F5 AWAF Data Guard feature is a security mechanism designed to prevent the leakage of sensitive information such as credit card numbers or Social Security numbers. Data Guard can either block the response or mask the sensitive data with asterisks (****), depending on the configuration. That’s what we’ll demonstrate in this lesson.
F5 AWAF Data Guard
create security policy
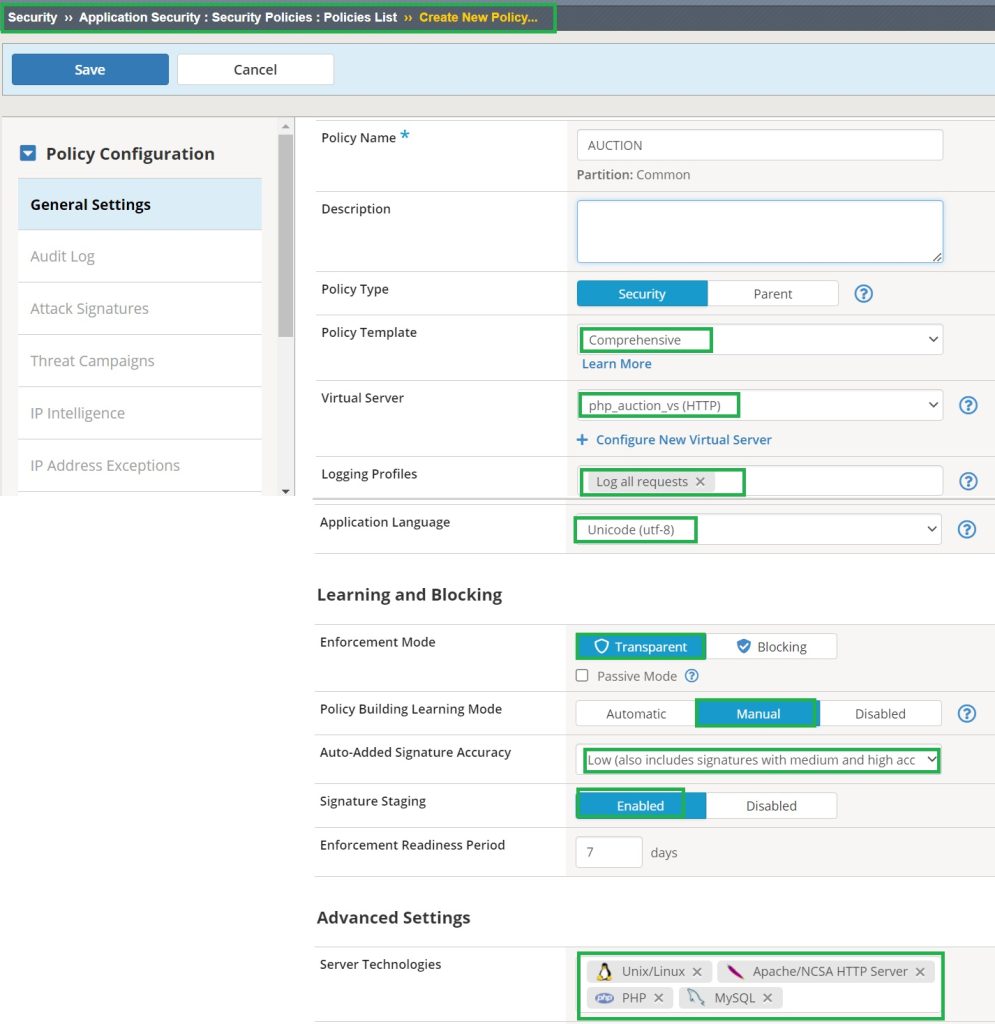
In the first step, we create a security policy based on comprehensive or other existing templates to apply to “hack-it-yourself” web applications.
