the browsers of other users. This can happen in vulnerable web applications, such as forum pages or comment sections, allowing the attacker to execute scripts in the browsers of other users who view the compromised content.
In the DVWA web application, you can simulate three types of XSS attacks: stored XSS, reflected XSS, and DOM-based XSS.
Stored XSS: The malicious script is stored on the server through a vulnerable web page and is executed in the browsers of other users when they view the same page.
Reflected XSS: The attacker injects a script into a user input field in which the entire user input or part of it is reflected to the users (e.g., search box). The script is reflected back in the server’s response and executed in the user’s browser.
DOM-based XSS: The vulnerability is on the client side. The script is executed by manipulating client-side code (e.g., a form or URL), which the application then runs in the user’s browser.
demonstrate XSS attacks
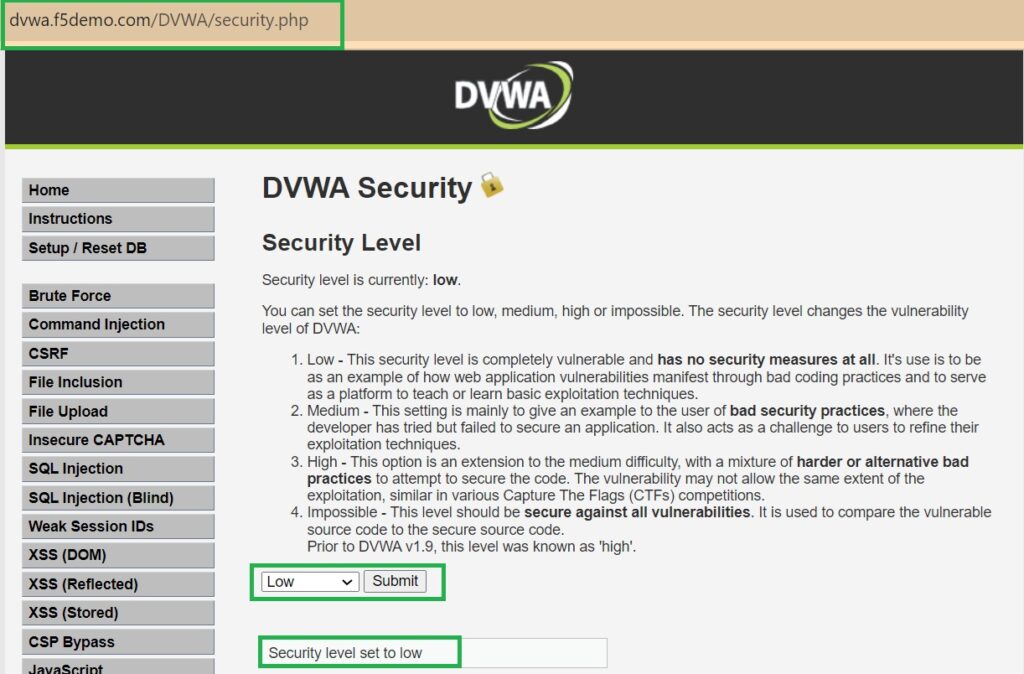
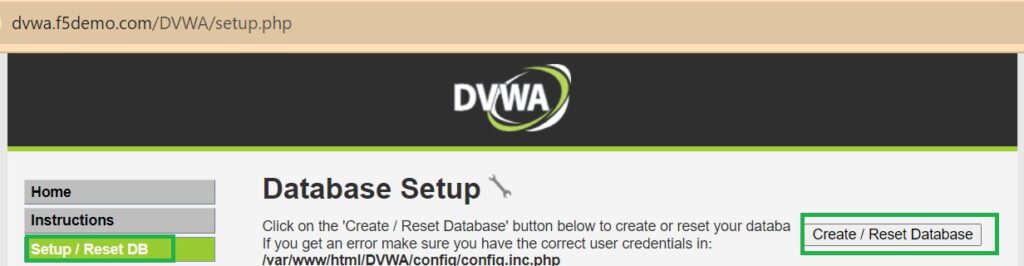
To demonstrate XSS attacks in DVWA, first ensure that the security level is set to low to make the application easily vulnerable, and reset all settings to their default state.
