In this section, we will explore and demonstrate the different learning modes available in F5 Advanced WAF (AWAF), including Never (wildcard only), Selective, Compact, and Always. Each mode determines how the F5 AWAF learns and adapts individually to each component of a web application.
Learning in F5 AWAF
To learn the concept of learning modes in F5 AWAF, I will focus on a specific component of a web application, the “parameter”, and limit the discussion to that to make the concept easier to understand.
what is "Parameter" in Web Application
Therefore, as a first step, it is good to know what parameters are in a web application.
In the context of web applications, a parameter is a named variable used to transfer data between the client and the server. Parameters can be part of a URL, form data, or even HTTP headers.
In the simplest form, you see the parameters in the URL.
For example, in a URL like
“http://example.com/page?param1=value1¶m2=value2”
param1 and param2 are parameters with the values value1 and value2 respectively.
what should be learned for each parameter?
To effectively protect a web application, F5 Advanced WAF (AWAF) requires a comprehensive understanding of all allowed parameters and their values within the application. This contains:
What is the allowed value type of each parameter? These are user input, static values, dynamic values, JSON or XML.
What data types have each individual parameters? Alphanumeric, Numeric, String, Boolean, Date/Time, IP Address or URL
What is the minimum and maximum value of each parameter? Which meta characters are allowed for individual parameters?
There are many details that F5 AWAF needs to know about the list of parameters and corresponding values for each web application.
what is learning mode definition?
Based on the learning mode, you now determine how F5 AWAF learns the properties of each parameter. Learn individually as each parameter can have different properties, or generalize the properties of all parameters into a single asterisk (*) parameter.
These are four learning modes in F5 AWAF and this is their definition:
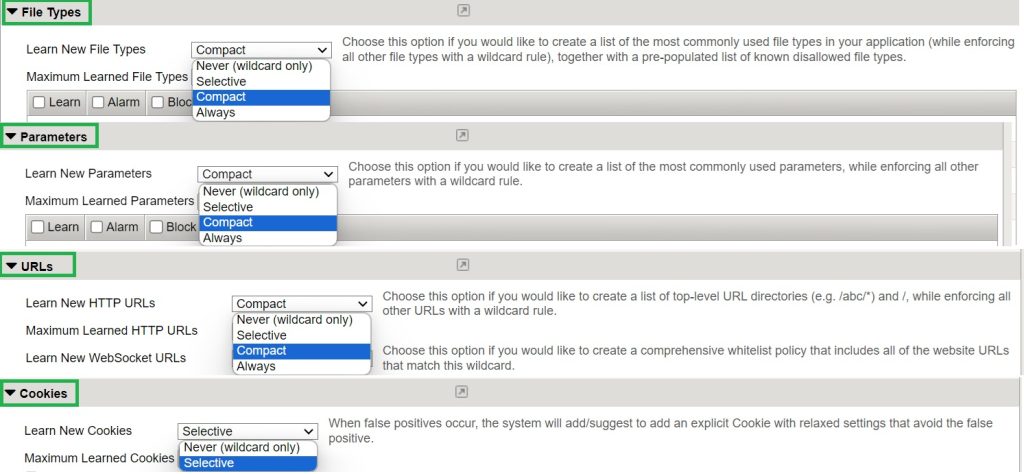
Never (wildcard only):
In this mode, F5 AWAF learns the properties of all parameters in a single asterisk (*) parameter. If the traffic property violates the policies defined in the asterisk parameter and is a false positive, the system suggests relaxing the asterisk parameter setting.
For instance, if a security policy defined by an asterisk (*) parameter specifies that the maximum length of a value must be 10 characters, and then legitimate traffic arrives with a specific parameter value that is 20 characters long, the policy will adapt. The maximum size for the asterisk parameter will be updated from 10 to 20 characters to accommodate this new observation.
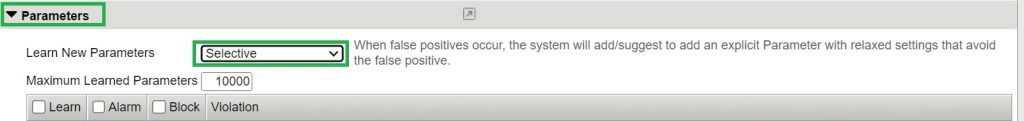
Selective:
In this mode, F5 AWAF learns the properties of all parameters in a single asterisk (*) parameter. If the traffic property violates the policies defined in the asterisk parameter and is a false positive, the system will add/suggest to add an explicit Parameter with relaxed settings that avoid the false positive.