To show you how to mask sensitive information, I configure the “Enforcement Mode” to “transparent“, the “Learning Mode” to “Manual” and enable “Signature Staging” to ensure that data leaks from the web application are not blocked . However, depending on your web application, you can of course block the traffic if they reveal sensitive data information.
demonstrate data leakage
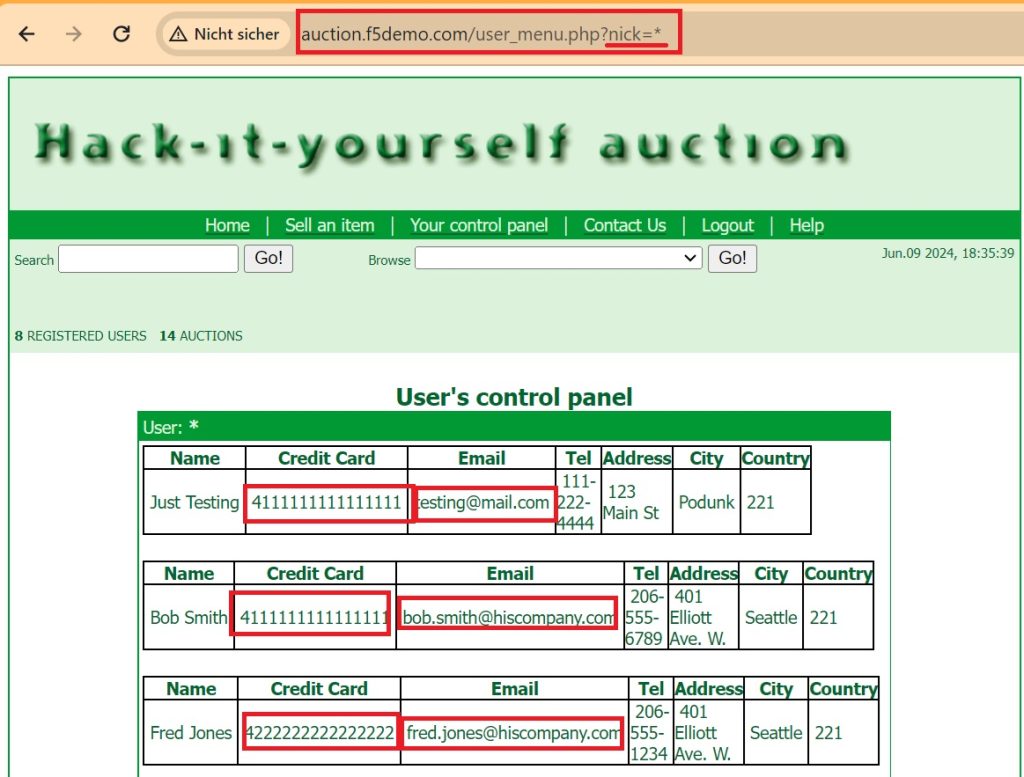
Before we implement Data Guard feature, we first examine how sensitive data can be leaked from “hack-it-yourself” web applications.
We log in with a normal user and then click on the control panel. Then in the URL, we change the value of the “nick” parameter to asterisk (*) to display credit card and email address information for all users.
enable "learn", "alarm" and "block" setting in data guard
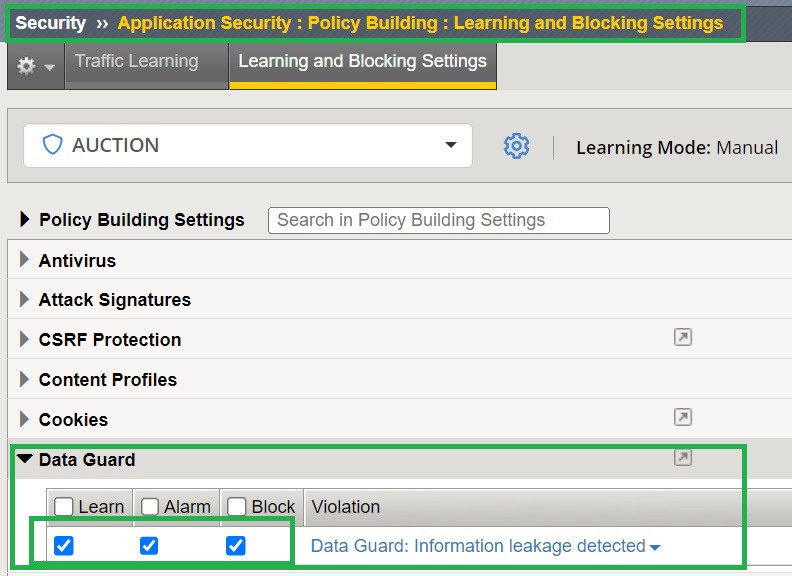
To configure the Data Guard feature, first ensure that the options „learn“, „alarm“, and „block“ are enabled in the “Learning and Blocking Settings” of the security policy.
These three options are included in almost all security parameters that you configure in the F5 AWAF module.
The “learn” option allows the system to generate learning suggestions for requests that cause violations. These suggestions can be used to refine the security policy by adding legitimate entities such as URLs, file types, or parameters that often appear in requests.
