DNSSEC helps to secure the domain name resolution process, ensuring its authenticity and protecting against malicious activities like cache poisoning and spoofing attacks. In this section, we will explore the theoretical concepts and hierarchical structure of DNSSEC to understand DNSSEC fundamental and how it works.
DNSSEC Terminologies and Process
DNSSEC and Digital Signature
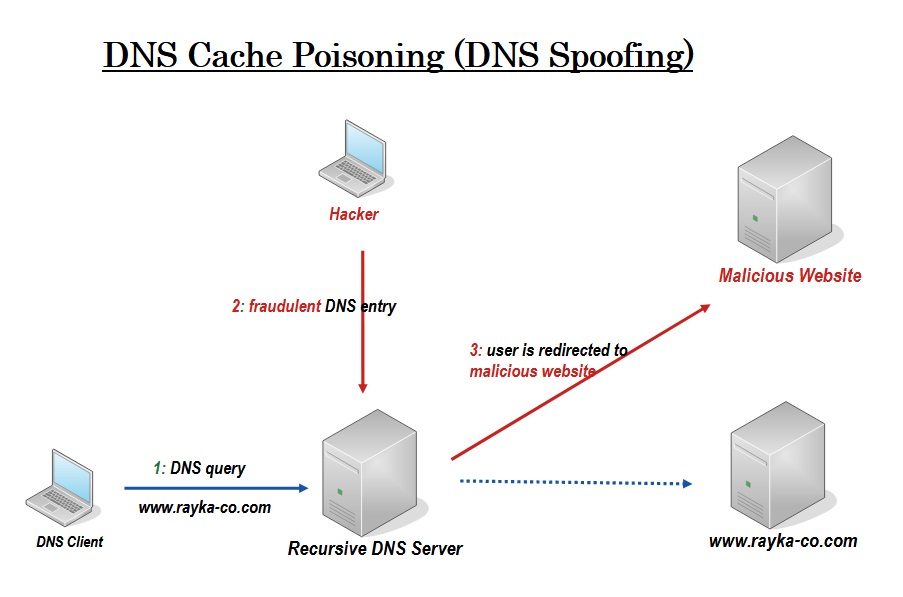
By default, the DNS protocol does not provide security.
This lack of security means that DNS responses cannot be authenticated. In other words, we are not sure about their origin and whether the response is legitimate or fake.
Therefore, without DNSSEC, users could be redirected to malicious websites, exposing them to various cyber threats such as cache poisoning and spoofing.
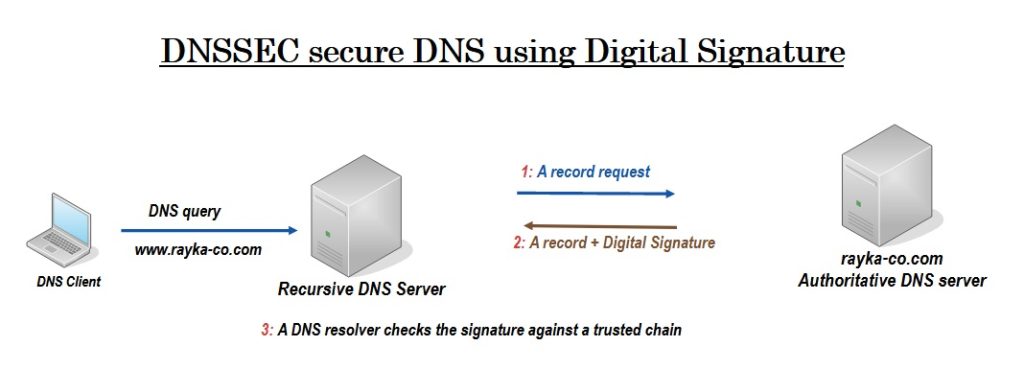
DNSSEC secures DNS replies by attaching a digital signature. When a DNS resolver gets a DNS reply, it checks this signature against a trusted chain. If the signature is verified, it confirms the reply is exactly as sent by the original source, with no alterations along the way.
