Cisco FTD URL Filtering feature gives the capability to control the websites that users on your network can access based on category, reputation, and also manual..
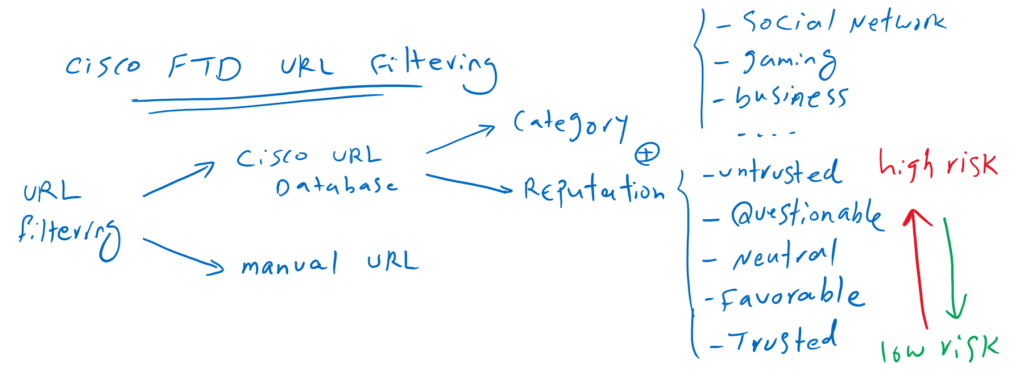
Cisco FTD URL Filtering Concept
Websites can be filtered based on category, reputation, combination of category and reputation and also manual URLs.
Social Networking, Gaming, Drugs and Business are some of these categories. Reputations are from trusted websites to untrusted and high-risk websites that come in each category.
If you allow a reputation level, all level below that will be also allowed. Similarly, if you block a reputation level, all above levels will be also blocked.
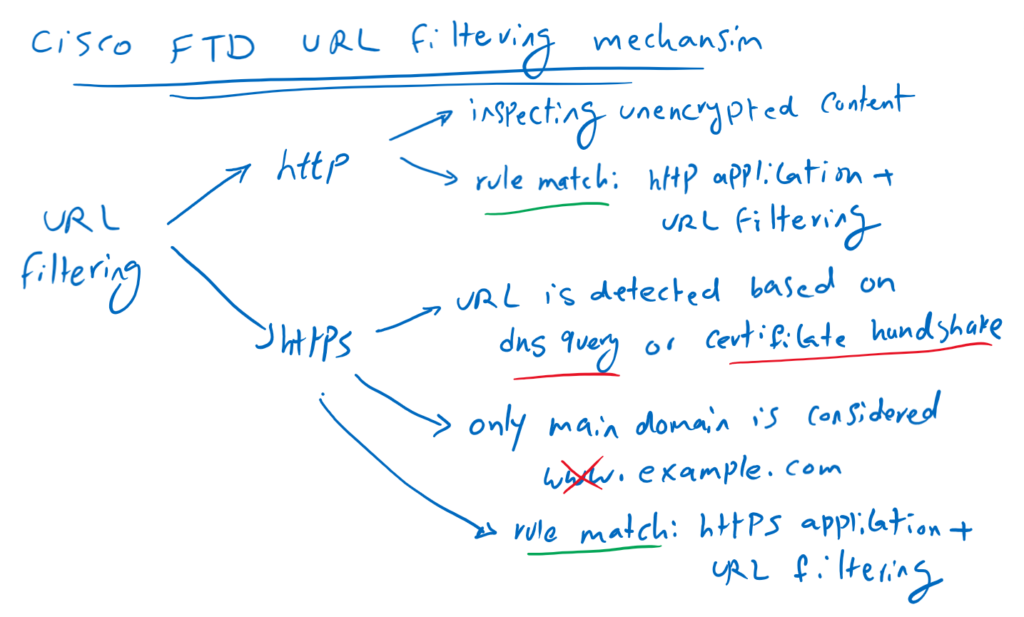
How URL Filtering Works in Cisco FTD
For HTTP traffic, that is easy to control traffic based on URL since the content of HTTP application header can be unencrypted and clear text.