For example, consider a security policy where a wildcard (*) parameter dictates a maximum value length of 10 characters. If legitimate traffic arrives with a parameter “q” and the value that is 20 characters long, the system will then recommend adding an explicit “q” parameter with a revised maximum length of 20 characters to reflect this new observation.
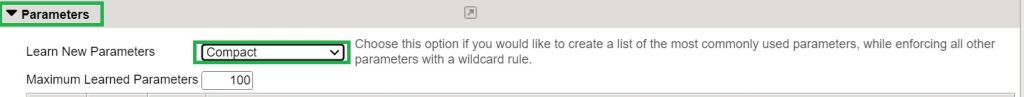
Compact:
In this learning mode, the properties of all parameters are configured under a single asterisk (*) parameter, except for those that occur frequently and have a learning score of 100. With this approach, policies for the most commonly used parameters are created individually, while the rest are grouped under the asterisk (*) parameter.
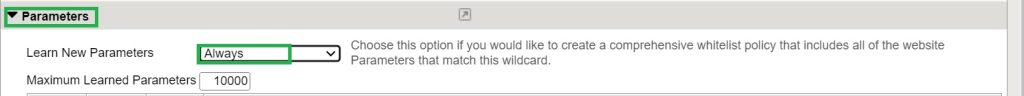
Always:
In this learning mode, each parameter in the web application is learned and fine-tuned individually, even if they have the same properties.
