Cisco FTD Threat Intelligence Director (TID) is a supplemental security intelligence solution to block IPs, URLs, and domains with bad reputations based on third-party sources and not just based on a specific source from a specific vendor.
what is Cisco FTD Threat Intelligence?
How threat information from third-party sources can be defined and exchanged in a standard way?
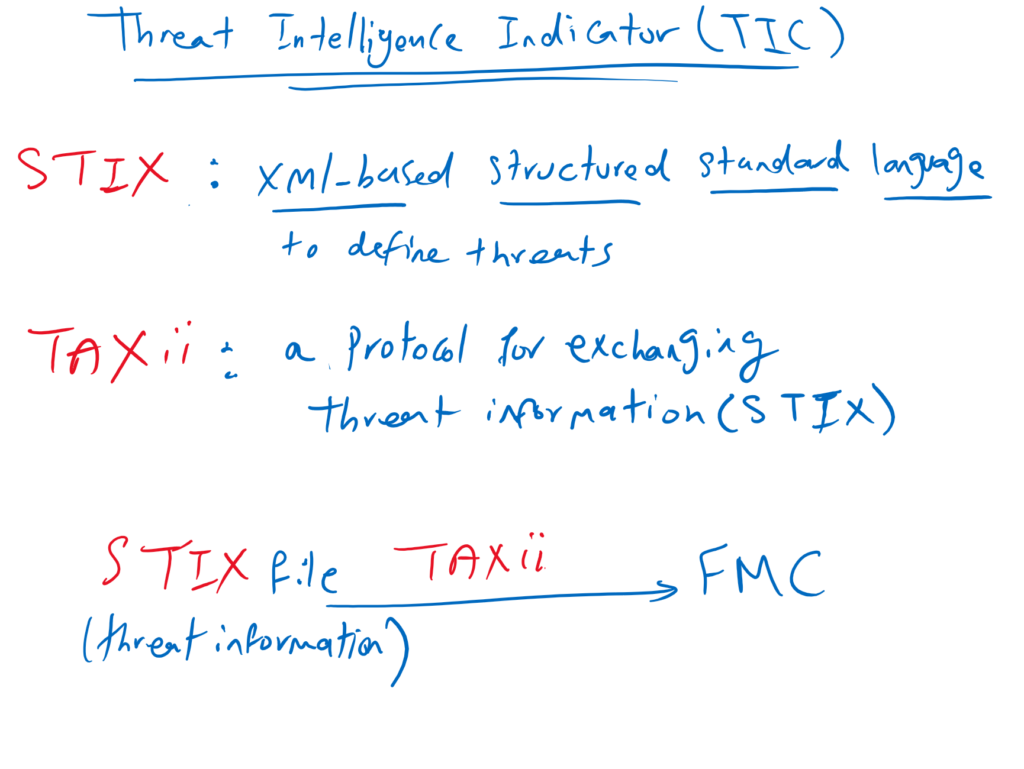
STIX is a XML-based structured language for defining threat information. TAXii is a protocol for exchanging cyber threat information. in other words we can manually upload STIX threat information into FMC or get it dynamically through TAXii protocol.
How Threats are stored in STIX files?
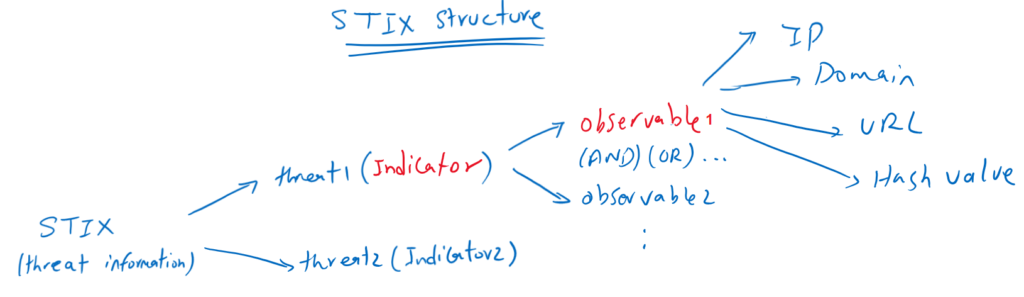
Each threat is identified by an indicator which is logical combination of one or more observables. Each observable is a single IP, Domain, URL or hash value in which FTD looks inside traffic
In other words, indicator include information regarding all of the characteristics associated with a threat which are combination of IP,URL, Domain and hash values.