When the “alarm” option is set, the system logs the violation event.
The “Block” option allows the system to block requests that trigger violations. In addition to setting the enforcement mode to blocking in security policy and disabling signature staging, setting the block option in „learning and blocking setting“ is also required to block a violation traffic.
enable and configure data guard feature
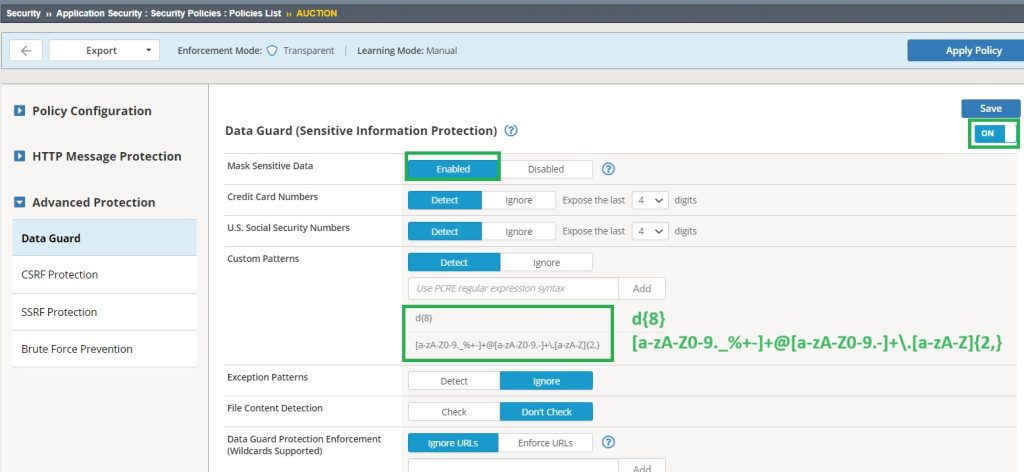
The next step is to enable and configure the data guard settings in the “Advanced Protection” section of the security policy.
By default it is disabled, we need to enable it.
When you enable it, by default, it detects and masks credit card numbers and social security numbers. However, you can use your own Perl-compatible regular expression to mask or block sensitive information.
In „hack-it-yourself“ web application, we have non-standard credit card numbers and email addresses to be protected.
I add two regular expressions. The first is for matching 8-digit numbers and the second is for matching email addresses to prevent this information from being leaked.
d{8}
[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}
Data Guard feature can also inspect file content types such as Microsoft Office documents, PDFs, or Windows portable executable files within responses, to prevent data leakage.
monitor the operation of data guard feature
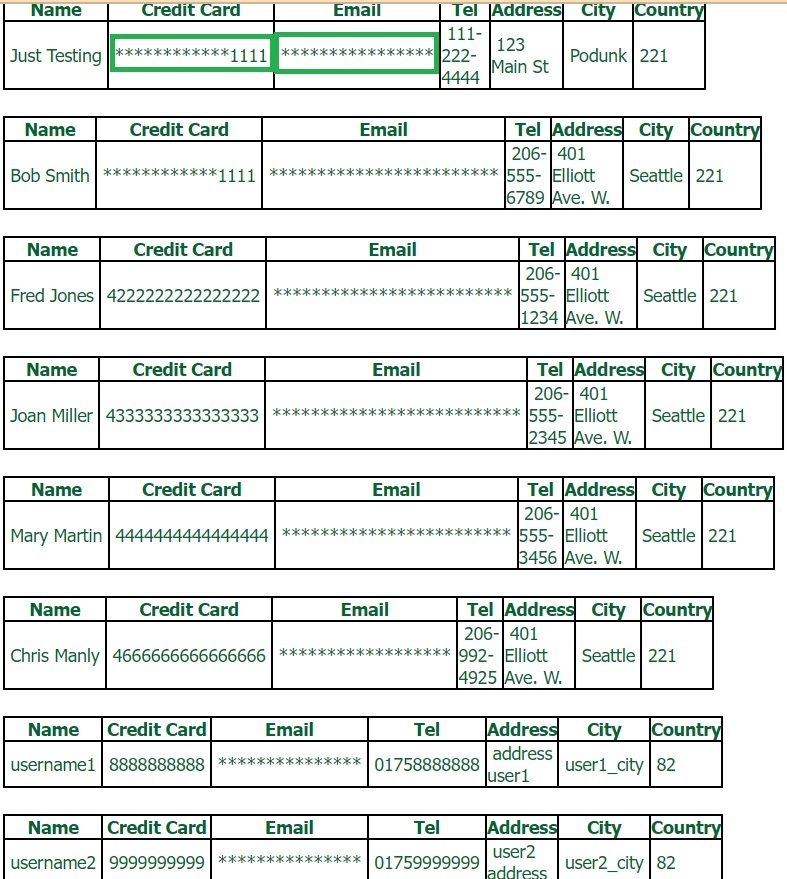
Now, let’s check the “hack-it-yourself” web application again to see whether credit card and email addresses are still being revealed.
As we can see, these information are masked with asterisks (****) and F5 AWAF protects these information from disclosure.
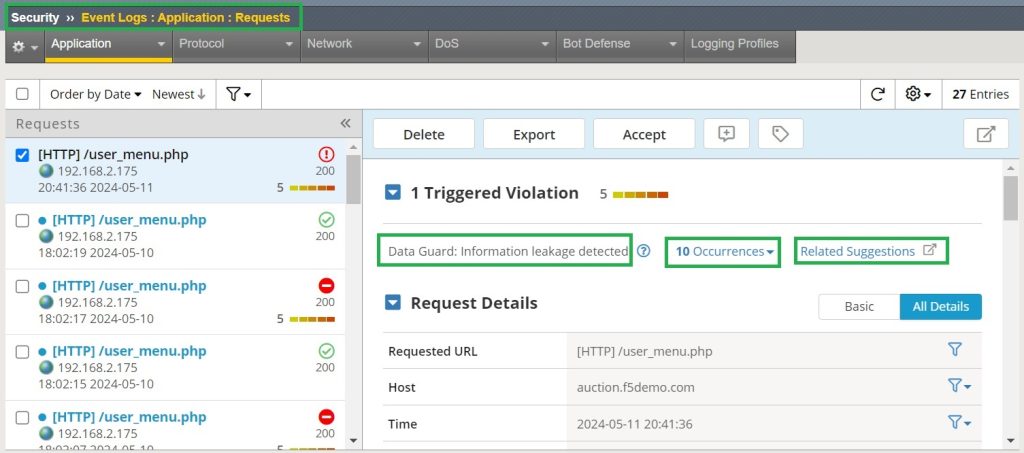
We can also review application security event logs to display data guard related alerts.
As you can see, an event log with a violation rating of 5 is created for information leaks. It also shows how many data leakage was detected.
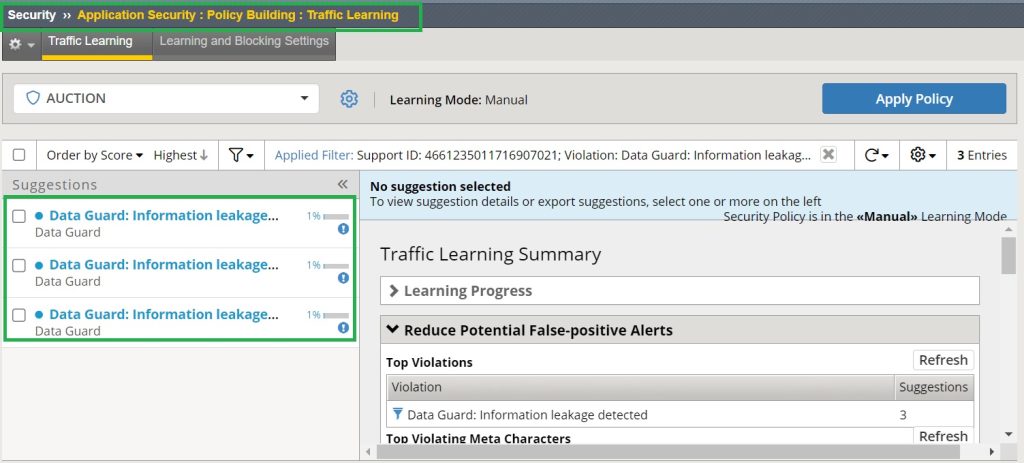
If you click on „related suggestions“ on the event log, then learning suggestions related to information leakage is displayed.
In the previous section, we have already discussed what learning suggestions are and how they can refine security policy.
May I know, the F5 AWAF Data Guard is to protect data leakage from responses if attacker tries to read the sensitive information from the responses. Will it also mask the sensitive data that needs to be displayed in the application?
yes, if the policy is configured properly