In every web application, only certain file types with predefined properties are permitted. F5 AWAF can either manually or automatically learn allowed file types and their unique properties for each web application. It then discard any file types that are not explicitly permitted, as well as those allowed file types but but whose properties fall outside the learned security policy.
File Type Learning Demonstration
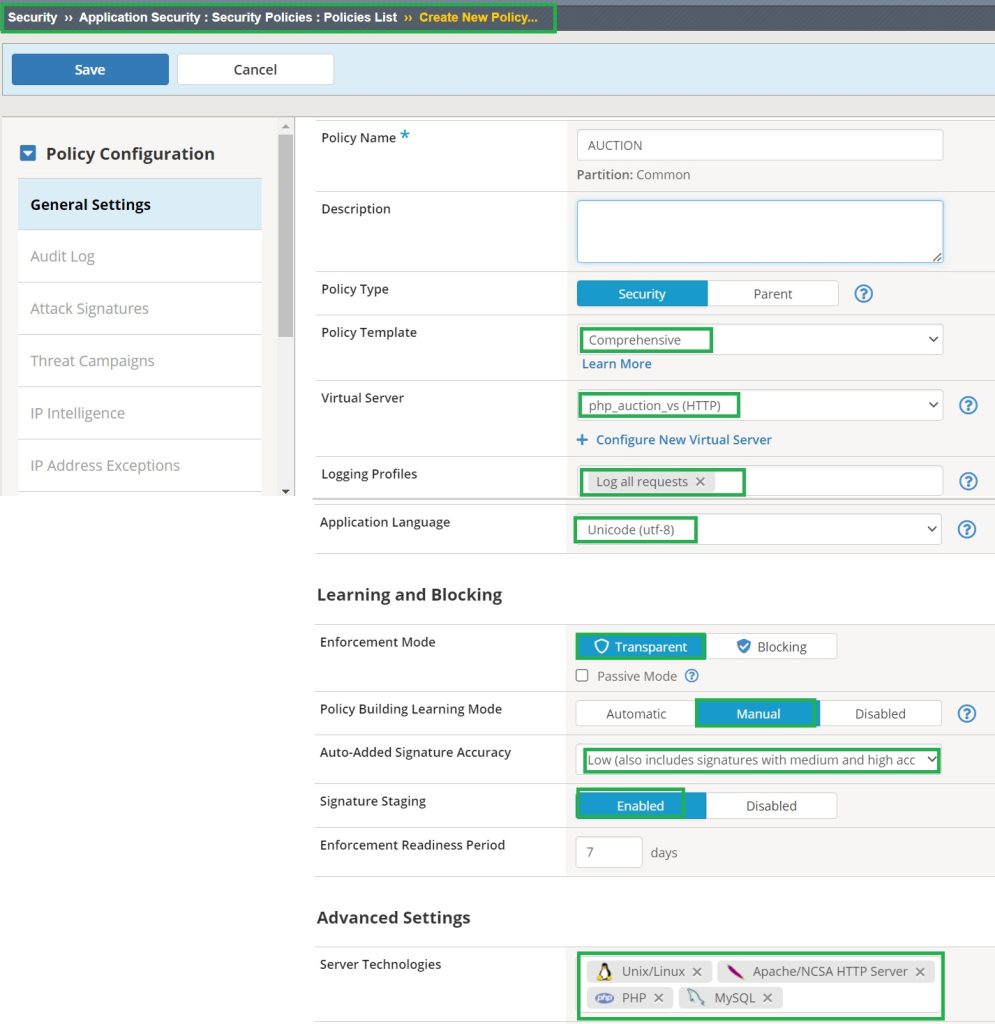
To begin the demonstration, we first create a security policy based on a “comprehensive” security template with default configuration and manual learning and assign it to the “Hack-it-yourself” web application.
In the first step, we go to the “Learning and Blocking Settings” where almost all security policy components are configured.
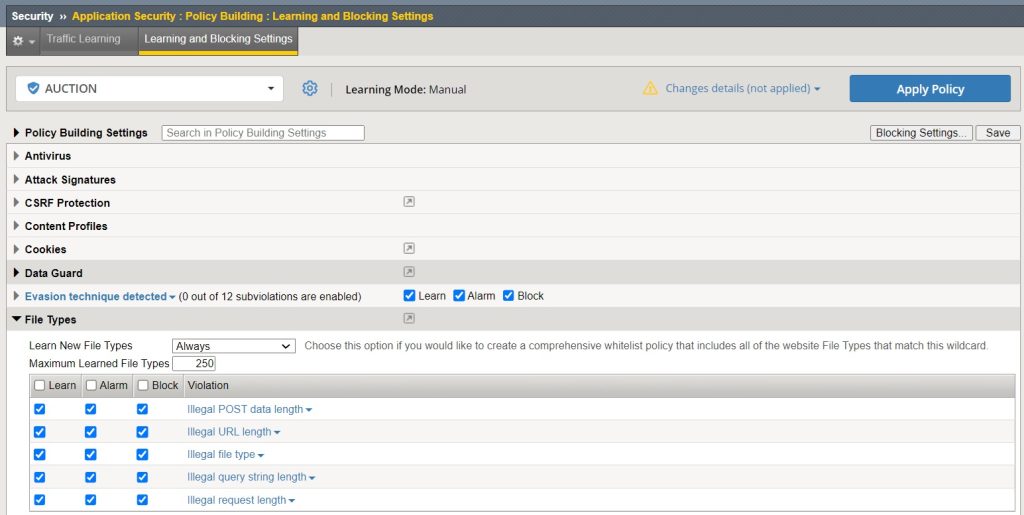
In the File Types section, the learning mode is set to ‘Always‘. This ensures that each file type associated with the web application is independently learned and governed by its own distinct security policy.
I also enable „learn“, „alarm“ and „block“ for all file type violations.
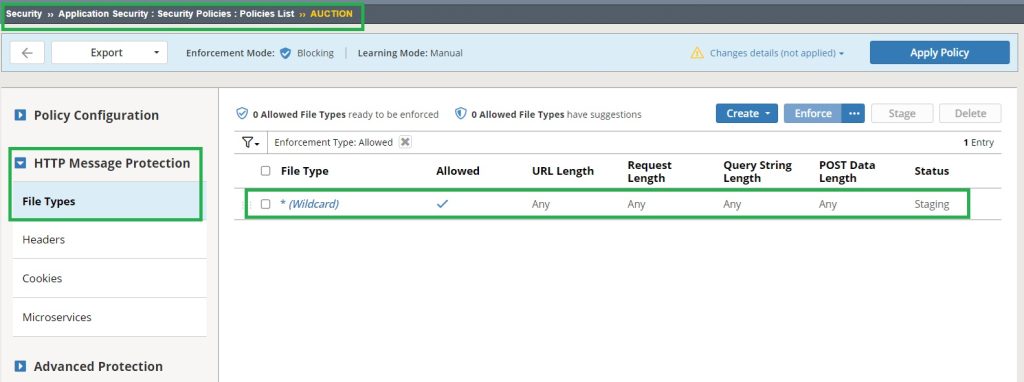
To determine which file types are allowed by default, navigate to the security policy section under ‘HTTP Message Protection‘ and select ‘File Types.’ The policy is configured to allow all file types without imposing restrictions on the ‘URL Length,’ ‘Request Length,’ ‘Query String Length,’ and ‘POST Data Length‘.
This is just a starting point for further policy customization based on the specific needs of the web application.
Now we will browse different sections of the Hack-it-yourself web application to meet different file types.
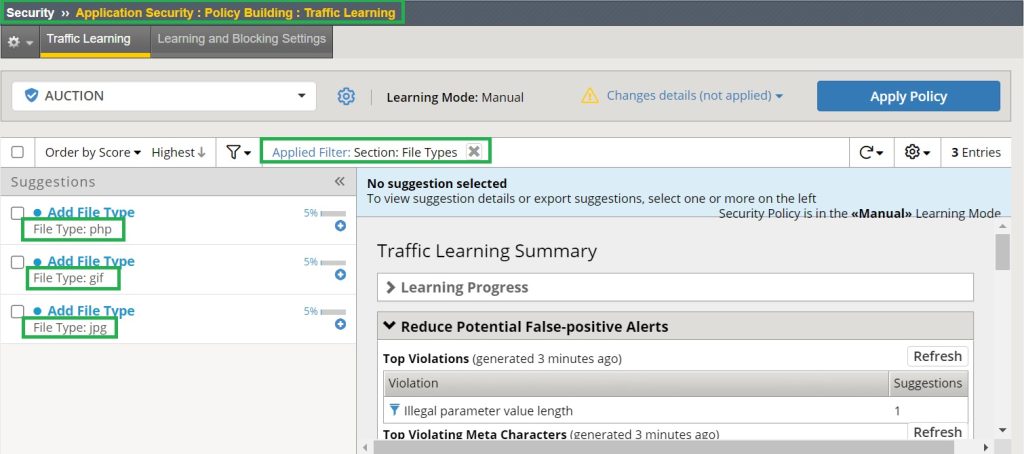
Then we check traffic learning to see what new file types are learned.
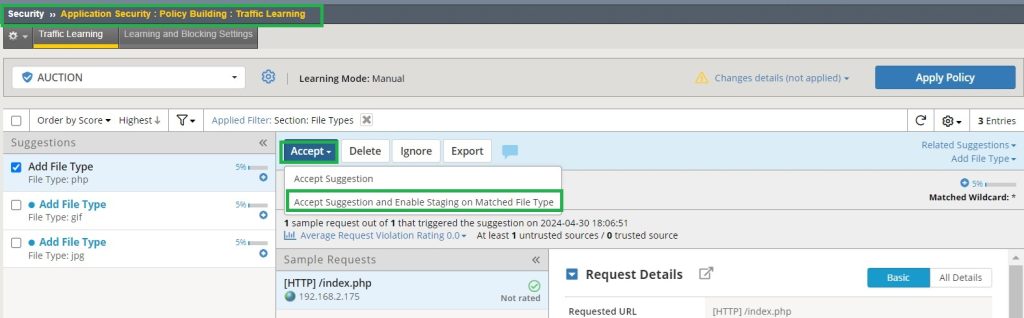
For instance, in my scenario, the file types ‘jpg‘, ‘php‘, and ‘gif‘ have been newly recognized.