An indicator can be simple indicator. Simple indicators contain a single observable, and complex indicators contain two or more observables.
How threat intelligence works in cisco FTD?
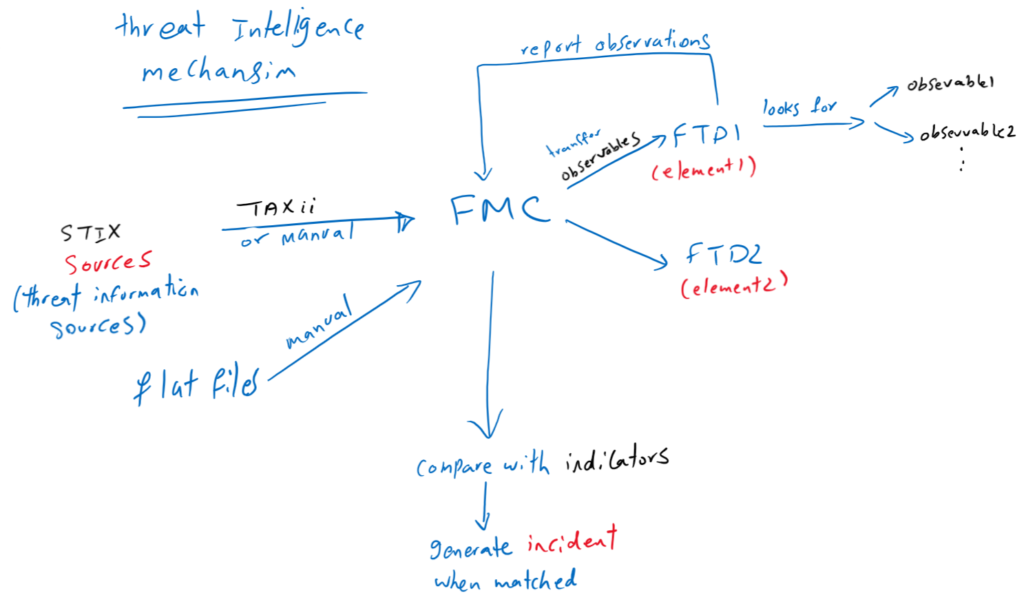
FMC get threat information data in the format of STIX or flat files from third party sources. threat information can be transferred manually or by the help of TAXii protocol to the FMC. FMC pushes observables information to all FTD devices in our network. FTD devices are called elements.
After the observables are published to the elements (FTDs), FTDs monitor traffic and report observables to the FMC when they are observed in traffic.
FMC collects observations from all FTDs, evaluates observations against indicators, and generates incidents when an indicator is matched.
TID and Security Intelligence
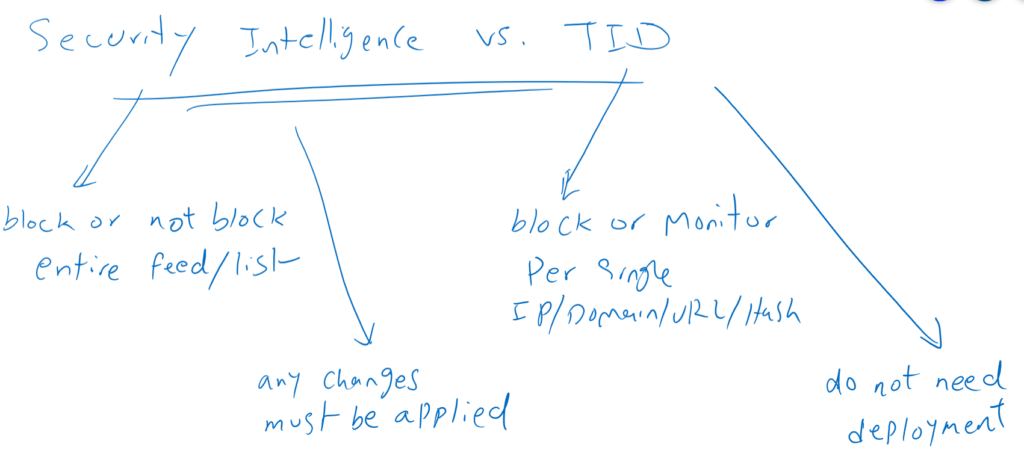
As you have seen, TID enhances the FTD ability to block connections based on security intelligence from third-party sources. TID brings the following main advantages.