Digital Signature Fundamental
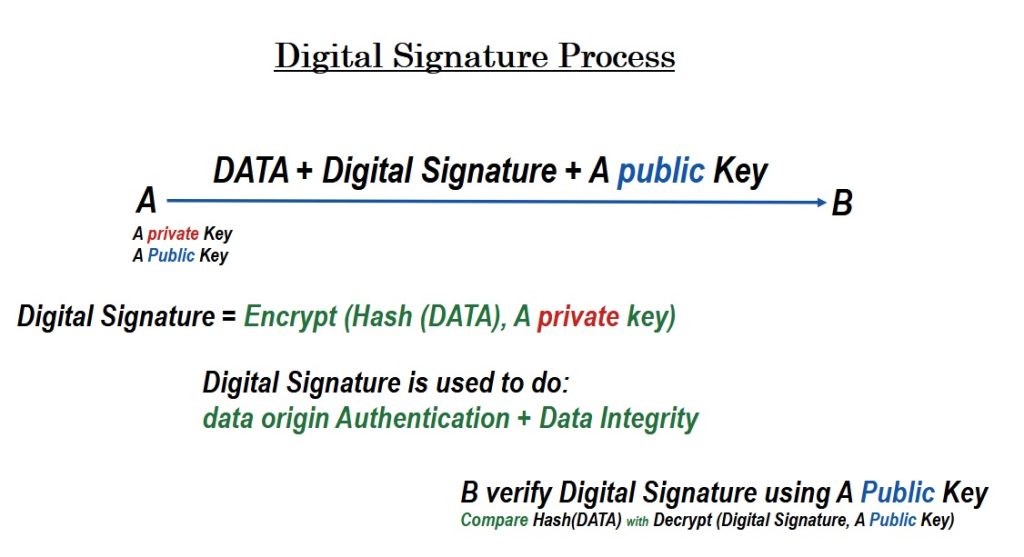
How does the digital signature work?
In the digital signature process, each party has two keys, a private key to sign the data and a public key that the other party uses to verify the signature.
The private key must be protected and secured, but the public key is sent to the other party for signature verification.
The digital signature is generated using an encrypted hash of the data using the sender’s private key.
The digital signature is verified by decrypting the digital signature using the sender’s public key and comparing it with the hash of the data. If they are identical, the authenticity of the data is confirmed.
DNSSEC terminologies
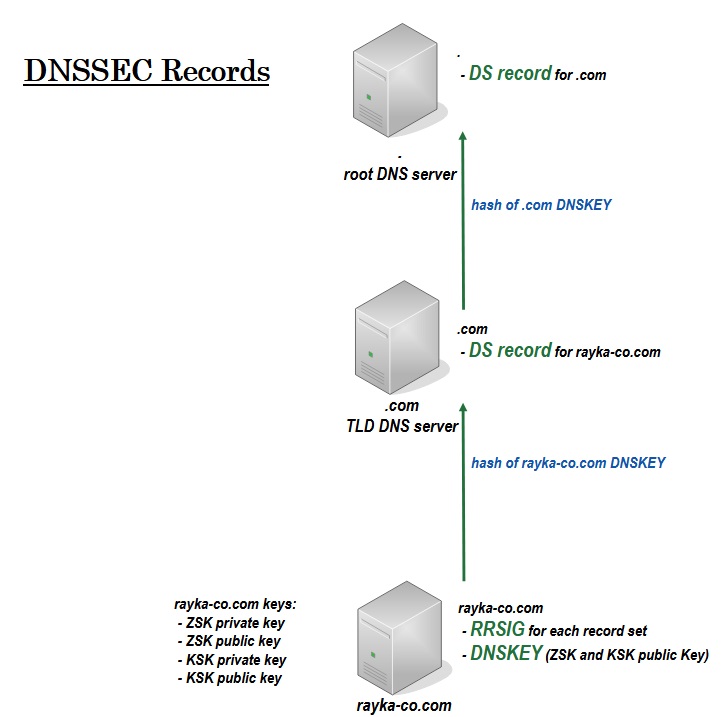
When you enable DNSSEC, some new entries are added to the DNS zone in the DNS hierarchy.
- RRSIG record containing the signature of records of the same type.
DNSKEY record that stores the public key. Typically there are two per zone, Zone Signature Key (ZSK) and the Key Signature Key (KSK).
The ZSK private key is used to sign the DNS records and store them as RRSIG record. The KSK private key is used to sign the ZSK public key to ensure that the ZSK has not been compromised. The ZSK signature result is stored in RRSIG for DNSKEY record.