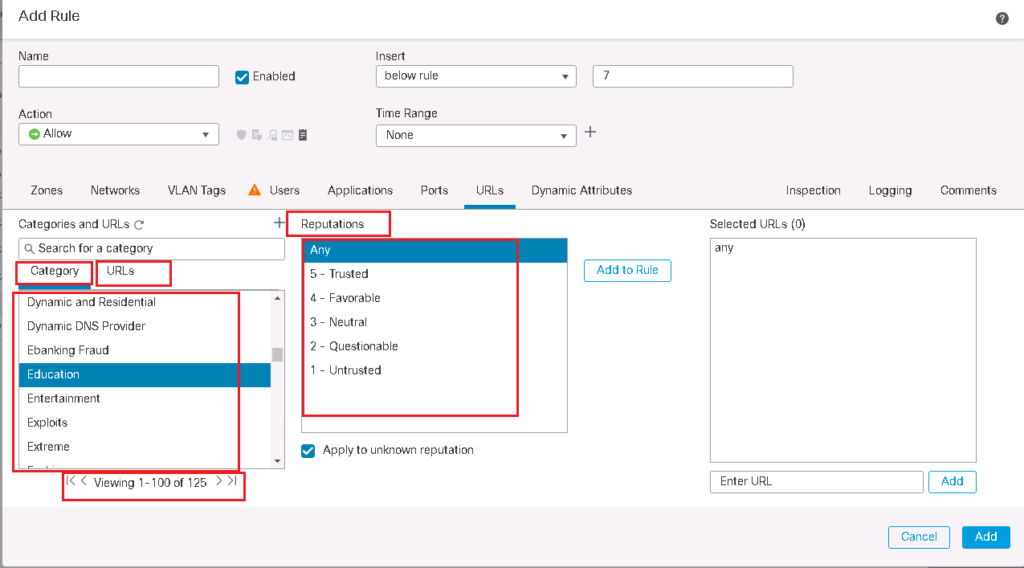
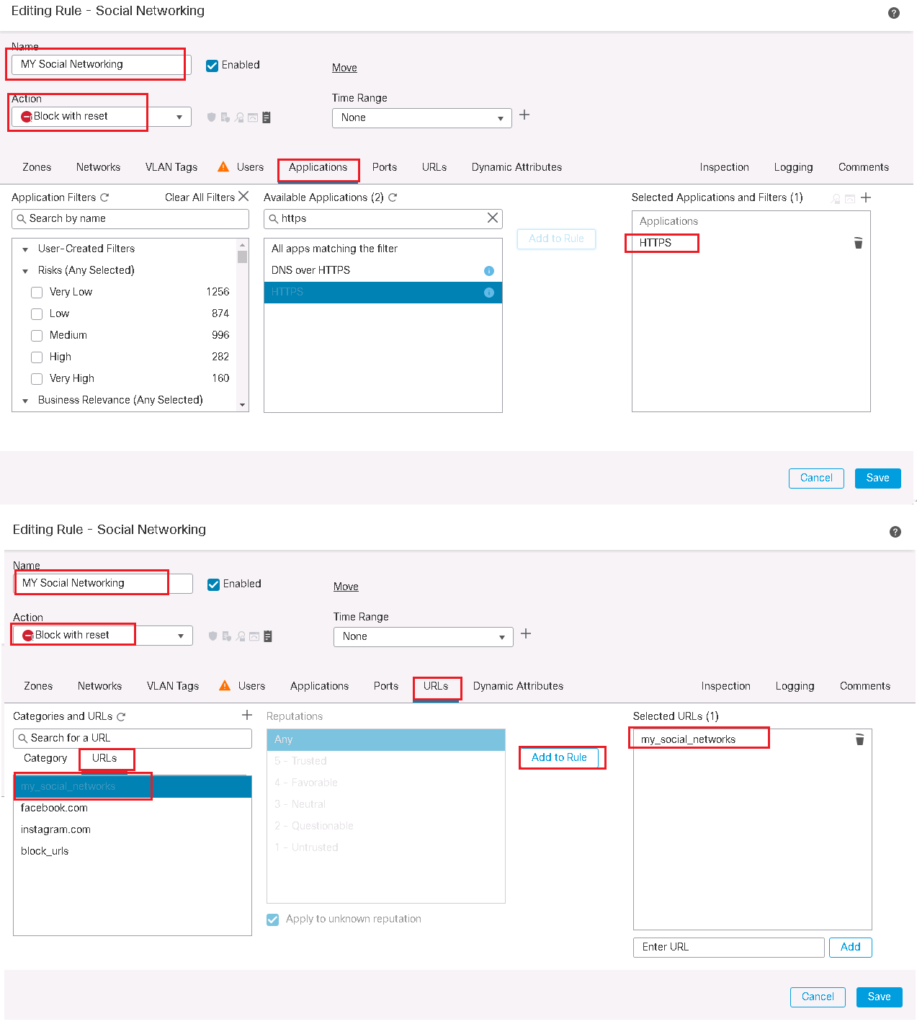
To configure a rule for HTTP URL filtering, select the HTTP protocol on the “Applications” tab and the URL on “URLs” tab.