- In security intelligence you can block or not block the entire list or feed but in TID you can monitor or block per observables.
- Another important feature in TID is that you don’t need to deploy changes and changes are applied immediately.
Configure Cisco FTD Threat Intelligence Indicator (CTID)
There is an intelligence menu in FMC that is used to configure threat intelligence.
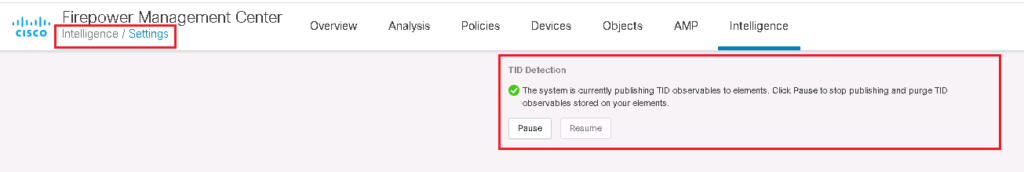
In Intelligence -> Settings menu, we can enable or disable Threat intelligence feature. By default it is enabled and all observables are published to FTDs.
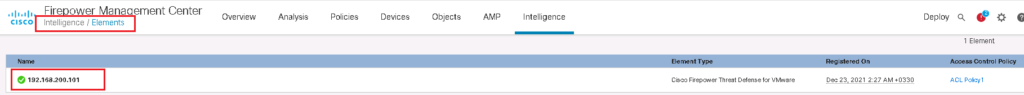
In Intelligence -> Elements menu, the list of FTDs where observables are published is displayed. This is the task of FTD to look the traffic to observe any object (IP/Domain/URL/Hash value) defined in observables.
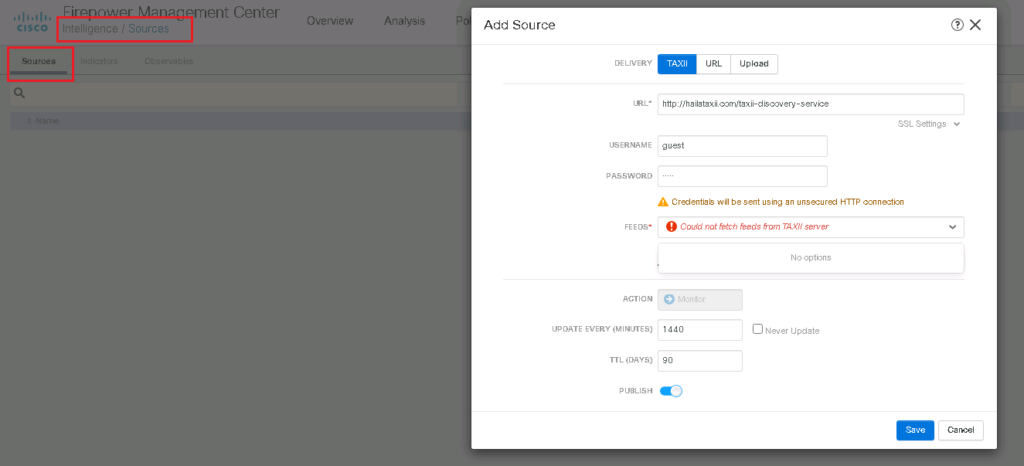
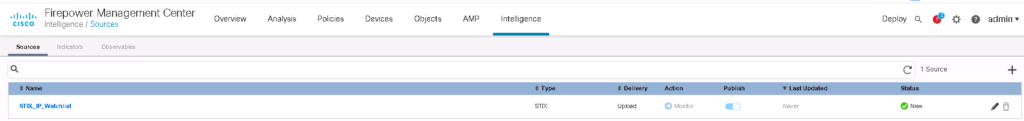
In Intelligence -> Sources -> Sources, we can add a new source of information, uploading manually or downloading dynamically through TAXii protocol. The source file can be a STIX file or a simple flat file.
Sample STIX file can be downloaded from this link.
As an example, in this link can be used with “guest” as the username and password as a sample for threat source to be received by the TAXii protocol.
username: guest
password: guest
as the first example, I try to download threat information source by TAXii protocol. my IP address is blocked and I am not able to download it. But probably there is no problem for you.
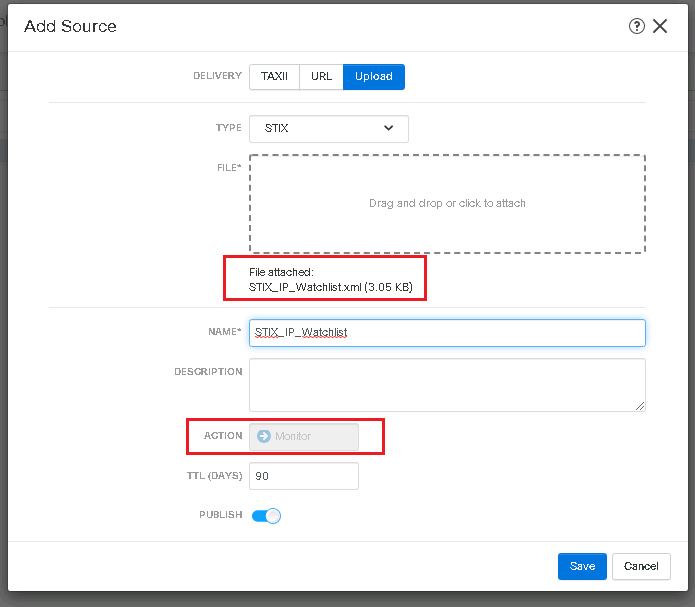
For the second example, I upload a STIX file. As you can see the action is monitor and we cannot change it.
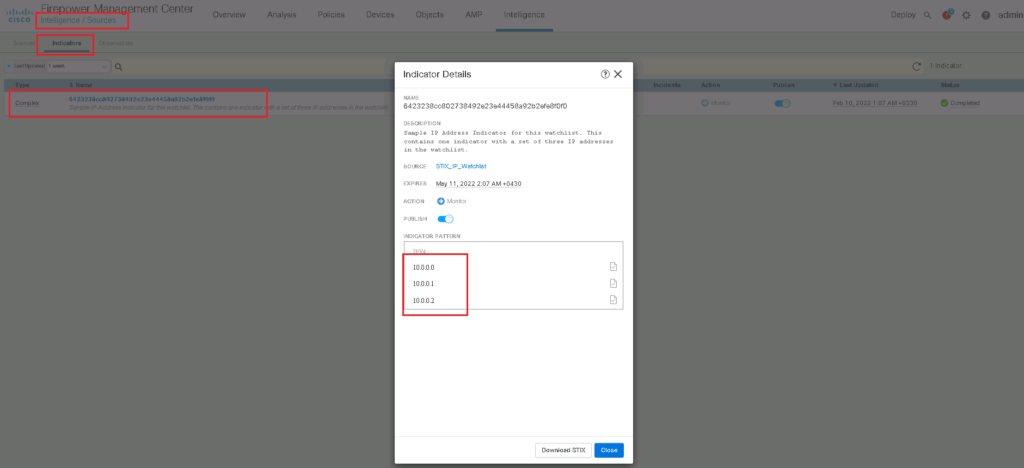
In indicator tab, we can see that this file has a single indicator which includes three observables with the format of IP address, 10.0.0.0, 10.0.0.1 and 10.0.0.2. FTD must look in traffic to observe these IP addressed.