DS record is in the parent zone and contains a hash of the DNSKEY from the child zone that contains the KSK.
When receiving and trusting the KSK public key from the parent zone, the ZSK public key in the child zone is verified. The trusted ZSK public key is then used to verify the DNS response signature.
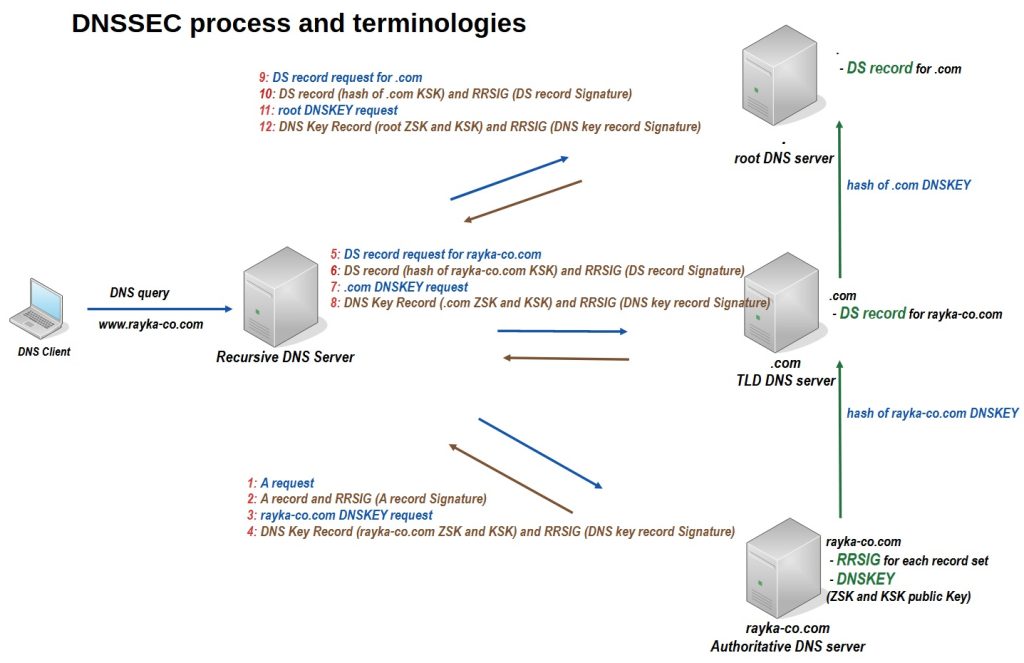
how DNSSEC works?
Now it’s time to learn how exactly DNSSEC works.
The user requests the local DNS server to resolve the name www.rayka-co.com. The local DNS server traverses the DNS hierarchy to find the authoritative DNS server. We assume that DNSSEC is already implemented in the DNS hierarchy of the rayka-co.com zone.
1. The local DNS server requests an A record for the name www.rayka-co.com from the authoritative DNS server.
2. The authoritative DNS server sends an A record and its signature using RRSIG.
3. The local DNS server then sends a DNSKEY record request to the authoritative DNS server to verify the signature.
4. The authoritative DNS server responds with the DNSKEY record containing the ZSK and KSK public keys and the DNSKEY signature.
5. The local DNS server then ask .com TLD DNS Server for the DS record for rayka-co.com. This is to make sure that rayka-co.com ZSK public key is not compromised.
6. The .com TLS DNS server responds with rayka-co.com DS record and corresponding RRSIG DS record.
7. Then the Local DNS server requests the DNSKEY record from the .com DNS server to verify the signature.
8. The .com DNS server responds with the DNSKEY record and corresponding RRSIG DNSKEY record.
9. Then the local DNS server requests the DS record of .com from the root servers.
10. The root DNS servers return the DS record and corresponding RRSIG DS record for .com.
11. Then the local DNS server requests for the root DNSKEY record.
12. The root DNS server returns the DNSKEY record and the corresponding RRSIG DNSKEY record.
13. Finally, the local DNS server validate the DNSKEY record and corresponding RRSIG DNSKEY record for root.
With validating and trusting DNS hierarchy, local DNS server will authenticate DNS reply.
Resource: