Juniper Unicast Reverse-Path-Forwarding (unicast RPF) feature is used to prevent spoofing attacks in which intruder spoof the source IP address in a way to seem that it comes from a legitimate address and it is usually used in DoS attacks.
Juniper Unicast Reverse-Path-Forwarding Fundamental
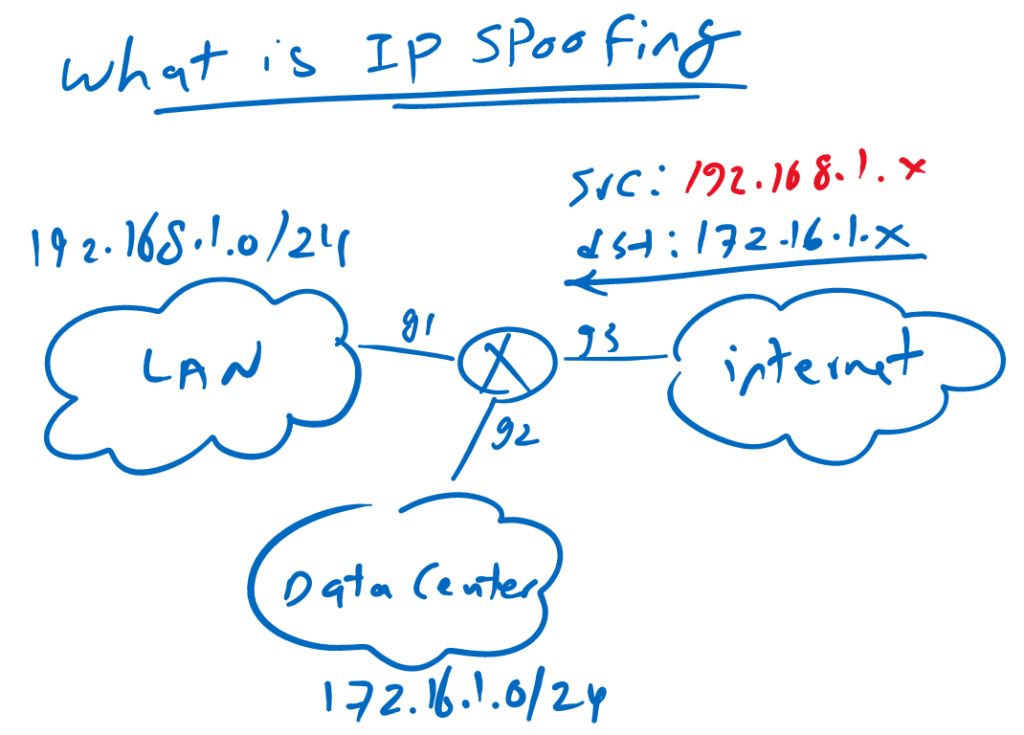
what is IP Spoofing?
To better understand how unicast RPF feature works, let’s first check what is IP spoofing.
This is an enterprise network in which LAN and data center are connected to the internet through enterprise core. 192.168.1.0/24 is the IP address range of LAN network and 172.16.1.0/24 is the IP address range of data center network.
LAN network is connected to the enterprise core through gigabit ethernet 1. Data center is connected to the enterprise core through gigabit ethernet 2. And interface gigabit ethernet 3 is to connect the network to the internet.
Now suppose that an attacker send a traffic from internet to the data center but with source address of 192.168.1.x which is obviously a fake IP address since the source of 192.168.1.x is located in interface gigabit ethernet 1 but the traffic is received in gigabit ethernet 3. this is what we call spoofing of the source IP address.
An attacker change the source IP address to show that it comes from a legitimate source so it can bypass firewall and filtering tools. Spoofing the source IP address very normal in DoS attacks.
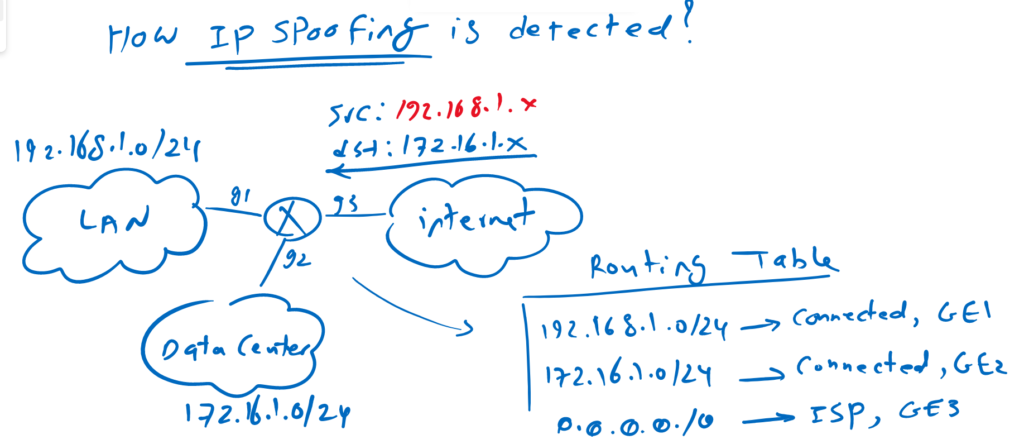
How we can detect that a packet is spoofed and how we can prevent packet spoofing?
