F5 AWAF automatic learning and policy building is a feature that identifies legitimate and malicious traffic automatically, using this information to dynamically create and adjust security policies. This is what will discuss and demonstrate in this section.
Automatic Policy Building Learning Mode
Automatic Learning and Policy Building in F5 AWAF
Throughout the course, we have always manually added new policies. Whenever a violation occurred, F5 AWAF provided a new learning suggestion. If the violation was a false positive, we accepted the learning suggestion to classify the traffic as legitimate and update the security policy accordingly.
Now the fundamental question is: How does F5 AWAF identify legitimate and malicious traffic automatically? To have a theoretical answer, each new traffic component is assigned a learning score and is considered legitimate when the learning score reaches 100, as we have discussed in Lesson 8.
Conceptually, for each traffic component, such as URL, File type, and Parameter, the learning score increases when more traffic appears from different sources and at different times. Alternatively, the score is immediately set to 100 if the traffic comes from a configured trusted source.
With automatic learning, legitimate traffic is not only identified and added to the security policy, but over time, as the volume of a specific type of traffic increases, it will transition out of stage mode and will be enforced.
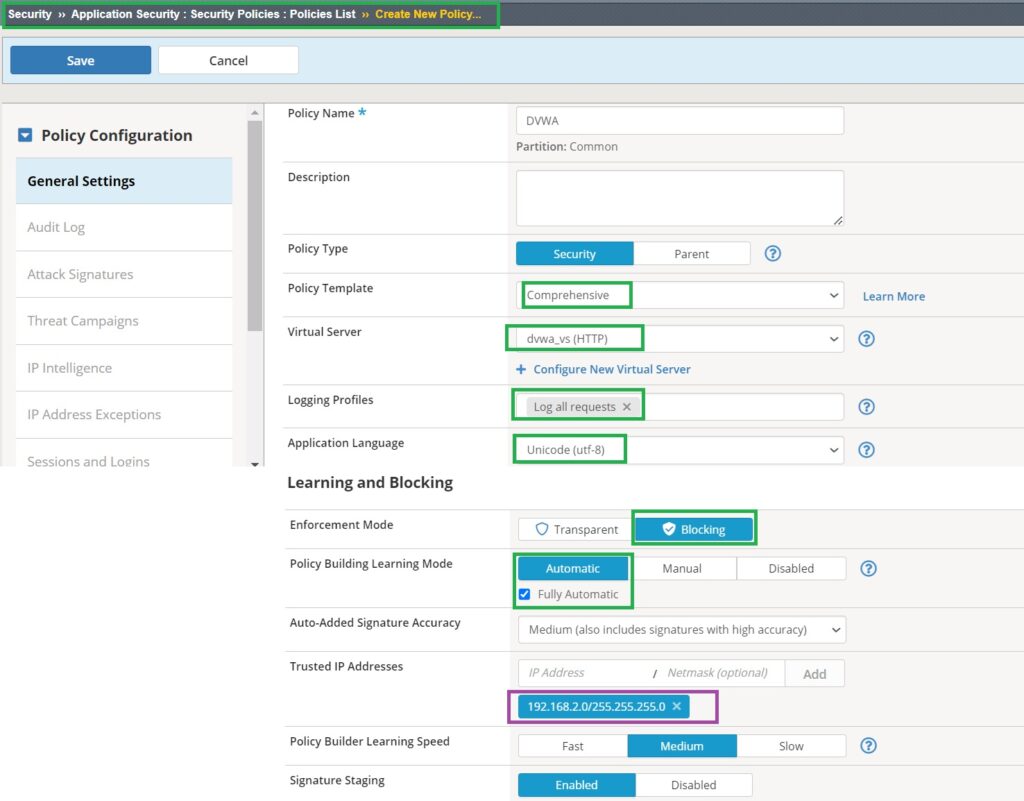
create Security Policy with Trusted IP address subnet
To start the demonstration, we will create a new security policy based on the comprehensive security policy template, set the “Enforcement Mode” to “Blocking,” and set the “Policy Building Learning Mode” to “Fully Automatic“.
The difference between Automatic and Fully Automatic modes in policy building learning is that in Automatic mode, some critical policy changes still require manual review and approval, such as those related to login credentials, session identifiers, or financial data. For this demonstration, we will choose the Fully Automatic option.
Another important configuration in the security policy is to designate the client IP address subnet as a trusted IP address range. Traffic from trusted IP addresses will immediately receive a learning score of 100, ensuring it is automatically accepted and added to the security policy. You can later modify trusted IP addresses and their properties in the section “Security Policy > General Settings > IP Address Exceptions”.