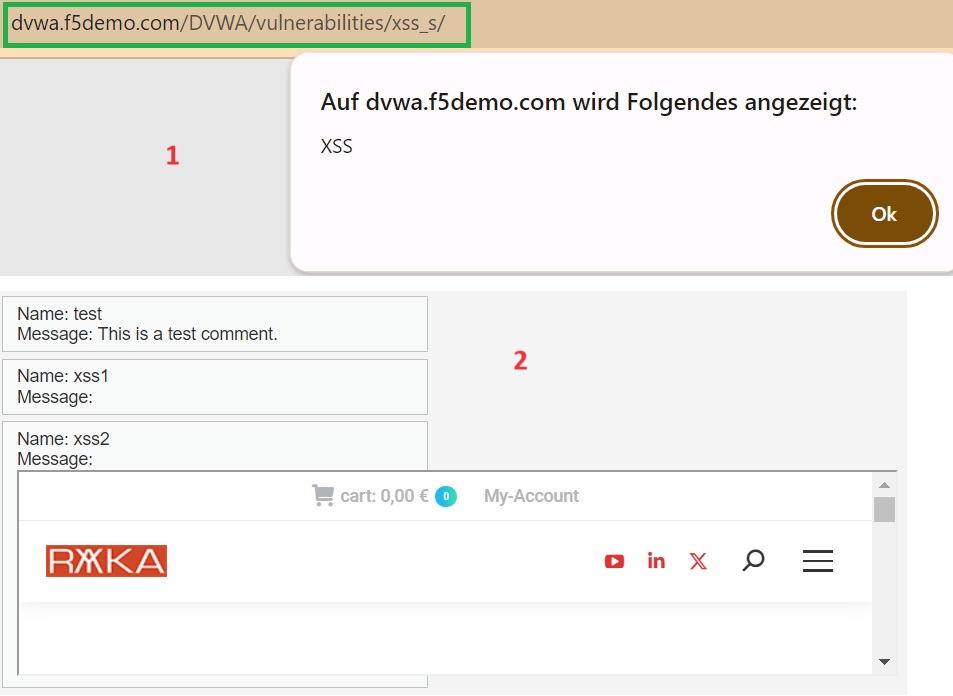
Stored XSS Attack
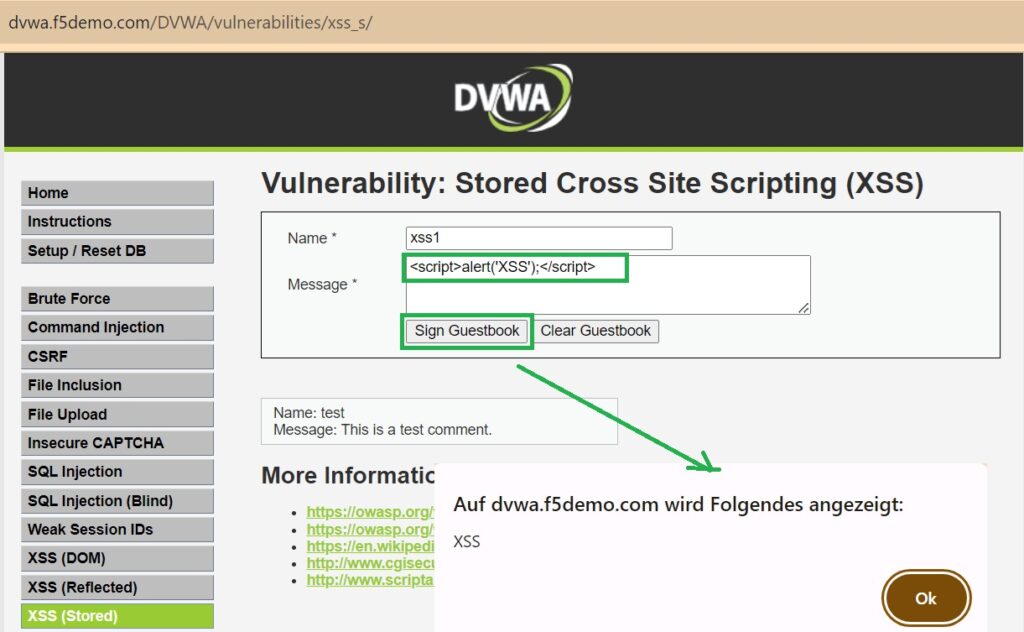
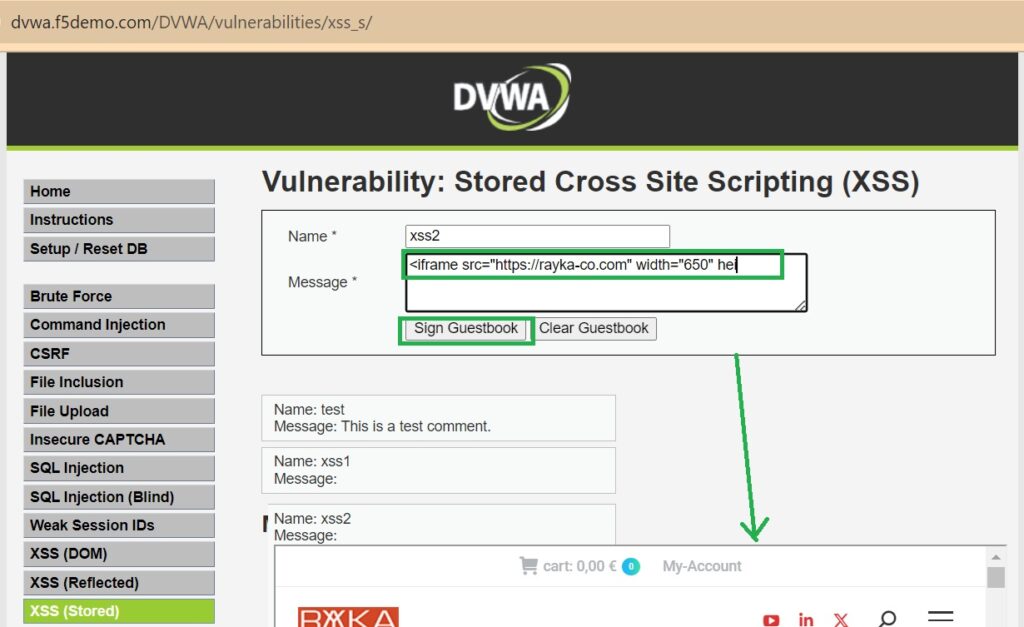
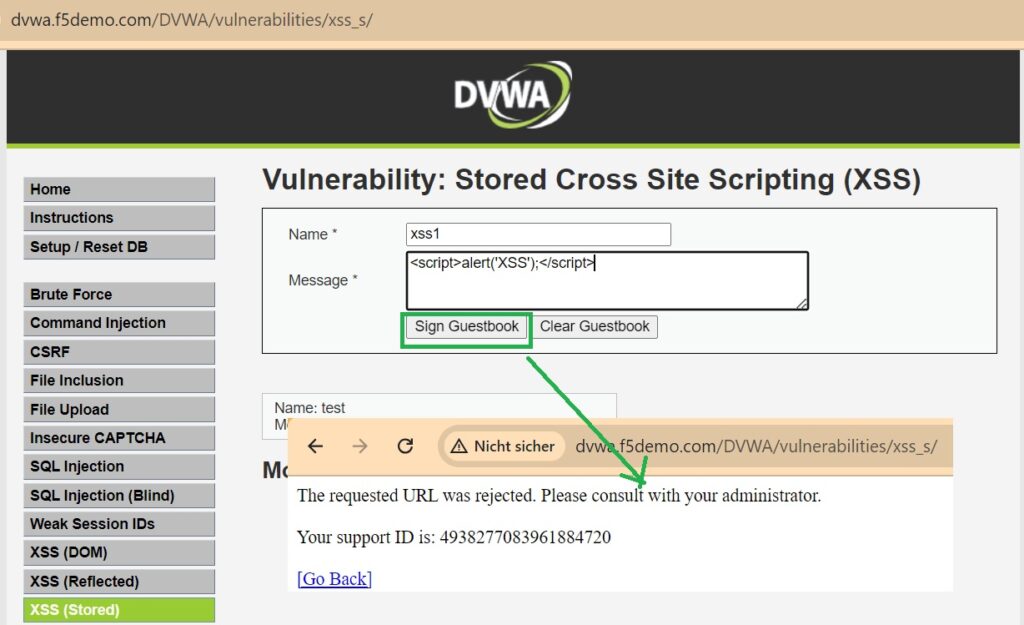
Then, in the stored XSS section, which allows sending a title and comment visible to all users, input a sample malicious script and an iframe code pointing to a malicious website.
For this demonstration, we use a simple script to display an alert and an iframe pointing to the RAYKA website.
<script>alert('XSS');</script>
<iframe src="https://rayka-co.com" width="650" height="320"></iframe>
If you log out and then log in as another user, “smithy”, in the DVWA web application, and access the stored XSS section to view messages from other users, the injected script and iframe will execute in your browser.