In this figure from human point of view it is completely obvious. But let’s check how router or a firewall can detect and prevent it
how IP Spoofing is prevented?
Packet spoofing is detected with the help of routing table.
As you can see in the routing table, route knows that 192.168.1.0/24 and 172.16.1.0/24 is connected to gigabit ethernet 1 and gigabit ethernet 2 and default route outgoing interface is gigabit ethernet 3.
When a packet is received in the router, the source of the packet is checked with routing table and the packet must be received in outgoing interface of the active route for the source IP address otherwise it will be discarded.
In this example the packet is received with source of 192.168.1.x and gigabit ethernet 1 is the outgoing interface of active route for the address 192.168.1.0/24, but the packet is received in gigabit ethernet 3. So this is an spoofing packet and will be discarded.
This is exactly how unicast RFP strict mode works.
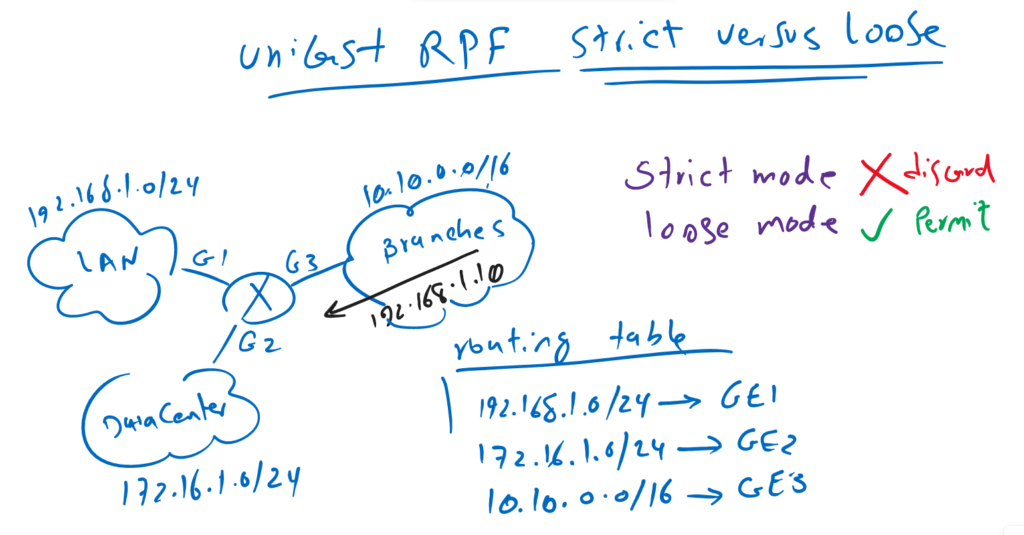
Juniper Unicast Reverse-Path-Forwarding strict and loose Modes
What we have explained is exactly unicast reverse-path-forwarding strict mode and is the default mode of RPF in juniper devices.
But there is another mode for unicast RPF which is called loose mode in which outgoing interface is not important and what is important is that there is a route for the source IP address. and if there is no route for the source IP address the packet will be discarded.
In this example, LAN, data center and WAN with IP address ranges 192.168.1.0/24, 172.16.1.0/24 and 10.10.0.0/16 are connected to interface gigabit ethernet 1, gigabit ethernet 2 and gigabit ethernet 3.
A packet is received in interface gigabit ethernet 3 with source address of 192.168.1.10. this packet will be permitted by unicast RPF loose mode since there is a route for 192.168.1.0/24 in the routing table. But this packet is discarded by unicast RPF default strict mode since the outgoing interface of 192.168.1.0/24 is gigabit ethernet 1 but the packet is received in gigabit ethernet 3.
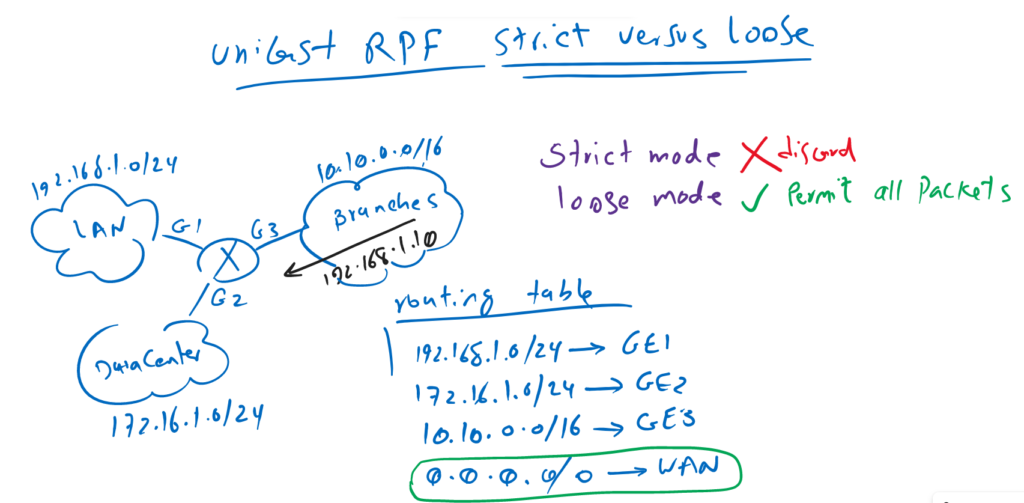
Unicast RPF loose mode will permit all packets if there is a default route in the routing table since the route will match every packet with any source IP address. in other words unicast RPF loose mode is somehow useless when there is a default route in the routing table.