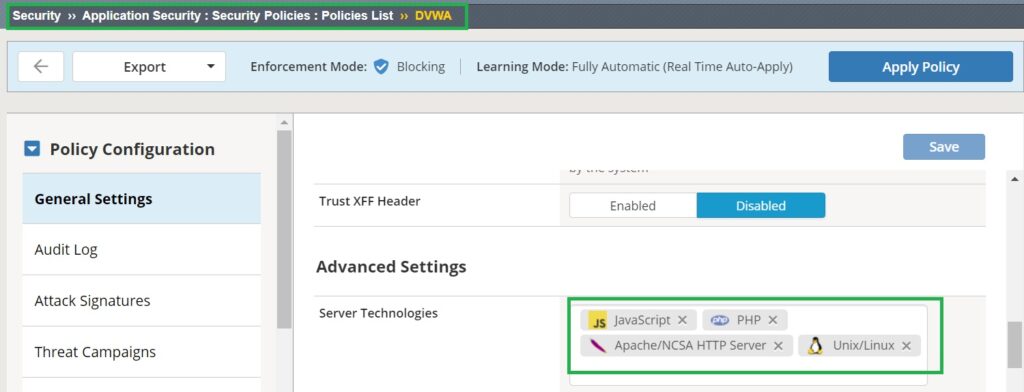
Another point is that, unlike previous policies, we do not configure server technologies manually, as these will be learned automatically.
Finally, we apply the new policy to the virtual server associated with the DVWA web application.
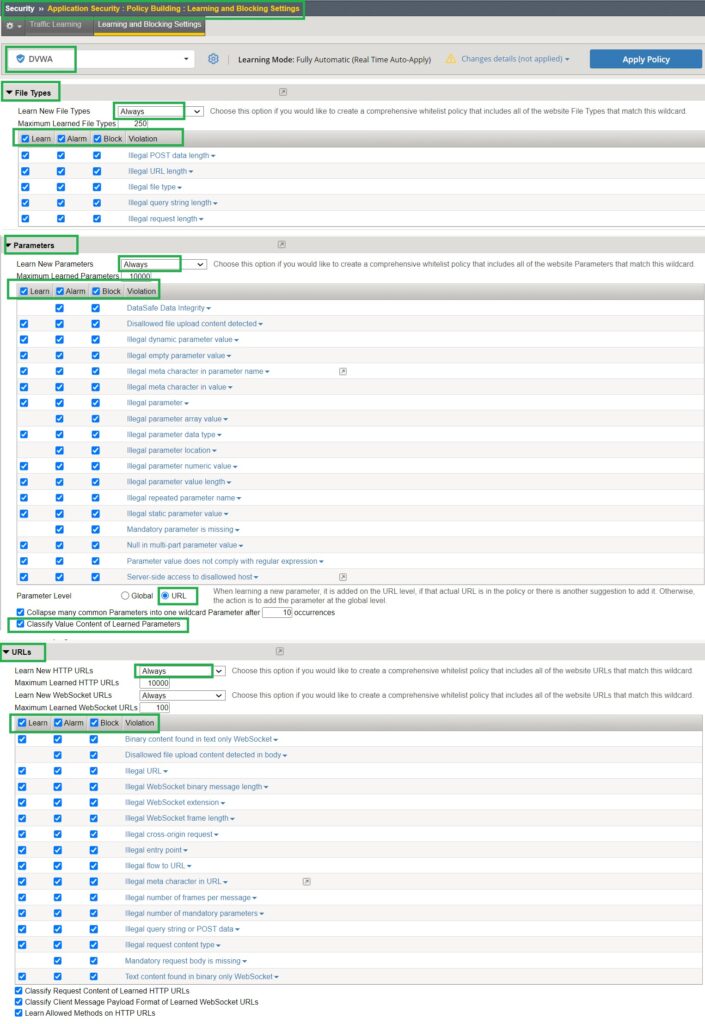
Configure Automatic Learning and Policy Building Parameters
In the Learning and Blocking Settings section, we configure the learning modes for ‘File Types‘, ‘Parameters‘, and ‘URLs‘ to ‘Always‘. We also enable ‘Learn,’ ‘Alarm,’ and ‘Block‘ for all violations to ensure that all critical traffic components are individually learned and added to security policy.