However, in learning mode, we focused on the parameter component of a web application, but you can select the learning mode for each component of a web application individually, such as file types, URLs and cookies.
Subsequently, each of the learning methods will be demonstrated practically.
create security policy
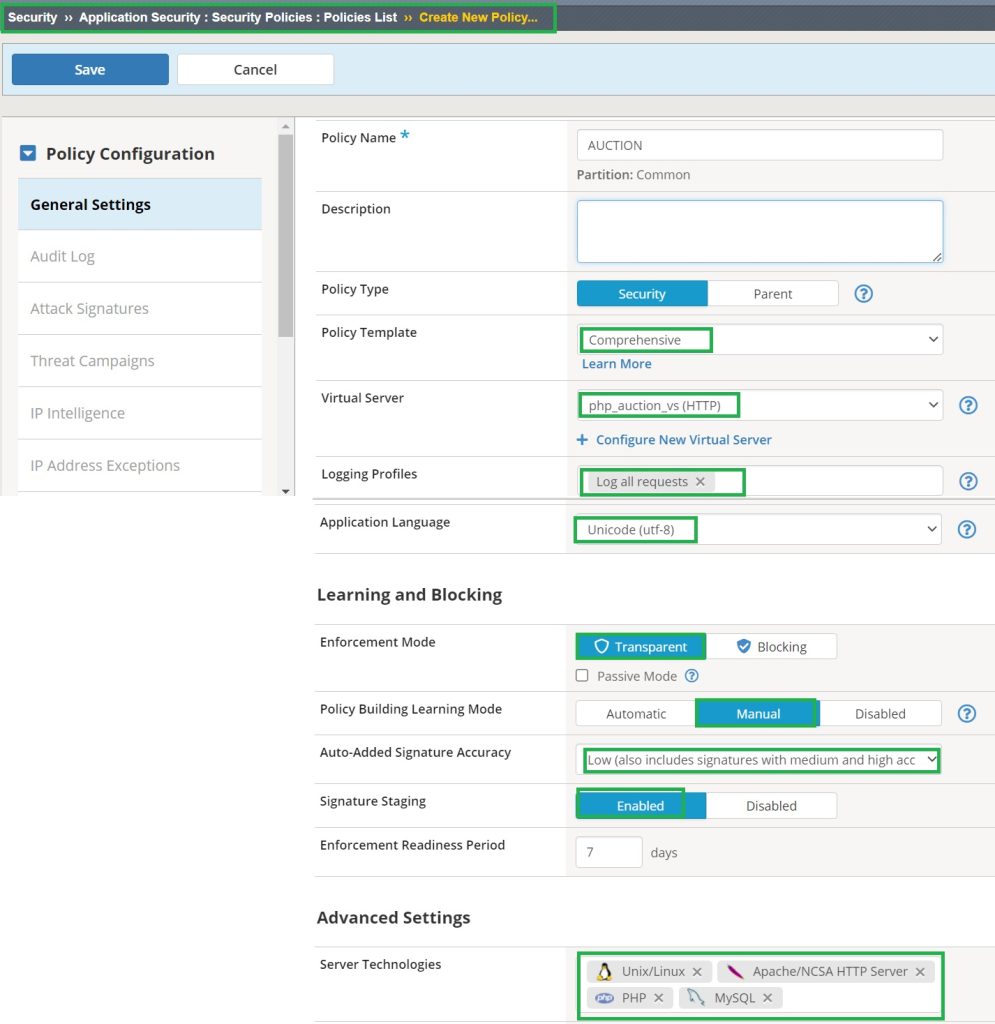
To start demonstration, first we create a security policy based on “comprehensive” security template with “Enforcement Mode” set to “Transparent“, “Learning Mode” set to “Manual“, and “Signature Staging” enabled and assigned to the “Hack-it-Yourself” web application.
Demonstration: Never (wildcard only)
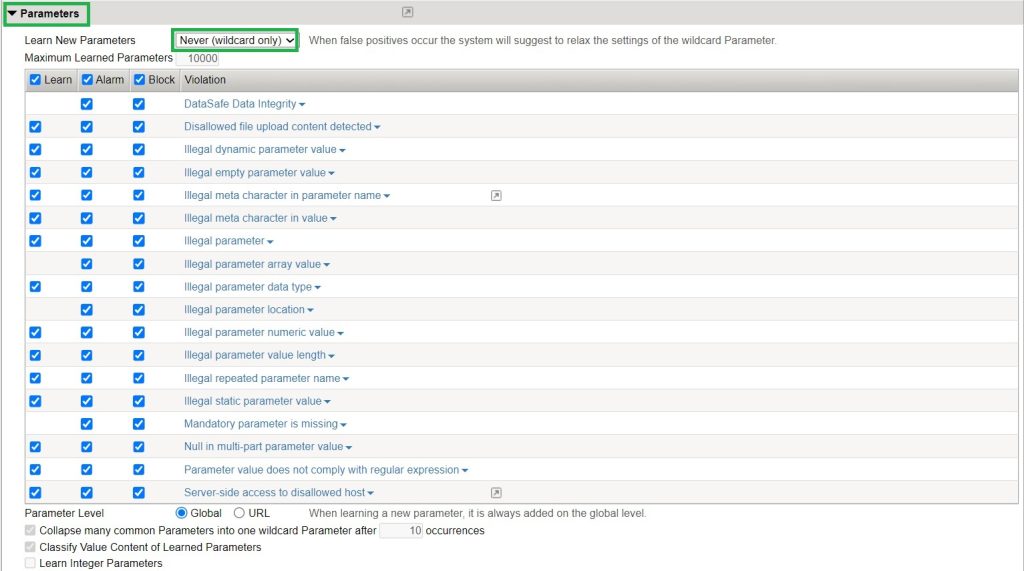
For the first demonstration, we select “Never (wildcard only)” in the parameter section in web application learning and policy setting.