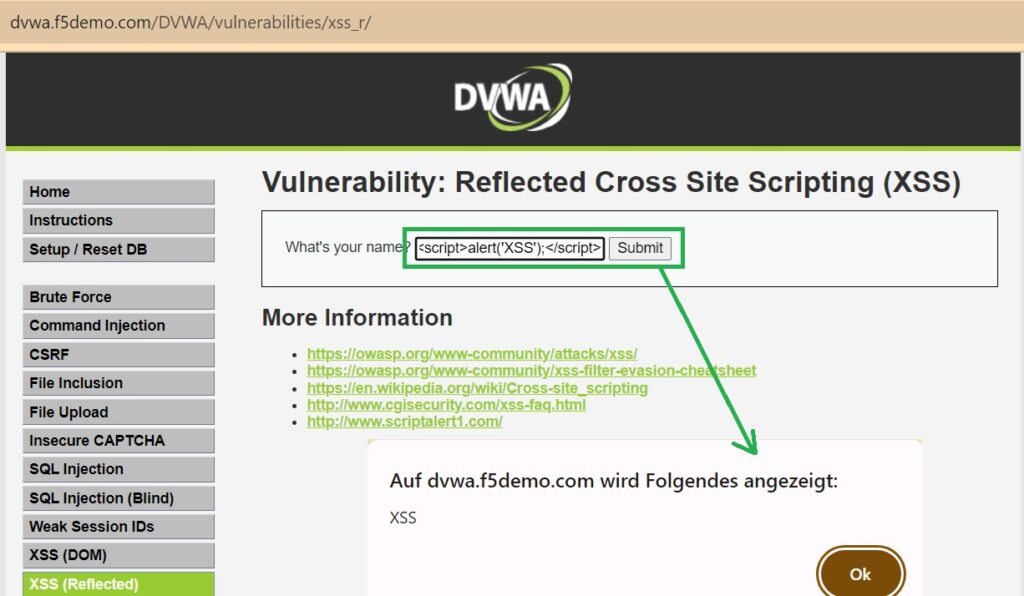
reflected XSS Attack
In the reflected XSS section of DVWA, users input data such as their name in search queries, which the server echoes back to them. Attackers exploit this by convincing victims, through tactics like crafted links or social media messages, to input malicious scripts into these vulnerable fields.
For instance, if a victim inputs an alert script into a search box, the vulnerable web application echoes this script back to the user, resulting in its execution in the victim’s browser.
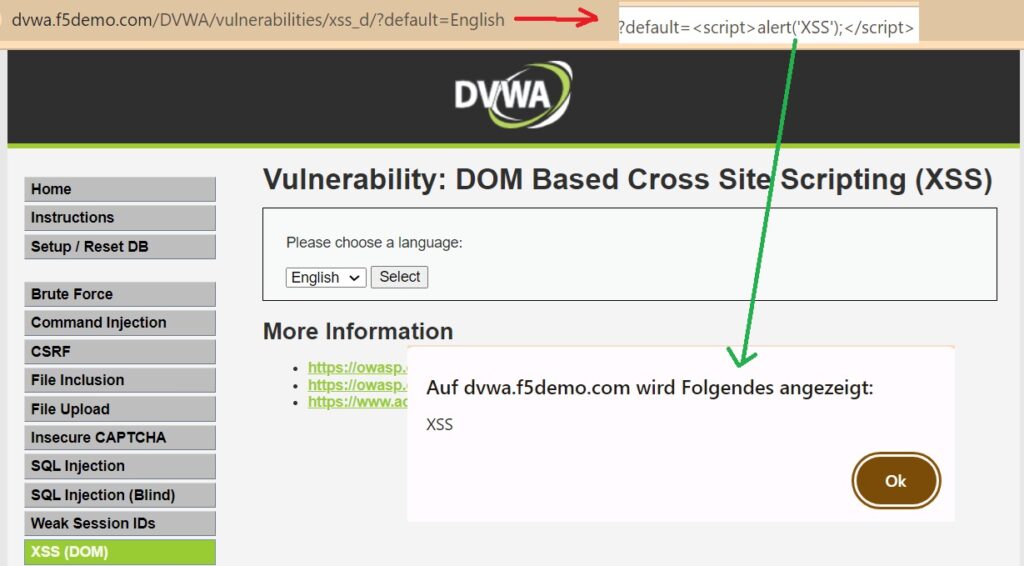
XSS (DOM) Attack
In the third type of XSS attack in the DVWA web application, users are allowed to choose the language, and their selection is reflected in the URL. In this attack, the attacker convinces the victim to click on a URL that includes a malicious script within user input in the URL.
As a demonstration, we can add an alert script in the user input.
F5 AWAF XSS mitigation
Now it’s time to use the F5 AWAF module to protect against XSS attacks. First, reset all changes in the DVWA web application to their default state.
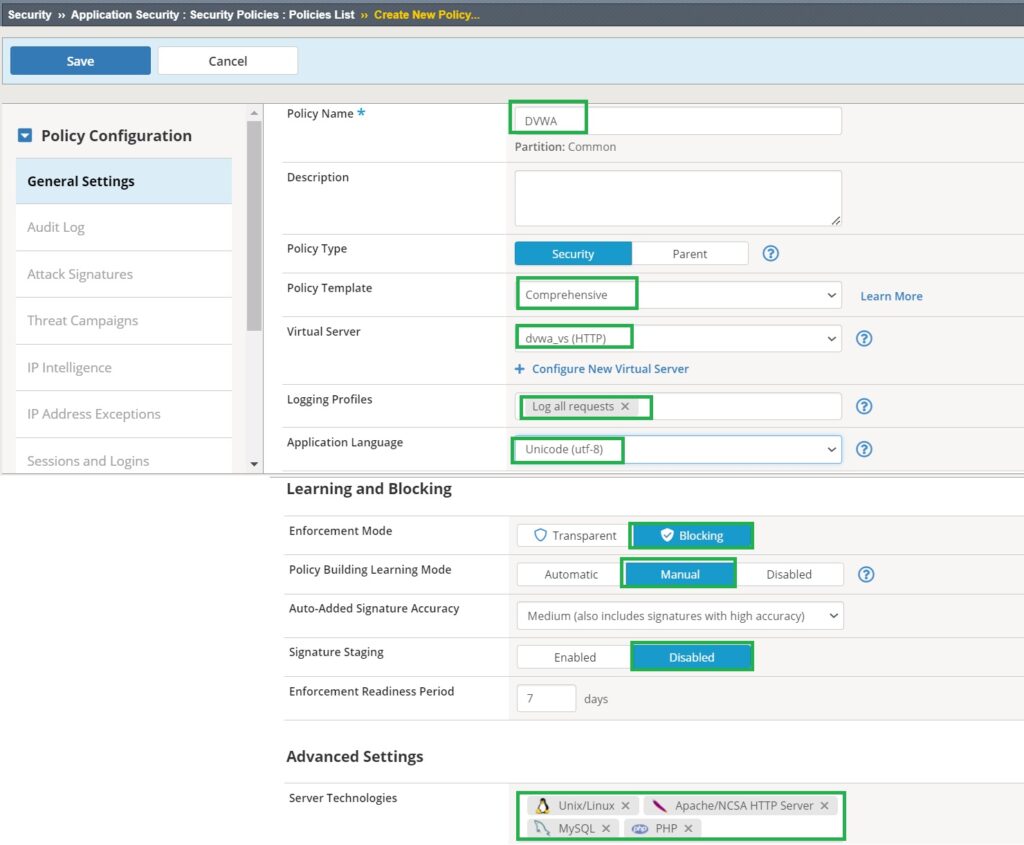
We create a security policy based on a comprehensive security template, setting “Enforcement Mode” to “Blocking,” “Learning Mode” to “Manual,” and “Signature Staging” to “Disabled.” We then assign this policy to the DVWA web application.
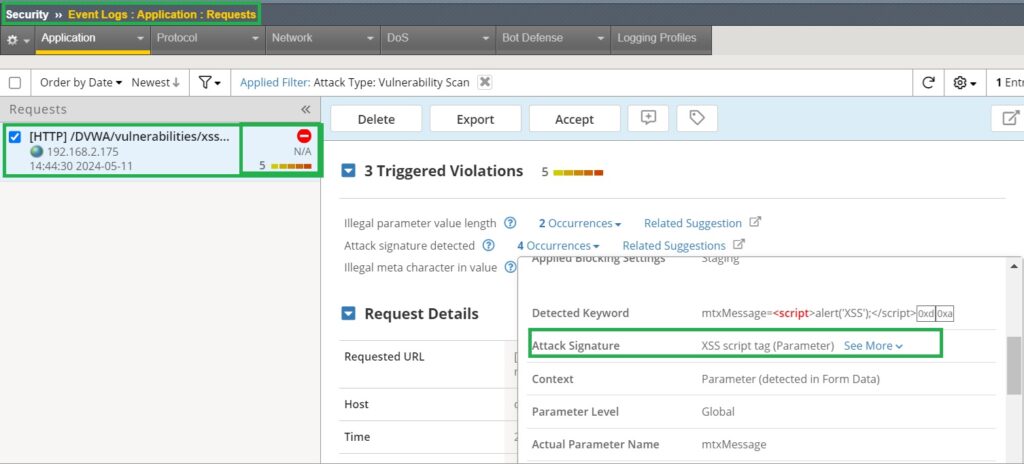
Next, we attempt to simulate the XSS attack once again. This time, the result shows that the attacker’s traffic is rejected.
Checking the application event log reveals that the traffic was blocked because it matched XSS-related attack signatures.