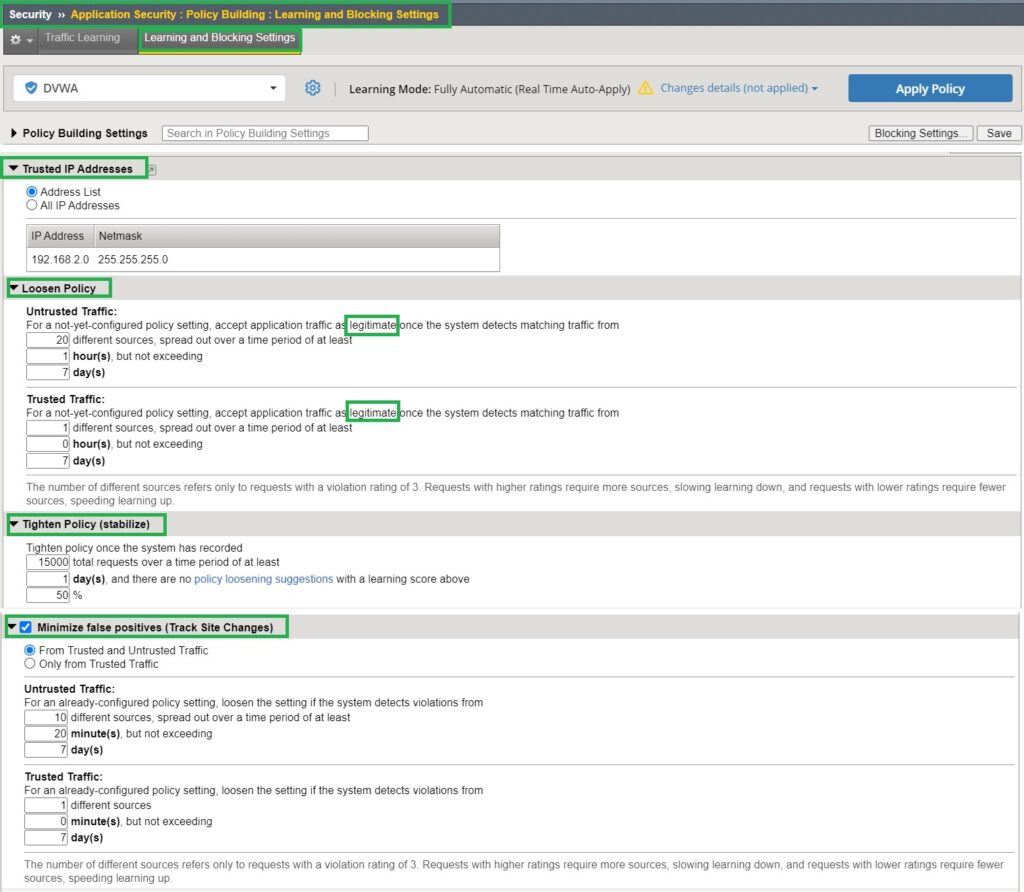
At the bottom of the ‘Learning and Blocking Settings’ page, you will find the ‘Trusted IP Address‘ section, where you can view the list of IP address subnets configured in your security policy.
Below this, there are three options: ‘Loosen Policy‘, ‘Tighten Policy (Stabilize)‘, and ‘Minimize False Positives (Track Site Changes)‘. These options allow you to adjust the parameters that control how the automatic policy-building learning mode works.
The option ‘Loosen Policy‘ determines how new traffic components are accepted and added into the security policy. It specifies the conditions under which a traffic component, such as a URL, file type, or parameter, is recognized as legitimate.
Specifically, it dictates the number of instances of a traffic component from trusted or untrusted clients within a given time range that must occur before the component is added to the security policy.
The option ‘Tighten Policy (Stabilize)‘ refers to the process of changing a newly automated security policy from staging to enforced mode. This occurs when a significant number of instances of a traffic component are observed, with only minimal security updates or changes required. This indicates that the policy is stable enough to be finalized and enforced.
And finally the option ‘Minimize False Positives (Track Site Changes)‘ option means that F5 AWAF continuously monitors and updates finalized security components to address false positives.
When many instances of a traffic component over a time range violate the current finalized security policy, it suggests that the policy may need to be adjusted to better accommodate legitimate traffic and reduce false positives.
I will leave all these values as they are since they seem to be logical for real network traffic.
Test Automatic Learning and policy Building
Next, we will generate traffic with new URLs, file types, and parameters.
To do this, I will log into the DVWA web application, reset the database, and set the security level to ‘Low.’
Afterward, I will navigate through various pages and input values, for example in the ‘SQL Injection’ and ‘XSS (Reflected)’ sections.
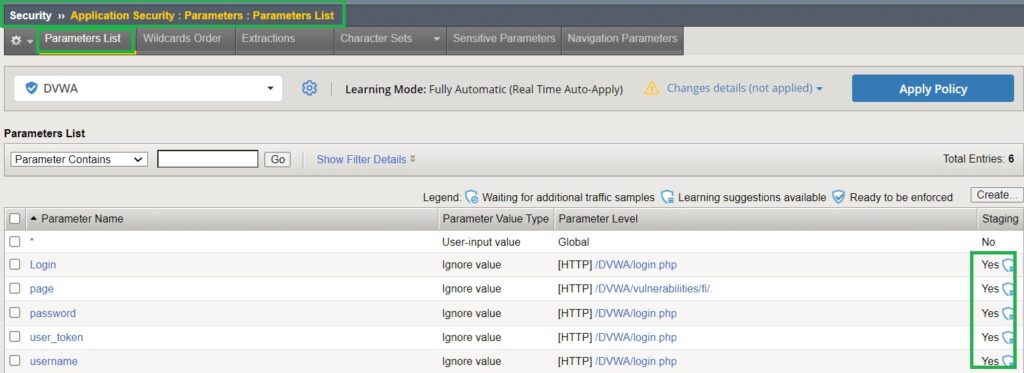
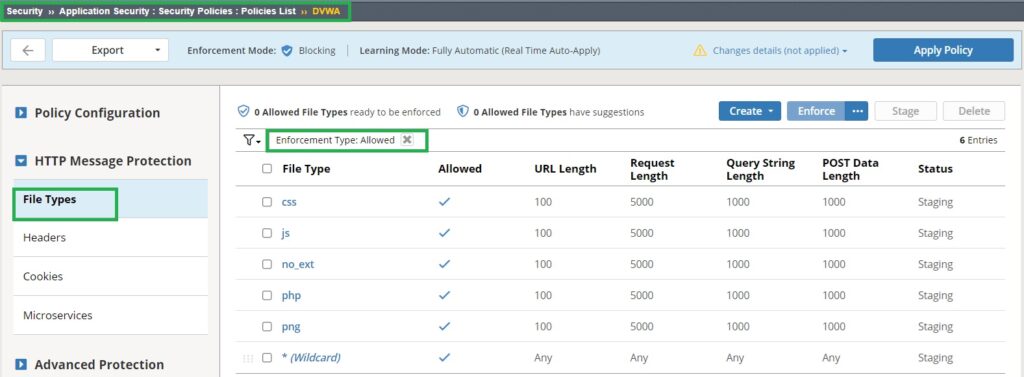
Next, we need to verify if new traffic components, URL list, parameters and file types, have been learned.
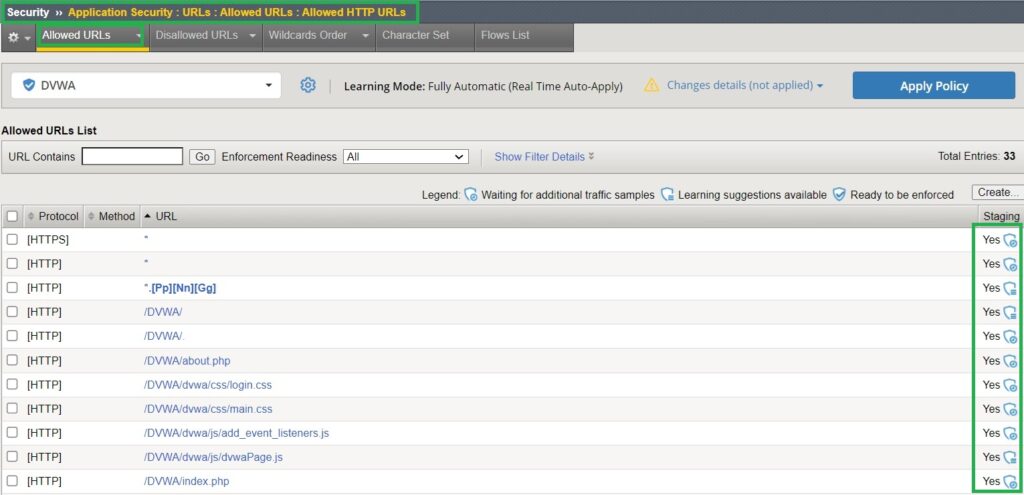
Check New URLs:
Navigate to Security > Application Security > URLs > Allowed URLs: Allowed HTTP URLs to view the list of new URLs that have been automatically learned and added to the security policy by F5 AWAF.