But for HTTPS traffic it is more difficult because the application header is encrypted and without SSL decryption policy it is not possible to read the content of application header.
For HTTPS traffic, the URL is detected based on DNS query or Certificate handshake in HTTPS negotiation.
With HTTPS URL filtering, only the main domain can be filtered, and subdomains and wildcards are not supported. For example, if you configure “www.example.com” as the URL in URL filtering, only the main domain “example.com” is considered and “www” cannot be checked.
To configure a rule for HTTPS URL filtering, select the HTTPS protocol on the “Applications” tab and the URL on “URLs” tab. If you do not specify HTTPS as protocol and only configure URLs in URL tab then DNS query will also be checked for URL filtering.
Cisco FTD URL Filtering Configuration
URL filtering through existing cisco categories and reputation
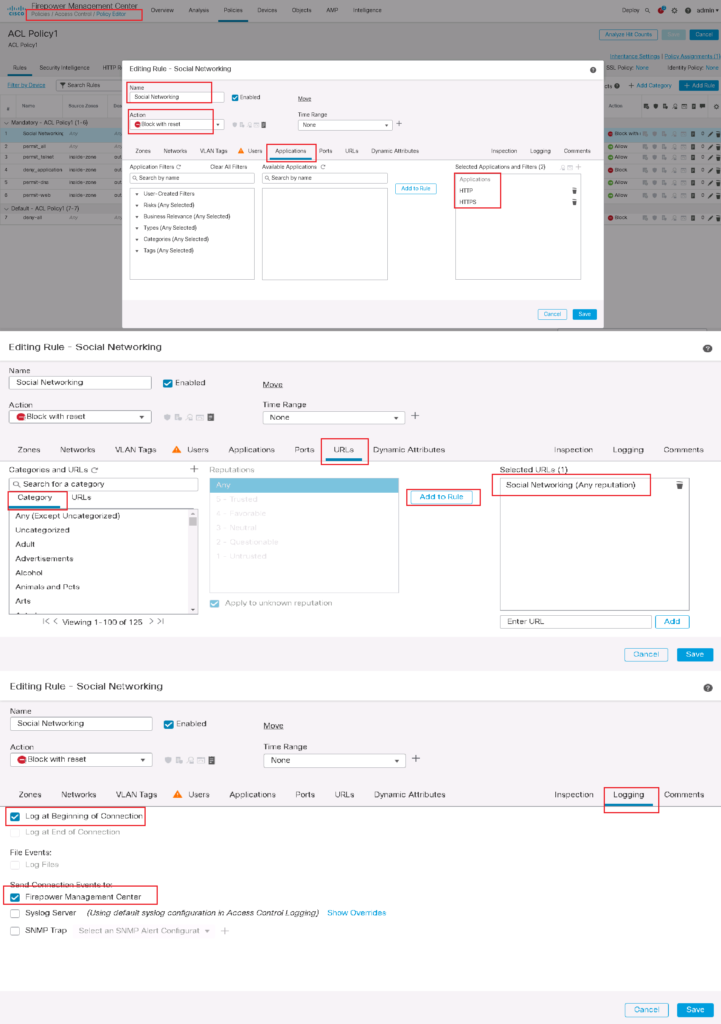
for the first scenario, we filter Social Networking websites of any reputation based on cisco URL category.