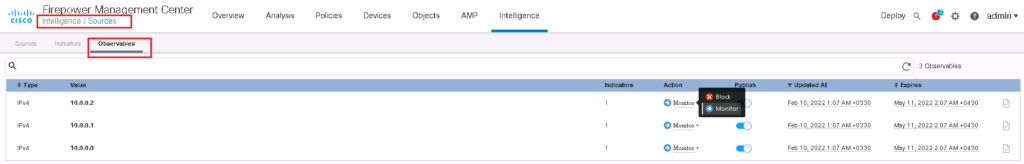
In observables tab, you can see that three observables inside this single indicator is displayed separately. We have the capability to change the action of each observable to block or monitor which is advantage of “Threat Intelligence” comparing to “Security Intelligence”.
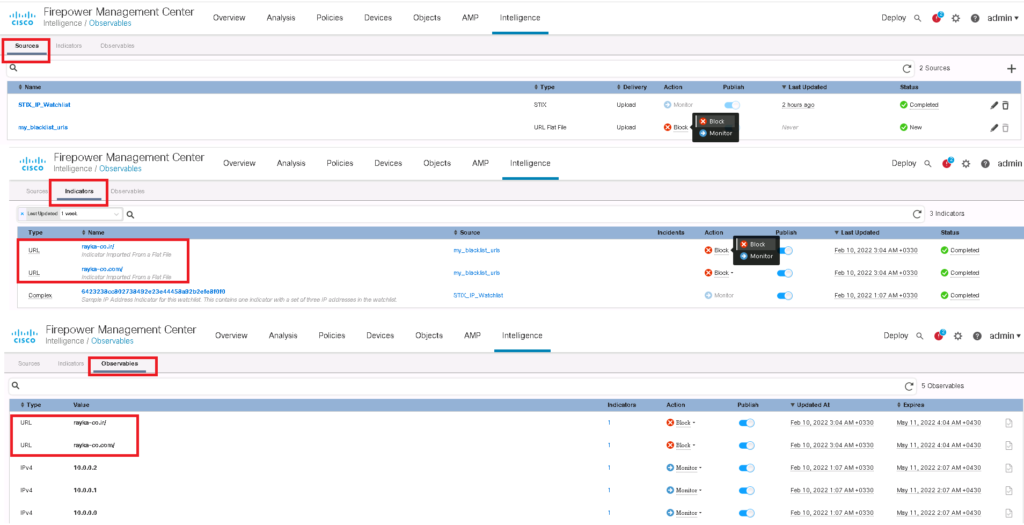
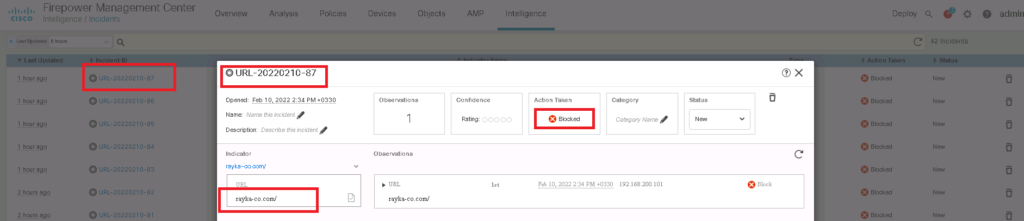
For the third example, I give a flat file including URL addresses that I have personally created. It includes two URLS. https://rayka-co.ir and http://rayka-co.com .
We have the option to give flat file with the content of different types including IP, URL, Domain, Email and Hash Value. We have also the capability to change the default action between “Monitor” and “Block”.
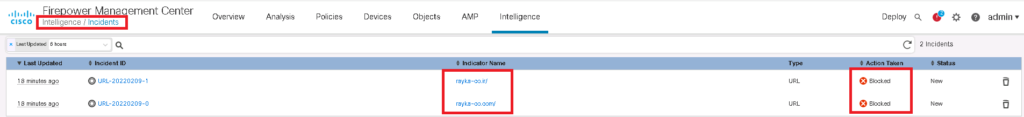
As we can see, each of our URLs are saved as a separate indicators and also observables.
Now we can generate traffic to rayka-co.ir and rayka-co.ir. we expect that we are blocked and indicator is matched and incident is generated.
Another excellent share. Am doing this for a client but with 7.2 .
Flow is the same but of course with ‘ light theme’ things are just in different places.
you are welcome
Hi Majid,
Do we need threat license for TID to work? Thank You