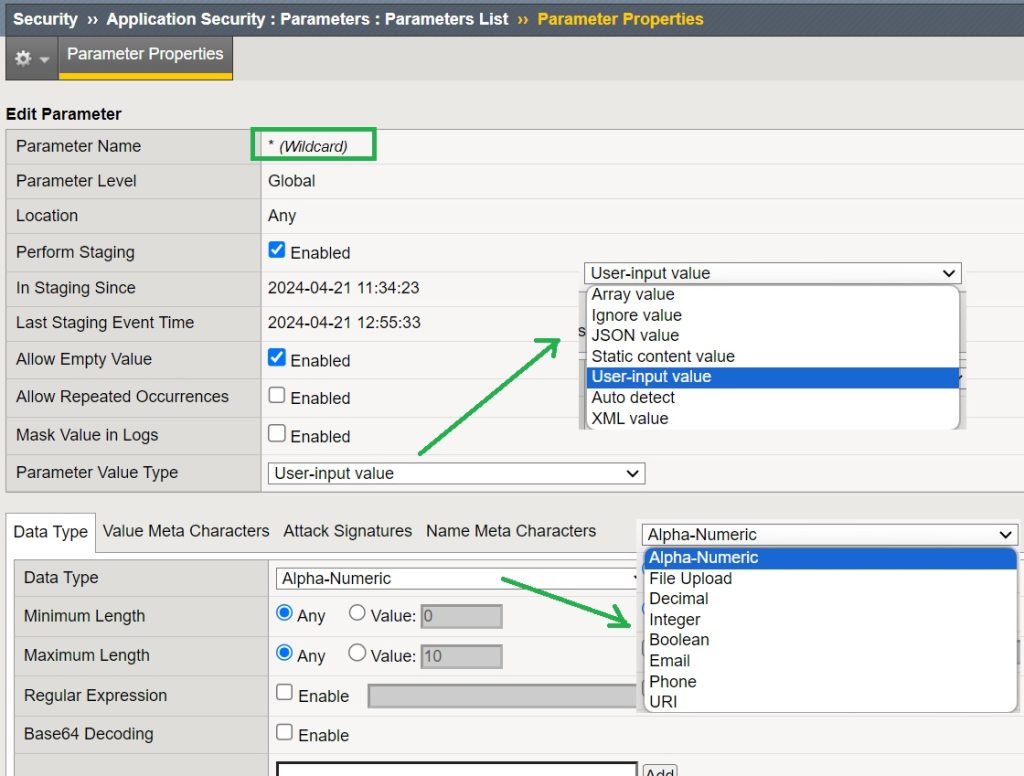
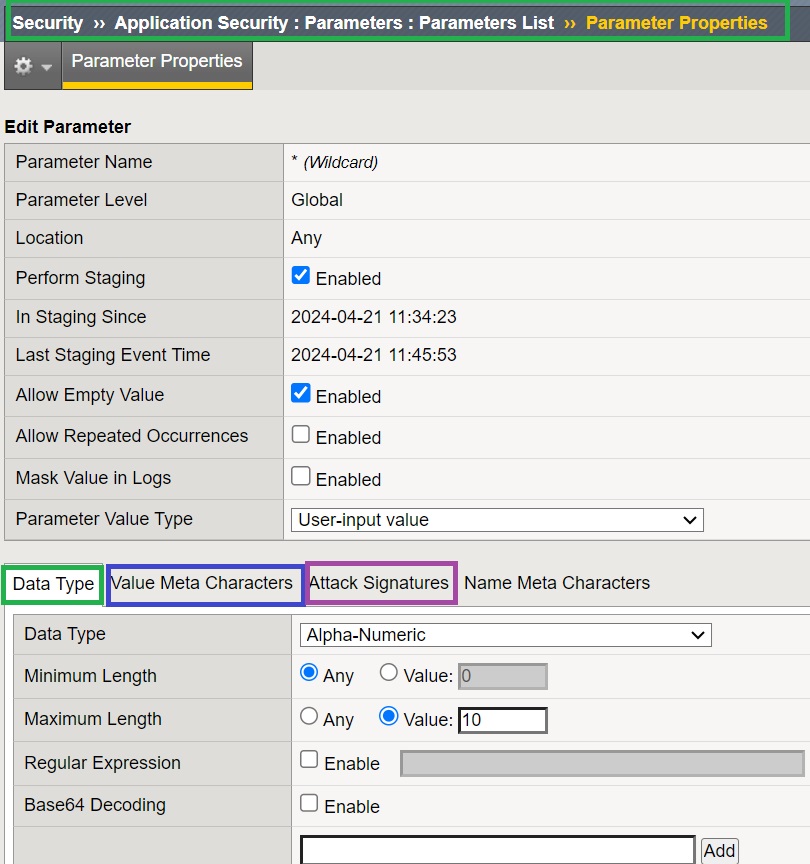
Before generating traffic, we see that there is only one parameter in the parameter list, which is an asterisk (*). This means that the policies of all parameters of the web application are configured and fine-tuned under this parameter.