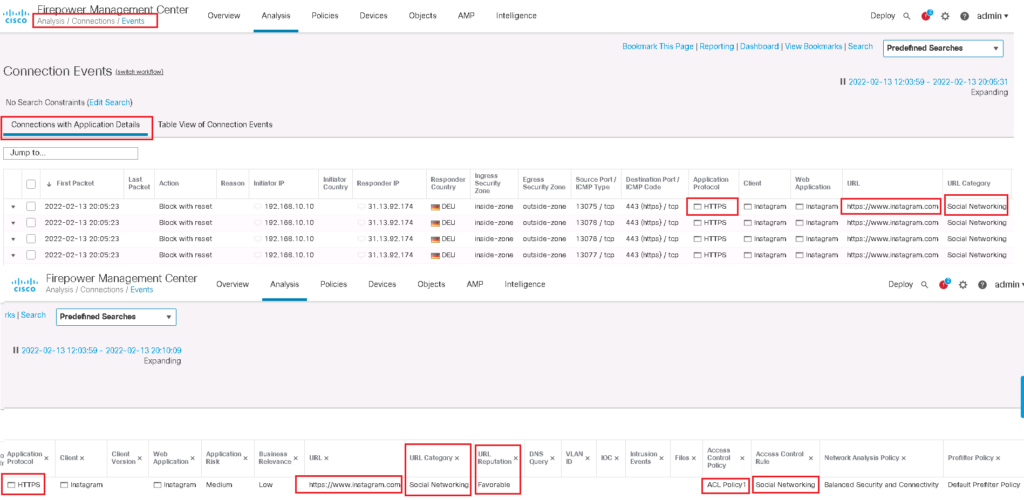
To configure the rule, we choose HTTP and HTTPS protocol in “Applications” tab and “Social Networking” URL category in “URLs” tab. We also enable logging so we can monitor Social Networking hit events.
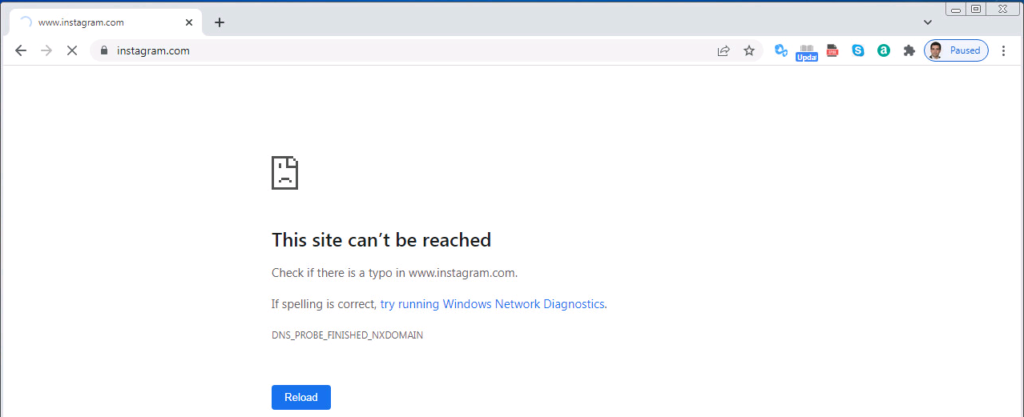
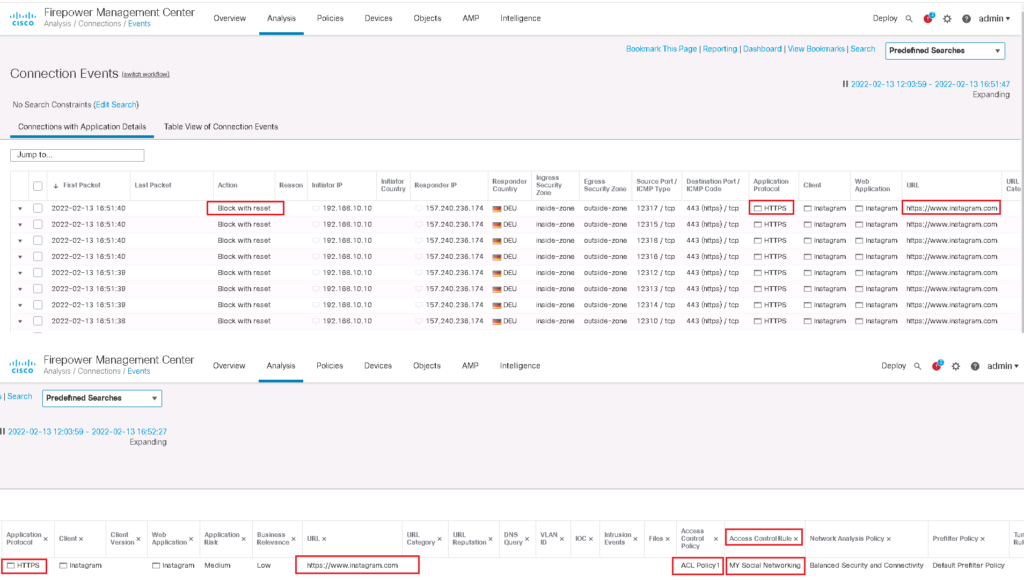
Then we check the connectivity with Instagram website through a computer behind cisco FTD. We expect that the computer is not able to browse “instagram.com”.
We can also approve that the traffic is matched with the configured URL access control role through connection event monitoring.
Manual URL Filtering
For the second scenario, we implement URL filtering through URL objects that is manually created.