I have pointed “somehow”, since loose mode can discard packets with the source address pointing to the discard interface which is out of our discussion.
Juniper Unicast Reverse-Path-Forwarding Basic Configuration
To enable unicast RPF feature in any interface, we use the command “rpf-check” for the strict mode and “rpf-check mode loose” for loose mode inside interface contextmode.
!!! strict mode
set interfaces ge-0/0/0 unit 0 family inet rpf-check
!!! loose mode
set interfaces ge-0/0/0 unit 0 family inet rpf-check mode looseJuniper Unicast RPF Active-Path and Feasible Path
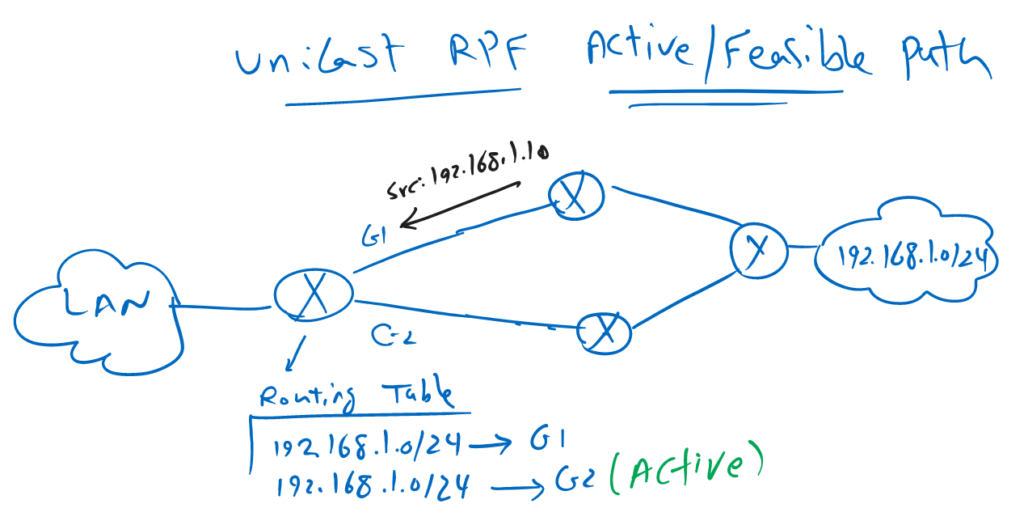
If a packet is received in an interface, in which more than one route exist for the source of the packet, then only the active route will be used to decide if packet will be discarded or allowed to be transferred.
To better understand it, in this figure a router receive a packet in interface G1 with the source address of 192.168.1.10. but in the routing table of the router, there are two path for the address 192.168.1.0/24 and outgoing interface G2 is the active route.
By default this packet is discarded in strict mode since only active route is the decision criteria for RPF checking.
With the command “set routing-options forwarding-table unicast-reverse-path feasible-paths”, we can change the policy so that the feasible paths are also acceptable to RPF check. This can be especially useful in networks with asymmetric routing.
!!! unicast RPF active-path or feasible-path
set routing-options forwarding-table unicast-reverse-path active-paths
or
set routing-options forwarding-table unicast-reverse-path feasible-pathsuse Fail-Filter to bypass Unicast RPF check
There is another feature in juniper Reverse-Path-Forwarding, name “fail-filter” to bypass unicast RPF check for some traffic. these traffic don’t pass RPF check but they are legitimate
For example the source of one DHCP packet is “0.0.0.0” and destination is “255.255.255.255”. if this packet is received on an interface with RPF checking, then it will be discarded.
To configure fail-filter, we have to first configure a firewall filter to accept these special packets then we apply it to the interface RPF check command.
!!! unicast RPF fail-filter
set firewall filter rpf-special-case-dhcp term allow-dhcp from source-address 0.0.0.0/32
set firewall filter rpf-special-case-dhcp term allow-dhcp from destination-address 255.255.255.255/32
set firewall filter rpf-special-case-dhcp term allow-dhcp then count rpf-dhcp-traffic
set firewall filter rpf-special-case-dhcp term allow-dhcp then accept
set firewall filter rpf-special-case-dhcp term default then log
set firewall filter rpf-special-case-dhcp term default then reject
set interfaces ge-0/0/0 unit 0 family inet rpf-check fail-filter rpf-special-case-dhcp