If we look at the asterisk parameter, we see that you can pass empty values for all parameters. You will also see that the values of all parameters are specified by user input. The data type is alphanumeric and the maximum length of all parameter values is 10.
By default, no meta characters are allowed and no attack signature is disabled.
generate traffic with various parameters
To demonstrate different learning modes, we need to generate traffic to the web application using different parameters.
To do this, I log in to the “Hack-it-yourself” web application with username1 and then click “Control Panel”.
In the URL “http://auction.f5demo.com/user_menu.php?nick=username1” you will see the parameter name “nick” with the value “username1”. Then I will change the parameter value to „username2“ and asterisk (*). Then I will add the parameter „name“ with the value „alex“ at the end of URL.
So far we have generated traffic with two parameters, “Nick” and “Name”.
To generate traffic with other parameter and different values, we search for something like “123456789” in the search field. The result of the request is sent to the server to the server with the parameter name “q” (query).
To generate parameter values with different size, different meta characters and also illegal data for the parameter “q”, we search for the following values in the search box.
123456789 123456789123456789 123456789123456789123456789123456789123456789123456789 abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890abcdefghijklmnopqrstuvwxyz1234567890 abc123!"§$%&/()=?_:;'ÄÖ <iframe src="https://rayka-co.com" title="RAYKA"></iframe> <script>
To see and compare the differences between the different learning modes, we generate identical traffic patterns for each learning mode we select in the parameter’s security policy.
Never (Wildcard only) learning mode result
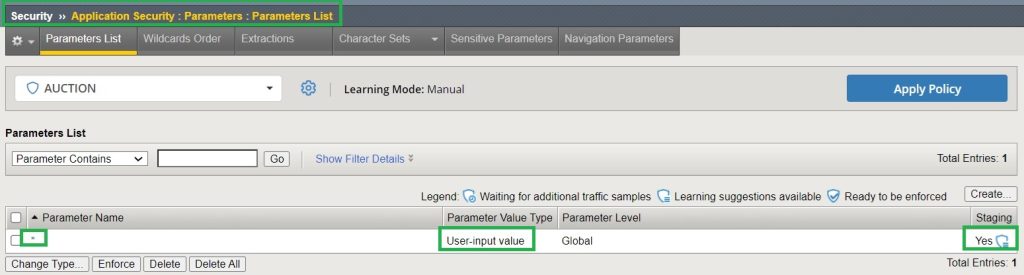
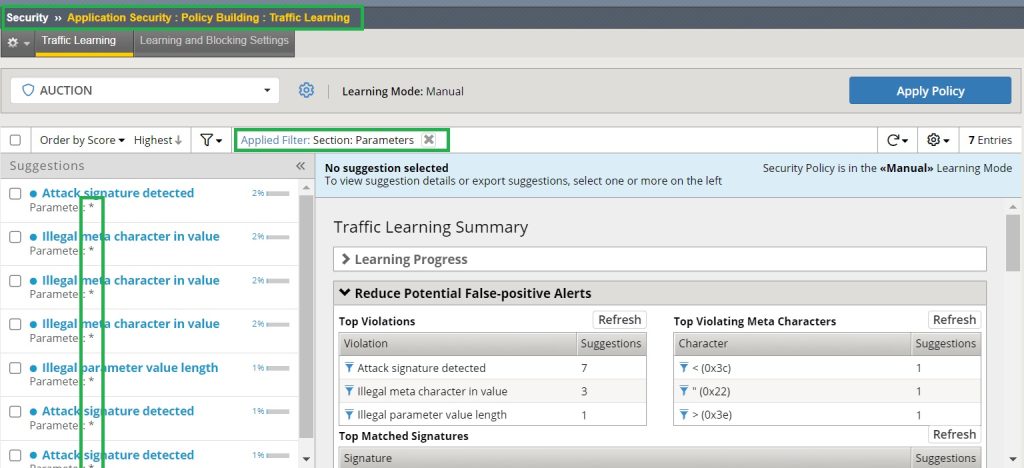
If we check “Security > Application Security > Policy Creation > Traffic Learning” and filter the output by the “Parameters” category, we can see the result of “Never (Wildcard only)” Learning mode.