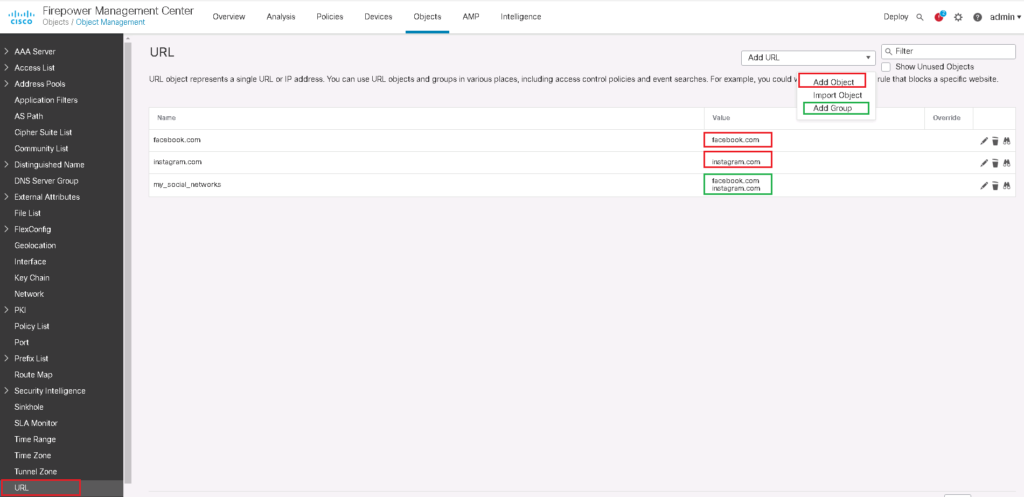
In “Objects -> Object Management -> URL”, we create a specific URL with “Add Object”. We create an object for “facebook.com” and an object for “instagram.com”. with “Add Group”, we can create our own categories. Here we create a category with the name of “my_social_networks”, that will contain both of the above objects.
These objects will be shown in URL tab in access control rule.
Then we change our previous rule to filter only websites inside our own category.
Then we test the connectivity and then monitor connection events to make sure if traffic is matched with our new access control rule.