Check New Parameters:
Go to Security > Application Security > Parameters: Parameters List to see the new parameters that have been automatically learned and added to the security policy.
Check New File Types:
In Security > Application Security > Security Policies: Policies List > DVWA > HTTP Message Protection > File Types, review the list of new file types used in the web application that have been automatically learned and added to the security policy.
Check Server Technologies:
Visit Security > Application Security > Security Policies: Policies List > DVWA > General Settings > Server Technologies to see the server technologies used in the web application that have been automatically learned and added to the security policy.
Verify Audit Log:
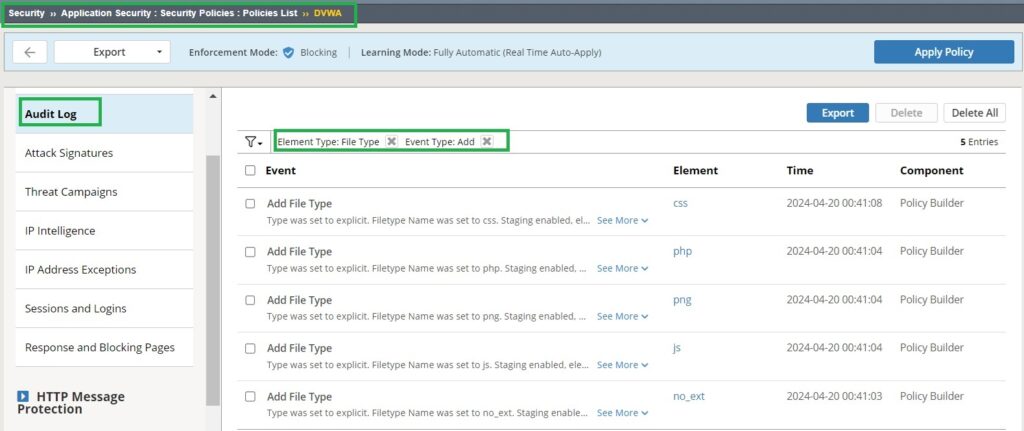
Check the Audit Log in Security > Application Security > Security Policies: Policies List > DVWA > General Settings to review how new components are added to the security policy. Filter the log based on Event Type set to Add and Element Type set to File Type to see each time when a new file type is added to the security policy.
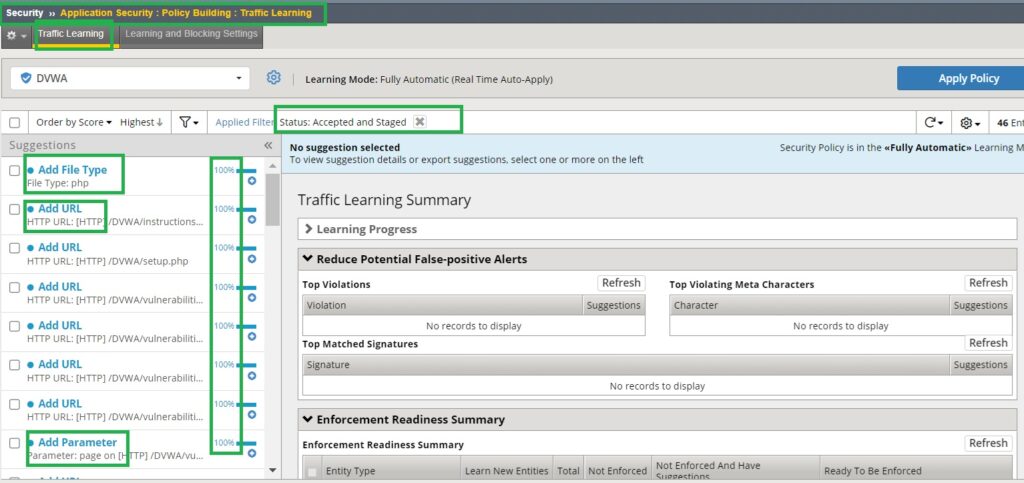
In the ‘Traffic Learning‘ section under ‘Security > Application Security > Policy Building‘, filter by the status ‘Accepted and Staged.’ You will notice that many traffic components are accepted because their learning scores have reached 100.