The result of learning in this mode shows that no new parameters are learned, but only a few meta characters and attack signatures in the asterisk parameter. That is, if we accept them, these meta characters will be added and these attack signatures will be disabled in the asterisk parameters security policy.
Demonstration: Selective
For the next demonstration, we select “Selective” as the learning mode in the parameter section in web application learning and policy setting.
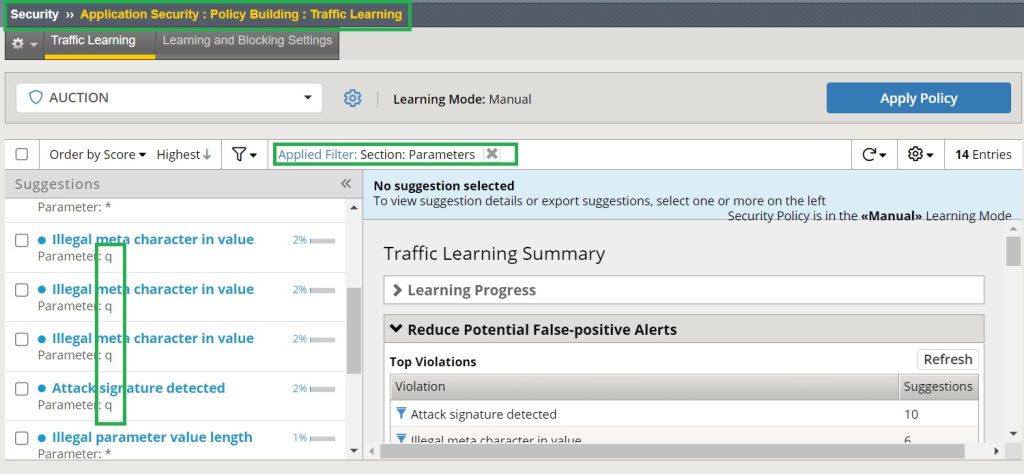
We generate the same traffic again and then check the learning result in the section. „Security > Application Security > Policy Creation > Traffic Learning”.
As you know, in selective mode, only parameters whose traffic violates the asterisk security policy are learned.
Since we violated the security policy for asterisk parameters only through search field or “q” parameters, the “q” parameters are learned with new meta characters and attack signatures.
In other words, if we accept it, the new parameter “q” with new security policies will be added to the list of application parameters.
Demonstration: Always
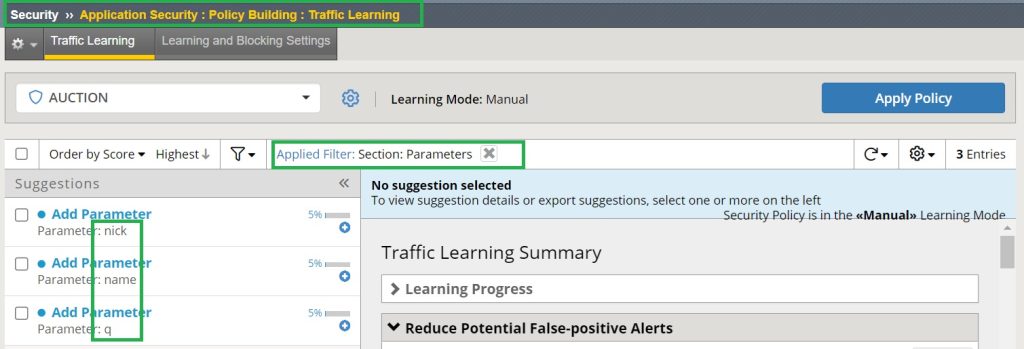
For the next demonstration, we select “Always” as the learning mode in the parameter section in web application learning and policy setting.
If we generate the same traffic pattern for the “Hack-it-yourself” web application, we see that all three parameters “nick”, “name” and “q” are learned individually.
In other words, if we accept these learning suggestions, individual security policies will be created for each parameter in the parameter list.
Demonstration: Compact
For the final demonstration, we select “Compact” as the learning mode in the parameter section in web application learning and policy setting.
As we discussed at the beginning of this lesson, in “Compact” learning mode, a parameter is learned when its learning score is 100.