If we manually accept these file types, we are accepting these file types as allowable file types in this web application. We accept and enable staging for these file types.
Staging allows traffic with properties deviating from those defined in the security policy to pass through without being rejected; instead, an alert is generated to signal the deviation.
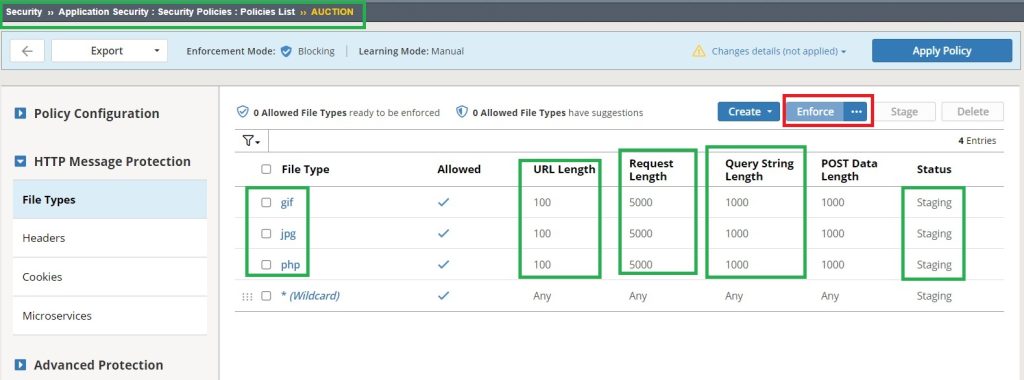
After a while we will enforce all learned file types, to guarantees that any file types not conforming to the security policy will be discarded.
It is worth noting that in practice, learning file types and various policy components is usually done automatically by F5 AWAF.
As a file type appears repeatedly over time, it gradually gains trust. Once the learning score reaches 100, indicating a high level of confidence in the file type’s legitimacy, it is then will automatically be added to the list of allowed file types.
If we check again the allowed file types in the security policy, we can see that in addition to the default asterisk (*), new file types with new properties have been added to the list. All of them are also in staging mode.
After a while, when all file types of a web application and their properties are learned, it is expected that the asterisk (*) will be deleted and all staging will be changed to enforced.
Enforce means that any deviation in the file type properties is discarded.
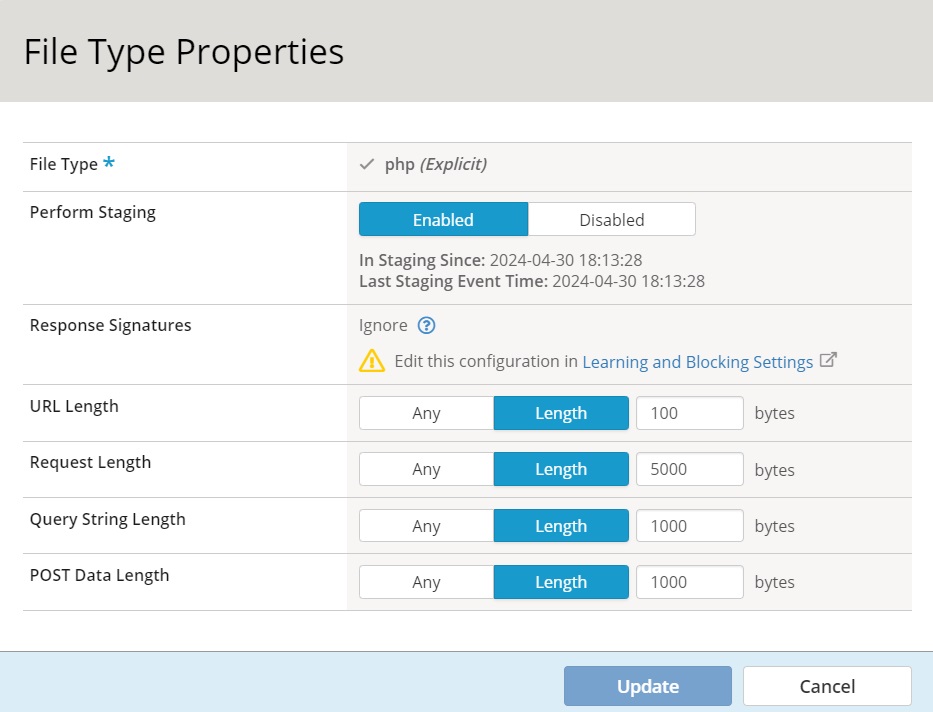
The file type properties, including “URL length”, “Request Length”, “Query String Length”, and “POST Data Length”, can be manually configured.