In previous lessons, we learned that the learning score of a learning suggestion increases when the same traffic comes from different sources at different times or when it is generated from a trusted source.
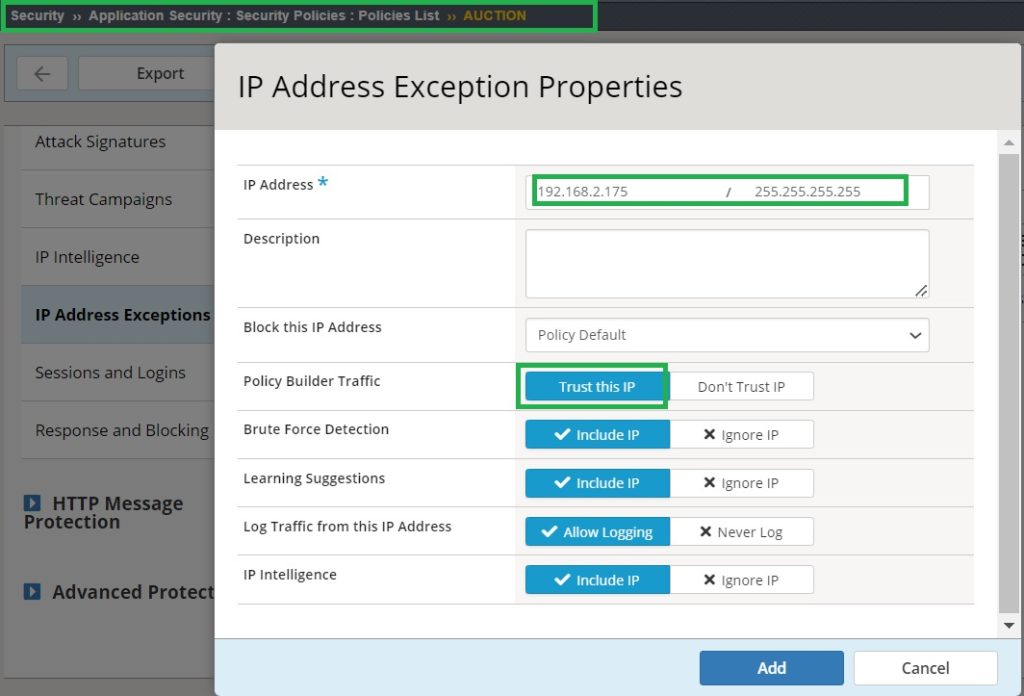
To simulate a traffic receiving a learning suggestion of 100, I add my client IP address as a trusted IP address in the security policy in the “IP Address Exceptions” section.
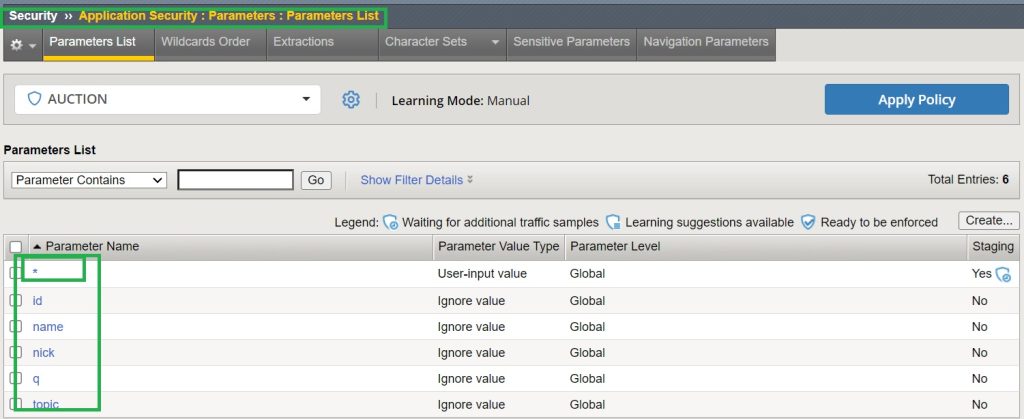
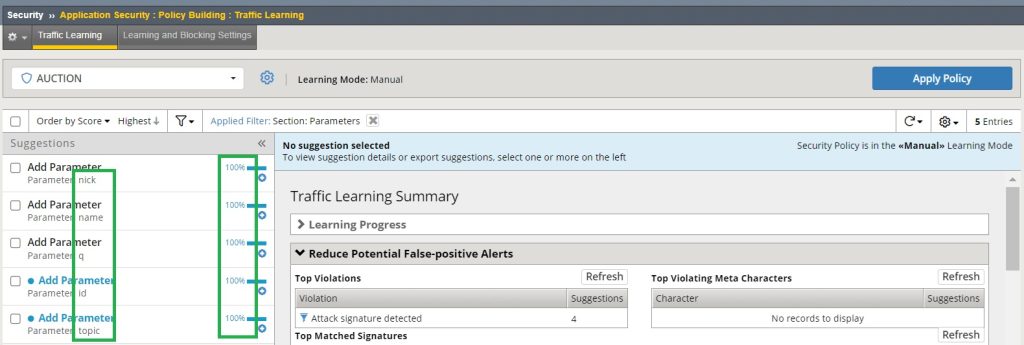
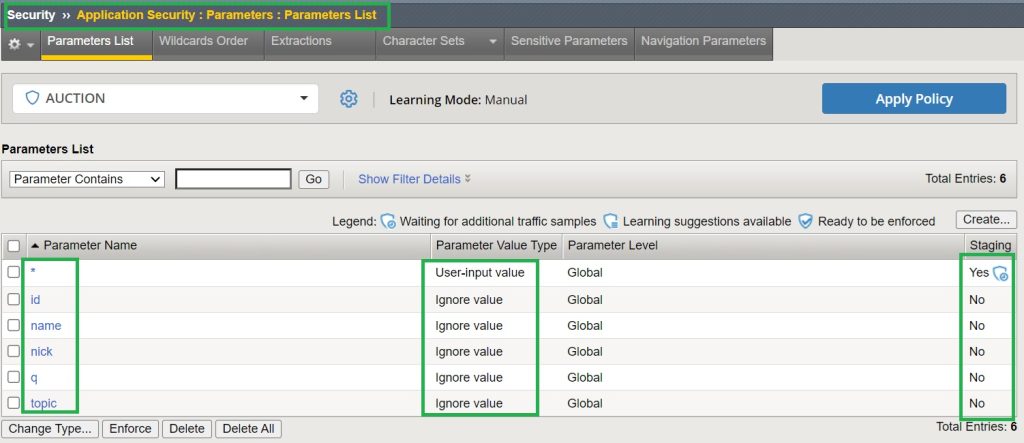
If we generate the same traffic pattern for the “Hack-it-yourself” web application, we see that all parameters including “nick”, “name”, “q”, “id” and „topic“ are learned individually.
The difference this time is that the learning score of all parameters are 100. This is because they are generated from a trusted source. And that is the reason why these parameters are learned in compact mode.
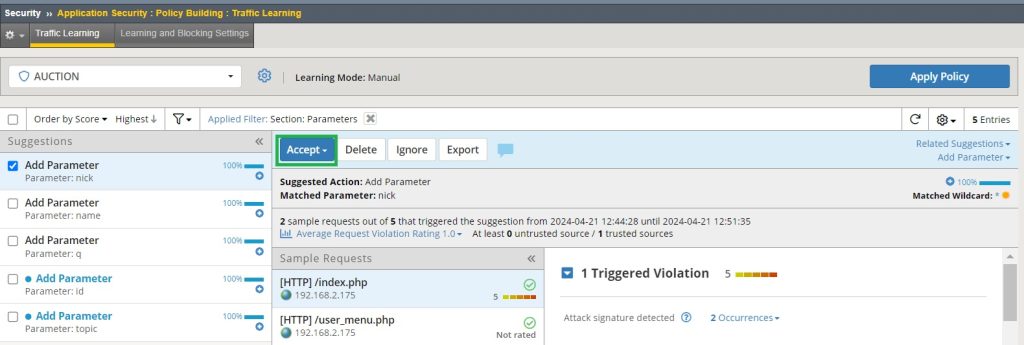
Now let’s accept all learning suggestions for all parameters.
Now if you check the parameter list in the section “Security > Application Security > Parameters > Parameter List”, you will see that in addition to the asterisk, all other learned parameters are also added.